Private consciousness of cybersecurity turned a necessity within the present scenario of accelerating digital transformation. On a enterprise stage or a person stage, you must shield your id, accounts, cash, and so forth.
Coupled with rising distant working alongside the COVID19 pandemic, cyberattacks and breaches have elevated. But most people and firms should not adequately ready for cyber assaults.
With primary private cybersecurity ideas, this text goals that can assist you improve your capability to guard your self towards the subtle strategies of hackers that proceed to evolve.
Let’s discover…
#1. Self-awareness Function and precaution
Regardless of this, programmers and software program producers are very cautious to guard the tip customers, however private cybersecurity is just like the lock of your own home door. Though many cops need to shield you, you additionally must lock your entrance door your self. Cybersecurity can also be everybody’s duty.
That you must be sure to are cognitively up to date. Most cybersecurity issues rely upon updating your information on the most recent hacking and malware developments. In lots of circumstances, the success of cyber threats was as a result of ignorance or neglect of some easy safety ideas.
#2. Understanding digital id and the character of the cyber world
On the web, you might have many alternative digital identities than your actual id. Within the cyber world, it’s important to enter your digital id qualities within the type of credentials to determine your self because the proprietor of the gadget/account, so you must shield these credentials fastidiously. It appears to be like like your actual credentials, face, sound and nationwide ID card, and many others.
So if attackers know your cyberworld credentials, which might normally be your username and password, you’ve got fallen prey to them. They’ll entry your non-public messages and pictures in your social media account or your checking account data and cash.

#3. Allow automated safety updates
On your gadgets’ software program, from the working system (Home windows, Android, Mac, and many others.) to the browser extension, you should set each software and software program in your gadgets to the automated replace possibility.

Updating software program provides new options and allows software program firms to repair bugs and take away vital vulnerabilities that hackers exploit to hold out their assaults.
Regardless of the horror brought on by the rise in cyber threats, updating all software program will permit you to take pleasure in secure computing and looking the net nearly midway.
As well as, you need to commonly replace your antivirus and firewall purposes. This was recognized for a very long time on the PCs, nevertheless it has lately been advisable for smartphones as nicely, though telephones nonetheless don’t mandate putting in antivirus because it does in Home windows OS.
The advantages of updating safety software program is that they sustain with the most recent cyber assault developments. This successfully helps shield your gadgets from new malicious information and viruses and protects your knowledge from assaults that injury or steal them.
Antivirus is not only for PCs, it is also for companies.
#4. Keep away from sharing and clicking unknown hyperlinks
For those who click on someplace with out checking the legitimacy of the web site or if you happen to obtain an attachment with out realizing the sender of the e-mail, malicious software program can find yourself in your gadget. It could possibly be an contaminated URL that installs ransomware that locks your entry to your knowledge except you pay cash to the hacker.

Additionally it is advisable to put in some browser plugins that block automated downloading of scripts or Java, whereas the content material of flash plugins can host malicious code.
Relating to sharing, don’t disclose your password and delicate data to anybody. Additionally, if you happen to use multi-factor authentication that mixes a number of forms of credentials, face, fingerprint, SMS-based authentication to your telephone with a single-use code, don’t give this SMS code to anybody else.
For instance, some attackers ask you to provide this code to affix a Whatsapp group, do not give them.
Generally, consultants stated that sharing is just not essential, not solely to your credentials, however even for a lot of your private data. It’s endorsed to share the minimal quantity of non-public data on social media. As well as, examine your privateness settings on all of your social media accounts, particularly Fb.
#5. Keep away from setting an simply discoverable password
Password must be straightforward to recollect, however this makes it straightforward to find!

Attackers use dictionary-based software program to strive thousands and thousands of attainable and mostly used passwords. Particularly keep away from these high 200 straightforward passwords which might be straightforward to find. As well as, don’t use your identify, surname, date of delivery or something private as a password; hackers can unexpectedly examine your life.
How do you create a password that’s straightforward so that you can bear in mind and not possible for hackers to determine? It could be greatest if you happen to create a fancy password, however in a approach which you could bear in mind it. Take for instance the primary letters of some quotes; this makes them a brand new non-dictionary. Then customise it with some numbers and symbols to extend its energy.
The password should even be lengthy. And it will assist if you happen to use a distinct password for every login, so that you want Password Supervisor software program. It ensures that you just solely have to recollect one lengthy password for all of your logins, and it is referred to as the grasp password.
#6. Concentrate on deceptive social engineering strategies
Social Engineering is usually utilized in advertising and marketing and politics. However within the cyber world, it’s typically used for hacking and deception. By gaining your belief to provide them a few of your credentials, they trick you into breaching your knowledge. It has change into simpler with the smartphone.

Lately, the variety of cyber assaults has elevated since using the smartphone.
Social engineering deception is just not based mostly on technological vulnerabilities, however on the conduct of individuals or customers. Social engineering deception existed earlier than computer systems, however computer systems and smartphones make it simpler to do. However we shouldn’t be afraid to make use of digital expertise if we actually perceive it.
To keep away from social engineering, you have to be conscious of some hidden biases about your self. For instance, you might have an electronic mail claiming that you just urgently have to reply inside 24 hours to get your inheritance and to provide them your password or ship them some cash or your password. One other instance, after they exploit respect for an authority just like the police or your boss to provide them your password. In any case, don’t give the password to anybody.
#7. All the time set up your apps from a respectable software program retailer.
Be sure to obtain your apps and software program from the unique web sites on the pc; keep away from these modified or cracked. Whenever you double-click the set up file (EXE), a message seems on the Home windows display with the identify of the software program writer.
If the message colour is blue and the identify of the writer is listed, it is OK. But when the writer identify is unknown and the message colour is yellow, you need to keep away from putting in this unknown writer software program; it could be that malware can corrupt your knowledge.
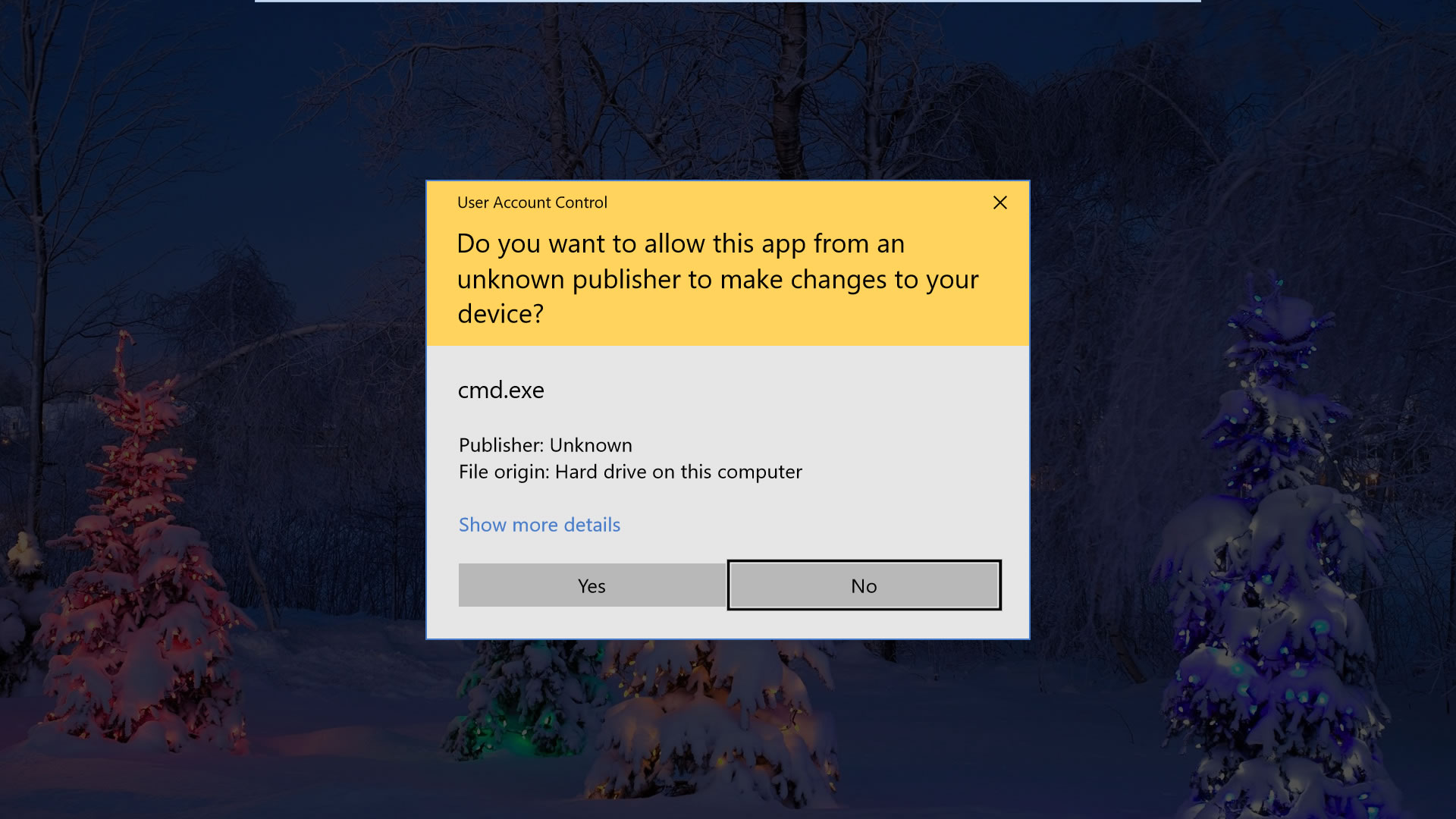
On your smartphone, all the time be certain that to put in solely from respectable safe shops, reminiscent of Google Play, Samsung Retailer, App Retailer. And keep away from putting in apps from third-party sources.
#8. Examine the e-mail tackle and hyperlink area identify
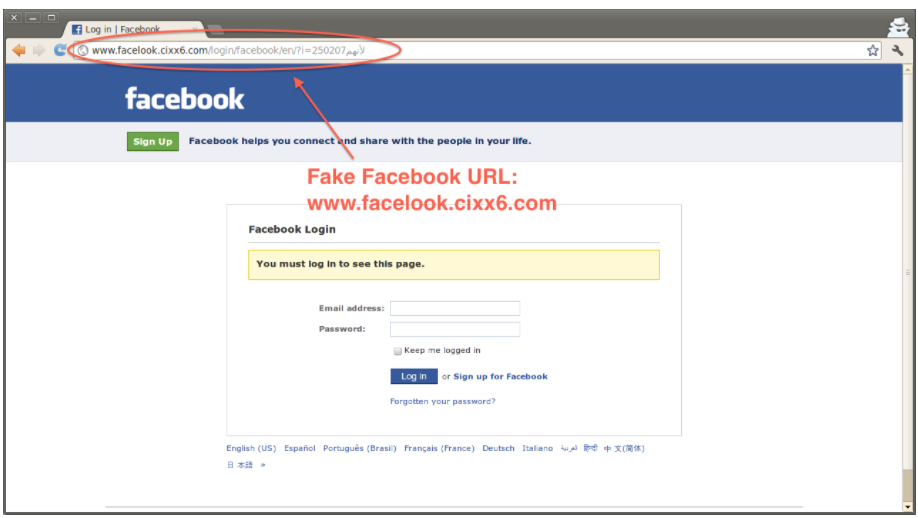
Whenever you obtain an electronic mail or open a URL, you must make certain of the sender’s area identify and electronic mail tackle. For instance, you possibly can open a URL that seems as a real-looking Fb web site. However if you happen to examine the area identify above within the area field, you would possibly discover one thing like “fb.instance.com”. This isn’t Fb’s unique area identify, or chances are you’ll discover one thing else, reminiscent of fb.com; notice right here is one other (o) letter. The identical goes for the e-mail tackle.
These pretend domains/electronic mail addresses are designed to trick and phishing you. For those who log in with the pretend Fb URL and enter your username and password, the hacker on the opposite finish will take it and hack into your Fb account. In case of pretend electronic mail, they could attempt to persuade you to pay some cash or give important data by claiming to be from Google safety group or Paypal and many others. So examine fastidiously the sender tackle of the e-mail .
#9. Distinguish between backup and cloud sync
Backing up is a necessary safety process even earlier than the proliferation of the Web; it secures a duplicate of your delicate knowledge and even your complete system and software program on an exterior drive or within the cloud. You’ll be able to get better your knowledge if it has been corrupted or compromised by a hacker, or even when solely the gadget crashes.
There are lots of choices for backup software program and {hardware}, and automated backup is one of the best. A few of them work in your native gadget and retailer the backup on an exterior drive, which doesn’t require high-speed web.
Some others add your knowledge to the cloud, please notice that cloud sync is just not a backup; within the cloud sync you might have a mirror of your information and knowledge. So when it’s modified or deleted out of your gadget, it should even be deleted within the cloud. However some cloud companies permit you to get better your information.
#10. Study extra about utilizing Wi-Fi safely
Folks usually like to make use of free public Wi-Fi.

When utilizing it, understand that it’s a fertile setting for hackers to steal your delicate data and even achieve entry to your smartphone/laptop computer. You need to use it to look at some movies or browse the net, however keep away from coming into any login situations for any of your accounts.
In another superior circumstances, chances are you’ll be stunned that your smartphone remains to be related to your house Wi-Fi router even after transferring to a distant place from your house. Be very conscious; it may be one other pretend Wi-Fi community in your space that emulates the identical identify and password as your house Wi-Fi community. It’s meant to interrupt your smartphone. Some individuals might imagine they’re one way or the other nonetheless related to the identical house WiFi router, however that is not possible for lengthy distances.
Conclusion
By now you need to have understood a number of the private fundamentals of cyber safety. That you must step ahead to cope with it, and so long as you keep awake and replace your safety instruments and consciousness, you are normally on the secure facet.

