The attention-catching view of various Open Supply Intelligence (OSINT) instruments which might be accessible available in the market.
In our day by day lives, we search for lots of knowledge on the web. If we don’t discover the anticipated outcomes, we often give up!
However have you ever ever imagined what lies in that tons of of web page outcomes? “Data”!
This may be attainable solely through the use of totally different instruments. Instruments play a major function in looking for data however, with out realizing the significance and utilization of instruments, it is not going to be useful for the customers. Earlier than getting began with the instruments, let’s have a transparent thought about OSINT.
What’s Open Supply Intelligence?
Open Supply Intelligence, briefly, referred to as OSINT, refers back to the assortment of knowledge from public sources to make use of it within the context of intelligence. As of in the present day, we live within the “world of the web” its influence on our lives may have each execs and cons.
The benefits of utilizing the web are, gives plenty of data and simply accessible by everybody. Whereas, the disadvantages are misusing the data and spending loads of time on it.
Now, right here comes the existence of OSINT instruments that are primarily used to gather and correlate data on the internet. Data will be accessible in numerous types; it may be textual content format, file, picture, and so forth. In line with the CSR Report for Congress, it has been stated that Open Supply Intelligence has been produced from the general public data that’s appropriately disseminated, collected, and exploited successfully. And makes this data accessible for the customers to handle a particular intelligence requirement.
Why we require OSINT instruments?
Allow us to contemplate one scenario or state of affairs through which we have to discover data associated to some subjects on the internet. For this you want first to look and do evaluation until you get the precise outcomes, this consumes loads of time. That is the principle motive why we want intelligence instruments as a result of the method talked about above will be carried out inside seconds utilizing these instruments.
We even can run a number of instruments to gather all the data associated to the goal, which will be correlated and used later.
So let’s deep dive into among the greatest OSINT instruments.
Legal IP
Legal IP is a distinguished OSINT search engine for cybersecurity, designed to gather and analyze menace intelligence by gathering real-time knowledge on over 4.2 billion IP addresses and cyber belongings. By way of Legal IP’s Asset Search and Area Search, customers can simply and shortly entry desired asset data.
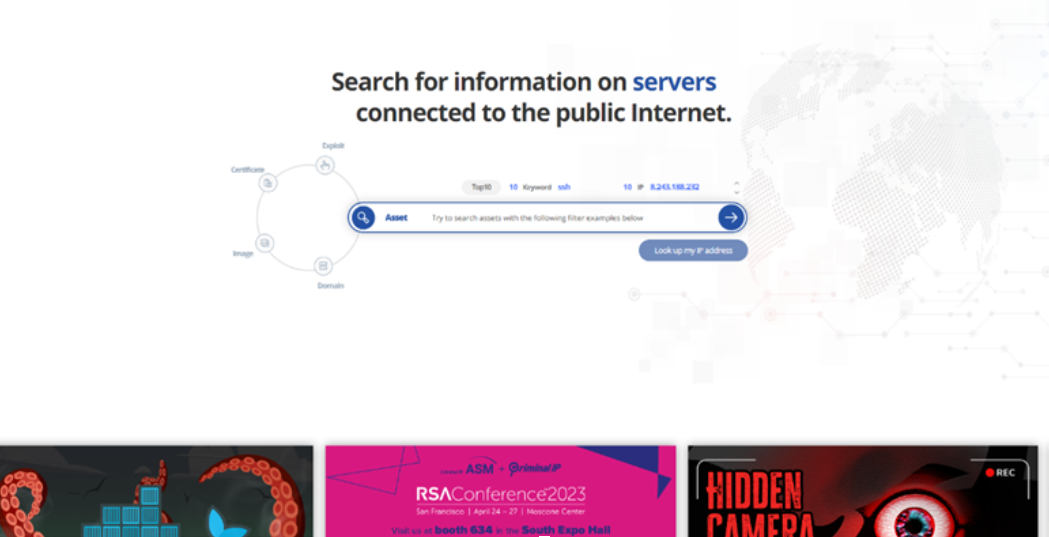
This features a complete vary of knowledge for pentesting, reminiscent of a 5-level threat rating, present open port data and vulnerabilities (CVE codes), chance of phishing URLs, abuse data, faux favicon utilization, linked IPs, and subdomain data.
Moreover, numerous search filters enable customers to successfully extract the specified belongings.
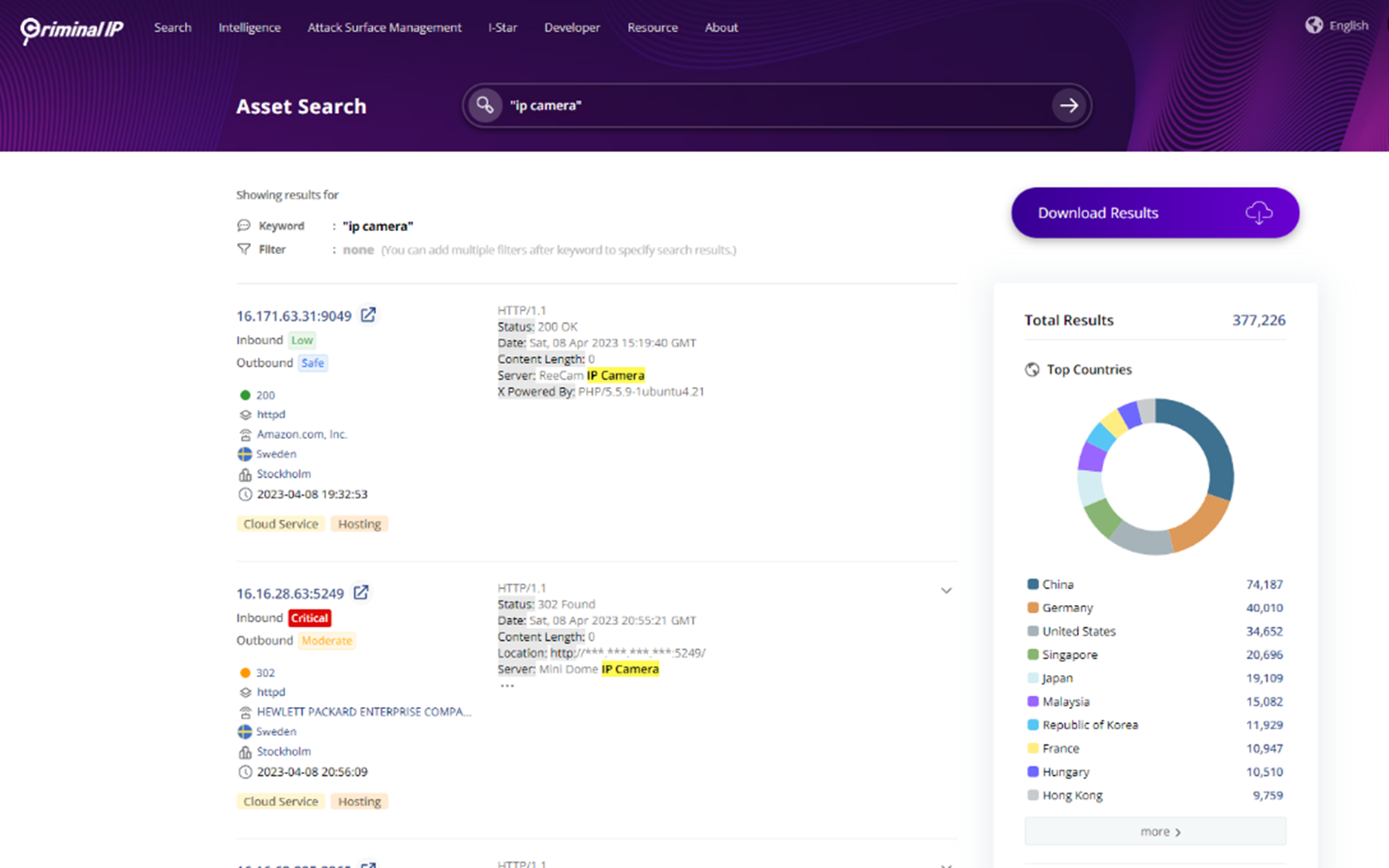
The search will not be restricted to phishing websites or malicious IPs, as it could additionally seek for all belongings linked to the web, together with IoT units and certificates.
Shodan
Google is essentially the most used search engine for all, whereas Shodan is a incredible and goldmine search engine for hackers to see uncovered belongings.
When in comparison with different serps, Shodan gives you the outcomes that make extra sense and associated to safety professionals. It primarily consists of data associated to belongings which might be being linked to the community. The units could differ from laptops, site visitors alerts, computer systems, and numerous different IoT units. This open-source device primarily helps the safety analyst in figuring out the goal and check it for various vulnerabilities, passwords, providers, ports, and so forth.
Furthermore, it gives customers with topmost versatile searches by the group.
For instance, allow us to contemplate the scenario through which the one person can see the linked netcams, webcams, site visitors lights, and so forth. We’ll take a look at among the use circumstances from Shodan:
- Testing “default Passwords”
- Property with VNC viewer
- Utilizing the RDP port open to testing the accessible belongings
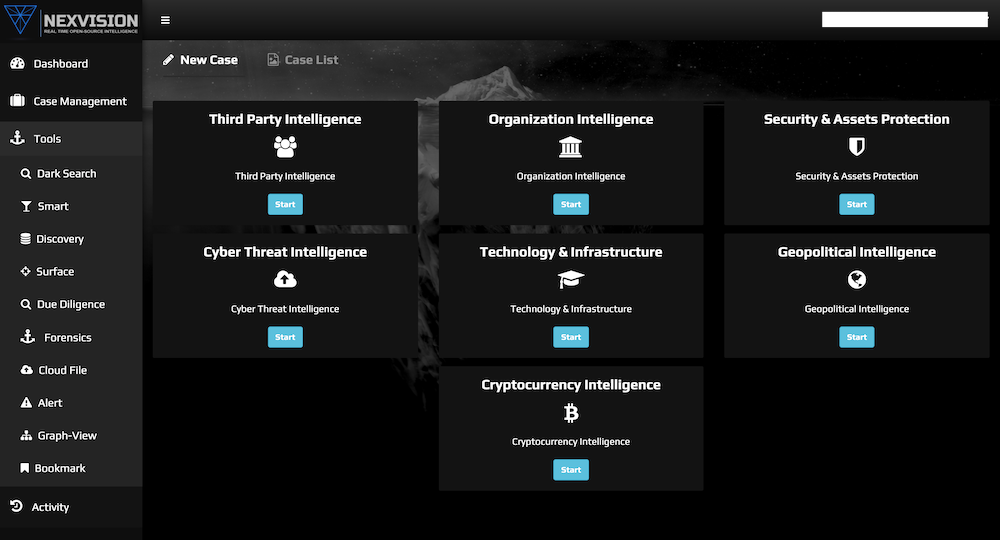
NexVision
NexVision is a sophisticated A.I.-powered OSINT answer that gives real-time intelligence from the Complete Internet (Clear Internet, Darkish Internet, and Social Media). It gives unprecedented entry to Darkish net searches by way of common browsers like Chrome and Safari, with out the usage of anonymizing browser Tor.
In the event you’re trying to conduct background checks, due diligence, buyer on-boarding compliance (KYC/AML/CFT), collect group intelligence, third social gathering intelligence, cyber menace intelligence, and even analysis on cryptocurrency addresses from a ransomware menace, NexVision gives correct real-time solutions.
NexVision is primarily utilized by the navy and governments, however has since 2020, been commercially accessible and relied on by Fortune 500 firms and small-medium companies (SMBs) alike for his or her intelligence and investigative wants. Their service features a direct subscription to their SaaS answer and buying intelligence stories.
The way it works:
In step one, its A.I. powered engine regularly collects knowledge, analyses it, and categorizes them, offering the most important commercially accessible knowledge lake. Within the second step, the engine makes use of machine studying to scale back false positives to offer extremely correct and contextualized outcomes. This enormously reduces the man-hours and time required in investigations and the alert fatigue that analysts face when met with giant quantities of irrelevant knowledge. Within the last step, all the outcomes are mirrored on the dashboard the place customers can simply visualize and make knowledgeable choices.
The dashboard permits customers to set key phrase alerts to observe targets in real-time, conduct investigations, and analyze outcomes while staying nameless.
The software program has a easy interface that’s designed for entry-level analysts. Analysts can entry and use military-grade and complete intelligence with out counting on scripts or writing a single line of code.
Its social media module screens knowledge from Meta (beforehand Fb), Instagram, LinkedIn, Discord, Twitter, Youtube, Telegram, and many others, and comes geared up with geo-location know-how to find out the supply and site of knowledge dissemination.
Social Hyperlinks is a software program firm that develops AI-driven options that extract, analyse and visualise knowledge from open sources together with social media, messengers, blockchains, and the Darkish Internet. Their flagship product SL Skilled empowers investigators and knowledge safety professionals to achieve their work goals faster and extra successfully.
SL Skilled provides a collection of custom-designed search strategies spanning greater than 500 open sources. The product’s superior search queries, lots of which depend on machine studying, enable customers to filter the info as it’s being gathered in a variety of subtle methods.
Nevertheless, Social Hyperlinks OSINT options do extra than simply collect data; in addition they provide superior evaluation instruments for refining knowledge as you progress by way of investigations, returning correct outcomes for an ever extra understandable image of the investigation.
Options
- An expert bundle of 1000+ unique search strategies for over 500 open knowledge sources together with all main platforms throughout social media, messengers, blockchains, and the Darkish Internet
- Superior automation options which leverage machine studying to ship an expansive vary of knowledge retrieval, displaying correct outcomes at exceptional speeds.
- Bespoke evaluation instruments allow knowledge to be considerably enriched and molded to the person’s specific functions.
- Seamless integration inside your IT infrastructure
- Social Hyperlinks provide coaching and help as a part of their product packages.
For organizations who want the last word OSINT answer, Social Hyperlinks even have an enterprise-grade platform SL Non-public Platform – an on-premise OSINT answer providing their widest vary of search strategies, full customization in line with the customers’ wants, and personal knowledge storage.
Google Dorks
Google Dorks have come into existence in 2002, and it provides efficient outcomes with glorious efficiency. This question-based open-source intelligence device is principally developed and created to assist customers in concentrating on the index or search outcomes appropriately and successfully.
Google Dorks gives a versatile means of looking for data through the use of some operators, and maybe it’s also referred to as Google Hacking. These operators make the search simpler to extract data. Under are among the operators or indexing choices supplied by Google Docker, and they’re:
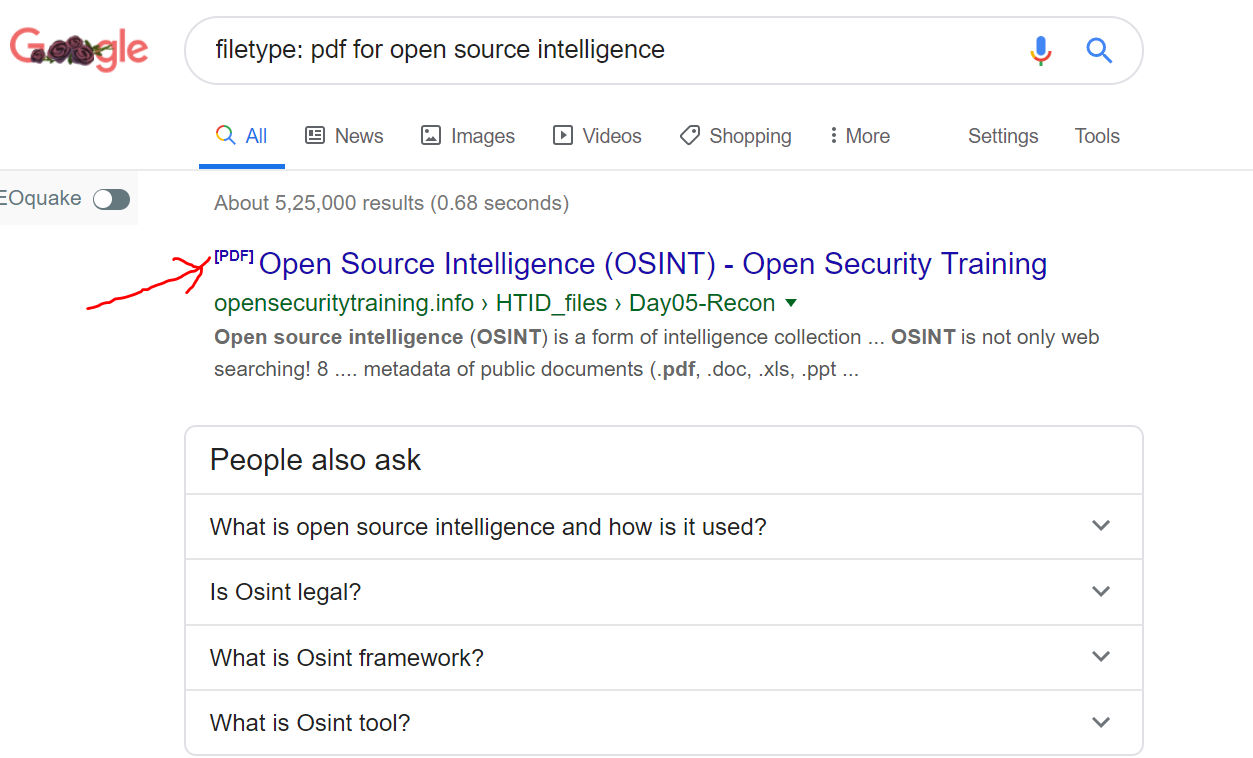
- Filetype: This operator is principally used to search out the file varieties or to seek for a specific string
- Intext: This indexing possibility is used to seek for a particular textual content on a particular web page.
- Ext: That is used to seek for a particular extension in a file.
- Inurl: Used to seek for the precise string or phrase within the URL
- Intitle: To seek for the title or phrases talked about above within the URL
Maltego
Maltego is designed and developed by Paterva, and it is among the inbuilt instruments in Kali Linux. This open-source intelligence device is principally used to carry out a major exploration towards numerous targets with the assistance of a number of in-built transforms (and in addition gives the aptitude to put in writing {custom} ones).
A programming language that you just use in Maltego is written in Java and shows as a built-in pre-packaged within the Kali Linux. As soon as the registration course of is finished, then the customers can use this device to create and develop efficient digital footprints of the actual goal on the web.
The anticipated outcomes could occur to IP conversion, AS quantity is recognized, Netblock can be recognized, even the phrases and areas are additionally recognized. These are all of the icons in Maltego that gives an in depth view and details about all of the icons.
You may even know extra details about the goal by digging extra into the method. Lastly, I can say that it is a wonderful device to trace the footprints of each single entity over the web. Maltego is obtainable throughout all common working methods.
TheHarvester
TheHarvester is an incredible device for locating emails, subdomains, IPs, and many others. from numerous public knowledge.
Under instance to search out the subdomains utilizing DNSdumpster.
[root@geekflare theHarvester]# python theHarvester.py -d geekflare.com -v -b dnsdumpster
*******************************************************************
* _ _ _ *
* | |_| |__ ___ / /__ _ _ ____ _____ ___| |_ ___ _ __ *
* | __| _ / _ / /_/ / _` | '__ / / _ / __| __/ _ '__| *
* | |_| | | | __/ / __ / (_| | | V / __/__ || __/ | *
* __|_| |_|___| / /_/ __,_|_| _/ ___||___/_____|_| *
* *
* theHarvester 3.1.0.dev1 *
* Coded by Christian Martorella *
* Edge-Safety Analysis *
* [email protected] *
* *
*******************************************************************
[*] Goal: geekflare.com
[*] Looking out DNSdumpster.
[*] No IPs discovered.
[*] No emails discovered.
[*] Hosts discovered: 3
---------------------
lab.geekflare.com:104.25.134.107
instruments.geekflare.com:104.25.134.107
www.geekflare.com:104.25.134.107
[*] Digital hosts:
------------------
[root@geekflare theHarvester]#TheHarvester can be accessible on Kali Linux. You may examine the Kali Linux set up information if you happen to want it.
BTW, there are extra instruments to search out subdomains.
Recon-Ng
Recon-ng is an efficient device to carry out reconnaissance on the goal.
All the energy of this device lies utterly within the modular method. The ability of modular instruments will be understood for these used Metasploit. Recon-ng has numerous built-in modules which might be used to focus on primarily whereas extracting data as per person wants. We will use the Recon-ng modules simply by including the domains within the workspace.
Workspaces are primarily created to hold out the operations inside it. The customers will likely be redirected to the workspace as quickly as it’s created. Contained in the workspace, the area will be notably specified utilizing add area <domainname>. Modules of Recon-ng are used to fetch details about the precise area after they (domains) are added into the recon-ng.
Among the glorious modules, reminiscent of google-site-web and bing-domain-web, are used to search out additional domains associated to the primary preliminary goal area. The results of these domains will likely be all of the listed domains to the various search engines. One other catchy module is bing_linkedin_cache which is principally used to fetch the small print of the e-mail addresses associated to the area. This module may also be used to leverage in performing social engineering.
Furthermore, utilizing different modules, we will get fetch the additional or further details about targets. So lastly, this open-source intelligence device is a incredible device and in addition should be included within the toolkit of researchers.
SpiderFoot
SpiderFoot is an open-source reconnaissance device accessible for Linux and Home windows. It has developed utilizing Python language with excessive configuration and runs just about on any platform. It integrates with straightforward and interactive GUI with a robust command-line interface.
It has routinely enabled us to make use of queries over 100+ OSINT sources to seize the intelligence on emails, names, IP addresses, domains, and many others. It collects an in depth vary of details about a goal, reminiscent of netblocks, e-mails, net servers, and plenty of extra. Utilizing Spiderfoot, you could in a position to goal as per your requirement as a result of it would acquire the info by understanding how they’re associated to one another.
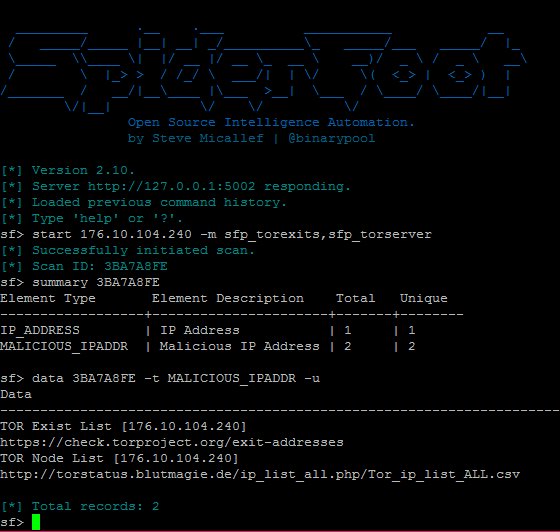
The info collected from a SpiderFoot will present a variety of details about your particular goal. It gives clear insights about attainable hacking threats that are results in vulnerabilities, knowledge leaks, and different very important data. So these insights will assist to leverage the penetration check and improve the menace intelligence to alert earlier than it will get attacked or stolen.
Creepy
Creepy is an open-source Geolocation intelligence device. It collects details about Geolocation through the use of numerous social networking platforms and picture internet hosting providers which might be already revealed someplace else. Creepy presents the stories on the map, utilizing a search filter primarily based on the precise location and date. These stories can be found in CSV or KML format to export for extra evaluation.
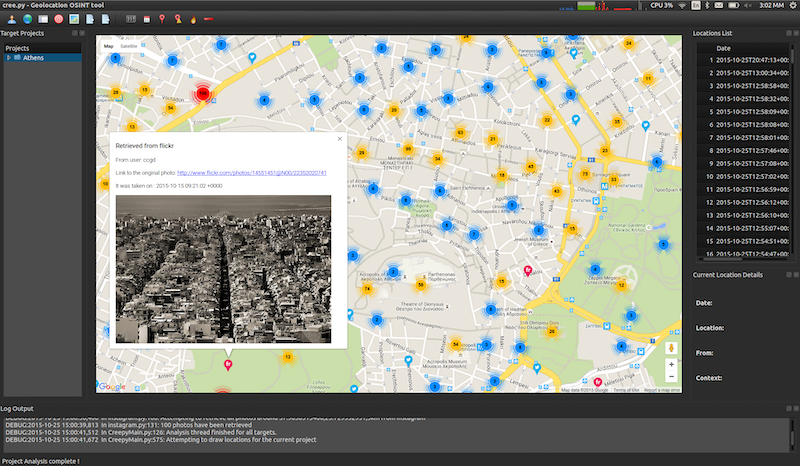
The primary performance in Creepy is split into two foremost tabs viz. ‘Targets’ and ‘map view’ tabs.
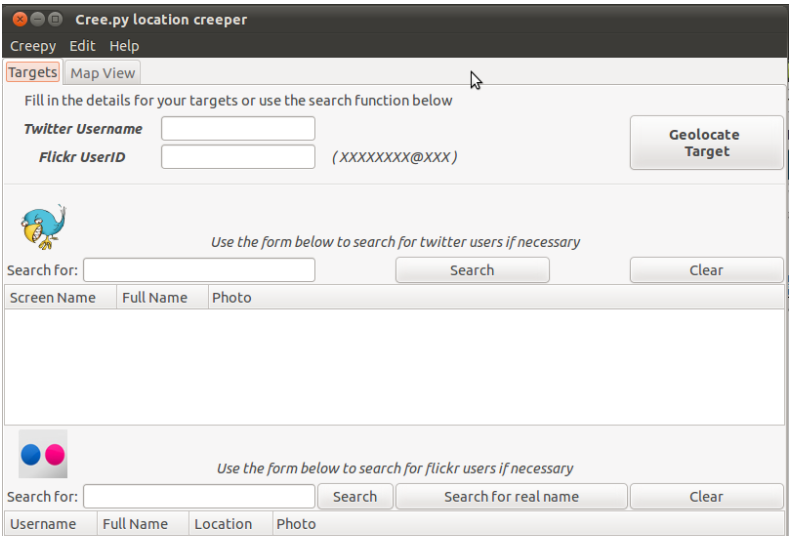
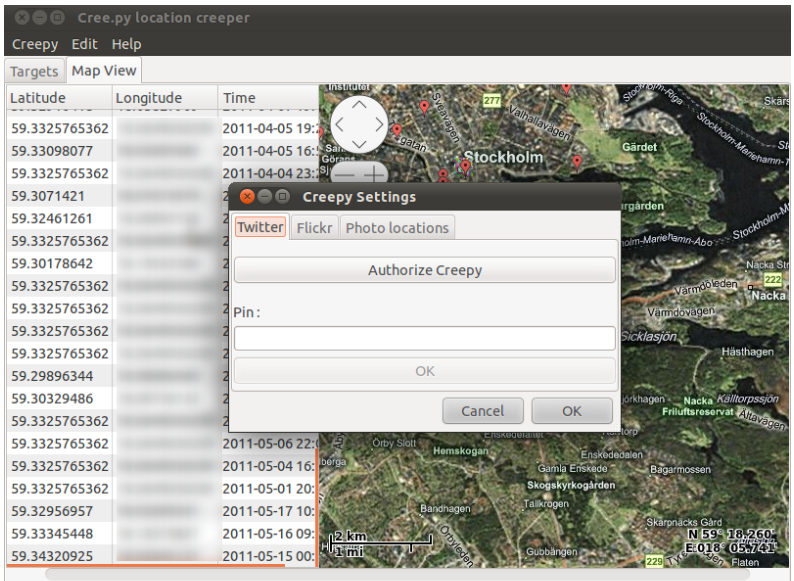
Creepy is written in python and in addition comes with a packaged binary for Linux distributions reminiscent of Debian, Backtrack, Ubuntu, and Microsoft home windows.
Conclusion
Penetration testing is difficult, and it requires data from numerous sources. I hope the above ONIST instruments enable you to with that.
You might also discover on-line pentest instruments for reconnaissance and exploit search.

