The e-commerce panorama has obtained an enormous enhance in latest instances as a consequence of developments in web applied sciences, permitting many extra individuals to connect with the web and make extra transactions.
At the moment, many extra companies depend on their web sites as a serious supply of revenue. Subsequently, precedence needs to be given to the safety of such net platforms. On this article, we check out a listing of a few of the finest cloud-based VAPT (Vulnerability Evaluation and Penetration Testing) instruments out there right now, and the way they can be utilized by a startup and small and medium-sized companies.
First, an internet or e-commerce enterprise proprietor wants to know the variations and similarities between Vulnerability Evaluation (VA) and Penetration Testing (PT) so as to make your choice when making selections about what’s finest for your corporation. Whereas each VA and PT provide complementary companies, there are solely refined variations in what they purpose to realize.
Distinction between VA and VT
When performing a Vulnerability Evaluation (VA), the tester makes an attempt to make sure that all open vulnerabilities within the software, web site or community are outlined, recognized, categorised and prioritized. A Vulnerability Evaluation could be a list-oriented train. This may be achieved by way of using scanning instruments, which we have a look at later on this article. It’s important to conduct such an train because it provides corporations a essential understanding of the place the loopholes are and what they should repair. This train additionally offers corporations with the mandatory data when configuring firewalls, corresponding to WAFs (Net Software Firewalls).
However, a Penetration Testing (PT) train is extra direct and is alleged to be purpose oriented. The purpose right here is just not solely to analyze the applying’s defenses, but additionally to use found vulnerabilities. The aim of that is to simulate real-life cyber-attacks on the applying or web site. A few of this may very well be carried out utilizing automated tooling; some will likely be listed within the article and can be carried out manually. That is particularly essential for corporations to know the extent of danger a vulnerability poses and to finest shield such a vulnerability from potential malicious exploitation.
Subsequently we might justify that; a Vulnerability Evaluation offers enter for performing penetration exams. Therefore the necessity to have full-featured instruments that let you obtain each.
Let’s discover the choices…
Astra
Astra is a full-featured, cloud-based VAPT software with a particular deal with e-commerce; it helps WordPress, Joomla, OpenCart, Drupal, Magento, PrestaShop and others. It comes with a collection of purposes, malware and community exams to evaluate the safety of your net software.
It comes with an intuitive dashboard that exhibits a graphical evaluation of threats blocked in your web site given a given timeline.
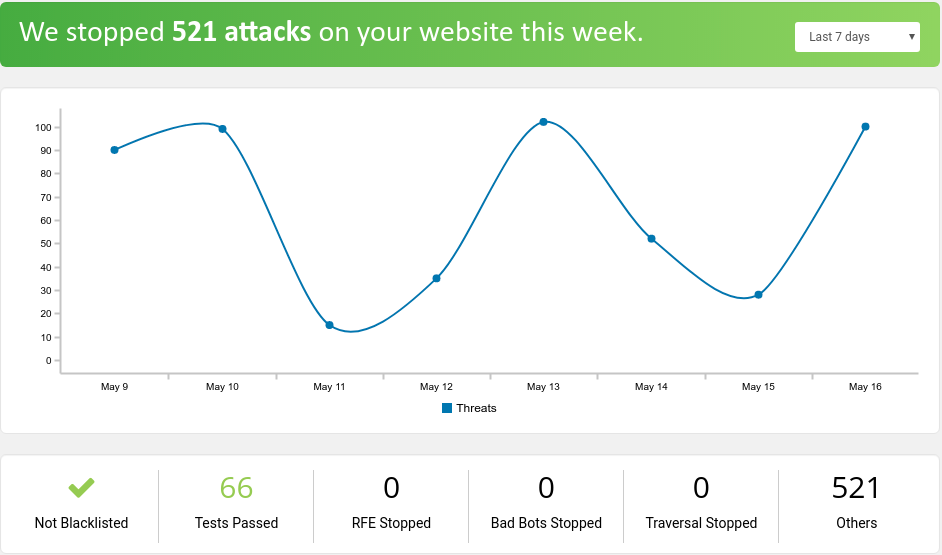
Some options embrace.
- Software Static and dynamic code evaluation
With static code and dynamic evaluation, which checks an software’s code earlier than and through runtime to make sure threats are detected in actual time for rapid remediation.
- Scan malware
It additionally runs an automatic software scan for recognized malware and removes it. Equally, file variations are checked to confirm the integrity of your information, which can have been maliciously modified by an inside program or an exterior attacker. Beneath the malware scan part, you may get helpful details about doable malware in your web site.
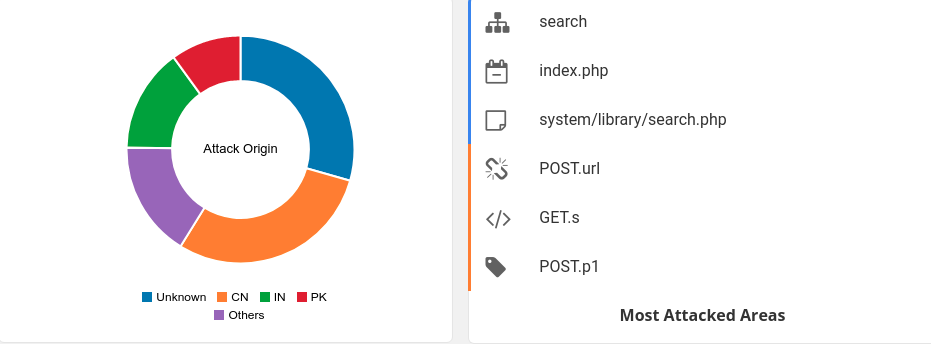
- Menace detection
Astra additionally does automated menace detection and logging, supplying you with perception into which components of the applying are most weak to assaults, which components are most exploited primarily based on earlier assault makes an attempt.
- Cost gateway and infrastructure testing
It performs cost gateway pen exams for purposes with cost integrations, in addition to infrastructure exams to make sure the safety of the applying’s custody infrastructure.
- Check community
Astra comes with a community penetration check of routers, switches, printers and different community nodes that may expose your organization to inside safety dangers.
By requirements, Astra’s exams are primarily based on main safety requirements, together with OWASP, PCI, SANS, CERT, ISO27001.
Invincible
Invicti is a turnkey resolution for medium to giant companies with plenty of options. It encompasses a sturdy scanning perform that’s proprietary Proof-Primarily based-Scanning™ know-how with full automation and integration.
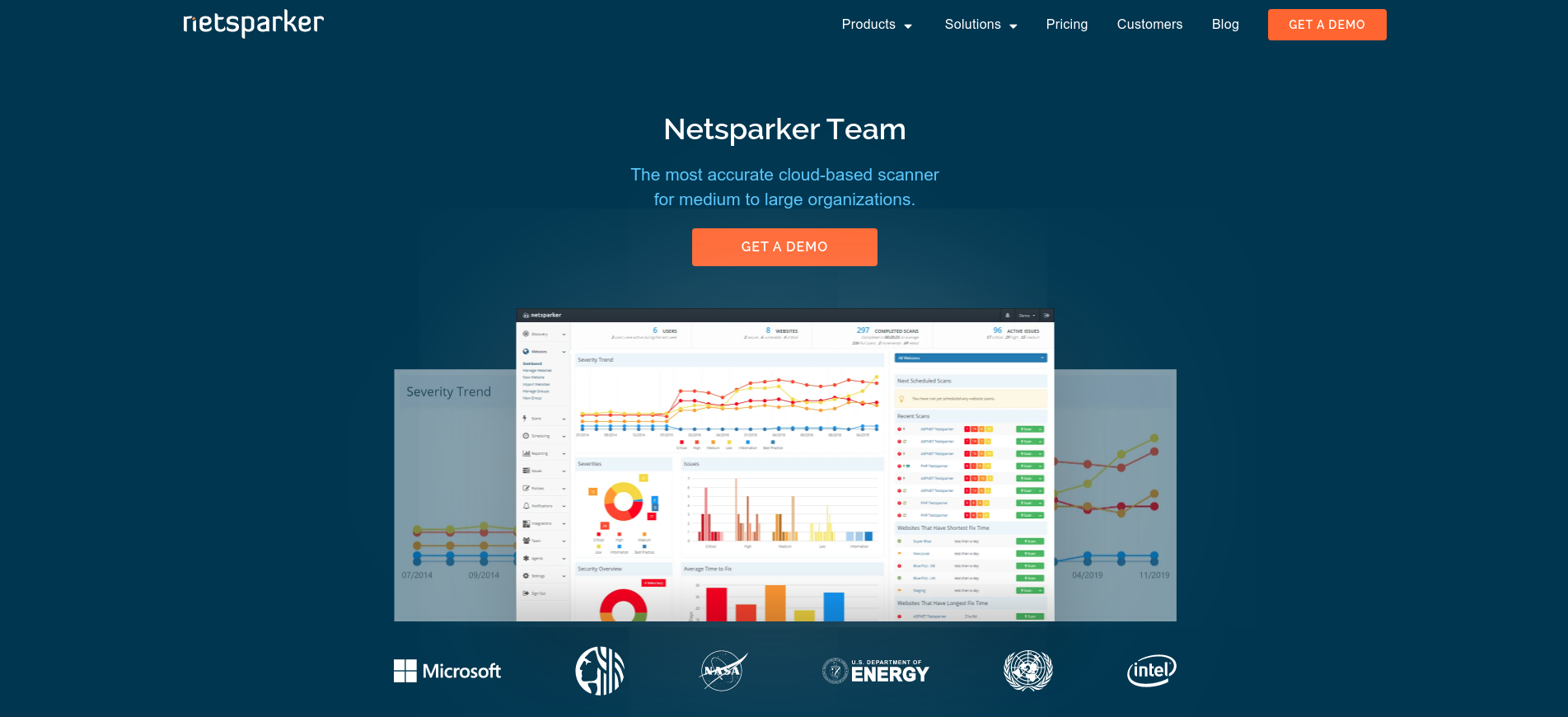
Invicti has a lot of integrations with present instruments. It’s straightforward to combine into concern monitoring instruments like Jira, Clubhouse, Bugzilla, AzureDevops, and so on. It additionally has integrations with undertaking administration methods like Trello. Likewise with CI (Steady Integration) methods corresponding to Jenkins, Gitlab CI/CD, Circle CI, Azure, and so on. This offers Invicti the flexibility to be built-in into your SDLC (Software program Improvement Life Cycle); therefore your construct pipelines can now embrace a vulnerability test earlier than deploying options to your enterprise software.
An intelligence dashboard provides you perception into which safety bugs exist in your software, their severity and which of them have been mounted. It additionally offers you with details about vulnerabilities from scan outcomes and doable safety loopholes.
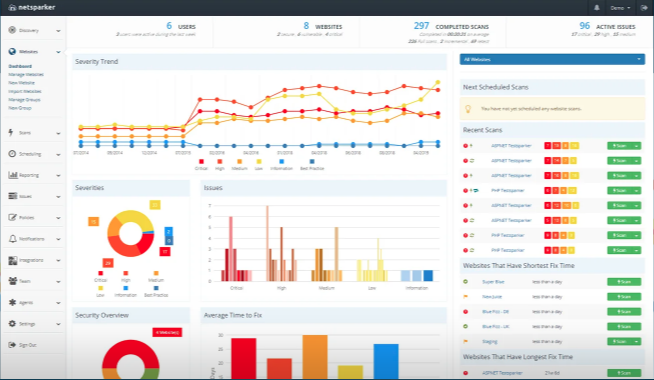
Shelf life
Tenable.io is an enterprise-ready net software scanning software that provides you key insights into the safety outlook of all of your net purposes.
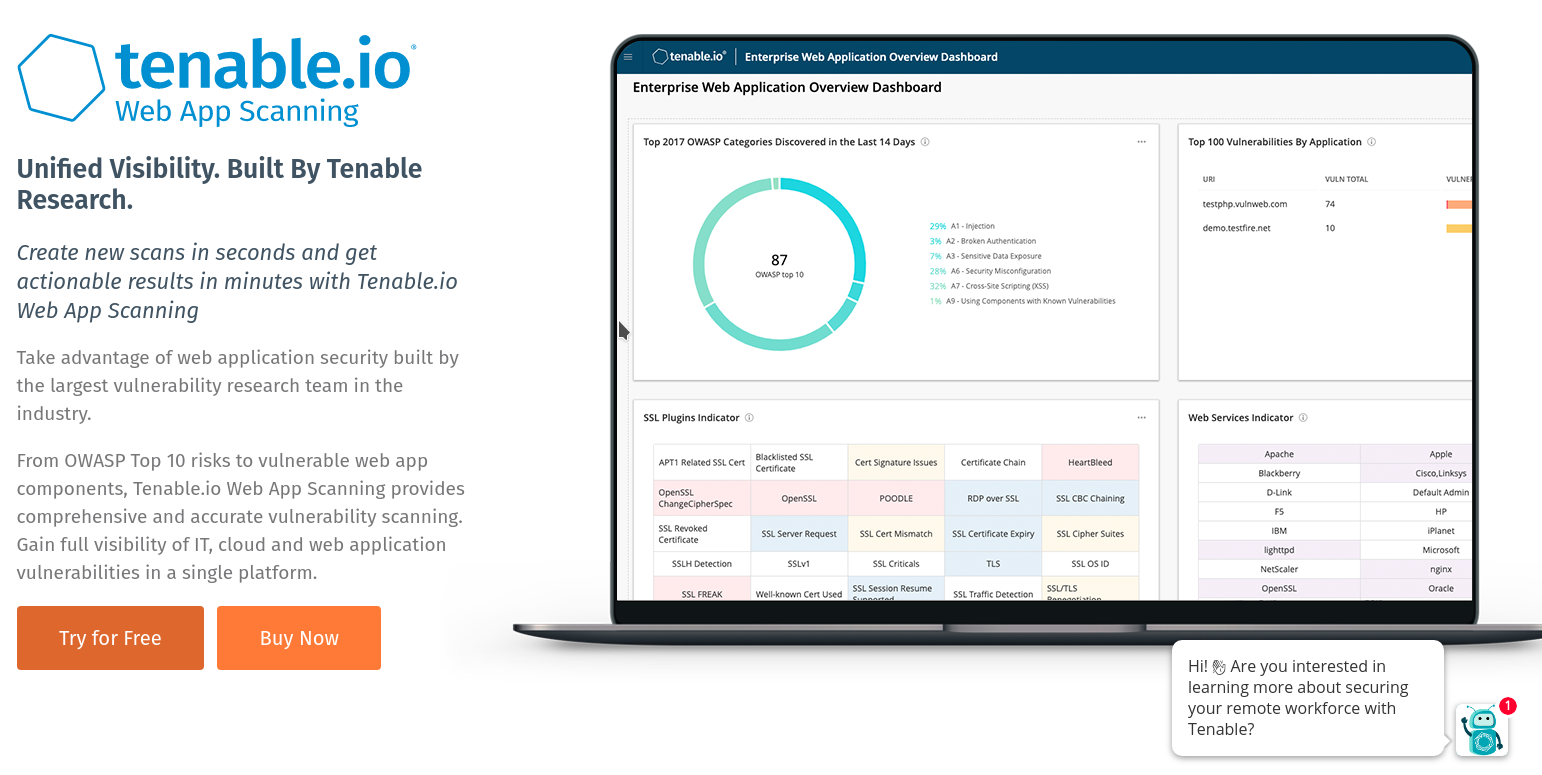
It’s straightforward to arrange and begin. This software doesn’t goal only a single software you’ve working, however all net apps you’ve deployed.
It additionally bases its vulnerability scanning on the very talked-about OWASP Prime Ten Vulnerabilities. This makes it straightforward for any safety generalist to launch an internet app scan and perceive the outcomes. You may schedule an automatic scan to keep away from the repetitive duties of manually rescanning purposes.
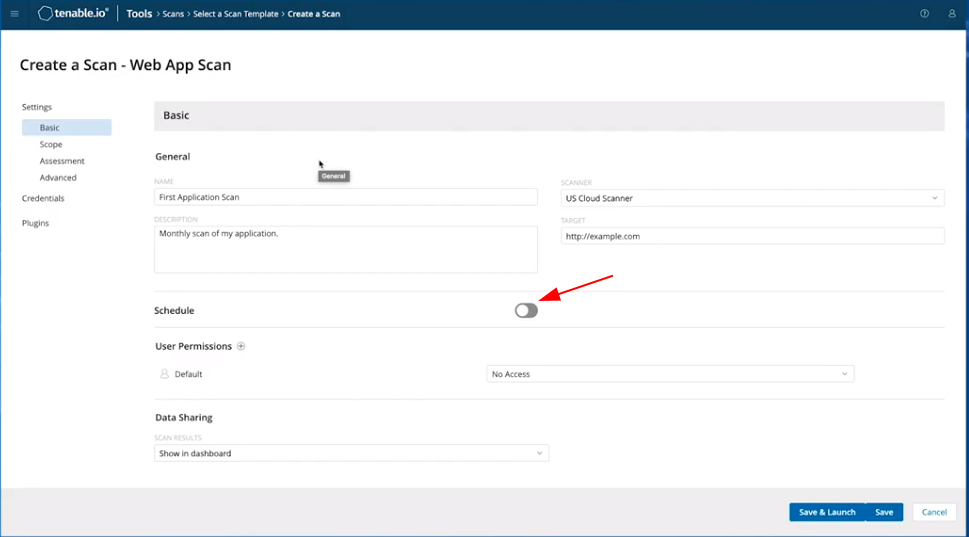
Pentest Instruments
Pentest-tools scanner provides you full vulnerability scan data to test on an internet site.
It consists of net fingerprinting, SQL injection, cross-site scripting, distant command execution, native/distant file recording, and so on. Free scanning can be out there, however with restricted options.
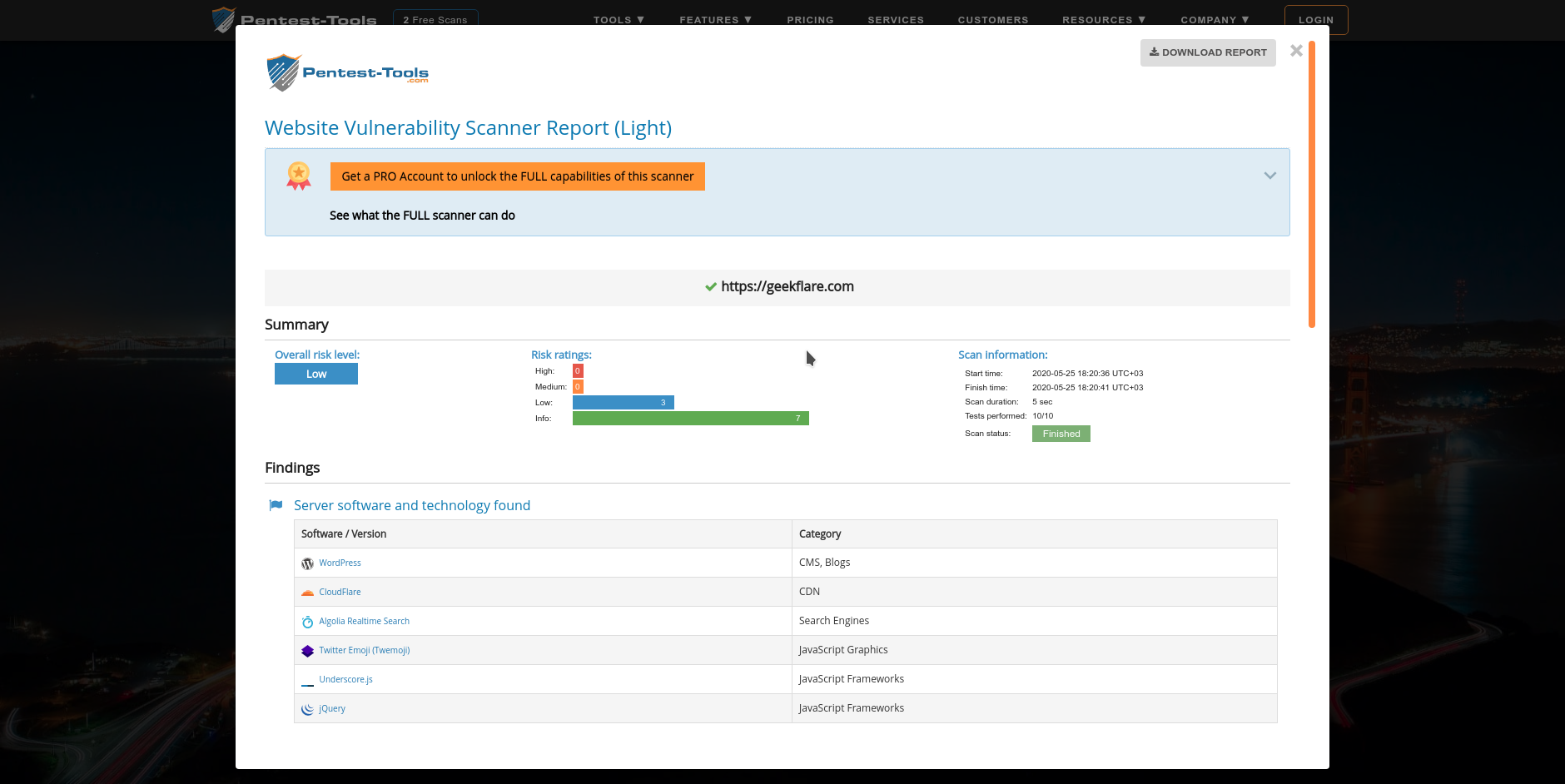
Reporting exhibits particulars of your web site and the assorted vulnerabilities (if any) and their severity ranges. Here’s a screenshot of the free ‘Gentle’ Scan report.
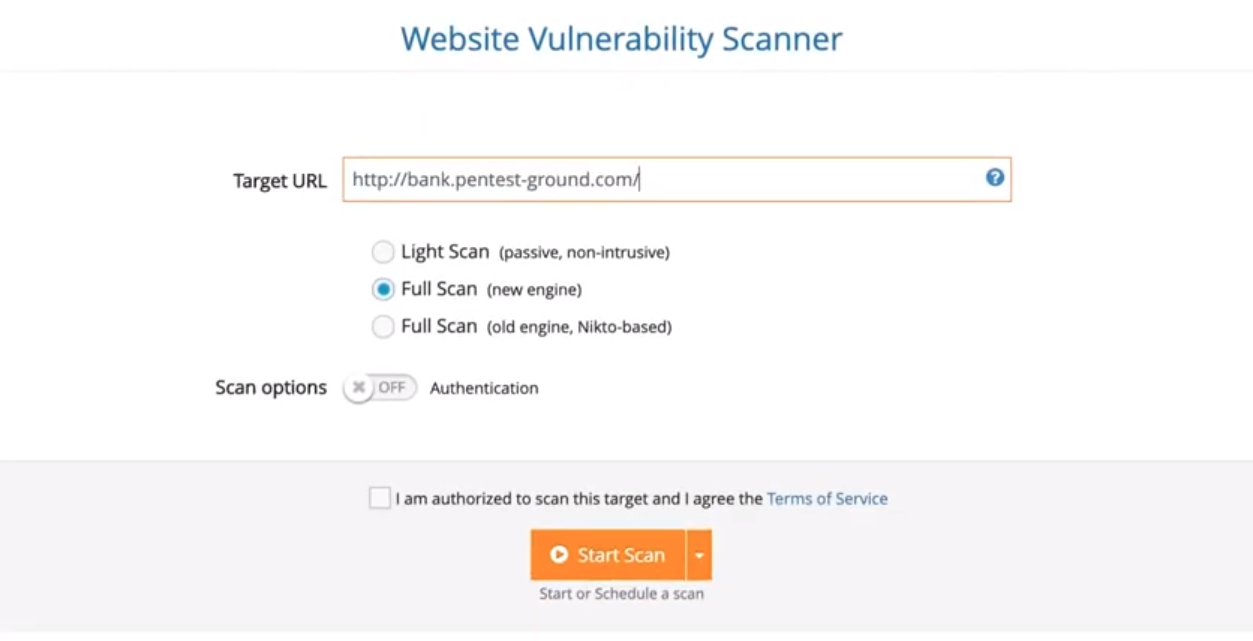
Within the PRO account you’ll be able to choose the scan mode you need to run.
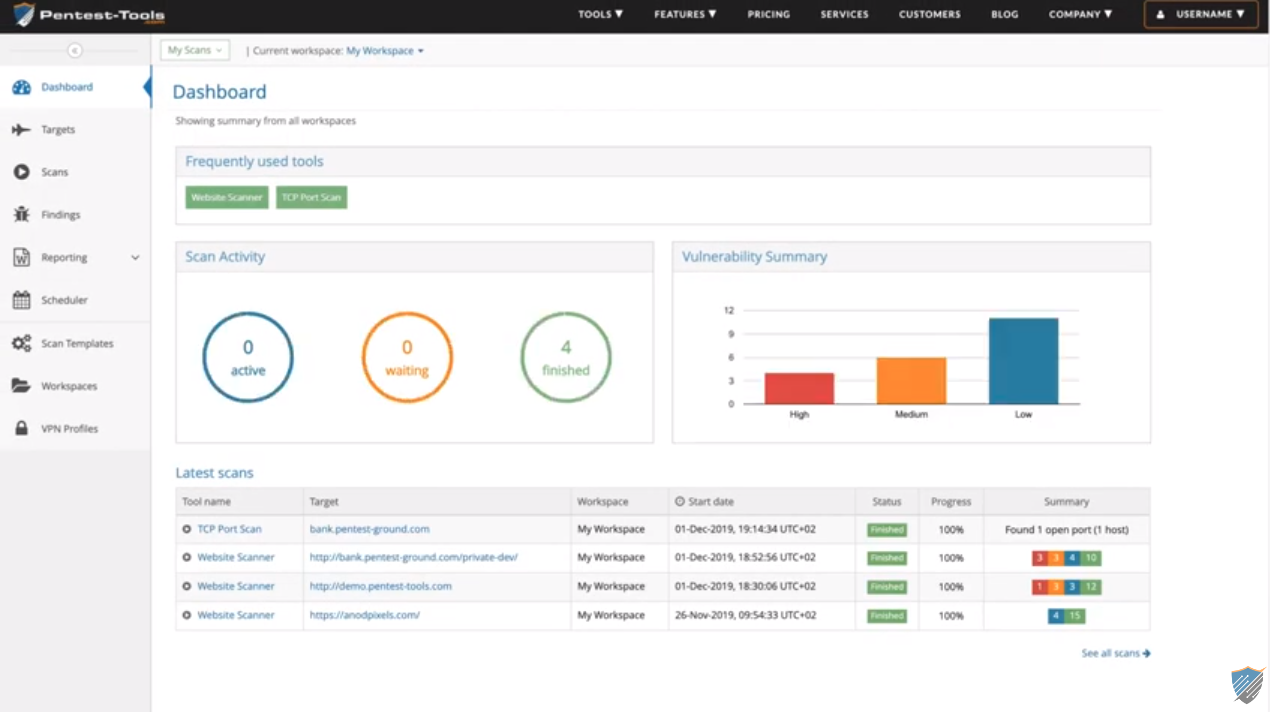
The dashboard is sort of intuitive and provides a great perception into all scans carried out and the completely different severity ranges.
Menace scanning can be scheduled. Likewise, the software has a reporting function that enables a tester to generate vulnerability reviews primarily based on the scans carried out.
Google SCC
Safety Command Middle (SCC) is a safety monitoring useful resource for Google Cloud.
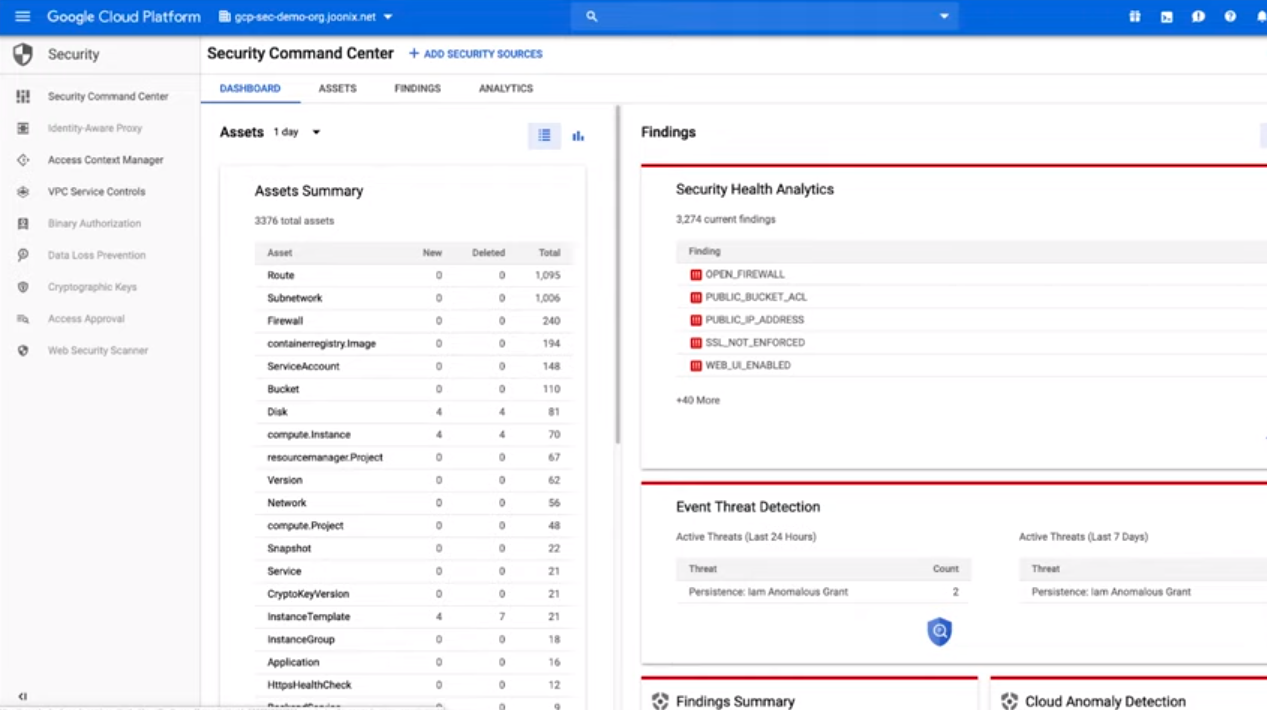
This offers Google Cloud customers the flexibility to arrange safety monitoring for his or her present tasks with out extra tooling.
SCC consists of a number of native safety assets. Included
- Cloud Anomaly Detection – Helpful for detecting malformed information packets generated by DDoS assaults.
- Cloud Safety Scanner – Helpful for detecting vulnerabilities corresponding to Cross-site Scripting (XSS), use of plaintext passwords, and outdated libraries in your app.
- Cloud DLP Knowledge Discovery – This exhibits a listing of storage buckets that include delicate and/or regulated information
- Forseti Cloud SCC Connector – Lets you develop your personal customized scanners and detectors
It additionally consists of companion options corresponding to CloudGuard, Chef Automate, Qualys Cloud Safety, Reblaze. All of which will be built-in into Cloud SCC.
Conclusion
Web site safety is a problem, however due to the instruments that make it straightforward to search out out what’s weak and mitigate on-line dangers. If you have not already, attempt the above resolution right now to guard your on-line enterprise.

