Scanning for cloud-based vulnerabilities is a necessary cybersecurity apply within the tech world.
Community operators apply fundamental safety measures when managing a community, however some hidden vulnerabilities might be tough to detect. Subsequently, a necessity arises for automated cloud safety scans.
Tech lovers are anticipated to have the ability to carry out fundamental scans for cloud surroundings vulnerabilities. This course of begins with attending to know cloud safety scanning instruments that may assist automate the detection of cloud vulnerabilities in a community.
There are a number of vulnerability scanners accessible at little to no value, however figuring out which of them are probably the most environment friendly is important.
What’s a vulnerability scanner?
A Vulnerability Scanner is a software program device designed to robotically look at purposes and networks for misconfiguration and safety flaws. These scan instruments carry out automated safety assessments to establish safety threats in a cloud community.
As well as, they’ve a continuously up to date database of vulnerabilities within the cloud, enabling them to carry out efficient safety scans.
Methods to choose the proper vulnerability scanner
For cloud safety, it’s important to make use of an appropriate vulnerability scanner. There are various vulnerability scanning instruments accessible on the Web, however not all of them supply what cloud safety testers search for in automated vulnerability scanners.
So, listed here are some components to look out for when choosing a vulnerability scanning device.
Choose a vulnerability scanner that:
- scans advanced internet purposes
- displays crucial programs and protection mechanisms
- recommends vulnerability remediation
- complies with rules and trade requirements
- has an intuitive dashboard that shows threat scores
It’s important to match and assess the instruments utilized in cloud vulnerability scanning and testing. They supply distinctive advantages that be sure that system networks and internet purposes run easily and are secure to be used in organizations and personal corporations.
Vulnerability scanning instruments present advantages for cloud monitoring and safety safety, together with:
- Scan programs and networks for safety vulnerabilities
- Performing ad-hoc safety assessments when required
- Monitoring, diagnosing and remediating vulnerabilities within the cloud
- Figuring out and resolving misconfigurations in networks
Listed here are the highest 5 cloud safety vulnerability scanners:
Intruder cloud safety
Intruder is a Cloud Vulnerability Scanning Device specifically designed for AWS, Azure and Google Cloud scanning. This can be a very proactive cloud-based vulnerability scanner that detects any form of cybersecurity weak point in digital infrastructures.
The intruder is very environment friendly because it finds cyber safety weaknesses in uncovered programs to forestall expensive knowledge breaches.
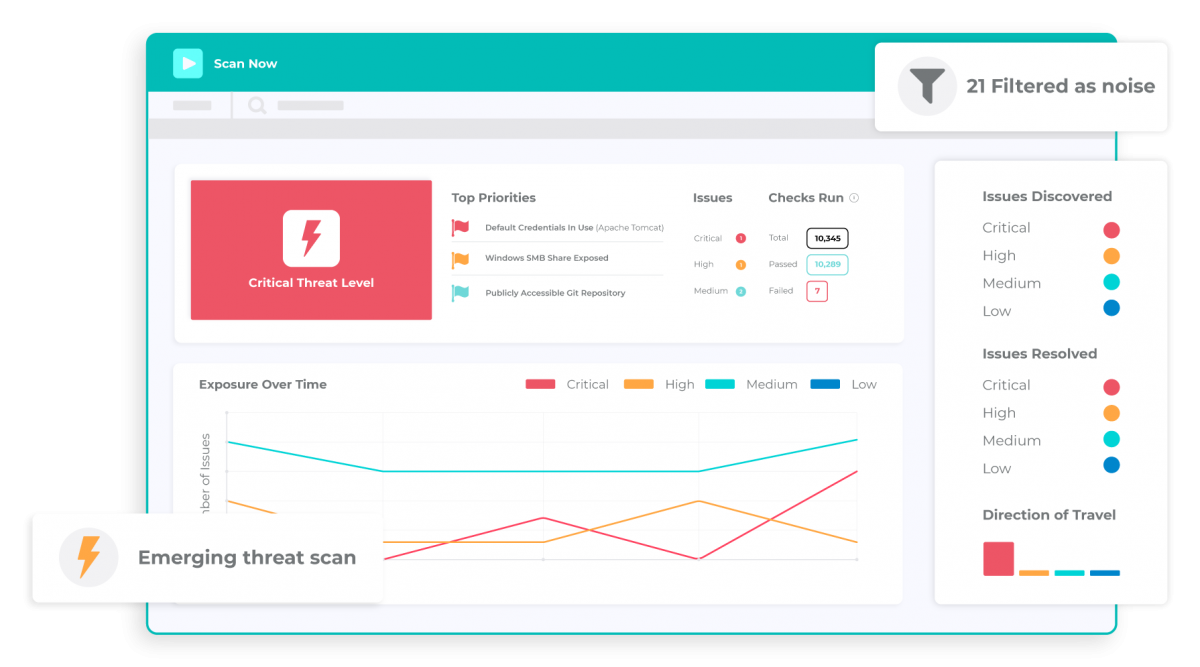
The energy of this vulnerability scanner for cloud-based programs lies in its perimeter scanning capabilities. It’s designed to find new vulnerabilities to make sure that the perimeter can’t be simply breached or hacked. As well as, it takes a streamlined method to bugs and threat detection.
Hackers will discover it very tough to penetrate a community if an Intruder Cloud Safety Scanner is used. It is going to detect all weaknesses in a cloud community to forestall hackers from discovering these weaknesses.
The intruder additionally presents a novel risk interpretation system, making the method of figuring out and managing vulnerabilities a straightforward nut to crack. That is extremely really useful.
Aqua Cloud safety
Aqua Cloud Safety is a vulnerability scanner designed to scan, monitor and remediate configuration points in public cloud accounts in line with greatest practices and compliance requirements on cloud-based platforms reminiscent of AWS, Azure, Oracle Cloud and Google Cloud.
It supplies a whole cloud-native software safety platform.
This is without doubt one of the greatest vulnerability scanners used for cloud native safety in organizations. Community safety operators use this vulnerability scanner for vulnerability scanning, cloud safety administration, dynamic risk evaluation, Kubernetes safety, serverless safety, container safety, digital machine safety, and cloud-based platform integrations.
Aqua Cloud Safety Scanner supplies customers with a number of CSPM editions, together with SaaS and Open-Supply Safety. It helps safe the configuration of particular person public cloud companies with CloudSploit and supplies complete options for multi-cloud safety posture administration.
Errors are virtually unavoidable inside a fancy cloud surroundings, and if not correctly monitored can result in misconfigurations that may escalate into severe safety vulnerabilities.
That’s the reason Aqua Cloud Safety has devised an built-in method to forestall knowledge leaks.
Qualys Cloud Safety
Qualys Cloud Safety is an excellent cloud computing platform designed to establish, classify and monitor vulnerabilities within the cloud whereas guaranteeing compliance with inside and exterior insurance policies.
This vulnerability scanner prioritizes scanning and restoration by robotically discovering and eradicating malware infections on internet purposes and system web sites.
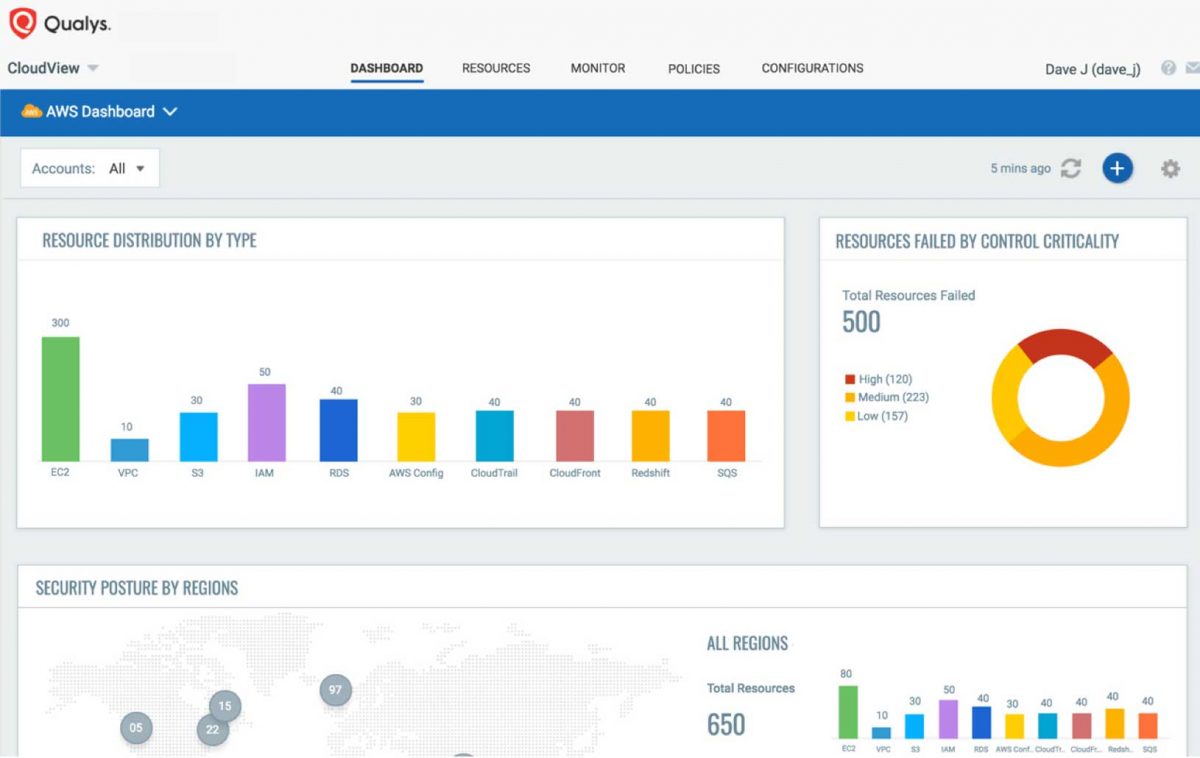
Qualys presents public cloud integrations that give customers full visibility into public cloud deployments.
Most public cloud platforms function on a “shared safety duty” mannequin, that means that customers are anticipated to guard their workloads within the cloud. This generally is a trouble if finished manually, so most customers will choose to make use of vulnerability scanners.
Qualys supplies full visibility with end-to-end IT safety and compliance throughout hybrid IT and AWS deployments. It constantly displays and evaluations AWS property and sources for safety vulnerabilities, misconfigurations, and non-standard deployments.
It’s the good vulnerability scanner for scanning cloud environments and detecting vulnerabilities in advanced inside networks.
It has a central interface with a single glass panel and a CloudView dashboard that permits customers to view monitored internet apps and all AWS property throughout a number of accounts by way of a centralized consumer interface.
Rapid7 Perception cloud safety
Rapid7 InsightCloudSec platform is without doubt one of the greatest cloud safety vulnerability scanners. This vulnerability scanner is designed to maintain cloud companies secure.
It options an perception platform that gives internet software safety, vulnerability administration, risk administration, bug detection and response, together with cloud safety skilled administration and consulting companies.
Rapid7 InsightCloudSec’s safe cloud companies assist transfer the enterprise ahead in the very best approach. It additionally permits customers to drive innovation by way of steady safety and compliance.
This cloud safety platform presents excellent advantages, together with cloud workload safety, safety posture administration, and identification and entry administration.
Rapid7 is a totally built-in cloud native platform that provides options reminiscent of; threat evaluation and auditing, unified visibility and monitoring, automation and real-time remediation, cloud identification administration and entry management, risk safety, extensible platform and infrastructure reminiscent of code safety, Kubernetes safety rails, and posture administration. The checklist is limitless.
CrowdStrike cloud safety
CrowdStrike Cloud Safety is a high vulnerability scanner designed for cloud safety companies. It stops cloud breaches with unified cloud safety administration and breach prevention for multi-cloud and hybrid environments on a single platform.
This platform has modified the way in which cloud safety automation is completed for internet purposes and networks.
CrowdStrike supplies full-stack cloud-native safety, defending workloads, hosts, and containers. It permits DevOps to detect and repair issues earlier than they negatively have an effect on a system.
As well as, safety groups can use this cloud safety scanner to defend in opposition to cloud breaches utilizing cloud-scale knowledge and analytics.
This vulnerability scanner reduces workload for cloud safety and DevOps groups by robotically optimizing cloud deployments with unified safety.
Options embrace automated cloud vulnerability detection, risk detection and prevention, and steady runtime safety, together with EDR for cloud workloads and containers.
As well as, it permits internet builders to construct and run internet purposes figuring out that they’re absolutely protected in opposition to an information breach. Because of this, when threats are hunted down and eradicated, cloud purposes will run easily, quicker and with utmost effectivity.
Conclusion
Vulnerability scanners are important for cloud safety as a result of they’ll simply detect system weaknesses and prioritize efficient options. This may assist scale back the workload for safety groups in organizations. Every of the vulnerability scanners mentioned on this information presents wonderful advantages.
These vulnerability scanners permit customers to carry out scans by logging into the web site as licensed customers. When this occurs, the weak spots within the programs are robotically monitored and scanned.
It additionally identifies any form of community packet configuration anomalies to forestall hackers from abusing system applications. Automated vulnerability evaluation is crucial for cloud safety companies.
Thus, vulnerability scanners can detect 1000’s of vulnerabilities and establish the precise threat of those vulnerabilities by validating them.
As soon as these are reached, they prioritize remediation primarily based on the chance degree of those vulnerabilities. All 5 vulnerability scanners reviewed are examined and trusted, so customers haven’t got to fret about any form of flaws.
Lastly, it’s important to notice that vulnerability scanning is completely different from penetration testing.
Vulnerability scanners uncover vulnerabilities and classify them primarily based on their risk degree. They correlate them with software program, units, and working programs related to a cloud-based community. Misconfigurations are additionally detected on the community.
Penetration testing, nevertheless, makes use of a unique methodology, which makes use of the detected vulnerabilities on a cloud-based community. Thus, penetration assessments are carried out instantly after the vulnerability scan has been carried out.
Each cloud safety processes are comparable and centered on guaranteeing that internet purposes and networks are safe and protected against threats.

