AWS offers safety companies and infrastructure, whereas clients are chargeable for configuring and sustaining these companies over time.
As corporations transfer their information and operations to the cloud, safety is a crucial issue to think about. Amazon Net Companies (AWS) is a broadly used cloud service supplier and Elastic Compute Cloud (EC2) is the most well-liked service. To make sure that your information, purposes and infrastructure stay safe, it’s important to safe your AWS EC2 occasion.
To assist defend your information, AWS presents a shared duty mannequin for safety. This mannequin helps clients perceive their safety obligations by dividing them into two classes: AWS duty and buyer duty.

The AWS Shared Duty Mannequin helps make clear the excellence between cloud safety and cloud safety. The mannequin states that AWS is chargeable for guaranteeing the safety of the underlying infrastructure that powers all cloud companies.
On the identical time, clients are chargeable for defending their content material and purposes operating on the AWS surroundings. This contains monitoring and defending information, configuring firewall guidelines, securing entry controls, and extra.
By following these greatest practices, you’ll be able to safe your AWS EC2 sources and guarantee they continue to be safe and compliant with {industry} requirements.
Handle person entry to EC2 occasion with IAM
Identification and entry administration (IAM) roles are a vital a part of AWS EC2 safety. IAM roles present a safe approach to grant entry to AWS companies. It means that you can securely entitle a person or software whereas controlling entry to sources inside your AWS surroundings.
In AWS, IAM roles enable purposes to make API requests from cases with out having to handle credentials; as an alternative of managing AWS credentials, you’ll be able to assign permission to make API requests utilizing IAM roles as seen beneath.
- Create an IAM position
- Specify which accounts or AWS companies can fill the position
- Set which API actions and sources the applying can entry when assuming the position
- Embrace the position when launching an occasion, or affiliate the position with an current occasion
- Have the applying retrieve a set of momentary credentials and use it to make requests to AWS
Permission for the next API operations is required to allow an IAM person to create an occasion subsequent to an IAM position or hyperlink or modify an IAM position for an current occasion.
{
"Model": "2012-10-17",
"Assertion": [
{
"Effect": "Allow",
"Action": [
"ec2:RunInstances",
"ec2:AssociateIamInstanceProfile",
"ec2:ReplaceIamInstanceProfileAssociation"
],
"Useful resource": "*"
},
{
"Impact": "Permit",
"Motion": "iam:PassRole",
"Useful resource": "arn:aws:iam::123456789012:position/DevTeam*"
}
]
}By creating IAM roles and assigning them to EC2 cases, you’ll be able to make sure that solely customers with the suitable permissions can entry delicate information and sources.
Limit entry to AWS EC2 cases with community entry controls
Top-of-the-line methods to make sure the safety of your AWS EC2 cases is to limit community entry. It’s best to solely enable entry from particular trusted IP addresses and ports while you configure community entry, for instance.
Arrange a community entry management checklist or safety group guidelines in your Digital Non-public Cloud (VPC) to just accept or reject particular IP addresses in your EC2 cases. Safety teams and community entry controls are efficient methods to limit entry to your AWS EC2 cases.
Safety teams will let you specify which IP addresses and ports are allowed to entry your EC2 occasion. Community entry controls can prohibit entry to particular companies and ports inside your occasion.

Carry out the next steps to arrange community ACL.
- Launch the Amazon VPC console
- Select community ACLs within the navigation pane
- Choose Create community ACL
- Identify your community ACL within the Create Community ACL dialog and select your VPC’s ID from the VPC checklist.
- Choose Sure, create
For every safety group, you’ll be able to configure guidelines to limit inbound or outbound site visitors. You may specify IP addresses, ports, protocols, and instructions (inbound or outbound). Carry out the next steps to create a safety group.
- Launch the Amazon VPC console
- Choose safety teams within the navigation pane
- Choose Create a safety group
- Kind a reputation and outline for the safety group (this course of can’t be undone)
- At VPC, select the VPC
- You may add safety group guidelines now or later
- You may add tags now or later. So as to add a tag, choose add a brand new tag and enter the tag key and worth
- Choose Create a safety group
When establishing safety teams, all the time be as restrictive as doable. Limit entry to solely needed ports and IP addresses, and ensure all different ports are blocked. Moreover, you should definitely overview safety group guidelines repeatedly to make sure they continue to be efficient.
Encryption of Amazon Machine photographs
Amazon Machine Photos (AMI) are digital machines that present the data wanted to launch an occasion. To guard your information saved in an occasion, it’s important to encrypt the AMI you employ.
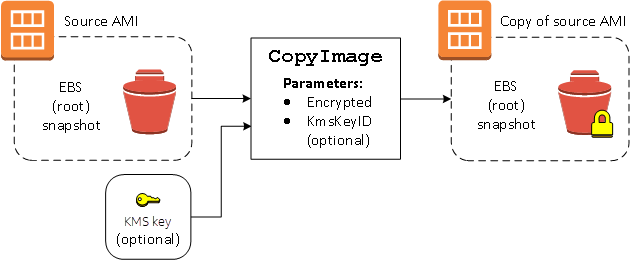
With AWS AMI encryption, clients can keep compliant with industry-standard encryption comparable to PCI-DSS, HIPAA, GDPR, APRA, MAS, and NIST4. AMI encryption keys use the AES-256 algorithm, which is thought for offering safe cryptographic hash capabilities for encryption at relaxation.
It ensures that the information saved within the AMI is protected against potential attackers and unauthorized entry. To guard your information saved in an occasion, AWS Key Administration Service (KMS) helps you handle encryption keys and use them to encrypt information saved in your AWS sources, comparable to EC2 cases.
KMS additionally means that you can handle entry management, audit logging, and key rotation to safe your information and provide help to meet your compliance necessities.
Use AWS CloudTrail to trace person exercise
CloudTrail is a service that permits customers to observe and audit AWS actions. With CloudTrail, you’ll be able to observe who made adjustments to your AWS sources and infrastructure. CloudTrail means that you can log all API calls in your account. It displays the next:
- Create, delete, and modify operations on sources comparable to EC2 cases, S3 buckets, VPCs, and extra
- Invocation of Lambda capabilities
- Different actions are taken within the AWS Administration Console
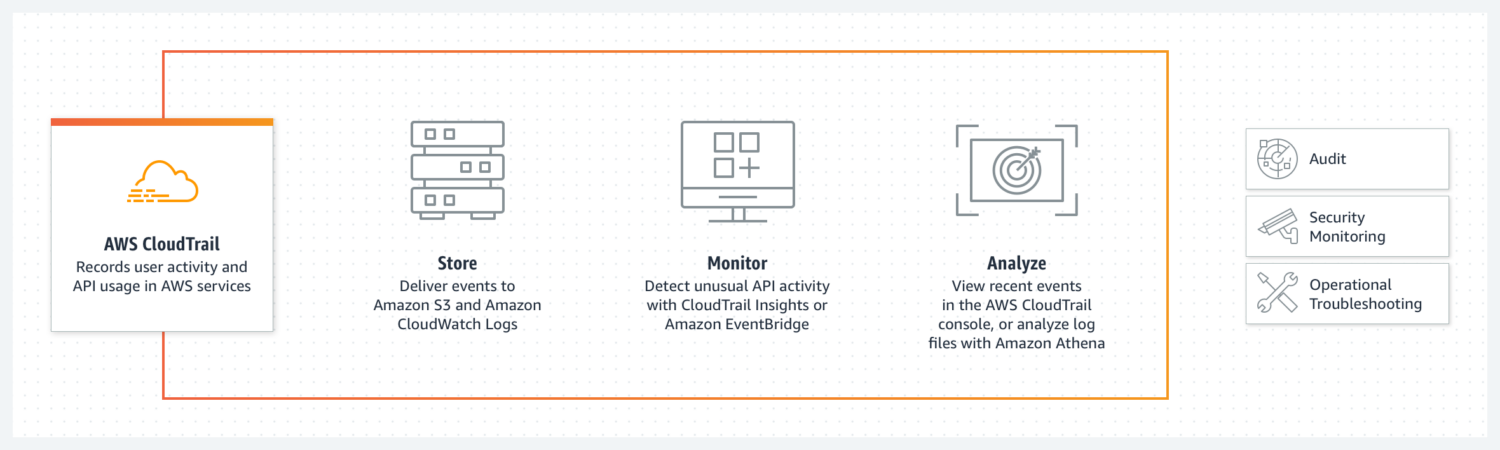
CloudTrail information a report of each motion taken within the type of an occasion. This occasion is written to a CloudTrail log file, which may then be used for additional evaluation and auditing. Enabling CloudTrail is a vital safety greatest observe for AWS EC2 environments as a result of it offers an audit path of all actions related to the surroundings.
To allow CloudTrail for an ongoing view of occasions in your AWS account, navigate to the CloudTrail console, choose ‘Create Path’ and configure the settings. After enabling CloudTrail logging, it’s important to overview the logs repeatedly and examine for unauthorized entry or suspicious exercise.
It’s also possible to use CloudTrail to detect anomalous conduct in your surroundings, comparable to sudden adjustments or suspicious exercise. By taking the time to correctly configure CloudTrail logging in your AWS EC2 surroundings, you’ll be able to make sure that your surroundings is safe and that each one exercise is monitored.
Verify the safety of the EC2 occasion working system
It is very important make sure the safety of the working system operating on the AWS EC2 occasion. You are able to do this by configuring the firewall, putting in and updating antivirus software program, and patching vulnerabilities.
- Firewalls must be configured to permit solely needed ports and protocols
- Antivirus software program must be put in and up to date repeatedly to stop malicious applications from infiltrating the system
- Patch administration must be used to make sure that all recognized vulnerabilities within the system are mounted
- Monitoring must be carried out to detect suspicious exercise. This may increasingly embody utilizing instruments comparable to LogRhythm to observe person exercise, entry, and adjustments to recordsdata and folders.
By implementing these measures, you’ll be able to make sure that your AWS EC2 occasion stays safe.
Allow Amazon CloudWatch logs
Amazon CloudWatch Logs are a precious software for monitoring, storing, and monitoring log information from purposes, working methods, and different sources operating on AWS. With CloudWatch Logs you’ll be able to simply discover, analyze and set alarms to observe your system’s exercise.
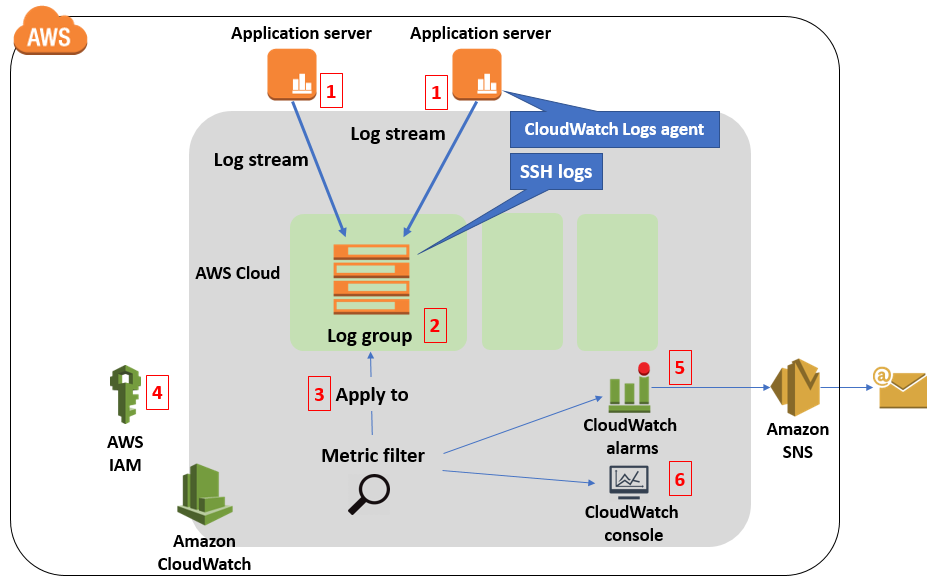
The advantages of CloudWatch Logs embody higher perception into system efficiency and the power to observe for potential safety vulnerabilities.
The CloudWatch agent might be downloaded and put in through the command line or through the Methods Supervisor Agent (SSM). It may be used to gather statistics and log recordsdata from Amazon EC2 cases and native servers.
When configuring the CloudWatch agent, that you must determine what varieties of logs must be collected and saved in CloudWatch Logs. You should additionally configure IAM roles for the CloudWatch agent in order that it has adequate privileges to entry and retailer the related information in CloudWatch Logs.
Conclusion
Knowledge breaches can occur at any time and have critical monetary and reputational penalties for corporations. Due to this fact, it’s important to take steps to make sure the safety of your AWS EC2 surroundings.
By proactively following these greatest practices and implementing efficient safety measures, corporations can scale back the chance of an information breach. As well as, educating customers concerning the significance of fine safety and good cyber hygiene practices will make sure that everybody in your group understands their position in protecting methods protected.
It’s also possible to discover among the greatest AWS monitoring instruments.

