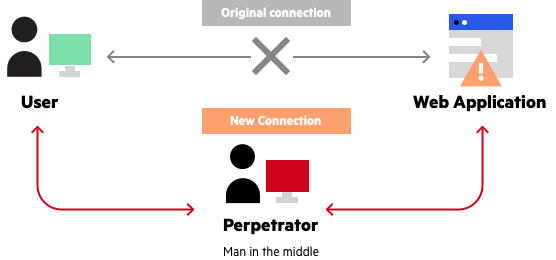
A person-in-the-middle (MITM) assault is when a foul actor interrupts an present community dialog or information switch. The attacker is in the course of the transmission path after which pretends or acts as a reliable participant within the dialog.
In follow, the attackers place themselves between incoming requests and outgoing responses. As a consumer, you’ll proceed to imagine that you’re speaking on to the reliable vacation spot server or internet software, similar to Fb, Twitter, on-line financial institution and others. In actuality, although, you are sending requests to the man-in-the-middle, who then talks to your financial institution or app in your behalf.
-
Picture by Imperva
As such, the person within the center will see every part together with all of your requests and responses you get from the vacation spot or goal server. Along with watching all conversations, the person within the center can change your requests and responses, steal your credentials, redirect you to a server they management, or commit different cyber crimes.
Typically, the attacker can intercept the communication stream or information of each events within the dialog. The attacker can then modify the knowledge or ship malicious hyperlinks or feedback to each reliable contributors. Typically, this will go unnoticed for a while, till later after a number of injury.
Frequent man-in-the-middle assault strategies
Sniff bundle:- The attacker makes use of numerous instruments to examine the community packets at a low stage. Sniffing permits attackers to see information packets they do not have entry to.
bundle injection:- the place attackers inject malicious packets into the info communication channels. Earlier than injecting, the criminals will sniff first to find out how and when to ship the malicious packets. After injection, the dangerous packets combine with the legitimate packets within the communication stream.
Session hijack: In most internet purposes, the login course of creates a short lived session token in order that the consumer doesn’t should sort within the password for each web page or future request. Sadly, an attacker utilizing numerous sniffing instruments can determine and use the session token, which they’ll now use to cross requests as in the event that they had been the reliable consumer.
SSL stripping: Attackers can use the SSL disable approach to intercept the reliable packets, modify the HTTPS based mostly requests and redirect them to the insecure HTTP equal vacation spot. Consequently, the host will begin making an unencrypted request to the server, exposing delicate information as plain textual content that’s straightforward to steal.
Penalties of MITM assaults
MITM assaults are harmful for any group and might result in monetary and reputational injury.
Often, the criminals can receive and misuse the group’s delicate and personal data. For instance, they’ll steal login credentials similar to usernames and passwords, bank card data and use them to switch cash or make unauthorized purchases. They’ll additionally use stolen credentials to put in malware or steal different delicate data, which they’ll use to blackmail the corporate.
For that reason, it’s essential to guard the customers and digital programs to attenuate the dangers of MITM assaults.
MITM assault instruments for safety groups
Along with utilizing dependable safety options and practices, it’s best to use the required instruments to watch your programs and determine vulnerabilities that attackers can exploit. That will help you make the correct alternative, listed below are some HTTP MITM assault instruments for safety researchers.
Hetty
Hetty is a quick open-source HTTP toolkit with highly effective options to assist safety researchers, groups and the bug bounty group. The light-weight device with an embedded Subsequent.js internet interface contains an HTTP man within the center proxy.
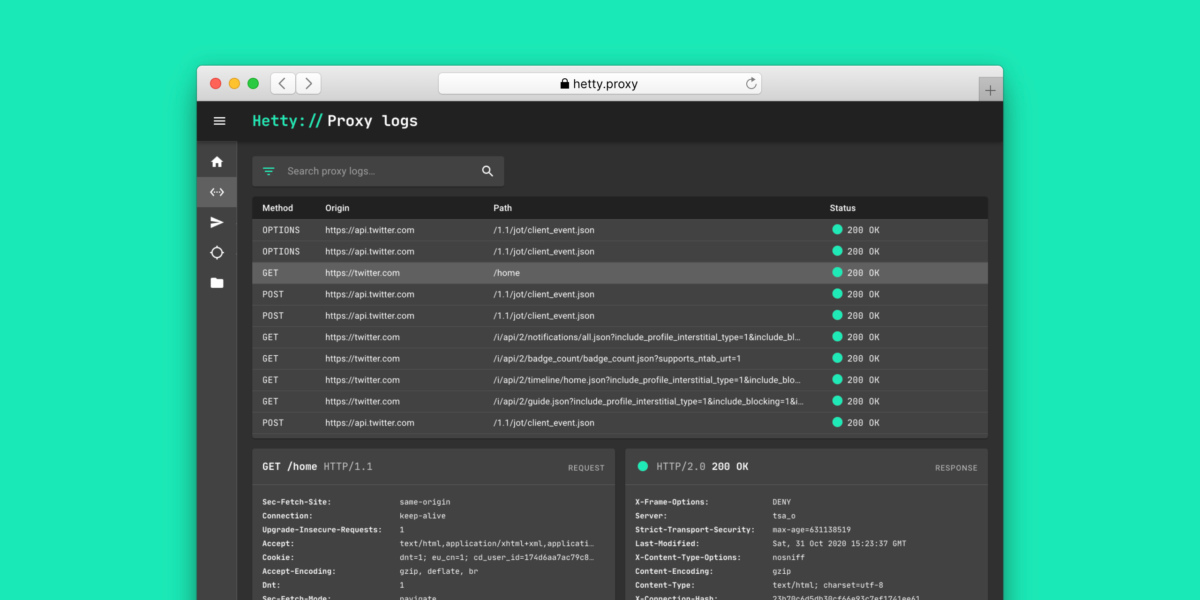
Most necessary options
- Means that you can search in full textual content
- It has a sender module that permits you to manually ship HTTP requests based mostly on the off requests from the proxy log or by creating them from scratch.
- An attacker module that permits you to routinely ship HTTP requests
- Straightforward set up and user-friendly interface
- Ship the HTTP requests manually by ranging from scratch, composing the request, or just copying from the proxy log.
Higher cap
Bettercap is a complete and scalable community reconnaissance and assault device.
The straightforward-to-use resolution supplies the reverse engineers, safety consultants and crimson groups with all of the options to check or assault Wi-Fi, IP4, IP6 networks, Bluetooth Low Vitality (BLE) gadgets and wi-fi HID gadgets. As well as, the device has community monitoring capabilities and different options like creating pretend entry factors, password sniffing, DNS spoofer, handshake seize, and so forth.
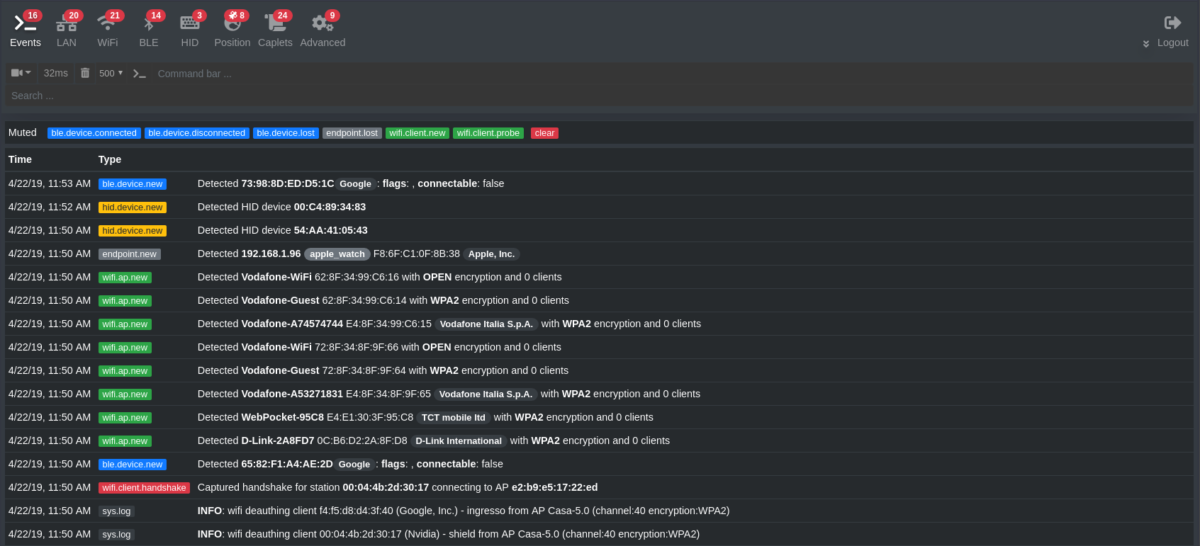
Most necessary options
- A strong built-in community sniffer for figuring out authentication credentials and gathering credentials
- highly effective, expandable
- Actively and passively examine and check IP community hosts for potential MITM vulnerabilities.
- Straightforward to make use of and interactive web-based UI that permits you to carry out all kinds of MITM assaults, sniff credentials, monitor HTTP and HTTP site visitors, and so forth.
- Extract all the info it collects, similar to POP, IMAP, SMTP, and FTP credentials, URLs visited and HTTPS hosts, HTTP cookies, information posted over HTTP, and extra. It then presents it in an exterior file.
- Manipulate or change TCP, HTTP, and HTTPS site visitors in actual time.
proxy.py
Proxy.py is a light-weight open-source WebSockets, HTTP, HTTPS and HTTP2 proxy server. Out there in a single python file, the fast device permits researchers to examine internet site visitors, together with TLS-encrypted apps, whereas consuming minimal assets.

Most necessary options
- It’s a quick and scalable device that may deal with tens of hundreds of connections per second.
- Programmable options similar to built-in internet server, proxy and HTTP routing customization, and so forth
- It has a light-weight design that makes use of 5-20 MB of RAM. It additionally depends on the usual Python libraries and requires no exterior dependencies.
- An actual-time customizable dashboard which you can lengthen with plugins. It additionally provides you the flexibility to examine, monitor, configure, and management the proxy.py at runtime.
- The safe device makes use of TLS to offer end-to-end encryption between the proxy.py and the shopper.
Mitmproxy
The mitmproxy is an easy-to-use, open-source HTTPS proxy resolution.
Total, the easy-to-install device works as an SSL man-in-the-middle HTTP proxy and has a console interface that permits you to examine and modify the site visitors move on the fly. You should utilize the command line based mostly device as an HTTP or HTTPS proxy to seize all community site visitors, see what customers are asking for and replay them. Often mitmproxy refers to a set of three highly effective instruments; the mitmproxy (console interface), mitmweb (web-based interface), and mitmdump (command line model).
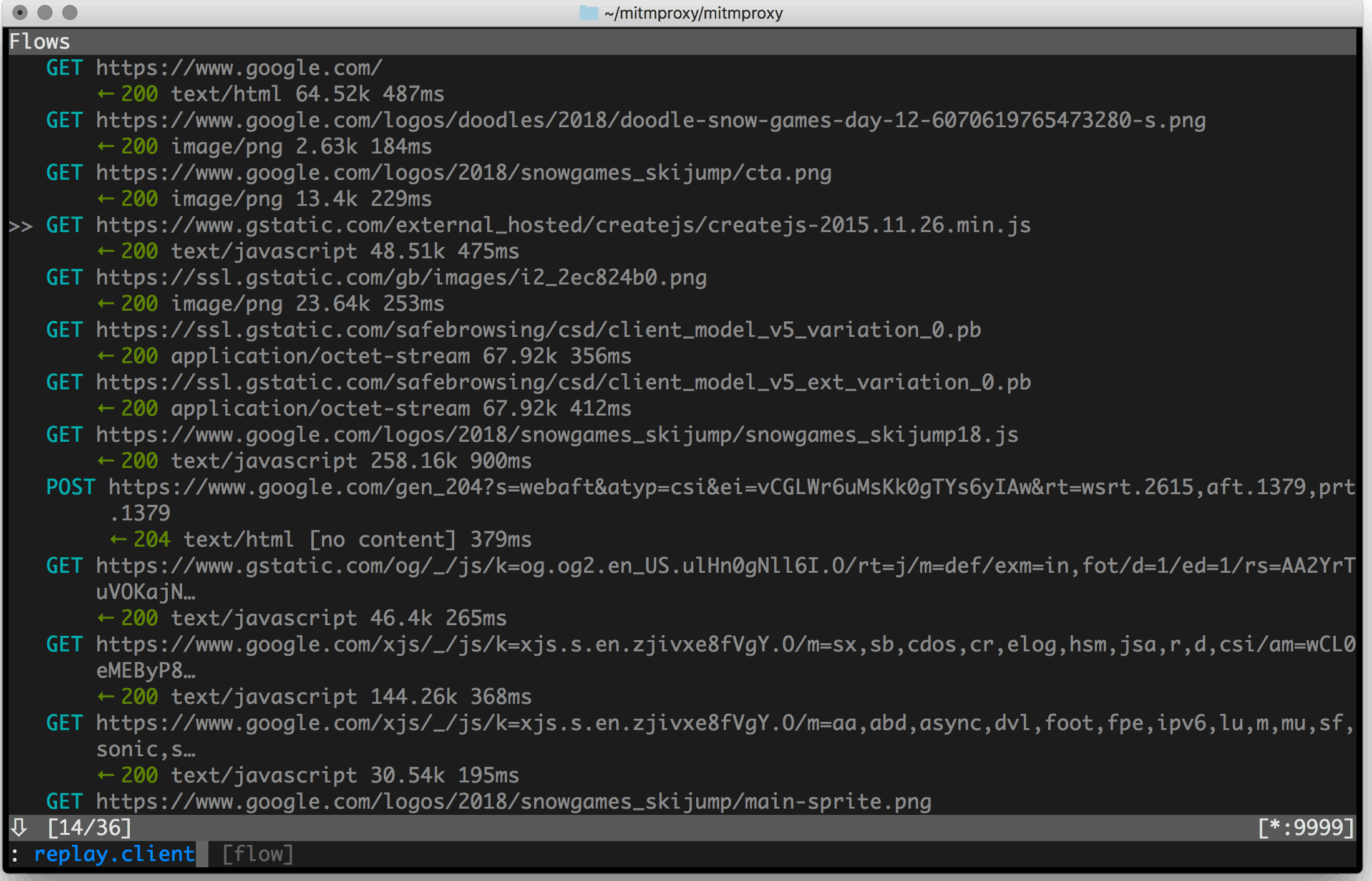
Most necessary options
- Interactive and dependable device for analyzing and modifying HTTP site visitors
- A versatile, secure, dependable, straightforward to put in and use device
- It permits you to intercept and modify the HTTP and HTTPS requests and responses immediately
- File and save the shopper and server facet HTTP conversations, replay them and analyze them sooner or later
- Generate the SSL/TLS certificates to intercept them immediately
- Reverse proxy capabilities help you ahead community site visitors to a different server.
Farmers
Burp is an automatic and scalable vulnerability scanning device. The device is an effective alternative for a lot of safety professionals. Total, it permits the researchers to check internet purposes and determine vulnerabilities that criminals can exploit and launch MITM assaults.
It makes use of a user-driven workflow to offer a direct view of the goal software and the way it works. Burp acts as an internet proxy server and is the man-in-the-middle between the online browser and the vacation spot servers. This lets you intercept, analyze and modify the query and reply site visitors.
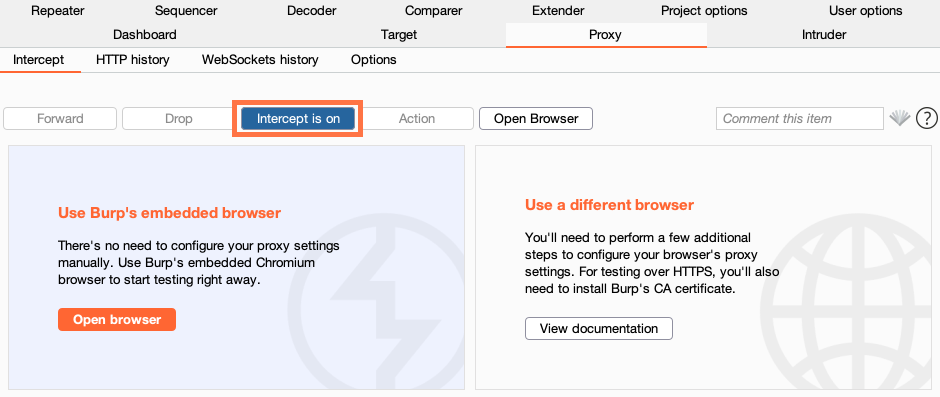
Most necessary options
- Intercept and examine the uncooked community site visitors in each instructions between the online browser and the server
- Breaks the TLS connection in HTTPS site visitors between the browser and the goal server, permitting the attacker to view and modify encrypted information
- Alternative of utilizing the Burps built-in browser or the exterior default internet browser
- Automated, quick and scalable vulnerability scanning resolution. It permits you to scan and check internet purposes quicker and extra effectively, figuring out a variety of vulnerabilities
- Show particular person intercepted HTTP requests and responses
- Manually assessment the intercepted site visitors to know the small print of an assault.
Ettercap
Ettercap is an open-source community site visitors analyzer and interceptor.
The great MITM assault device permits researchers to parse and analyze all kinds of community protocols and hosts. It will probably additionally register the community packets on a LAN and different environments. Moreover, the multifunctional community site visitors analyzer can detect and cease man-in-the-middle assaults.
Most necessary options
- Intercept community site visitors and seize credentials similar to passwords. It will probably additionally decrypt encrypted information and extract credentials similar to usernames and passwords.
- Appropriate for deep packet sniffing, testing, community site visitors monitoring and real-time content material filtering.
- Helps energetic and passive eavesdropping, parsing, and evaluation of community protocols, together with these with encryption
- Analyze a community topology and decide the working programs put in.
- Straightforward to make use of graphical consumer interface with interactive and non-interactive GUI management choices
- makes use of analytics strategies similar to ARP interception, IP and MAC filtering, and others to intercept and analyze site visitors
Stop MITM assaults
Figuring out MITM assaults is not very straightforward as a result of it occurs out of attain of customers, and it is laborious to detect as a result of attackers make every part look regular. Nevertheless, there are a number of safety practices organizations can use to forestall man-in-the-middle assaults. These embrace;
- Safe web connections at work or dwelling networks, for instance by utilizing efficient safety options and instruments in your servers and computer systems, dependable authentication options
- Implement robust WEP/WAP encryption for the entry factors
- Guaranteeing that every one web sites you go to are safe and have HTTPS within the URL.
- Don’t click on on suspicious emails, messages and hyperlinks
- Implement HTTPS and disable insecure TLS/SSL protocols.
- Use Digital Personal Networks every time doable.
- Use the above instruments and different HTTP options to determine and tackle any man-in-the-middle vulnerabilities that attackers can exploit.

