Infrastructure-as-Code (IaC) is revolutionizing fashionable IT infrastructure, making it safer, cost-effective and performance-efficient.
Consequently, the adoption of IaC expertise is quickly growing within the industrial area. Organizations have begun to broaden their capabilities for provisioning and deploying cloud environments. It options applied sciences similar to Terraform, Azure Useful resource Supervisor templates, AWS Cloud Formation templates, OpenFaaS YML, and extra.
Beforehand, organising an infrastructure required stacking tangible servers, information facilities to accommodate {hardware}, configuring community connections, and so forth. However now all of those are doable with traits like cloud computing, the place the processes take much less time.
IaC is among the key parts of this rising pattern, and let’s perceive what it is all about.
perceive IC
Infrastructure-as-Service (IaC) makes use of high-performance descriptive coding to automate IT infrastructure provisioning. With this automation, builders not must manually handle and run servers, database connections, working methods, storage, and plenty of different components whereas creating, deploying, or testing software program.
Infrastructure automation has change into important for enterprises as we speak, enabling them to deploy numerous purposes fairly ceaselessly.
Motive: Accelerating enterprise processes, lowering threat, controlling prices, tightening safety and responding successfully to new aggressive threats. In truth, IaC is a must have DevOps follow to advertise fast utility lifecycle by empowering the groups to construct and function software program infrastructure successfully.
Nevertheless, as a result of IaC is so sturdy, you’ve an enormous duty in managing safety dangers.
In response to TechRepublic, DivvyCloud researchers discovered that information breaches because of cloud misconfiguration price $5 trillion in 2018-2019.
Due to this fact, not following the most effective practices can result in safety holes, similar to compromised cloud environments, which may result in points similar to:
Community exposures
Insecure IaC practices could be the premise for on-line assaults. Examples of some IaC misconfigurations are publicly accessible SSH, cloud storage providers, web accessible databases, configuring some open safety teams and extra.
Drifting configuration
Regardless that your builders observe IaC finest practices, sure emergency conditions can pressure your operations workforce to straight change the configuration within the manufacturing setting. However the infrastructure ought to by no means be modified after you deploy it as this breaks the immutability of the cloud infrastructure.
Unauthorized privileged escalations
Organizations use IaC to run cloud environments which will embrace software program containers, microservices, and Kubernetes. Builders use sure privileged accounts to run cloud purposes and different software program, which carries privileged escalation dangers.
Compliance violations
Unlabeled assets created with IaC can result in ghost assets, inflicting difficulties in visualizing, detecting, and attaining publicity inside the true cloud setting. Consequently, cloud perspective anomalies can happen that may go undetected for prolonged intervals of time and result in compliance violations.
So what is the resolution?
Properly, you could be sure that no stone is left unturned when adopting IaC in order that it would not open the door for potential threats. Develop IaC finest practices to mitigate these points and take full benefit of the expertise.
One strategy to obtain that is to make use of an environment friendly safety scanner to search out and repair cloud misconfigurations and different safety vulnerabilities.
Why scan IaC for vulnerabilities?
A scanner follows an automatic course of to scan numerous components of a tool, utility, or community for potential safety flaws. To verify all the things goes easily, you must run scans usually.
Benefits:
Elevated safety
A good scan instrument makes use of the newest safety practices to mitigate, tackle, and resolve on-line threats. On this method, your organization’s and clients’ information could be protected.
Popularity security
When a corporation’s delicate information is stolen and falls into the fallacious fingers, it will probably trigger huge reputational injury.
Compliance Monitoring
All your organizational practices have to be lined by compliance to maintain what you are promoting operating. Safety holes can jeopardize this and put an organization in dire straits.
So, with out additional ado, let’s check out a number of the finest scanning instruments to examine IaC for vulnerabilities.
Checks
Say no to cloud misconfigurations by utilizing Checkov.
It’s meant for analyzing static codes for IaC. To detect misconfigurations within the cloud, it scans your cloud infrastructure, which is managed in Kubernetes, Terraform and Cloudformation.
Checkov is a Python primarily based software program. Due to this fact, writing, managing, coding and versioning change into simpler. Checkov’s built-in insurance policies embrace compliance and safety finest practices for Google Cloud, Azure, and AWS.
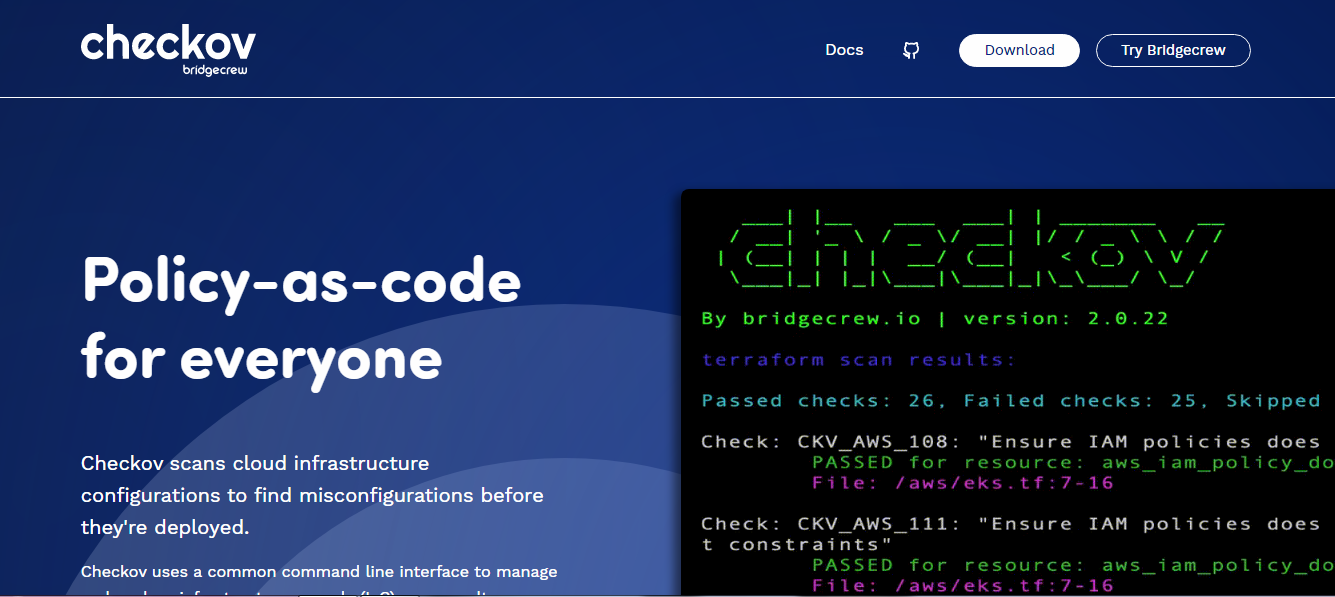
Verify your IaC on Checkov and get output in a wide range of codecs together with JSON, JUnit XML or CLI. It may possibly deal with variables successfully by constructing a graph that reveals the dynamic code dependency.
As well as, it facilitates inline suppression for all accepted dangers.
Checkov is open-source and straightforward to make use of by following these steps:
- Set up Checkov from PyPI with pip
- Choose a folder containing Cloudformation or Terraform recordsdata as enter
- Execute scanning
- Export the consequence to color-coded CLI print
- Combine the consequence into your CI/CD pipelines
TFlint
A Terraform linter – TFLint focuses on checking for potential errors and supplies finest safety practices.
Whereas Terraform is a good instrument for IaC, it might not validate provider-specific points. That is when TFLint is useful for you. Obtain the newest model of this instrument to your cloud structure to resolve such points.
To put in TFlint use:
- Chocolatey for Home windows
- Homebrew for macOS
- TFlint by way of Docker
TFLint additionally helps numerous suppliers by way of plugins similar to AWS, Google Cloud, and Microsoft Azure.
Terrafirma
Terrafirma is one other static code evaluation instrument used for Terraform plans. It’s designed to detect safety misconfigurations.
Terrafirma supplies output in tfjson as an alternative of JSON. To put in it you should use virtualenv and wheels.
Accuracy
With Accurics you’ve an excellent alternative to guard your cloud infrastructure towards misconfigurations, doable information leaks and coverage violations.
For this, Accurics performs code scans for Kubernetes YAML, Terraform, OpenFaaS YAML and Dockerfile. This manner you’ll be able to detect issues earlier than they will even hinder you and make options to your cloud infrastructure.
By performing these checks, Accurics ensures that there aren’t any anomalies within the infrastructure configuration. Shield the whole cloud stack, together with software program containers, platforms, infrastructure, and servers. Future-proof your DevOps lifecycle by implementing compliance, safety, and governance.
Get rid of drift by detecting adjustments in your provisioned infrastructure, probably inflicting perspective drift. Get full visibility in actual time, outlined by code throughout your total infrastructure, and replace codes to revive the cloud or replicate genuine adjustments.
You may as well notify your builders of a difficulty by integrating with environment friendly workflow instruments similar to Slack, webhooks, e mail, JIRA, and Splunk. It additionally helps DevOps instruments together with GitHub, Jenkins and extra.
You need to use Accurics within the type of a cloud resolution. Alternatively, you’ll be able to obtain the self-hosted model relying in your group’s necessities.
You may as well strive their open-source Terrascan, which may scan Terraform towards over 500 safety insurance policies.
CloudSploit
Mitigate safety dangers by scanning Cloudformation templates in seconds utilizing CloudSploit. It may possibly scan greater than 95 safety vulnerabilities in additional than 40 varieties of sources, comprising a variety of AWS merchandise.
It may possibly effectively detect dangers and deploy safety features earlier than your cloud infrastructure is launched. CloudSploit supplies plugin-based scanning the place you’ll be able to add safety checks when AWS provides assets to Cloudformation.
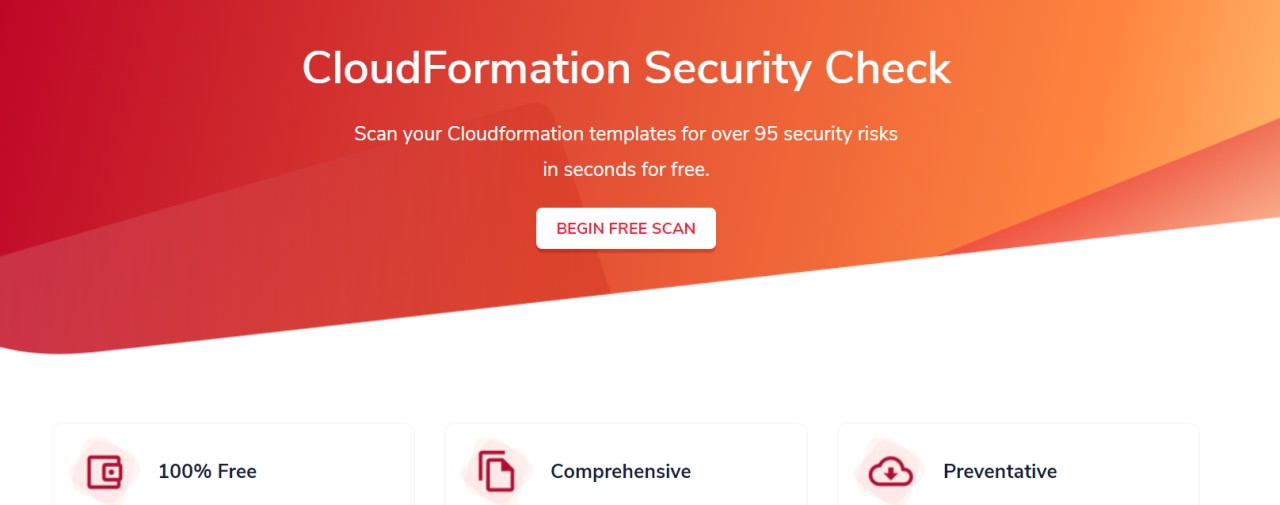
CloudSploit additionally supplies API entry to your comfort. Plus, you get a drag and drop function or paste a template to get leads to seconds. Whenever you add a template to the scanner, it compares every supply setting towards unidentified values and returns the consequence: warning, success or failure.
As well as, you’ll be able to click on on any consequence to view the supply concerned.
Trives
Trivy, a usually up to date safety scanning instrument, focuses on offering complete protection when detecting vulnerabilities. It releases new variations each month that focus on completely different working methods and programming languages, with completely different variations and sources of vulnerabilities.
It’s an distinctive all-in-one open-source safety scanner and is thought for its reliability, velocity and user-friendly interface. This highly effective instrument makes it easy to establish vulnerabilities, IaC misconfigurations, SBOM detection, cloud scans, and so on.
Trivy extends its capabilities by together with the flexibility to scan Infrastructure as Code (IaC) configurations. It successfully identifies widespread misconfigurations in well-liked IaC instruments similar to Terraform, CloudFormation, Docker, Kubernetes and different configuration recordsdata, enhancing the safety of those precious assets.
It’s a versatile multi-container scanning resolution with no exterior dependencies. It scans native and distant pictures, works with a number of container engines, and is suitable with archived/extracted pictures and uncooked file methods, and git repositories.
Plus, it is moveable: it runs rapidly and successfully on any working system or CPU structure, making certain environment friendly preliminary scan occasions and enabling repetitive high-speed scans.
Conclusion
Infrastructure-as-Code is changing into more and more well-liked within the trade. And why not: it has introduced vital adjustments to IT infrastructure, making it stronger and higher. Nevertheless, not working towards IaC with warning can result in safety vulnerabilities. However don’t worry; use these instruments to scan IaC for vulnerabilities.
Do you need to be taught Terraform? Then view this on-line course.

