Take steps throughout improvement to strengthen your internet backend and maintain it safe.
Small companies, banks and plenty of industries rely on internet purposes. From the second you construct an online software, it’s essential to make certain of protocols to test for vulnerabilities as improvement progresses to forestall safety breaches, knowledge leaks and monetary issues.
Essentially the most harmful internet assaults are people who occur on the server facet the place knowledge is saved and analyzed.
What’s Backend?
An online software consists of two components: frontend and backend.
- The frontend is consumer facet, it’s the half the consumer interacts with. Often it’s constructed with HTML, CSS and Javascript.
- The backend is server facet. It is mainly how the applying works, making use of the enterprise logic, modifications and updates. Among the standard server-side tech stacks cowl PHP, NodeJS, Java, Ruby, C, Python, database, safety (authentication, entry management, and so forth.), construction, and content material administration.
A little bit reminder earlier than we begin – authentication, entry management and session administration
It’s regular for us to combine up the phrases. So let’s shortly make clear:
- Authentication includes proving the identification of the consumer (e.g. password, username, safety questions, fingerprints)
- Entry management is about what the consumer has entry to the applying. It enforces the coverage that customers can not act exterior their supposed permissions.
- Session administration issues responses and request transactions related to the identical consumer. It’s an trade mechanism used between the consumer and the applying after he has efficiently authenticated.
Let’s discover the next for higher back-end internet safety.
Injection defects

Since 2010, OSWAP labeled injection as essentially the most harmful internet software threat.
Injection errors enable a consumer to supply knowledge containing key phrases that change the conduct of queries constructed on the database. For instance, let’s assume we’ve a SQL script that checks if an identical entry exists within the database.
uname = request.POST['username'] passwd = request.POST['password'] sql = "SELECT id FROM customers WHERE username='" + uname + "' AND password='" + passwd + "'" database.execute(sql)
An attacker can now manipulate the password discipline utilizing SQL injection, for instance by getting into the password ‘OR 1 =’ 1, ensuing within the following SQL question:
sql = "SELECT id FROM customers WHERE username='' AND password='password' OR 1='1'
This offers the attacker entry to all consumer tables of the database, the place the password is at all times legitimate (1 = ‘1’). In the event that they log in as an administrator, they’ll make any modifications they need.
Methods to forestall it?
It is rather SIMPLE injection errors.
One of the best and easy method to confirm that there are not any injection errors is a radical handbook overview of the supply code to confirm that queries in opposition to the database are achieved by means of ready statements. You too can use instruments to test for vulnerabilities.
And also you additionally have to do the next.
- Use ORMs (Object Relational Mapping Instruments).
- Escape all inputs. A date discipline ought to by no means include something apart from dates.
- Isolate your knowledge in order that solely the issues that needs to be accessible from a sure location are saved in that location.
- Write error codes for correct dealing with. Do not make your database or your backend too intensive.
Troy Hunt received an excellent course on SQL injection. If you’re , you’ll be able to analysis that.
Damaged authentication

As talked about earlier, authentication has to do with offering credentials. It’s the entrance line of protection in opposition to unrestricted entry. Nevertheless, poor implementation and non-compliance with safety insurance policies can result in damaged authentication.
Damaged authentication often occurs by means of three patterns:
- Credentials stuffings: the place the attacker has a listing of legitimate usernames and passwords and might automate the assault to search out out if the credentials are legitimate.
- Bruteforce assault: the place the applying permits weak passwords for customers or directors.
- Session Hijacking: The place the applying shows or doesn’t run the session ID or URL after login.
In all circumstances, the attacker might acquire entry to an necessary account and rely on the corporate which might result in cash laundering, identification theft or the disclosure of legally protected, extremely delicate data.
Methods to forestall it?
Earlier than implementing the authentication system, ask your self: What can an attacker obtain if the authentication system is compromised?
And in response to the reply, you are able to do the next.
- Implement multi-factor authentication to forestall automated assaults.
- Encourage (or power) the consumer to have an excellent password coverage.
- Restrict failed logins.
- Use environment friendly algorithm hash. When selecting an algorithm, bear in mind the utmost password size.
- Check the session timeout system and be certain that the session token is invalidated after logout.
Damaged entry management

Entry management exists to make sure what the authenticated consumer is allowed to do. Authentication and session administration are the idea or guidelines of entry management. However when these guidelines aren’t arrange correctly, it may possibly result in vital issues.
Frequent entry management errors embody:
- CORS misconfiguration permitting unauthorized API entry.
- Manipulation of metadata for direct entry to strategies.
- Pressured shopping: The attacker tries a URL, modifications paths (e.g. http://web site.area/consumer/ to http://web site.area/admin) and should even uncover necessary recordsdata.
Methods to forestall it?
Often, defective entry errors come up from ignorance of the important necessities of efficient entry management.
- Deny by default, besides public sources.
- Uncheck the record of server directories and ensure no backup recordsdata are current.
- Limit API entry to cut back the influence of automated assaults.
- Invalidate JWT tokens after logout on the backend facet.
Information publicity
Additionally known as knowledge breaches, knowledge publicity is a cyber menace that threatens companies and their prospects.
It happens when the applying doesn’t adequately defend data corresponding to login credentials or delicate knowledge corresponding to bank cards or medical information. Greater than 4,000 information are violated each minute.
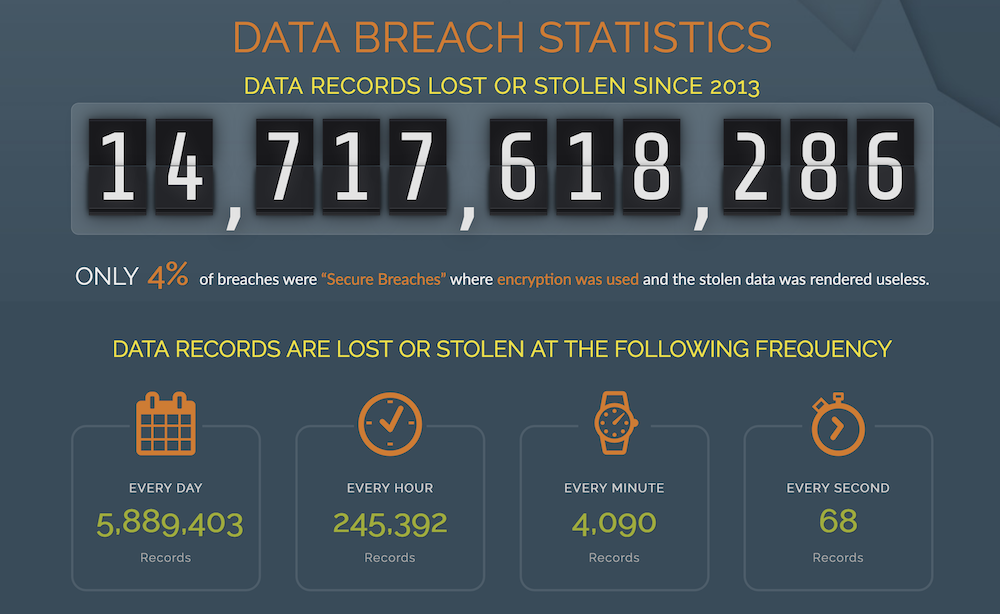
The influence on enterprise is critical from a monetary standpoint: a median breach can value $3.92 million, in response to IBM.
Methods to forestall it?
As a backend developer, you need to ask your self what’s the data that must be protected.
After which to keep away from such flaws:
- Encrypt delicate knowledge: Encrypt every part for knowledge in REST. Be certain that to make use of safe gateways (SSL) for knowledge in transit
- Establish the info that wants further safety and restrict entry to just a few legit customers by implementing key-based encryption.
- Keep away from a weak encryption algorithm: use up-to-date and robust algorithms.
- Have a safe backup plan.
Insecure deserialization
Serialization and deserialization are ideas used when knowledge is transformed into object format to be saved or despatched to a different software. Serialization consists of changing knowledge into object format corresponding to XML or JSON to make it usable. Deserialization is simply the reverse course of.
Assaults in opposition to deserializers can result in denial-of-service, entry management, and Distant Code Execution (RCE) assaults if there are lessons that may be modified to vary conduct.
The second instance of the OWASP high 10 doc offers an excellent illustration of PHP object serializer:
a:4:{i:0;i:132;i:1;s:7:"Mallory";i:2;s:4:"consumer";
i:3;s:32:"b6a8b3bea87fe0e05022f8f3c88bc960";}It is a tremendous cookie that incorporates data corresponding to consumer ID, consumer stage and hashed password.
An attacker can modify the serialized object to realize administrative privileges:
a:4:{i:0;i:1;i:1;s:5:"Alice";i:2;s:5:"admin";
i:3;s:32:"b6a8b3bea87fe0e05022f8f3c88bc960";}Methods to forestall it?
It’s essential to not settle for serialized objects from untrusted sources.
You must also:
- By no means belief consumer enter.
- Validate knowledge: In case your software is besides a string, ensure that it is a string earlier than utilizing it
- Use a test mark to make sure that the info has not been modified. It’s helpful that you’re sending knowledge between two trusted sources (e.g. storing knowledge on the consumer facet).
server XSS

Server XSS (Cross-site scripting) is a sort of injection when an attacker makes use of an online software to ship malicious code to totally different customers. It happens when the attacker publishes edited knowledge that incorporates malicious code that’s saved by the applying. This vulnerability is on the server facet; the browser simply shows the reply.
For instance, in a discussion board, consumer posts are saved in a database, usually with out authentication. Attackers use this chance so as to add messages containing malicious scripts. Then different customers obtain this hyperlink by e mail or see the publish in query and click on on it.
Methods to forestall it?
After major identification of all operations doubtlessly in danger for XSS that want safety, think about the next.
- Validate enter: test for enter size, use regex matches, and permit solely a sure set of characters.
- Validate output: If the applying copies a knowledge merchandise in its responses that comes from a consumer or a 3rd occasion, this knowledge should be HTML encoded to scrub up doubtlessly malicious characters.
- Restrict Enable HTML: For instance, you probably have a remark weblog system, solely enable the usage of sure tags. If attainable, use an applicable framework for user-supplied HTML markup to make sure that it doesn’t include any method to execute JavaScript.
Conclusion
The event part is essential for internet software safety. And it’s best to think about incorporating a safety vulnerability scanner into the event lifecycle in order that recognized points are resolved earlier than manufacturing.

