As with all cloud companies, you have to take accountability for securing cloud storage.
On this article, we talk about the most effective tricks to safe AWS S3 storage.
Earlier than we see the ideas for securing AWS S3 storage, we have to know why that is essential. By 2017, it had disclosed important knowledge reminiscent of personal social media accounts and categorized Pentagon knowledge.
Since then, each group pays shut consideration to securing their knowledge saved within the AWS S3.
Does this imply that S3 is an insecure Amazon Net Companies storage resolution? In no way, S3 is a safe storage resolution, however it will depend on the consumer how they wish to safe their knowledge.
AWS shared accountability mannequin
Most options supplied by the general public cloud supply a Shared Accountability Mannequin. Which means that the accountability for the safety of the cloud platform lies with AWS and the cloud prospects are chargeable for the safety within the cloud.
This shared mannequin helps to forestall knowledge breaches. The diagram under exhibits the general accountability of the AWS and the shopper’s accountability for securing the info.
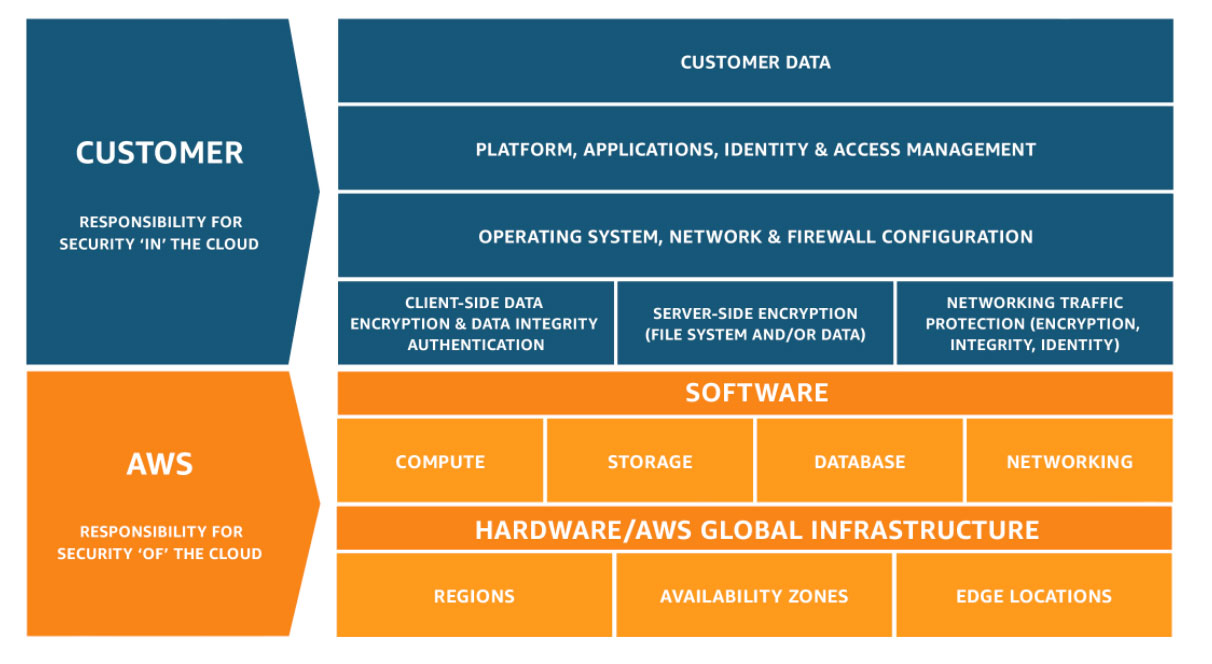
Research the diagram above to familiarize your self with the duties it is advisable tackle. Preventive measures to safe S3 storage are important, however each menace can’t be averted. AWS affords quite a few methods that can assist you proactively monitor and forestall the chance of knowledge breaches.
Let’s check out the next finest practices to safe AWS S3 storage.
Create personal and public bucket
If you create a brand new bucket, the default bucket coverage is personal. The identical applies to the newly uploaded objects. You could manually grant entry to the entity you wish to entry the info.
Utilizing the mix of bucket insurance policies, ACL and IAM insurance policies present the correct entry to the correct entities. However this turns into complicated and tough when you hold each personal and public objects in the identical bucket. Mixing each the private and non-private objects in the identical bucket results in cautious evaluation of ACLs resulting in a waste of your productive time.
A easy method is to separate the objects right into a public bucket and a personal bucket. Create a single public bucket with a bucket coverage to grant entry to all objects saved in it.
{
"Impact": "Enable",
"Principal": "*",
"Motion": "s3:GetObject",
"Useful resource": "arn:aws:s3:::YOURPUBLICBUCKET/*"
}Then create one other bucket to retailer personal objects. By default, all entry to the bucket is blocked for public entry. You may then use the IAM coverage to grant entry to those objects to particular customers or utility entry.
Encrypt knowledge at relaxation and in transit
Allow encryption to guard knowledge at relaxation and in transit. You may set this up in AWS to encrypt objects on servers earlier than storing them in S3.
This may be achieved utilizing commonplace AWS managed S3 keys or your keys created within the Key Administration Service. To implement knowledge encryption in transit by utilizing the HTTPS protocol for all bucket operations, add the code under to the bucket coverage.
{
"Motion": "s3:*",
"Impact": "Deny",
"Principal": "*",
"Useful resource": "arn:aws:s3:::YOURBUCKETNAME/*",
"Situation": {
"Bool": { "aws:SecureTransport": false }
}
}Use CloudTrail
CloudTrail is an AWS service that data and maintains the path of occasions that happen within the AWS companies. The 2 varieties of CloudTrail occasions are knowledge occasions and administration occasions. Knowledge occasions are disabled by default and are far more granular.
The administration occasions confer with the creation, deletion, or replace of S3 buckets. And the info occasions confer with the API calls made on the objects like PutObject, GetObject or GetObject.
Not like administration occasions, knowledge occasions price $0.10 per 100,000 occasions.
You create a particular monitor to log and monitor your S3 bucket in a particular area or worldwide. These paths retailer logs within the S3 bucket.
CloudWatch and Alerts
Having a CloudTrail setup is nice for monitoring, however if you would like management over alerts and self-healing, use CloudWatch. AWS CloudWatch gives immediate occasion logging.

You can too arrange CloudTrail inside a CloudWatch log group to create log streams. Having a CloudTrail occasion within the CloudWatch provides some highly effective options. You may set the metric filters to allow CloudWatch alert for suspicious exercise.
Arrange lifecycle coverage
Establishing a lifecycle coverage protects your knowledge and saves you cash. By setting the lifecycle coverage, you progress the undesirable knowledge to make it personal and delete it later. This ensures that the undesirable knowledge is not accessible to the hackers and saves cash by releasing up the area. Allow the lifecycle coverage to maneuver the info from default storage to AWS Glacier to save cash.
Later, the info saved within the Glacier may be deleted if it not provides worth to you or the group.
S3 Block public entry
AWS has taken steps to automate the performance to dam public entry to a bucket, beforehand utilizing a mixture of CloudWatch, CloudTrail, and Lambda.
There are instances the place builders unintentionally make the objects or bucket public. To forestall unintended entry to creating the bucket or objects public, these options turn out to be useful.
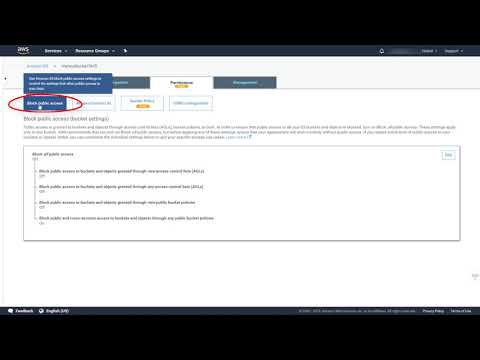
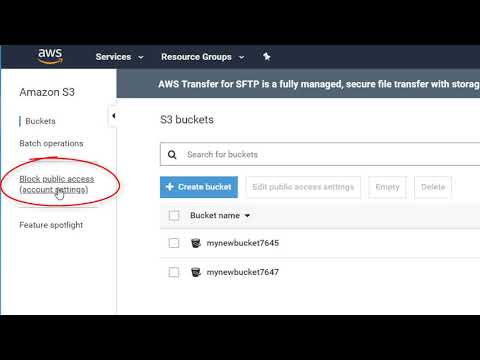
The brand new Block Public Entry setting characteristic prevents anybody from making the bucket public. You may allow this setting within the AWS console, as proven within the video above. You can too apply this setting on the account stage, as defined within the video under.
Hearken to AWS Trusted Advisor
AWS Trusted Advisor is a built-in characteristic used to investigate the AWS sources inside your account and suggest finest practices.
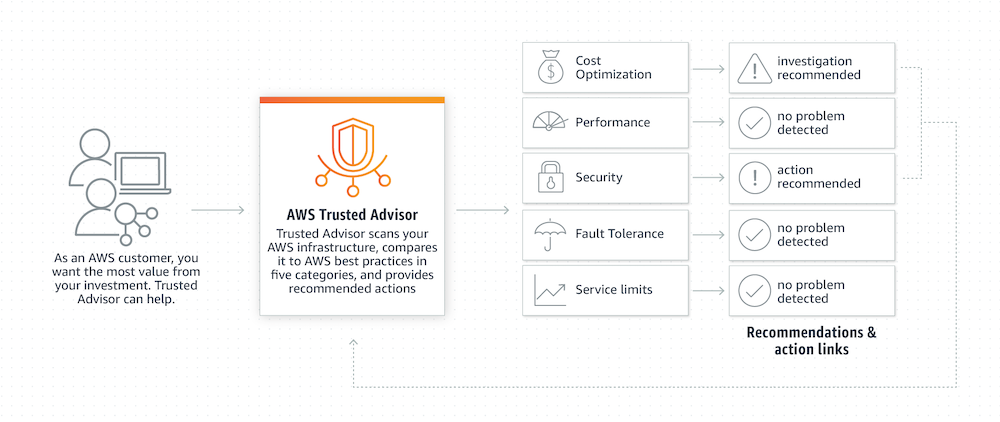
They provide suggestions in 5 classes; one of many essential options is safety. Since February 2018, AWS notifies you when the S3 buckets are made publicly accessible.
Third-party AWS safety instruments
Other than Amazon, there’s a third social gathering that gives safety instruments to safe your knowledge. They will prevent an enormous period of time whereas conserving the info secure. A number of the common instruments are talked about under:
Safety monkey
It’s a software developed by Netflix to trace the AWS coverage adjustments and alerts if unsafe configurations are discovered. Safety Monkey performs quite a few audits on S3 to make sure finest practices are in place. It additionally helps the Google Cloud Platform.
Cloud custodian
Cloud Custodian helps you handle sources in a cloud aligned with finest practices. In easy phrases, after getting recognized the most effective observe, you need to use this software to scan the sources within the cloud to make sure compliance.
If they don’t seem to be met, you need to use many choices to ship alerts or implement the lacking coverage.
Cloud Mapper
Duo Safety has created the Cloud Mapper, an incredible software for cloud visualization and audit. It has an identical characteristic of Safety Monkey to run the scan of S3 buckets for any misconfigurations. It gives an incredible visible illustration of your AWS infrastructure to enhance identification of different points.
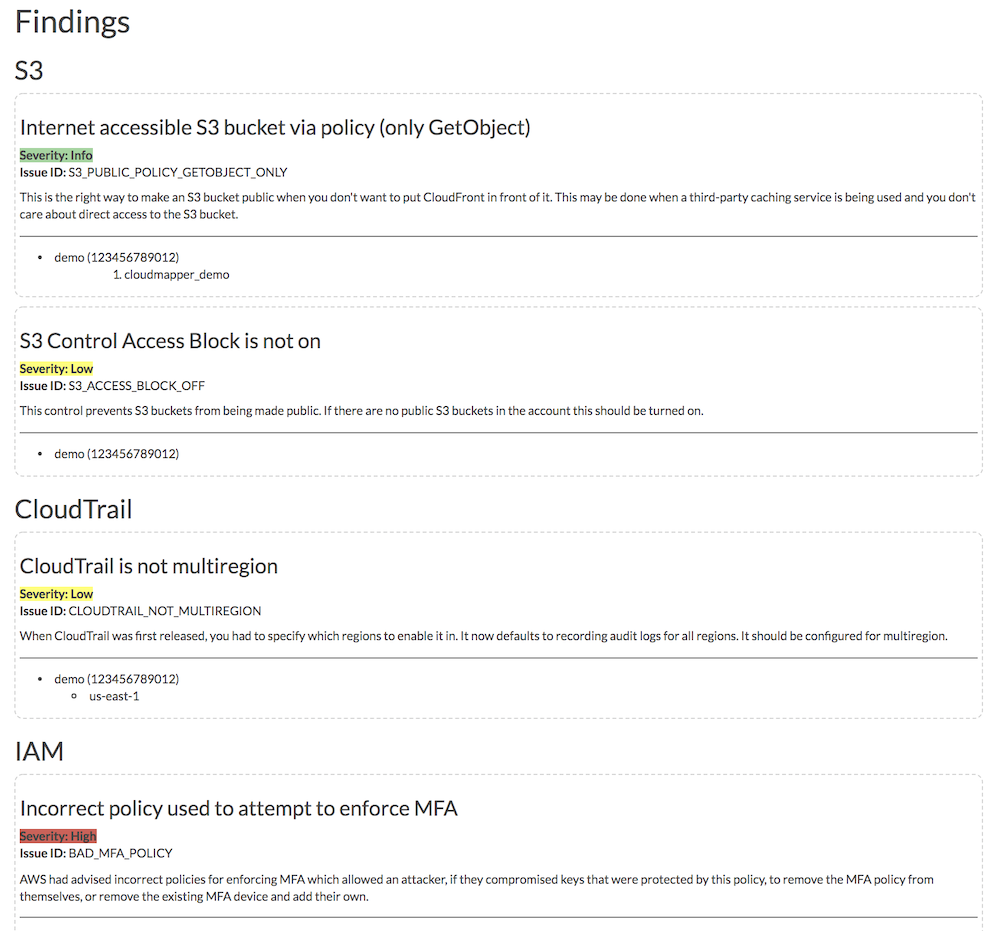
And it affords glorious reporting.
Conclusion
Since a lot of the work is completed utilizing knowledge, conserving it safe ought to be one of many core duties.
One can by no means know when and the way the info breach will happen. Therefore, a preventive motion is at all times advisable. Prevention is healthier than treatment. Securing the info will prevent hundreds of {dollars}.
When you’re new to the cloud and eager about studying AWS, take a look at this Udemy course.

