Joomla is the second well-liked CMS for a web site with greater than 4.5% market share and development.
Safety is simply as vital as a web site’s design and content material, however we frequently ignore it till it is negatively impacted. Improperly configured/hardened Joomla server may be weak to many, together with distant code execution, SQL injection, cross-site scripting, info leakage, and many others.
Safety is a course of cycle, which ought to at all times be carried out in opposition to net functions. On this article, I’ll speak about instruments to scan Joomla web site for vulnerabilities to guard in opposition to hurt.
Hacker goal
Joomla safety scan by Hacker Goal has two choices.
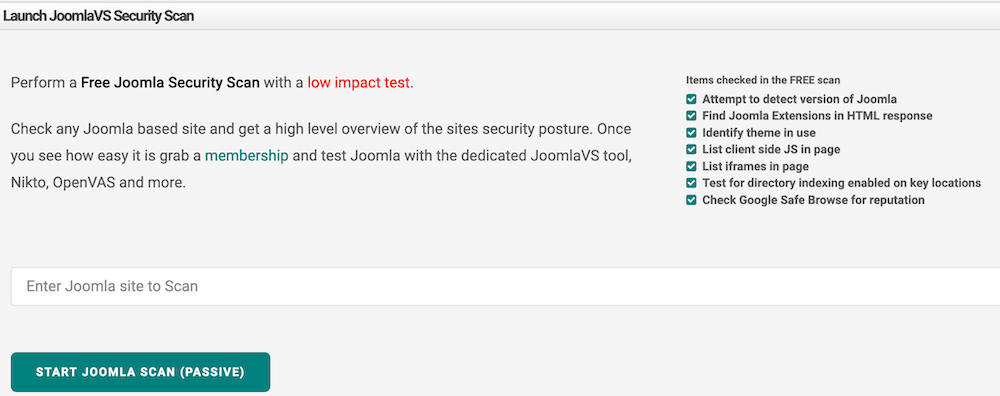
passive scan – this can be a FREE scan and does the next.
- Google search for protected shopping
- Lookup listing index
- Exterior hyperlink and their net status
- Record of exterior iFrames, JavaScript
- Geolocation and website hosting lookup
Aggressive, lively scan – this requires membership and aggressive monitoring to detect recognized exploits and vulnerabilities in themes, extensions, modules, parts and Joomla core.
SiteGuarding
SiteGuarding is a cloud-based web site safety scanner that additionally presents a Joomla extension to research your web site.
Within the FREE model of the extension, you get the next.
- Scan as much as 500 information
- Every day virus database replace
- Report
- One scan per day
- Heuristic logic
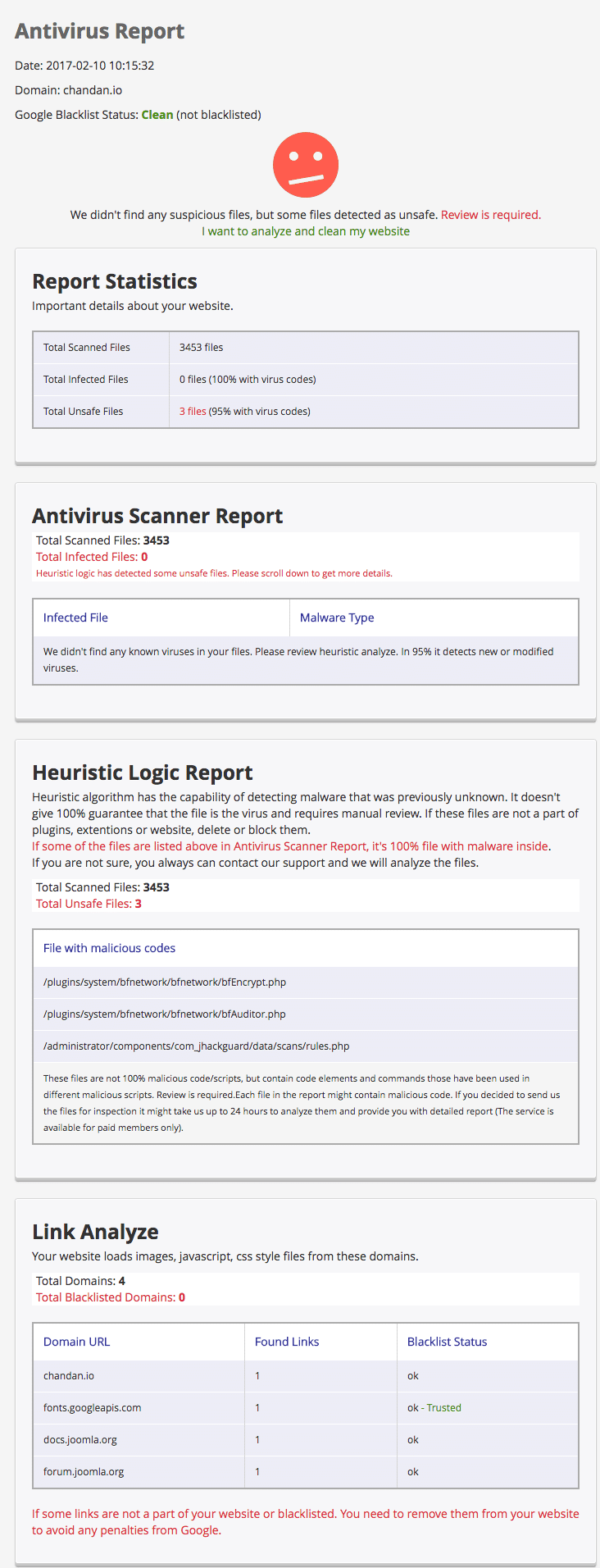
You might also need to attempt their Antivirus Scanner extension.
To detect
Detectify is an enterprise-ready SaaS scanner for complete web site auditing with over 1000 vulnerabilities together with OWASP prime 10. It performs safety checks on CMS resembling Joomla, WordPress, Drupal, and many others. to make sure CMS particular vulnerabilities are coated.
It isn’t fully free, however you possibly can benefit from their trial supply to see the way it works.
JAMS
JAMSS (Joomla Anti Malware Scan Script) is a script that you’ll want to set up within the root location of your web site.
Script set up is nothing however importing the file jamss.php frequent to your net root. JAMSS identifies typical fingerprints, traces that might have been compromised. The script doesn’t hurt something and to entry the scan report; you simply go to yourwebsite.com/jamss.php
JUICES
Web site Examine by SUCURI checks for recognized malware, blacklisting, SPAM, defacement and offers you details about an online server, hyperlinks and included scripts.
Safety test
Safety Examine extension protects your web site for greater than 90 assaults sample, and it has a built-in vulnerability checker to check put in extensions for safety vulnerabilities.
Joomscan
Joomscan is without doubt one of the hottest open-source instruments that will help you discover recognized vulnerabilities of Joomla Core, Elements and SQL Injection, Command execution. There are two methods to get this working.
- Obtain from the OWASP website and set up in your PC
- Use Kali Linux which comes with over 600 instruments together with Joomscan
After putting in Joomscan, here is easy methods to run it on the Joomla website to scan the vulnerability.
./joomscan –u http://joomlawebsite.comEx, I ran my take a look at website.
root@Chandan:~# joomscan -oh -u http://techpostal.com
..|''|| '|| '||' '|' | .|'''.| '||''|.
.|' || '|. '|. .' ||| ||.. ' || ||
|| || || || | | || ''|||. ||...|'
'|. || ||| ||| .''''|. . '|| ||
''|...|' | | .|. .||. |'....|' .||.
=================================================================
OWASP Joomla! Vulnerability Scanner v0.0.4
(c) Aung Khant, aungkhant]at[yehg.net
YGN Ethical Hacker Group, Myanmar, http://yehg.net/lab
Update by: Web-Center, http://web-center.si (2011)
=================================================================
Vulnerability Entries: 611
Last update: February 2, 2012
Use "update" option to update the database
Use "check" option to check the scanner update
Use "download" option to download the scanner latest version package
Use svn co to update the scanner and the database
svn co https://joomscan.svn.sourceforge.net/svnroot/joomscan joomscan
Target: http://techpostal.com
Server: Apache
X-Powered-By: PHP/5.4.45
## Checking if the target has deployed an Anti-Scanner measure
[!] Scanning Handed ..... OK
## Detecting Joomla! primarily based Firewall ...
[!] No recognized firewall detected!
## Fingerprinting in progress ...
Use of uninitialized worth in sample match (m//) at ./joomscan.pl line 1009.
~Unable to detect the model. Is it certain a Joomla?
## Fingerprinting executed.
Vulnerabilities Found
==========================
# 1
Data -> Generic: htaccess.txt has not been renamed.
Variations Affected: Any
Examine: /htaccess.txt
Exploit: Generic defenses applied in .htaccess usually are not out there, so exploiting is extra more likely to succeed.
Susceptible? Sure
# 2
Data -> Generic: Unprotected Administrator listing
Variations Affected: Any
Examine: /administrator/
Exploit: The default /administrator listing is detected. Attackers can bruteforce administrator accounts. Learn: http://yehg.web/lab/pr0js/view.php/MULTIPLEpercent20TRICKYpercent20WAYSpercent20TOpercent20PROTECT.pdf
Susceptible? Sure
# 3
Data -> Core: A number of XSS/CSRF Vulnerability
Variations Affected: 1.5.9 <=
Examine: /?1.5.9-x
Exploit: A collection of XSS and CSRF faults exist within the administrator utility. Affected administrator parts embrace com_admin, com_media, com_search. Each com_admin and com_search comprise XSS vulnerabilities, and com_media incorporates 2 CSRF vulnerabilities.
Susceptible? N/A
# 4
Data -> Core: JSession SSL Session Disclosure Vulnerability
Variations effected: Joomla! 1.5.8 <=
Examine: /?1.5.8-x
Exploit: When working a website beneath SSL (all the website is pressured to be beneath ssl), Joomla! doesn't set the SSL flag on the cookie. This will permit somebody monitoring the community to search out the cookie associated to the session.
Susceptible? N/A
# 5
Data -> Core: Frontend XSS Vulnerability
Variations effected: 1.5.10 <=
Examine: /?1.5.10-x
Exploit: Some values had been output from the database with out being correctly escaped. Most strings in query had been sourced from the administrator panel. Malicious regular admin can leverage it to realize entry to tremendous admin.
Susceptible? N/A
# 6
Data -> Core: Frontend XSS - HTTP_REFERER not correctly filtered Vulnerability
Variations effected: 1.5.11 <=
Examine: /?1.5.11-x-http_ref
Exploit: An attacker can inject JavaScript or DHTML code that will probably be executed within the context of focused consumer browser, permitting the attacker to steal cookies. HTTP_REFERER variable will not be correctly parsed.
Susceptible? N/A
# 7
Data -> Core: Frontend XSS - PHP_SELF not correctly filtered Vulnerability
Variations effected: 1.5.11 <=
Examine: /?1.5.11-x-php-s3lf
Exploit: An attacker can inject JavaScript code in a URL that will probably be executed within the context of focused consumer browser.
Susceptible? N/A
# 8
Data -> Core: Authentication Bypass Vulnerability
Variations effected: Joomla! 1.5.3 <=
Examine: /administrator/
Exploit: Backend accepts any password for customized Tremendous Administrator when LDAP enabled
Susceptible? N/A
# 9
Data -> Core: Path Disclosure Vulnerability
Variations effected: Joomla! 1.5.3 <=
Examine: /?1.5.3-path-disclose
Exploit: Crafted URL can disclose absolute path
Susceptible? N/A
# 10
Data -> Core: Consumer redirected Spamming Vulnerability
Variations effected: Joomla! 1.5.3 <=
Examine: /?1.5.3-spam
Exploit: Consumer redirect spam
Susceptible? N/A
# 11
Data -> Core: Admin Backend Cross Web site Request Forgery Vulnerability
Variations effected: 1.0.13 <=
Examine: /administrator/
Exploit: It requires an administrator to be logged in and to be tricked right into a specifically crafted webpage.
Susceptible? N/A
# 12
Data -> CoreComponent: com_content SQL Injection Vulnerability
Model Affected: Joomla! 1.0.0 <=
Examine: /parts/com_content/
Exploit: /index.php?possibility=com_content&activity=blogcategory&id=60&Itemid=99999+UNION+SELECT+1,concat(0x1e,username,0x3a,password,0x1e,0x3a,usertype,0x1e),3,4,5+FROM+jos_users+the place+usertype=0x53757065722041646d696e6973747261746f72--
Susceptible? No
# 13
Data -> CoreComponent: com_search Distant Code Execution Vulnerability
Model Affected: Joomla! 1.5.0 beta 2 <=
Examine: /parts/com_search/
Exploit: /index.php?possibility=com_search&Itemid=1&searchword=%22percent3Bechopercent20md5(911)%3B
Susceptible? No
# 14
Data -> CoreComponent: MailTo SQL Injection Vulnerability
Variations effected: N/A
Examine: /parts/com_mailto/
Exploit: /index.php?possibility=com_mailto&tmpl=mailto&article=550513+and+1=2+union+choose+concat(username,char(58),password)+from+jos_users+the place+usertype=0x53757065722041646d696e6973747261746f72--&Itemid=1
Susceptible? No
# 15
Data -> CoreComponent: com_content Blind SQL Injection Vulnerability
Variations effected: Joomla! 1.5.0 RC3
Examine: /parts/com_content/
Exploit: /index.php?possibility=com_content&view=%' +'a'='a&id=25&Itemid=28
Susceptible? No
# 16
Data -> CoreComponent: com_content XSS Vulnerability
Model Affected: Joomla! 1.5.7 <=
Examine: /parts/com_content/
Exploit: The defaults on com_content article submission permit entry of harmful HTML tags (script, and many others). This solely impacts customers with entry stage Writer or larger, and solely you probably have not set filtering choices in com_content configuration.
Susceptible? N/A
# 17
Data -> CoreComponent: com_mailto Electronic mail Spam Vulnerability
Model Affected: Joomla! 1.5.6 <=
Examine: /parts/com_mailto/
Exploit: The mailto element doesn't confirm validity of the URL previous to sending.
Susceptible? N/A
# 18
Data -> CoreComponent: com_content view=archive SQL Injection Vulnerability
Variations effected: Joomla! 1.5.0 Beta1/Beta2/RC1
Examine: /parts/com_content/
Exploit: Unfiltered POST vars - filter, month, yr to /index.php?possibility=com_content&view=archive
Susceptible? No
# 19
Data -> CoreComponent: com_content XSS Vulnerability
Model Affected: Joomla! 1.5.9 <=
Examine: /parts/com_content/
Exploit: A XSS vulnerability exists within the class view of com_content.
Susceptible? N/A
# 20
Data -> CoreComponent: com_users XSS Vulnerability
Model Affected: Joomla! 1.5.10 <=
Examine: /parts/com_users/
Exploit: A XSS vulnerability exists within the consumer view of com_users within the administrator panel.
Susceptible? N/A
# 21
Data -> CoreComponent: com_installer CSRF Vulnerability
Variations effected: Joomla! 1.5.0 Beta
Examine: /administrator/parts/com_installer/
Exploit: N/A
Susceptible? N/A
# 22
Data -> CoreComponent: com_search Reminiscence Comsumption DoS Vulnerability
Variations effected: Joomla! 1.5.0 Beta
Examine: /parts/com_search/
Exploit: N/A
Susceptible? No
# 23
Data -> CoreComponent: com_banners Blind SQL Injection Vulnerability
Variations effected: N/A
Examine: /parts/com_banners/
Exploit: /index.php?possibility=com_banners&activity=archivesection&id=0'+and+'1'='1::/index.php?possibility=com_banners&activity=archivesection&id=0'+and+'1'='2
Susceptible? No
# 24
Data -> CoreComponent: com_mailto timeout Vulnerability
Variations effected: 1.5.13 <=
Examine: /parts/com_mailto/
Exploit: [Requires a valid user account] In com_mailto, it was potential to bypass timeout safety in opposition to sending automated emails.
Susceptible? N/AAs you possibly can see within the outcomes above, it scans for over 20 vulnerabilities and notifies you if one is discovered so you possibly can repair and safe Joomla.
Pentest Instruments
Joomla Vulnerability Scan by Pentest-Instruments is powered by the JoomlaVS instrument.
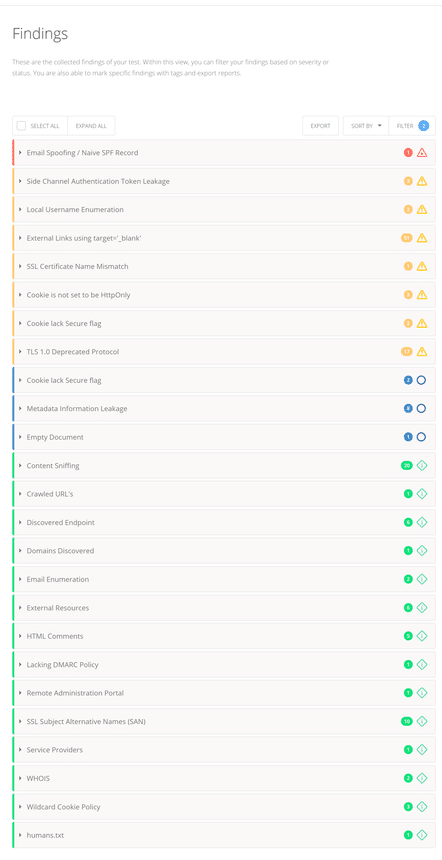
You possibly can run this take a look at in your website to shortly see if the core, template, and module are weak. After the take a look at is accomplished, it generates a ravishing report with all of the discovering particulars. It is like doing a penetration take a look at.
Conclusion
I hope the above instruments assist you scan Joomla for vulnerabilities and preserve your web site protected. Listed below are among the helpful ones sources to maintain you knowledgeable about Safety.
- Record of Joomla Susceptible Extensions – http://vel.joomla.org/
- Joomla CVE Particulars – http://www.cvedetails.com/vulnerability-list/vendor_id-3496/product_id-16499/Joomla-Joomla-.html
- Joomla Developer Community (Safety Heart) – http://developer.joomla.org/security-centre.html
- Joomla Safety Documentation – https://docs.joomla.org/Safety
- Instruments to Scan Web site Safety – https://geekflare.com/online-scan-website-security-vulnerabilities/
- Joomla Safety Greatest Follow – https://geekflare.com/joomla-security/

