Reverse Engineering is the method of analyzing a product or system with the intention to perceive its design, inner workings, and performance.
Reverse engineering is usually used to realize a greater understanding of a product or system with the intention to enhance it, to create competing merchandise or techniques, or to establish and repair flaws or vulnerabilities.
It’s generally utilized in fields resembling software program improvement, manufacturing, and safety. Nevertheless, reverse engineering may also be used for malicious functions, resembling stealing commerce secrets and techniques or creating counterfeit merchandise. Because of this, reverse engineering is usually regulated by legal guidelines governing mental property and commerce secrets and techniques.
To turn into proficient in reverse engineering, a safety skilled ought to have a robust understanding of laptop science and programming, in addition to expertise with instruments and strategies generally utilized in reverse engineerings, resembling disassemblers and debuggers.
How does Reverse Engineering Work?

Reverse engineering is the method of analyzing a system to grasp its parts, features, and operations with the intention to perceive the way it works or to create a duplicate or imitation of it.
Reverse engineering is used to establish vulnerabilities or weaknesses within the system, create appropriate or various variations of the system, and enhance upon the unique design.
The method of reverse engineering usually entails disassembling a system or machine to grasp its parts and the way they match collectively. This may contain taking aside bodily gadgets or analyzing the code and construction of software program techniques.
As soon as the system has been disassembled, the person parts are studied and analyzed with the intention to perceive their perform and the way they work collectively to allow the general system to perform.
Nevertheless, you will need to respect the mental property rights of others when utilizing reverse engineering and to solely use it for authorized and moral functions.
Objective of Reverse Engineering in Safety
The aim of reverse engineering in safety is to establish and mitigate potential vulnerabilities in a product or system. That is usually accomplished by inspecting the product or system’s design, code, or parts with the intention to perceive the way it works and establish any potential weaknesses.
For instance, a safety researcher could use reverse engineering to check the design of a software program software with the intention to establish any potential vulnerabilities that could possibly be exploited by attackers. This might contain inspecting the appliance’s code, analyzing its community communications, or learning its interactions with different techniques or parts.
As soon as potential vulnerabilities have been recognized, the safety researcher can then work to develop options to mitigate these vulnerabilities, resembling by patching the appliance’s code or implementing extra safety measures. This may help to enhance the general safety of the product or system and shield it from potential assaults.
Steps in Reverse Engineering

Reverse engineering usually entails the next steps:
- Determine the product or system to be reverse-engineered: This usually entails figuring out the precise software program product or system that must be studied higher to grasp its design, inner workings, and performance.
- Accumulate details about the product or system: It entails amassing details about the product or system from numerous sources, resembling its design paperwork, code, or consumer manuals.
- Analyze the product or system: This usually entails analyzing the collected data with the intention to perceive the system’s design and performance. This will likely contain taking the product or system aside, learning its parts and interactions, or inspecting its design paperwork or code.
- Create a mannequin of the product or system: This step usually entails making a mannequin that precisely represents its design, inner workings, and performance. This mannequin can then be used to check the product or system in better element or make modifications or enhancements.
- Use the data gained from reverse engineering: As soon as the mannequin has been created, the data gained from reverse engineering can be utilized to enhance the product or system, create competing merchandise or techniques, or establish and repair flaws or vulnerabilities. This will likely contain altering the product or system’s design, code, or parts or creating new merchandise or techniques primarily based on the data gained.
Let’s get began with the greatest reverse engineering instruments.
Ghidra
Ghidra is a free and open-source software program reverse engineering (SRE) suite of instruments developed by the Nationwide Safety Company (NSA). It’s used to disassemble, decompile, and analyze binary code.
Ghidra was designed to be a strong and scalable SRE instrument, and it’s utilized by each authorities businesses and the broader SRE neighborhood. This instrument was made obtainable to the general public in 2019, and it may be downloaded and used without spending a dime.

It has a user-friendly interface and a modular design, which permits customers to customise the instrument to fulfill their particular wants.
Moreover, Ghidra features a decompiler that may convert meeting code right into a higher-level language, resembling C or Java, which may make it simpler to grasp the performance of a binary file.
Androguard
Androguard is an open-source toolkit for reversing and analyzing Android purposes. It’s written in Python and can be utilized to research the construction and habits of Android apps.
Androguard contains a wide range of instruments for performing several types of evaluation, together with disassembling, decompiling, and deobfuscating Android apps. It may be used to research the code of an app, extract its assets, and establish potential vulnerabilities.
Androguard is extensively utilized by researchers and safety professionals to research the safety of Android apps.
It affords a wide range of options for reverse engineering, together with help for a number of file codecs, the power to carry out static and dynamic evaluation, and integration with different instruments resembling IDA Professional and radare2.
ImHex
ImHex is a hex editor, which is a kind of software program that enables customers to view and edit the uncooked binary knowledge of a file. Hex editors are sometimes utilized by programmers, safety researchers, and different technical customers to look at the contents of a file at a low stage. They’re notably helpful for analyzing information which can be in a binary format, resembling executables or different sorts of compiled code.
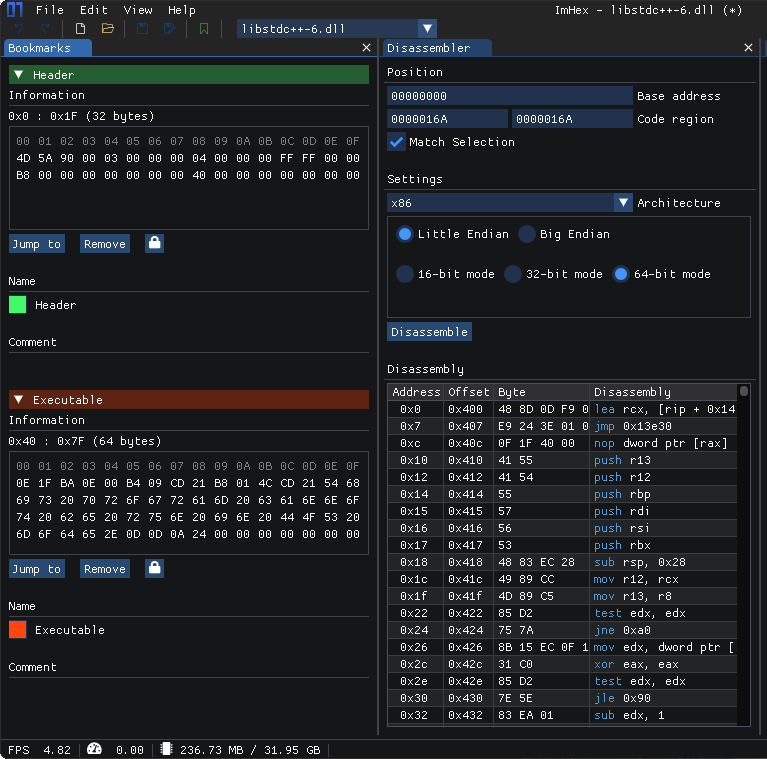
ImHex is a free and open-source hex editor that’s obtainable for Home windows and Linux. It has a user-friendly interface and a wide range of options that make it straightforward to make use of.
Among the key options of ImHex embrace help for big information, a versatile search and substitute perform, and the power to check information side-by-side. ImHex additionally permits customers to outline their very own knowledge sorts, which will be helpful for inspecting particular sorts of knowledge inside a file.
Radare2
Radare2 is an open-source reverse engineering framework that’s used for disassembling, analyzing, and debugging binary information. It’s written in C and is on the market for a variety of platforms, together with Home windows, Linux, and macOS.
This instrument is extensively utilized by safety researchers for a wide range of functions, together with reverse engineering, vulnerability evaluation, and forensics. It has a command-line interface and a strong scripting engine that enables customers to automate complicated duties and prolong the capabilities of the instrument.
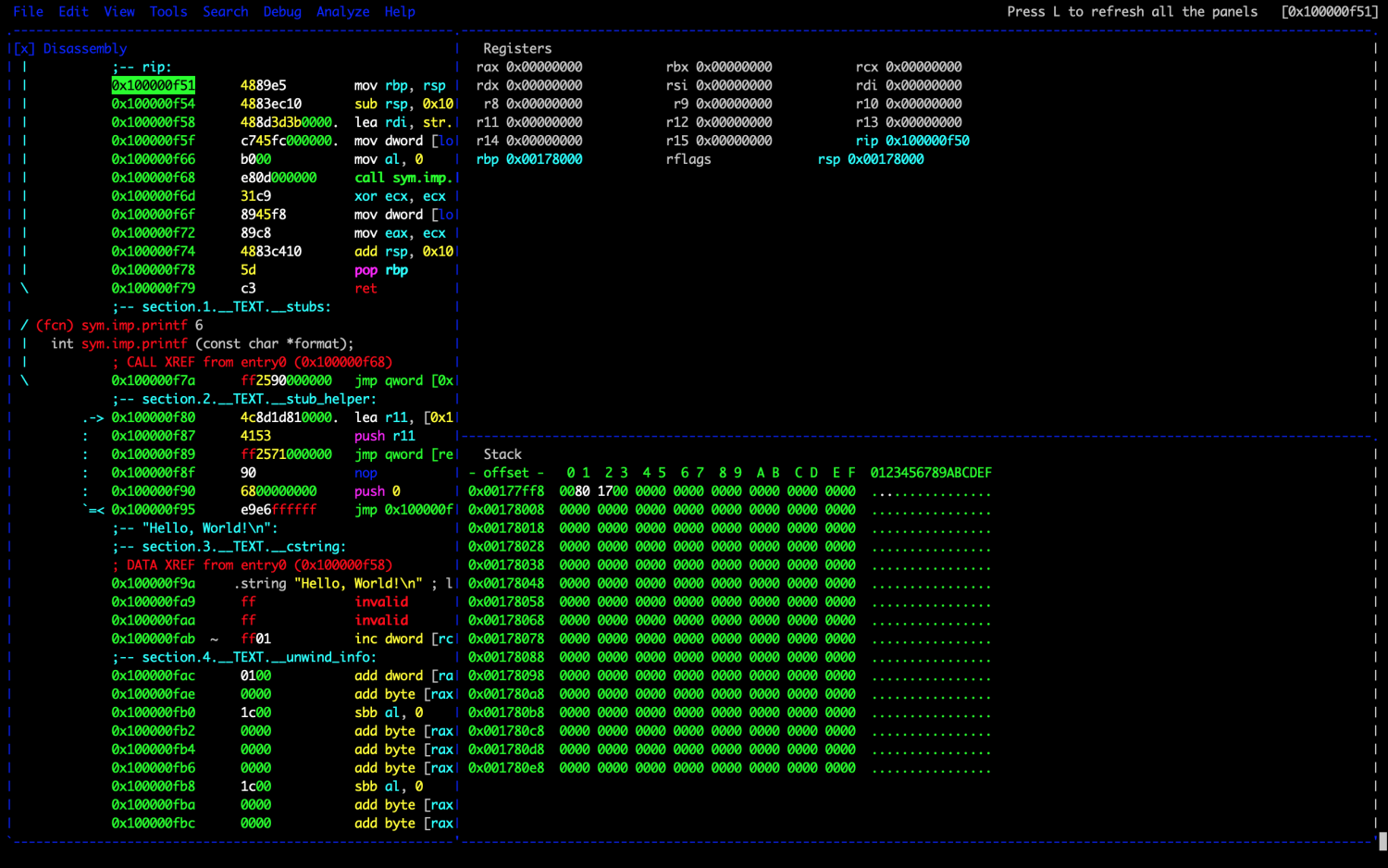
Radare2 additionally features a disassembler that can be utilized to transform binary code into human-readable meeting directions, making it simpler to grasp the inside workings of a binary file.
It affords numerous options for reverse engineering, together with help for a number of architectures and file codecs, the power to carry out static and dynamic evaluation, and integration with different instruments resembling debuggers and disassemblers.
IDA Professional
IDA Professional (quick for Interactive Disassembler Professional) is a industrial disassembler and debugger that’s generally utilized by safety researchers to research compiled code. It may be used to reverse engineer executables and different binary information.
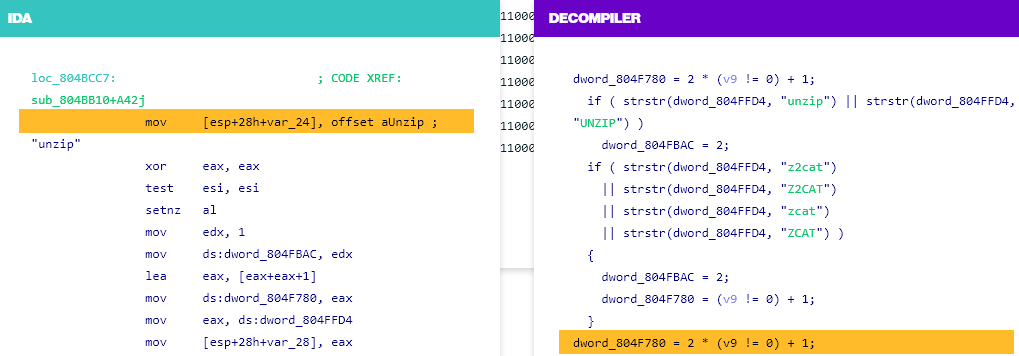
It additionally affords a wide range of options for static and dynamic evaluation, together with help for a number of architectures and file codecs, the power to create and modify disassemblies, and integration with different instruments resembling debuggers and decompilers.
IDA Professional helps cross-platform compatibility and likewise affords a graphical consumer interface in addition to a scripting language for automating complicated duties. It’s thought-about one of the vital highly effective and feature-rich disassemblers obtainable, however it is usually recognized for its steep studying curve and excessive value.
Hiew
Hiew is a binary file viewer and editor for Microsoft Home windows. It’s a fashionable instrument amongst software program builders and safety researchers. Hiew permits customers to view and edit the uncooked knowledge of a binary file, in addition to disassemble machine code into meeting language.
It may also be used to seek for patterns or strings inside a binary file and to check two information for variations. Hiew is just not open supply and isn’t freely obtainable, however it may be bought from its developer’s web site.
Apktool
Apktool is a free and open-source instrument for reverse engineering Android apk information. It’s written in Java and will be run on any platform that helps Java. Apktool permits customers to decode the assets in an apk file and rebuild the app with some modifications.
It’s generally utilized by Android builders and modders to customise apps, in addition to by safety researchers to carry out static evaluation on Android apps.
It may decode the assets in an apk file and create a human-readable illustration of the app’s code and contents.
Apktool may also be used to carry out safety evaluation on Android apps, because it permits customers to examine the app’s code and assets. This permits customers to make modifications to the app’s look and habits.
Nevertheless, It will be important for customers to respect the mental property rights of app builders and use Apktool just for authorized and moral functions.
edb-debugger
EDB is a free and open-source debugger for Linux, Home windows, and macOS. It’s a highly effective instrument that can be utilized to research and debug a variety of executables, together with ELF, PE, Mach-O, and Java class information.
EDB contains a wide range of options that make it a helpful instrument for software program improvement and reverse engineering.
One of many key options of EDB is its user-friendly interface, which makes it straightforward to make use of even for many who are new to debugging. It contains a wide range of views, resembling a disassembly view, a reminiscence map, and a register view, that present detailed details about the state of this system being debugged.
EDB additionally permits customers to set breakpoints, single-step via code, and examine the values of variables, making it straightforward to research and debug applications.
Moreover, EDB contains help for a wide range of processor architectures and working techniques, making it a flexible instrument that can be utilized on a variety of platforms.
Java Snoop
JavaSnoop is a instrument that enables customers to switch the habits of Java purposes at runtime. It’s designed for use for safety testing and evaluation, and it may be used to establish and exploit vulnerabilities in Java purposes.
JavaSnoop works by attaching to a operating Java course of and injecting code into it, permitting the consumer to switch the habits of the appliance on the fly. This may be helpful for figuring out and testing the safety of Java purposes.
JavaSnoop is on the market as a stand-alone instrument and as a plug-in for the favored Burp Suite internet software safety testing platform. It’s written in Java, and it may be run on any platform that helps Java, together with Home windows, Linux, and macOS.
Among the key options of JavaSnoop embrace the power to intercept and modify methodology calls, view and modify the values of variables, and outline customized hooks to automate duties.
Conclusion
Reverse engineering is a helpful talent for safety professionals as a result of it permits them to grasp the design, inner workings, and performance of a product or system with the intention to establish and mitigate potential vulnerabilities or flaws.
This may be notably helpful for figuring out and mitigating zero-day vulnerabilities, that are vulnerabilities which can be unknown to the producer or developer and haven’t but been patched.
Reverse engineering could be a difficult and sophisticated talent to grasp. Nonetheless, it may be a helpful instrument for safety professionals seeking to establish and mitigate potential vulnerabilities in software program purposes and techniques.
You may additionally be excited about studying about the most effective NetFlow analyzers and collector instruments on your community.

