Cyber safety is essentially the most regarding subject as cyber threats and assaults are on the rise.
Attackers are actually utilizing extra subtle strategies to assault the techniques. People, small companies or massive organizations are all affected. Thus, all these firms, be they IT or non-IT firms, have understood the significance of cyber safety and targeted on taking all potential measures to face cyber threats.
With increasingly cyber threats and hackers in play, organizations and their workers should take a step ahead to cope with this. Since we like to attach every part to the web, this additionally will increase the prospect of vulnerabilities, breaches and defects.
Gone are the times when passwords had been sufficient to guard the system and its information. All of us need to shield our private {and professional} information, which is why cybersecurity is what it is advisable know to make sure information safety.
So let’s discuss defining the time period Cyber Safety….
What’s Cyber Safety?
Cyber safety is the method and strategies concerned in defending delicate information, laptop techniques, networks and software program purposes from cyber assaults. The cyberattacks are normal terminology overlaying a variety of subjects, however a few of the fashionable ones are:
- Tampering with techniques and information saved in them
- useful resource exploitation
- Unauthorized entry to the focused system and entry to delicate data
- Interfering with the conventional operation of the corporate and its processes
- Utilizing ransomware assaults to encrypt information and extort cash from victims
The assaults are actually turning into extra progressive and complicated and might disrupt safety and hacking techniques. So it’s a large problem for each enterprise and safety analyst to beat this problem and battle again with these assaults.
To grasp the necessity for cybersecurity measures and their practices, let’s take a short take a look at the kinds of threats and assaults.
ransomware
Ransomware is a file encrypting software program program that makes use of a singular, strong encryption algorithm to encrypt the recordsdata on the goal system.

The authors of the Ransomware risk generate a singular decryption key for every of the victims and retailer it on a distant server. Thus, customers can’t entry their recordsdata by any software.
The creators of the ransomware reap the benefits of this and demand a big ransom from victims with a purpose to present the decryption code or decrypt the info. However such assaults don’t assure information restoration even after the ransom is paid.
Botnet assaults
Botnets had been initially designed to carry out particular duties inside a bunch.
It’s outlined as a community or group of units linked to the identical community to carry out a activity. However that is now utilized by dangerous actors and hackers who attempt to entry the community and inject malicious code or malware to disrupt its operation. A number of the botnet assaults embrace:
- Distributed Denial of Service (DDoS) assaults
- Spreading spam emails
- Stealing confidential data
Botnet assaults are typically carried out towards large-scale firms and organizations due to their large information entry. This assault permits the hackers to regulate many units and compromise them because of their evil motives.
Social Engineering Assaults
Social engineering is now a standard tactic utilized by cybercriminals to gather delicate data from customers.

It will possibly trick you by displaying enticing commercials, costs and big provides and asking you to enter your private data and checking account data. Any data you enter there might be cloned and used for monetary fraud, identification fraud, and so forth.
It’s value saying one thing concerning the ZEUS virus which has been energetic since 2007 and is used as a social engineering assault methodology to steal victims’ banking data. Along with monetary losses, social engineering assaults also can obtain different damaging threats to the affected system.
Hijacking cryptocurrencies
Hijacking cryptocurrency is the brand new addition to this cyber world.

As digital currencies and mining develop into fashionable, so do cybercriminals. They’ve found their evil benefit in cryptocurrency mining, which entails advanced computer systems in mining digital currencies akin to Bitcoin, Ethereum, Monero, Litecoin, and so forth.
Cryptocurrency traders and merchants are the smooth targets for this assault.
Cryptocurrency hijacking is also called “Cryptojacking”. It’s a program designed to silently inject mining codes into the system. Thus, the hacker silently makes use of the CPU, GPU, and energy sources of the attacked system to mine for the cryptocurrency.
The approach is principally used to mine Monero cash. Since mining is a fancy course of, it consumes essentially the most CPU sources, which impacts the efficiency of the system. It is usually carried out underneath all of your bills so the sufferer may find yourself with an enormous electrical energy and web invoice.
It additionally shortens the lifetime of the affected system.
Phishing
Phishing is a fraudulent act of sending spam emails by impersonating that they arrive from a respectable supply.

Such emails have a robust topic line with attachments akin to an bill, job postings, nice provides from respected transport firms, or different necessary emails from senior firm officers.
The phishing assaults are the most typical cyber-attacks that goal to steal delicate information akin to login credentials, bank card numbers, checking account particulars, and so forth. To keep away from this, it is advisable study phishing electronic mail campaigns and their preventive measures. You may as well use electronic mail filtering applied sciences to forestall this assault.
As well as, 2019 will search for the potential of biometric assaults, AI assaults and IoT assaults. Many firms and organizations are witnessing large-scale cyber assaults, and there’s no finish to it. Regardless of ongoing safety analyzes and updates, the emergence of cyber threats is constant. So it is value educating your self on the fundamentals of cybersecurity and its implementation.
The Key Idea of Cyber Safety?
Cyber safety is a really broad time period however it’s primarily based on three elementary ideas often known as ‘The CIA triad“.
It consists of confidentiality, integrity and availability. This mannequin is designed to information the group in cybersecurity coverage within the area of knowledge safety.
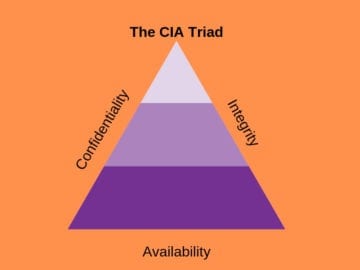
Confidentiality
It defines the principles that prohibit entry to data. Confidentiality consists of the measures to forestall cyber attackers and hackers from accessing delicate data.
In a company, individuals can or can’t entry data primarily based on its class by authorizing the suitable individuals in a division. In addition they obtain correct coaching on sharing data and securing their accounts with robust passwords.

They’ll change the way in which information is processed inside a company to make sure information safety. There are a number of methods to make sure confidentiality, akin to two-factor authentication, information encryption, information classification, biometric authentication, and safety tokens.
Integrity
This ensures that the info is constant, correct and dependable over the interval in query. It implies that the info should not be altered, altered, deleted or accessed illegally inside the transit.
Correct measures should be taken in a company to make sure its security. File permissions and consumer entry management are the measures that management the info breach. Instruments and applied sciences should even be applied to detect any change or breach within the information. A number of organizations use a checksum and even a cryptographic checksum to confirm the integrity of information.
To deal with information loss, unintentional deletion and even cyber-attacks, common backups must be made. Cloud backups are actually essentially the most trusted answer for this.
Availability
The supply of all needed elements, akin to {hardware}, software program, networks, units and safety tools, should be maintained and upgraded. This ensures clean operation and entry to information with none disruption. Additionally ensures fixed communication between the elements by offering enough bandwidth.

It additionally implies that you go for additional safety tools in case of any calamities or bottlenecks. Instruments akin to firewalls, catastrophe restoration plans, proxy servers and backup answer ought to make sure that DoS assaults will be handled.
For a profitable method, it should undergo a number of layers of safety to make sure the safety of each a part of CyberSecurity. Particularly in the case of computer systems, {hardware} techniques, networks, software program applications and the shared information.
Conclusion
Attaining an efficient cybersecurity method in a company requires the individuals, processes, computer systems, networks and know-how of a company, massive or small, to be equally accountable. If all elements complement one another, it’s fairly potential to withstand the intense cyber threats and assaults.
If you happen to’re curious to be taught extra, take a look at this entire cybersecurity course.

