AWS Secrets and techniques Supervisor permits you to securely retailer all of your credentials, information, passwords, and different secrets and techniques.
Cyberattacks are rising quickly throughout the globe, aiming to steal confidential data and cash and leaving organizations devastated.
Because of this there’s a want to make use of robust companies like Secrets and techniques Supervisor that may shield your information.
On this article, I’ll talk about AWS Secrets and techniques Supervisor and the way useful it may be for you.
Let’s begin!
What Is AWS Secrets and techniques Supervisor?
AWS Secrets and techniques Supervisor is a device that helps customers handle, rotate, and retrieve their secrets and techniques, like passwords, API keys, database and software credentials, and so forth., all through every one’s lifecycle.
A secret right here could be a confidential, priceless piece of details about your group that you simply need to retailer securely. It may be a credential like a password and a consumer identify, an OAuth token, an AWS credential, SSK keys, encryption keys, certificates and personal keys, and extra.
The primary purpose of AWS Secrets and techniques Supervisor is to handle and safeguard your information used for accessing IT assets, companies, purposes, and methods. It shops and manages secrets and techniques and information in a centralized place, making it simpler for reliable customers to entry them with out requiring complicated code.
AWS Secrets and techniques Supervisor permits you to rotate secrets and techniques throughout varied AWS companies like Redshift, RDS, and DocumentDB. This allows all of the keys and database credentials to be up to date continuously throughout these companies. As well as, you may rotate secrets and techniques on demand or on a schedule utilizing the device’s in-built console, AWS SDK, or AWS CLI.
Furthermore, AWS Secrets and techniques Supervisor gives higher information management and robust encryption for information safety. It additionally permits you to monitor your protected data and audit it with the assistance of varied integrations accessible.
Its greatest customers are giant companies with respect to enterprise measurement and software program firms with respect to business sort.
AWS Secrets and techniques Supervisor: Options
#1. Secret Storage and Administration
Not solely storage, however you can too handle your secrets and techniques simply with Secrets and techniques Supervisor. To handle information on the platform, you may carry out varied actions along with your information:
- Making a secret and database
- Modifying a secret
- Discovering a secret
- Deleting a secret that you simply now not require
- Restoring a secret that you’ve misplaced or deleted
- Replicating a secret to a different AWS area
- Selling a replicated secret to a given standalone secret inside AWS Secrets and techniques Supervisor
You’ll be able to retailer your credentials on the platform after creating your account in Amazon Aurora, Amazon RDS, Amazon DocumentDB, or Amazon Redshift. You are able to do it by utilizing the Secrets and techniques Supervisor console, AWS SDK, or AWS CLI.
#2. Robust Safety

AWS Secrets and techniques Supervisor makes use of robust encryption to safeguard all of your secrets and techniques from unauthorized customers. It encrypts your secrets and techniques utilizing AWS Key Administration Service (KMS) keys.
Secrets and techniques Supervisor makes use of AWS Id and Entry Administration (IAM) to permit customers to entry their secrets and techniques securely. It gives superior entry controls and authentication.
- Authentication is used for verifying the identification of the consumer making the request. And the identification is completed by means of a sign-in course of requiring multi-factor authentication (MFA) tokens, entry keys, and passwords.
- Entry management is used to make sure that authorised customers can solely carry out sure operations on secrets and techniques.
Aside from these, Secrets and techniques Supervisor makes use of insurance policies defining which customers can entry what assets and take which actions on these secrets and techniques or assets. It allows you to use AWS IAM Roles Wherever and acquire momentary credentials for safety in IAM for servers, purposes, containers, and different workloads operating out of AWS.
As well as, you may allow the identical IAM roles and insurance policies in your workloads that you’ve created for AWS apps to entry your assets in each AWS and on-premises units (like software servers).
#3. Secrets and techniques Rotation

AWS Secrets and techniques Supervisor permits you to rotate secrets and techniques on a schedule or on demand with out disrupting or redeploying your lively purposes.
Right here, secrets and techniques rotation refers back to the strategy of updating a company’s secrets and techniques periodically. So, while you rotate a given secret, you will want to replace the info or credentials within the secret in addition to the service or database. As well as, it allows you to automate secret rotation and save time by establishing and automating secrets and techniques rotation by way of the console and AWS CLI to save lots of time.
To replace a secret, AWS Secret Supervisor leverages the perform AWS Lambda and calls it based mostly on the set-up schedule. For this, you will want to arrange a selected schedule to allow rotation after a sure interval, like 90 days or 30 days. It can be performed by making a cron expression.
Furthermore, the Secrets and techniques Supervisor can label the model of the key throughout rotation by utilizing staging labels. It will probably name a perform many instances throughout rotation by giving totally different parameters.
Right here’s how one can rotate a secret:
- Create the key’s new model. It will probably have a brand new username and password together with extra secret information.
- Change the present credentials within the service or database. Doing this can match new credentials within the new secret model. Primarily based on the rotation technique you might be implementing, a brand new consumer will likely be created having the identical entry permissions as that of the present consumer.
- Take a look at the newly created secret model by permitting it to entry the service or database. Primarily based on the entry sort that your purposes require; you may embrace learn and write entry.
- Carry out the rotation by shifting the brand new model from the previous model to the brand new secret model. Retain the previous model and add it to the earlier model to keep away from dropping the key altogether.
#4. Secret Monitoring

Since breaches and inefficiencies can occur at any time, it’s essential to control your secrets and techniques and take wanted actions when there’s nonetheless time. AWS Secrets and techniques Supervisor permits you to monitor your information utilizing monitoring instruments and instantly report in case one thing goes incorrect.
It is possible for you to to make use of logs to analyze any sudden modifications or utilization. If discovered, you can too roll again the undesirable modifications and retrieve the earlier model. As well as, you may configure automated checks to detect any try and secret deletion or inappropriate secret utilization.
Right here’s what you’re going to get with secret monitoring:
- Log occasions utilizing AWS CloudTrail: AWS CloudTrail can document API calls as occasions from the console for secret rotation and deletion. It should present you recorded occasions from the final 90 days. You may as well arrange CloudTrail to ship log recordsdata on to Amazon S3 bucket from a number of AWS areas and accounts.
- Monitor utilizing CloudWatch: With CloudWatch, you may simply monitor your secrets and techniques by letting it acquire and course of uncooked information into real-time, readable metrics. The info will likely be saved for 15 months to gauge your service or app’s efficiency.
- Match the occasions utilizing EventBridge: With EventsBridge, it’s potential to match occasions from AWS CloudTrail log recordsdata. For this, configure the riles on the lookout for these occasions and ship a brand new occasion to take motion to a goal.
- Monitor scheduled secrets and techniques for deletion: By combining Amazon CloudWatch Logs, Easy Notification Service (SNS), and CloudTrail, you may arrange alarms to inform in case of any unauthorized try and delete a secret.
Upon receiving an alarm, you should have the time to assume whether or not you actually need to get it deleted or cease deletion. Alternatively, you may permit a consumer to make use of a brand new secret and supply them with entry permissions.
#5. Integrations
AWS Secrets and techniques Supervisor integrates with loads of different Amazon and AWS instruments. The listing consists of Alexa for Enterprise, AWS App2Container, App Runner, Amazon AppFlow, AWS AppConfig, Amazon Athena, Amazon DocumentDB, AWS DataSync, AWS CodeBuild, Amazon ElasticCache, Amazon EMR, AWS Elemental Reside, Amazon QuickSight, Amazon Redshift, AWS Migration Hub, Amazon RDS, and extra.
Why Use AWS Secrets and techniques Supervisor

Enhanced Safety Posture
Secrets and techniques Supervisor allows you to improve your group’s safety posture because you don’t want any hard-coded credentials in your software’s supply code. By storing your credentials within the Secrets and techniques Supervisor, you may keep away from security-related compromises by somebody who can entry the app or its parts.
Catastrophe Restoration
A catastrophe can knock in your door at any time, similar to a cyber breach. This can lead you to lose your essential data, passwords, and different credentials and information. Or, you may lose your information as a consequence of unintentional deletion.
Utilizing the device, you may change your hard-coded credentials with a name within the runtime to the AWS Secrets and techniques Supervisor in an effort to dynamically retrieve your credentials when in want.
Lowered Dangers

Secrets and techniques Supervisor allows you to configure a rotation schedule in order that the secrets and techniques can rotate mechanically when the time comes. This fashion, you may change your long-term secrets and techniques with short-term secrets and techniques, which helps cut back the dangers of safety compromises.
As well as, rotating credentials doesn’t require software updates or modifying software purchasers because you received’t retailer your credentials with the appliance.
Assembly Compliance Necessities
Wanting on the rising safety and privateness dangers, regulatory our bodies like GDPR and HIPAA require organizations to stick to their compliance commonplace to make sure they’re dealing with buyer and enterprise information securely. Thus, use solely an software or service that’s protected and compliant with relevant rules.
AWS Secrets and techniques Supervisor, you may monitor your secrets and techniques to detect any safety vulnerability or threat that may compromise your information and take motion beforehand. This basically safeguards your corporation and buyer data, which is very essential to sustaining compliance. You may as well higher put together your self for audits by documenting all the pieces.
Moreover, you may leverage AWS Configs to evaluate your secrets and techniques and the way their compliance along with your group’s inside insurance policies, rules, and business pointers. It allows you to outline compliance necessities and inside controls for secrets and techniques and determine secrets and techniques that aren’t compliant.
Higher Controls

You’ll get higher management of your secrets and techniques, methods, and different information with fine-grained insurance policies and entry controls. AWS IAM will guarantee the fitting particular person has the fitting degree of entry permissions to the fitting assets. Directors can create or delete accounts, permit or limit entry to customers, add or take away members, and carry out many actions based mostly on the wants and conditions.
AWS Secrets and techniques Supervisor: How you can Setup and Use it
Right here’s how one can arrange and use AWS Secrets and techniques Supervisor:
- Arrange your AWS account by coming into the required particulars.
- Log in to your AWS account
- Go to the AWS Secrets and techniques Supervisor console
- Find the “Retailer a brand new secret” possibility and click on on it to create and retailer your secret.
How you can Create and Retailer a New Secret
For making a secret in Secrets and techniques Supervisor, you require permission from the SecretsManagerReadWrite managed insurance policies. When a secret is created, Secret Supervisor will generate a CloudTrail log entry.
Comply with the under steps to retailer your entry tokens, API keys, and credentials in AWS Secrets and techniques Supervisor:
1. Open the AWS Secrets and techniques Supervisor console
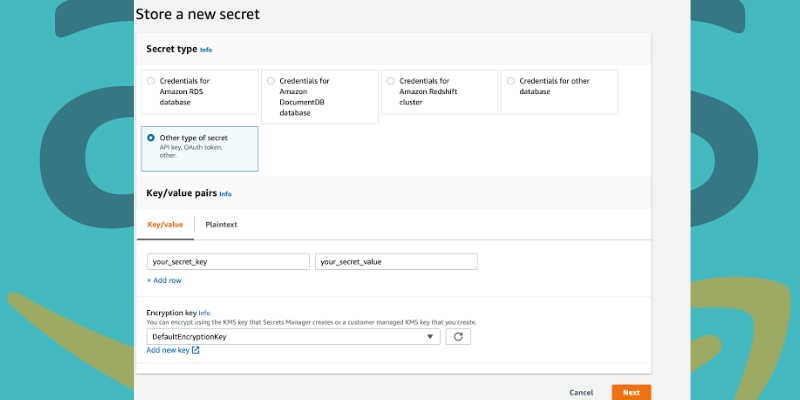
2. Click on on “Retailer a brand new secret”.
You will see that the web page “Select secret sort”. Subsequent, carry out the next steps:
- Choose “Different sort of secret” for the kind of secret you need to create.
- You will notice Key/worth pairs. Enter a secret in key/worth pairs in JSON. Or, choose the tab Plaintext and enter your secret in a format of your alternative. It’s potential to retailer secrets and techniques as much as 65536 bytes.
- Choose the AWS KMS key utilized by Secret Supervisor to encrypt the key worth. Largely, you may go for
aws/secretsmanagerfor utilizing the managed key. It incurs no price. - To entry a secret from a unique AWS account or use your KMS key to allow rotation or implement a coverage to this key, choose “Add new key” or choose a key that’s buyer managed from the given listing. Nevertheless, a customer-manged secret is paid.
- Choose “Subsequent”
3. From the web page “Configuration secret”,
- Enter a Secret identify and its description. The identify will need to have 1-512 Unicode characters.
- You’ll be able to add tags to a secret from the Tags part. You may as well embrace a useful resource coverage by selecting “Edit permissions”.
- As well as, it’s additionally potential to copy a secret to a unique AWS area by selecting “Replicate secret”. These steps are non-compulsory.
- Select “Subsequent”
4. If you need, you may allow computerized rotation from the web page “Configuration rotation”. This step can also be non-compulsory. Select subsequent.
5. Overview the key’s particulars from the “Overview” web page and choose “retailer”. And you might be performed; the Secret Supervisor will return to the secrets and techniques listing. You need to see the newly added secret there; if not, refresh.
Aside from the console, you can too add a secret by means of AWS SDK and AWS CLI.
AWS Secrets and techniques Supervisor vs. AWS Parameter Retailer
AWS Parameter Retailer is an software administration device by AWS Techniques Supervisor (SSM) that enables customers to create a key-value parameter, which may save an software’s configurations, credentials, product keys, and customized surroundings variables.
Then again, AWS Secrets and techniques Supervisor is a service that allows you to create, retailer, handle, retrieve, and rotate credentials, keys, API tokens, and so forth.
Each these companies have related interfaces the place it’s simple to declare your key-value pairs for secrets and techniques and parameters. Nevertheless, they do on the next grounds:
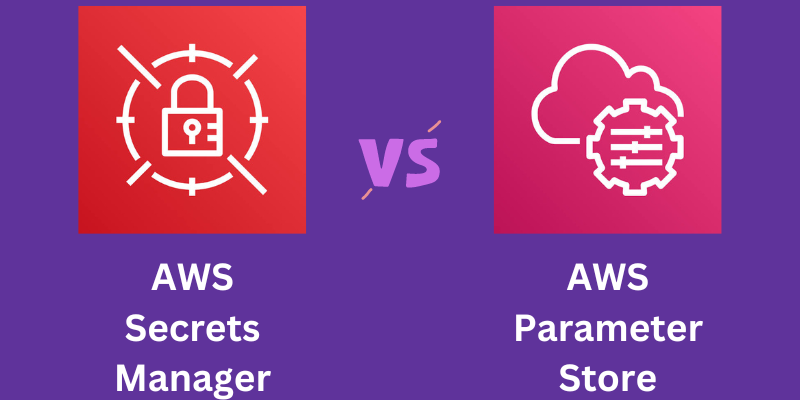
| AWS Secrets and techniques Supervisor | AWS Parameters Retailer | |
| Storage measurement | Shops as much as 10 kb of secret measurement | Shops as much as 4096 characters or 4 kb for an entry and may go as much as 8 kb for superior parameters |
| Limits | Can retailer 500k secrets and techniques/area/account | Can retailer 10,000 commonplace parameters/area/account |
| Value | It’s paid, costing $0.40/secret/month | Free for traditional parameters and prices $0.05/10,000 API requires superior parameters |
| Rotation | Affords computerized rotation for any secret at any time and could be configured | You will have to write down a perform by your self to replace credentials |
| Cross-account entry | Sure | No |
| Cross-region replication | Sure | No |
| Kind of credentials | It’s for confidential information that wants encryption, so, restricted use circumstances. | Wider use case since you may retailer extra sorts of credentials together with app configuration variables like product keys, URLs, and so forth. |
Conclusion
Whether or not you might be from a small, medium-sized, or giant enterprise, you need to use AWS Secrets and techniques Supervisor to create and retailer your secrets and techniques. It gives enhanced safety, privateness, entry controls, options, and capabilities to safeguard your secrets and techniques from unauthorized entry.
You may additionally discover easy methods to carry out AWS Safety Scanning and configuration monitoring.

