Risk actors leverage internet browsers to infiltrate customers’ computer systems or company networks. They achieve this by creating malicious web sites that may set up malware on customers’ computer systems and trigger irreparable injury. However with browser isolation, you’ll be able to safeguard your internet shopping exercise to stop frequent web-based assaults.
What’s browser isolation expertise precisely, how does it work, and what are the advantages of utilizing browser isolation? Let’s discover out.
What Is Browser Isolation?
Browser isolation, also referred to as internet isolation, is a safety resolution that comprises your shopping exercise in an remoted setting like a digital machine, sandbox, or the cloud, barricading your gadget from the inherent threat of on-line shopping.
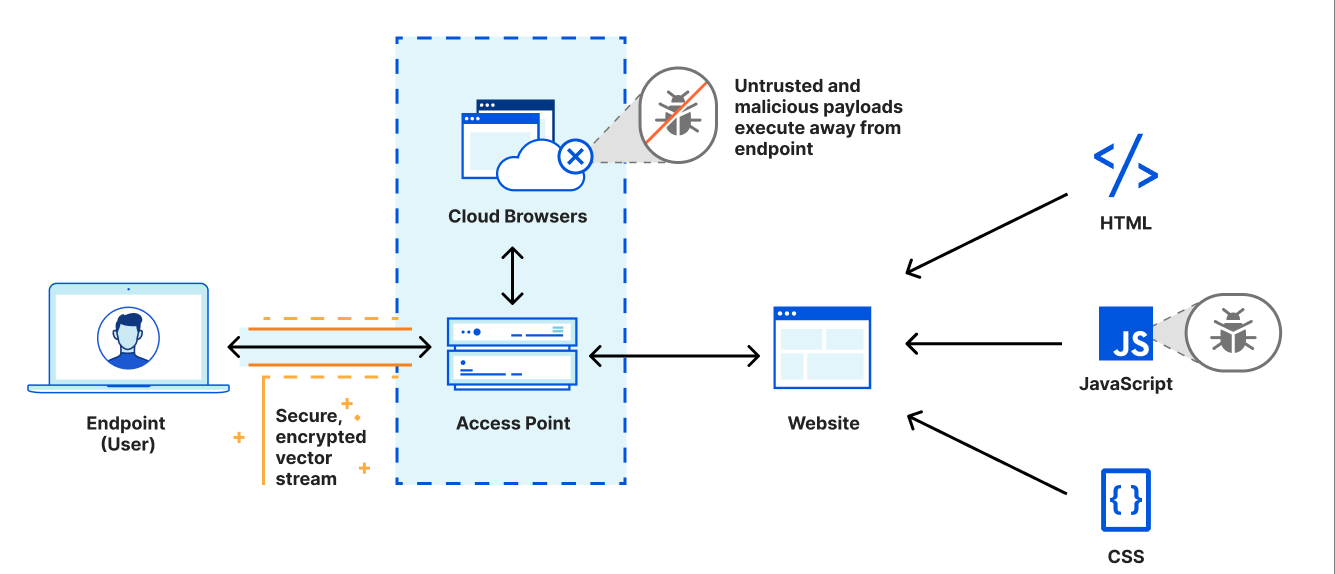
When you kind an internet site, your browser hundreds content material and code from the web site’s server and executes code inside your browser. The method appears innocent, however it isn’t.
A risk actor can create a malicious web site or internet app riddled with dangerous code and share its hyperlink with you through phishing assaults. Whenever you attain the malicious website by clicking on the hyperlink, the malicious code will mechanically get downloaded in your gadget, infecting your gadget or community.
Browser isolation supplies your gadget with an extra layer of safety by protecting your shopping exercise confined to an remoted setting.
How Browser Isolation Works

Browser isolation works by confining shopping exercise to an remoted setting. This merely means your internet browser runs in its personal setting and doesn’t work together together with your gadget’s working system.
In the event you are available in contact with malware, the malware doesn’t go previous the remoted setting. And your gadget stays protected from malware or different web-based threats.
There are alternative ways internet isolation applied sciences can work, however the typical course of entails the next:
- Take away your shopping exercise out of your system and run it in a digital setting or the cloud.
- Mechanically delete the browser setting when you finish your shopping session. This ensures that malicious content material or hidden malicious code discovered throughout a session is worn out on the finish of a session.
- Whenever you open the safe digital browser once more, you’re going to get a clear browser free from malware or malicious code.
Browser isolation helps customers browse the net as they sometimes do whereas defending their gadget and company community from malware and different on-line threats.
And the perfect half is the customers is not going to see any distinction. They’ll see as if the browser is operating on their native computer systems.
Totally different Sorts of Browser Isolation
Listed here are the three forms of browser isolation strategies you must learn about.
#1. Distant Browser Isolation
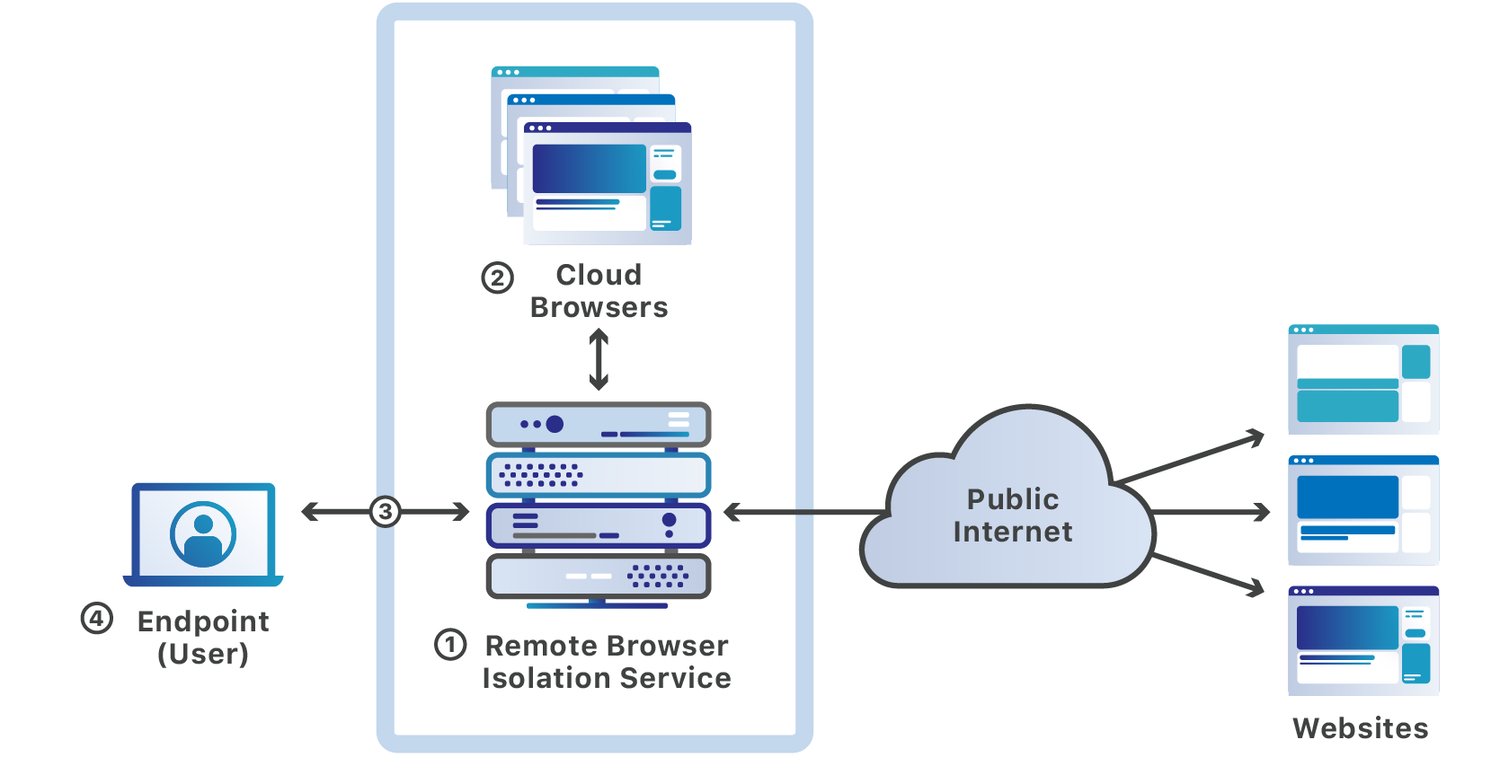
Within the distant browser isolation (RBI) expertise, a consumer’s shopping session is hosted on a distant server, away from the consumer’s gadget and company community.
As RBI hundreds internet pages and executes related JavaScript code on a cloud server, a corporation’s inside community stays protected against malicious content material, malicious downloads, and different web-based threats.
Now the query comes-how does distant browser isolation work?
The next are key methods how distant browser isolation expertise works:
- The supplier providing distant browser isolation companies sends customers movies or photos of their shopping exercise. This technique is also referred to as “pixel pushing.” The tip customers obtain solely pixels, not any code, so it protects the customers’ units from malicious code execution.
- On this technique, distant browser isolation distributors open and rewrite internet pages to take away malicious internet content material earlier than sending it to the customers. This method is known as the DOM mirroring approach.
#2. On-Premises Browser Isolation
On-premises browser isolation expertise defends customers the identical manner as distant or cloud-hosted browser isolation does. However the distinction is shopping exercise is hosted on the servers managed by the organizations.
The disadvantage of on-premises browser isolation is that organizations should present their very own servers for browser isolation, which may be pricey.
Additionally, isolation normally occurs throughout the group’s firewall. This implies finish customers’ units are protected against malicious JavaScript, however organizations’ inside networks are at all times in danger.
Due to this fact, choosing distant or cloud-based browser isolation is an clever alternative.
#3. Shopper-Aspect Browser Isolation
Within the client-side browser isolation technique, internet pages/internet apps load, and related JavaScript code executes on the customers’ units however in an remoted setting, utilizing sandboxing or virtualization.
The core idea of browser isolation is predicated on bodily stopping dangerous code from downloading on the system. However client-side browser isolation really hundreds doubtlessly malicious content material on the consumer’s gadget, although on a digital machine. So it nonetheless poses dangers to units and networks. That is the rationale why corporations favor to not implement client-side browser isolation.
Why You Want an Remoted Browser Setting

Most internet browsers mechanically execute all JavaScript related to internet pages. This implies risk actors can make use of malicious JavaScript to infiltrate programs and networks.
Listed here are frequent threats web customers can mitigate by implementing browser isolation expertise.
#2. Drive-By Obtain Assaults
Risk actors typically exploit browser vulnerabilities to put in malicious code on customers’ units. Many web sites serving malicious advertisements can even obtain malicious code to customers’ programs. However with browser isolation, malicious code shall be downloaded on an remoted setting (distant server) separated from the native machine.
#3. Clickjacking
In easy phrases, a clickjacking assault tips customers into considering that they’re clicking on one factor, however they’re clicking on one other factor in actuality. Risk actors make use of clickjacking to ship internet site visitors to rip-off web sites, generate faux advert income, or obtain malware on customers’ units.
Virtualized internet browsers are sometimes outfitted with expertise to dam a lot of the malicious code served utilizing promoting and third-party websites.
#4. Malvertising
Risk actors inject malicious code into reliable advert networks. And when the malicious advertisements are displayed on the customers’ computer systems, the code shall be executed, infecting the customers’ units. However with browser isolation, there no native code execution.
As all code execution occurs in an remoted setting, typically on the cloud, the native units keep protected against browser-based assaults.
#5. Cross-Website Scripting
Risk actors inject malicious code into widespread web sites to put in malware on the units of web customers who go to these web sites.
Having browser isolation expertise carried out in your gadget can preserve your gadget protected. It is because the code execution will occur in an remoted setting on the cloud, away out of your gadget.
#6. Phishing Redirection Assaults

Hackers create phishing web sites to put in malware, steal login credentials, and swindle cash.
You go to a phishing web site considering that you’re on a reliable web site. However, in actuality, the web site was arrange by a risk actor with malicious intent.
Most reputed browser isolation distributors incorporate state-of-the-art internet safety expertise to dam zero-day phishing web sites. This prevents you from visiting a phishing web site.
#7. On-Path Browser Assaults
Risk actors can view customers’ internet shopping periods, distort content material, and impersonate the consumer by means of an on-path browser assault. As no path to entry company assets from the browser exists in browser isolation, it will possibly scale back the injury attributable to such an assault.
Advantages of Browser Isolation
Listed here are the important thing advantages of implementing browser isolation in your organization.
Defend From Net-Based mostly Assaults

Retaining your shopping periods away out of your gadget can forestall web-based assaults like malware, drive-by obtain, or clickjacking.
Save Time for IT Directors
Historically, IT directors are prone to blacklist malicious web sites to stop staff from accessing these web sites. Additionally, IT directors might require to watch alerts when customers open doubtlessly unsafe web sites knowingly or inadvertently.
Browser isolation takes this burden off their shoulders. As malicious code can’t go previous the remoted setting, there is no such thing as a have to implement web-filtering options.
Enhance Productiveness
Typically, organizations restrict internet entry attributable to safety causes. For instance, staff might not obtain PDF information or different forms of paperwork because of the threat of hidden malware in such information.
As staff can’t entry the net freely, it will possibly hamper their productiveness. With browser isolation, staff can safely entry the net with out restrictions. This, in flip, improves their productiveness.
Defend From Phishing

Browser isolation protects customers from phishing assaults. As all web-based emails are opened on a distant server, malicious attachments or malicious code don’t attain the native units.
What’s extra, main browser isolation distributors use state-of-the-art expertise to dam phishing web sites and phishing emails.
Present Conduct Analytics
By implementing browser isolation expertise, corporations can acquire insights into staff’ internet actions. In consequence, they’ll determine insider threats and implement corrective measures.
Cut back the Want for Complicated Endpoint Safety Options
As browser isolation takes shopping periods on the cloud or in a digital setting, it prevents malware and different web-based threats from focusing on the customers’ units.
Consequently, corporations might not have to implement complicated endpoint safety options to guard their endpoints.
The right way to Decide the Greatest Browser Isolation Software
When selecting a browser isolation resolution, you’ll want to make sure that it has the next options:
- It is best to be capable to combine it with widespread e-mail purchasers to supply phishing safety. This may enable all hyperlinks in your emails to open in an remoted setting on the cloud, making certain malicious code can’t be downloaded in your gadget.
- Your chosen browser isolation resolution ought to will let you configure read-only internet pages for suspicious or unknown internet pages. This function will assist shield customers from credential theft.
- It ought to will let you management and handle company shopping insurance policies primarily based on consumer location, URL class, and extra.
- The answer should comply with the zero-trust structure and give you a quick shopping expertise.
Additionally, you must go for an answer that means that you can disable or allow downloading and importing.
Some reputed browser isolation options are Apozy, Silo, Kasm Workspaces, Seraphic Net Safety, and Puffin Cloud Isolation.
Browser Isolation and Zero Belief Safety Structure
The zero belief mannequin is a safety strategy that focuses on verifying the whole lot, trusting none.
In different phrases, you shouldn’t belief customers, functions, and internet site visitors by default. A web site a consumer has already loaded on their system 500 instances safely can infect their system after they load it 501 instances.
So, to implement the idea of zero belief safety, you could make sure that each web site ought to be checked for malicious content material each time it’s loaded in your system to maintain your system safe. And browser isolation helps you do this.
Browser isolation prevents web-based assaults by protecting shopping exercise contained in an remoted setting as a substitute of relying in your staff to depict protected on-line habits.
Challenges of Browser Isolation Know-how
Browser isolation expertise enhances cybersecurity in organizations. However you’ll want to contemplate some computing and user-experience drawbacks earlier than committing to a browser isolation vendor.
In-Ample Safety

Within the DOM mirroring isolation, sure forms of malicious content material from internet pages are filtered out earlier than sending the rest of the net pages to the customers.
Nevertheless, refined phishing pages might conceal malicious content material as different forms of content material the browser isolation supplier permits. This will open the customers’ units to varied web-based assaults.
Restricted Web site Assist
When a browser isolation resolution removes malicious content material from internet pages, as occurs within the DOM mirroring approach, it will possibly break sure internet pages. In consequence, the net pages might not render appropriately or in any respect.
Web site homeowners additionally often make modifications to their web sites that may break DOM reconstruction performance.
Gradual Velocity On account of Latency
Whenever you implement distant browser isolation, your entire staff’ internet site visitors shall be routed by means of the cloud-based system earlier than being forwarded to them. In consequence, there may be some latency within the connection, degrading the consumer expertise.
Inadequate Finances
Implementing distant browser isolation requires corporations’ internet site visitors to be routed by means of and analyzed on the cloud. And streaming encrypted pixels of internet pages to the endpoints calls for tons of bandwidth and processing energy. So many organizations can discover it costly to deploy these options throughout all staff.
Conclusion
Net browsers are an indispensable instrument to entry the net. However conventional internet browsers can’t give you optimum safety from web-based assaults, corresponding to phishing, malware, clickjacking, and far more. So you must begin utilizing a browser isolation resolution in your group to safeguard your knowledge and programs.
Even for those who don’t work in an expert setting, you’ll be able to reap the identical safety advantages from utilizing browser isolation. In any case, hackers don’t discriminate relating to focusing on individuals.
You might also learn in regards to the final information to securing Google Chrome.

