Cloud safety posture administration supplies a method to repeatedly monitor the cloud setting, present visibility, and establish and deal with vulnerabilities whereas predicting potential dangers.
Securing a cloud setting in the present day is tough resulting from its dynamic nature and the way it connects and disconnects to tons of of networks and different assets. Lack of enough visibility might result in unnoticed misconfigurations and different safety flaws that attackers can exploit and achieve unauthorized entry to the infrastructure.
Normally, incorrect and insecure configurations enhance the assault floor, making it simpler for criminals to assault. Ultimately, this results in the publicity of delicate or confidential data, non-compliance fines, and monetary and fame losses, and different dangers.
Ideally, a Cloud Safety Posture Administration (CSPM) deployment ensures that the cloud setting’s safety aligns with greatest practices and set guidelines and expectations.
What Is Cloud Safety Posture Administration (CSPM)?
Cloud Safety Posture Administration (CSPM) is a set of instruments and practices that allow organizations to evaluate the cloud and establish and resolve misconfigurations, compliance violations, and different safety dangers.
Whereas some cloud service suppliers akin to Amazon AWS, Google Cloud, Microsoft, and others have inbuilt CSPM capabilities, organizations on different platforms that don’t supply these ought to contemplate third-party instruments.
The options play a significant position in cloud safety by figuring out, remediating, or alerting IT groups on safety misconfigurations, dangers, non-compliance and different vulnerabilities. Some instruments present automated detection and remediation of flaws.
In addition to detecting and mitigating dangers, a CSPM software supplies steady monitoring and visibility into the group’s cloud safety posture. Moreover, some instruments present suggestions for hardening safety.
Why Is Cloud Safety Posture Administration Essential?
With the cloud comprising a variety of various applied sciences and elements, it turns into tough for organizations to maintain observe of all the pieces, particularly if they don’t have the proper instruments.
Any group utilizing cloud providers ought to think about using a CSPM software. Particularly, that is important for organizations with important workloads, in extremely regulated industries, and people with a number of cloud providers accounts.
Advantages of utilizing CSPM embody:
- Performing steady scanning and figuring out the safety posture in actual time.
- Permits a corporation to achieve steady visibility throughout the whole cloud infrastructure.
- Computerized detection and remediation of misconfigurations and compliance points
- Performing compliance benchmarking and audits to make sure that the group is following greatest practices.
Regardless of the flexibleness and productiveness that the cloud infrastructure supplies, it suffers from a variety of safety challenges, particularly when misconfiguration and different unhealthy practices enhance the assault floor. To handle these, organizations ought to deploy CSPM instruments to supply visibility and establish and remediate the dangers.
A typical CSPM software will repeatedly monitor the cloud infrastructure and generate an alert at any time when it detects a difficulty. Relying on the issue, the software could remediate the chance mechanically.
In any other case, a immediate alert additionally permits the safety, builders, or different groups to rectify the issue in good time. Moreover, a CSPM allows organizations to establish and deal with any gaps which will exist between the current and the specified states of their cloud setting.
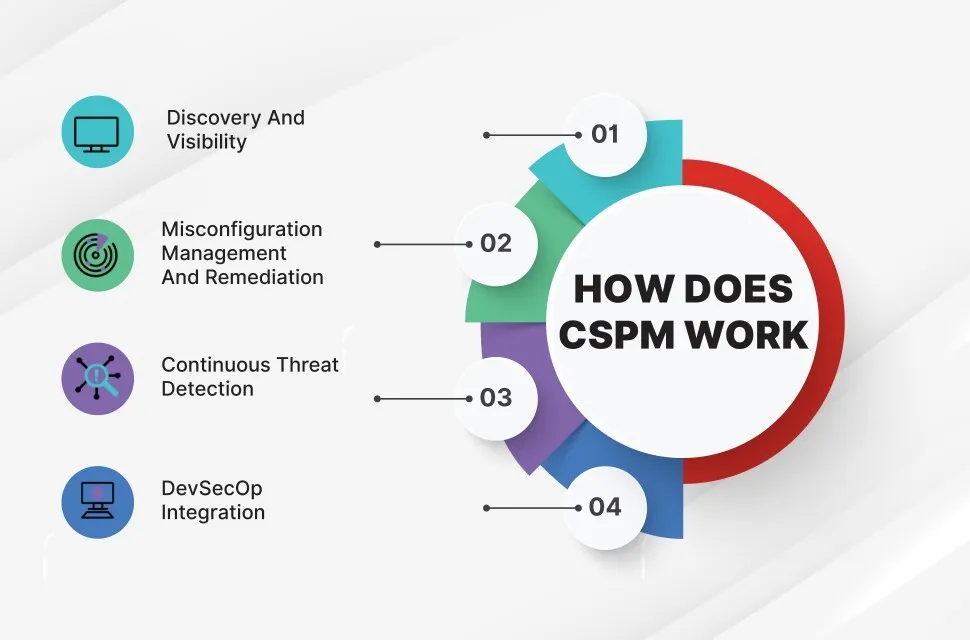
How Does CSPM Work?
A CSPM resolution supplies steady monitoring and visualization of the cloud infrastructure to allow the invention and classification of assorted cloud elements and assess present and potential dangers.
Most instruments evaluate lively insurance policies and configurations in opposition to a set baseline to establish drifts and dangers. Additional, some rule-based CSPM options work as per the set guidelines.
Alternatively, some options use machine studying to detect modifications within the applied sciences and person conduct after which modify how they evaluate.
A typical CSPM has the next most important capabilities:
- Repeatedly monitor the cloud setting and providers and supply full visibility of the elements and configurations.
- Benchmark the cloud configurations and insurance policies in opposition to a set of acceptable tips.
- Detect misconfigurations and coverage modifications.
- Establish present, new and potential threats.
- Right misconfigurations primarily based on pre-built guidelines and business requirements. This helps to cut back dangers resulting from human errors that would end in incorrect configurations.
Though the CSPM helps to handle a variety of misconfiguration and compliance points, they might differ in how they operate. Some help automated remediation in actual time.
Nevertheless, automated remediation could differ from one software to a different. Others help custom-made automation. Moreover, some are particular to sure cloud environments, akin to Azure, AWS, or one other service.
Some CSPM options present automated and steady monitoring, visibility, menace detection, and remediation. Relying on the answer, it could resolve the dangers mechanically, ship alerts, and make suggestions and different capabilities.
What Is a Safety Misconfiguration and Why Does It Happen?
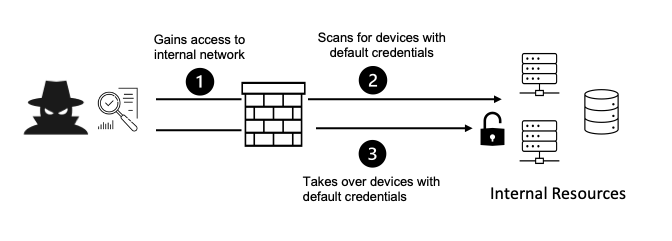
Safety misconfiguration is when the safety controls are configured wrongly or left insecure, akin to with default settings. This creates vulnerabilities, safety gaps, and glitches that go away the networks, techniques, and knowledge uncovered and vulnerable to numerous cyberattacks.

Misconfigurations happen primarily resulting from human error when groups fail to implement safety settings accurately or by no means.
Typical unhealthy practices embody utilizing the default settings, poor or no documentation of the configuration modifications, granting extreme or dangerous permissions, incorrect settings by the service supplier, and extra.
It additionally happens resulting from enabling pointless options, accounts, ports, providers, and different elements that enhance the assault floor.
Different the explanation why misconfigurations happen embody the next:
- Displaying delicate data on error messages
- Poor, weak, or lack of encryption
- Misconfigured safety instruments, unprotected platforms, directories, and recordsdata.
- Unsuitable {hardware} configurations, akin to utilizing default IP deal with, {hardware} and software program credentials, and settings.
Find out how to Implement CSPM in Your Group?
A CSPM lets you repeatedly assess your cloud setting and establish and deal with safety gaps. Nevertheless, implementing an efficient CSPM resolution requires correct planning, technique, and time. As a result of completely different cloud environments and aims, the method could differ from one group to the opposite.
In addition to the proper software alternative, the groups ought to comply with the perfect practices when implementing the answer. And there are a number of elements to contemplate.
Identical to some other monetary dedication, the safety groups should outline the aims of the CSPM along with getting the approval of the senior administration. Afterward, they need to take the next steps.
- Outline the aims, such because the dangers you wish to detect and resolve. Moreover, establish and interact the related groups to supervise the deployment.
- Establish the proper CSPM resolution, and use the preconfigured or your customized guidelines to detect the misconfigurations and different vulnerabilities.
- Set up tips on how to consider or assess the cloud environments.
- Repeatedly scan your cloud setting and belongings to establish and deal with safety dangers, together with those who modifications within the cloud setting could introduce.
- Consider the outcomes and set up the important areas to prioritize the remediation. Some instruments could assist to evaluate the severity of the dangers it detects and prioritize these to resolve first.
- Resolve detected dangers mechanically or manually. Additionally, you can configure the software to inform related groups to take motion.
- Recurrently repeat the method and fine-tune it to handle modifications that would have occurred within the ever-evolving cloud environments.
How a CSPM Software Supplies Visibility of Cloud Infrastructure?
Most organizations could not know the quantity and varieties of their cloud assets, these operating, and the way their configurations. Normally, the shortage of visibility into their cloud setting could result in operating numerous providers with a number of misconfigurations.
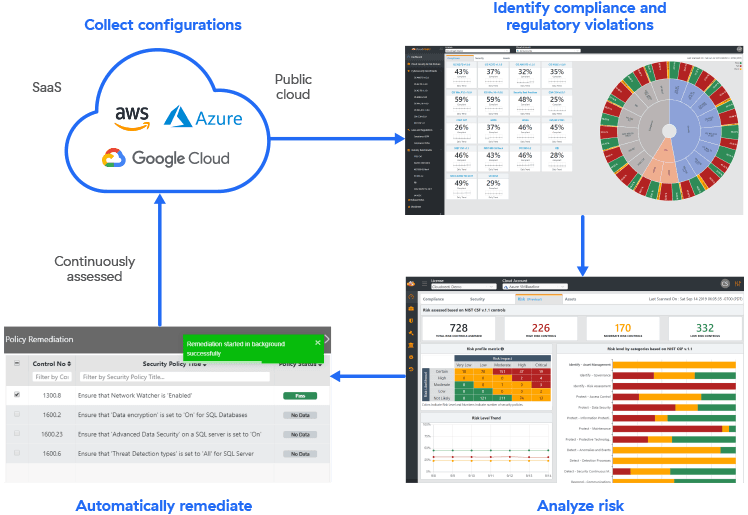
A typical CSPM software repeatedly scans the cloud setting to supply visibility into the safety posture. Because it does this, it discovers the belongings, providers, and different cloud assets whereas assessing the safety by checking for misconfigurations and different vulnerabilities.
Typically, the software visualizes the belongings and helps the organizations to find and perceive community interconnections, providers, workloads, pathways to knowledge, and different assets. This enables groups to establish misconfigurations, safety vulnerabilities, unused belongings, and providers, in addition to verify the integrity of just lately put in {hardware} or software program techniques, and many others.
For instance, the CSPM software discovers cloud belongings akin to digital machines, Amazon S3 buckets, and different assets. It then supplies the visibility of the cloud setting, together with its belongings, safety configurations, compliance, and dangers. Additionally, the visibility permits the groups to search out and deal with blind spots.
Challenges of Cloud Safety Posture Administration
Though the CAPM instruments present a number of safety advantages, in addition they have numerous disadvantages. These embody:
- Some CSPM instruments with out vulnerability scanning options depend on different options. And this could complicate the deployment and response.
- Lack of enough expertise to deploy and preserve the CSPM resolution.
- Computerized remediation might end in issues. Typically, resolving issues mechanically is quicker and extra environment friendly if completed proper. Nevertheless, some points could require handbook intervention.
- In observe, most CSPM instruments don’t proactively cease ransomware, malware, and different assaults. Mitigating an assault could take a number of hours, which might imply extra harm. Moreover, the software could not detect threats propagating laterally throughout the cloud setting.
- Some CSPM capabilities are normally accessible as merchandise of the cloud service supplier or options of different cloud-based instruments, akin to cloud workload safety platform (CWPP) and Cloud Entry Safety Dealer (CASB). Sadly, these cloud-first instruments don’t present on-premise safety.
Studying Sources
Under are some programs and books that may enable you perceive extra about cloud safety posture administration and different practices
#1. Test Level Bounce Begin: CloudGuard Posture Administration: Udemy
Test Level Bounce Begin: CloudGuard Posture Administration is a free, easy, and informative on-line course provided by Udemy. You solely want the identical fundamental laptop expertise to know the CSPM.
#2. Container Safety & Cloud Safety utilizing AQUA – Udemy
The Container Safety & Cloud Safety utilizing AQUA course will enable you find out about container photographs, their safety, and tips on how to scan them with Aqua safety options.
Additionally, you will learn to detect misconfigurations in an AWS platform, about cloud safety posture administration, and tips on how to implement it utilizing the Aqua resolution.
#3. Cloud Safety Posture Administration Full Self-Evaluation Information
The guide guides you on tips on how to assess your safety posture, visualize your cloud assets and decide who’s utilizing them. It additionally comes with digital instruments that allow you to evaluate the safety measures, insurance policies, and different options in place.
| Preview | Product | Score | Worth | |
|---|---|---|---|---|
|
|
Cloud Safety Posture Administration Full Self-Evaluation Information | $81.41 | Purchase on Amazon |
Additional, you’ll have a look at previous assaults and challenges your group goes by means of to guard the workloads. Moreover, you’ll assess how safe is your functions and knowledge, who has entry to them, and who is permitted to take sure actions.
The CSPM self-assessment information will enable you set up your CSPM challenges and tips on how to overcome them and defend your cloud setting.
#4. Cloud Safety Technical Reference Structure
The guide supplies reference structure the CISA, OBD, and different safety businesses advocate.
| Preview | Product | Score | Worth | |
|---|---|---|---|---|
|
|
Cloud Safety Technical Reference Structure | $9.10 | Purchase on Amazon |
It reveals that organizations and businesses migrating their workloads to the cloud ought to defend their knowledge assortment and reporting utilizing numerous instruments, together with the CSPM.
Remaining Phrases
The cloud infrastructure repeatedly modifications, and organizations with out enough visibility could expose their setting to assaults. As such, it’s important to recurrently audit the safety settings, configurations, and controls to make sure compliance, even after including a brand new element. The groups ought to then deal with any drift within the configuration as quickly as doable.
A method of attaining that is by utilizing a dependable cloud safety posture administration resolution. The software supplies visibility that permits organizations to guard their cloud belongings in opposition to non-compliance and misconfigurations, akin to outdated safety updates, incorrect permissions, unencrypted knowledge, expired encryption keys, and many others.
Subsequent, try tips on how to discover internet server vulnerabilities with the Nikto scanner.


