Cyber Kill Chain is a safety mannequin developed by Lockheed Martin in 2011 that outlines the steps of a cyber assault, serving to to know, establish and defend threats.
Should you’re curious, Lockheed Martin is a worldwide aerospace, protection, weapons and safety firm.
And the Cyber Kill Chain (CKC) is likely one of the fashionable safety fashions that cybersecurity specialists seek advice from to kind a technique and defend organizations in opposition to cyberattacks.
Why is Cyber Kill Chain Necessary in Cyber Safety?

Let’s be sincere; Cyber safety will not be that easy. It typically sounds easy and convincing whenever you give finish customers the ideas they should keep secure on the web.
Nevertheless, when coping with an actual cyber assault, organizations have to know loads of technical issues about it. You may’t count on a corporation to defend itself in opposition to cyber assaults with just a few safety suggestions, are you able to?
So a framework (or a mannequin) is required to put the muse for understanding cyber-attacks and having the ability to defend in opposition to them accordingly.
Cyber Kill Chain is a standard safety mannequin that serves as a basis to assist perceive the phases of a cyber assault. It contains seven phases, which we are going to focus on beneath.
Position of Cyber Kill Chain in Cyber Safety

Cyber Kill Chain isn’t just restricted to offering insights a few cyber assault, but additionally helps organizations discover methods to detect attackers, forestall entry from unauthorized customers, mitigate an lively assault and cease an attacker throughout the community .
This helps organizations and cybersecurity specialists develop a technique that may assist with that.
Cyber Kill Chain alone can’t assure all the things, there are a number of issues that matter outdoors the community or internally in a corporation, and this mannequin doesn’t embrace all of that.
Phases of the Cyber Kill Chain
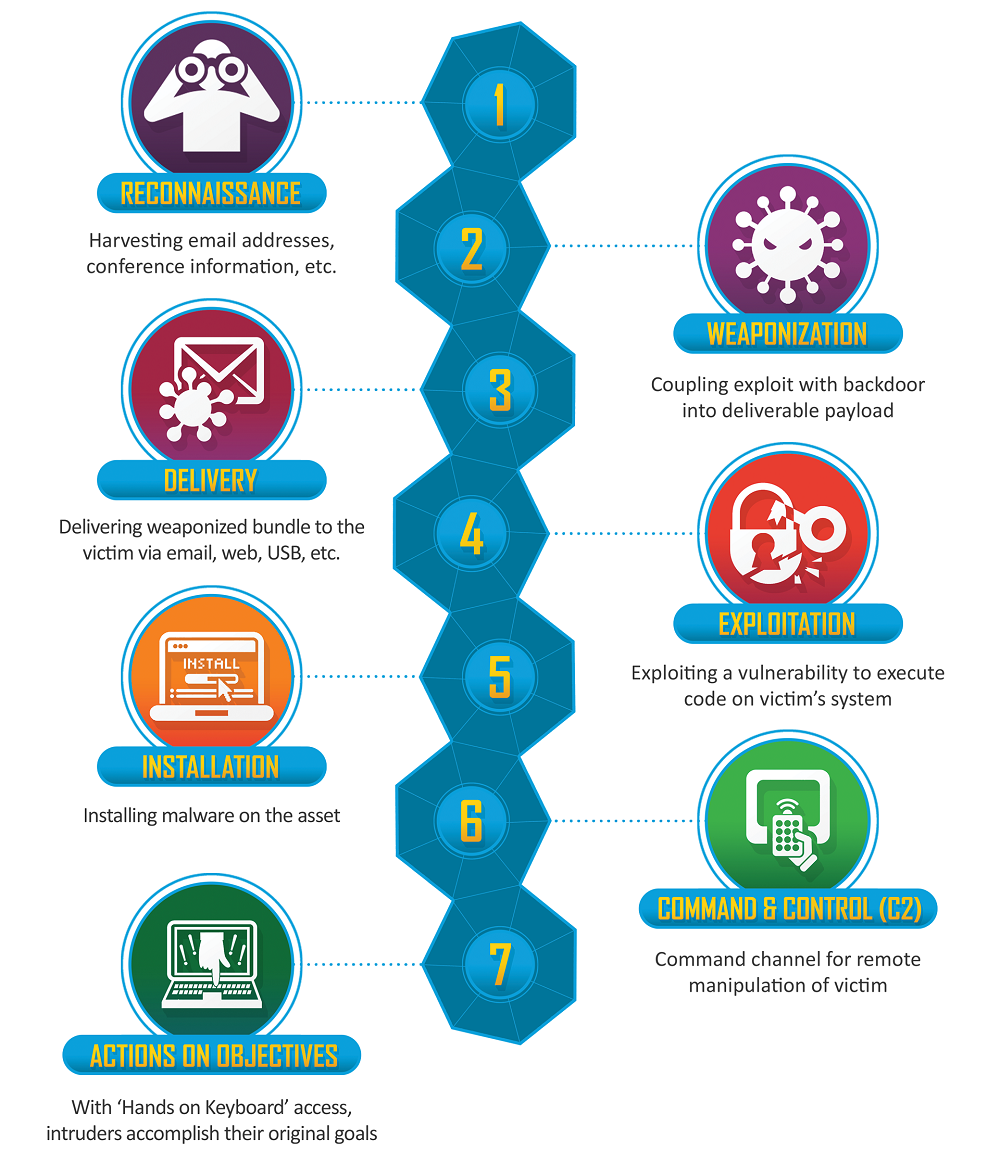
The CKC framework consists of seven steps to explain a cyber assault. They’re:
- Reconnaissance
- Armament
- Supply
- Exploitation
- Set up
- Command and management
- Motion
#1. Reconnaissance
Reconnaissance is the primary stage of the Cyber Kill Chain and is all about info gathering.
The attacker gathers insights right into a community’s entry factors and weaknesses and scans for vulnerabilities. Not solely restricted to figuring out them, but additionally amassing electronic mail addresses, addresses and different software-related information that may assist devise malicious methods to hold out the assault.
The extra particulars the attacker has, the extra influential the assault may be. This surveillance section of the assault can happen offline or on-line. So it is probably not attainable for anybody to get a suspicion of a malicious actor at this stage.
To handle this section, organizations and their workers should concentrate on privateness, whether or not limiting bodily location to approved customers or asking all related customers to not share delicate private info on-line.
For instance, everybody ought to use privateness instruments to guard their on-line identification.
#2. Armament

Right here, the malicious actor creates the weapon i.e. the malware or device for use within the cyber-attack.
Generally they use present instruments or modify them in keeping with the objective to arrange for supply, which is the subsequent step.
The weapon created for the assault will rely upon the goal of the malicious actor. For instance, some desire to disrupt providers, others need to steal information, and nonetheless others need to demand a ransom for conserving delicate information.
The weapon may be something that aligns with that goal.
#3. Supply
This is likely one of the essential phases the place the attacker’s luck begins.
If the supply succeeds, the malware penetrates and begins its work. And if it fails, all methods for the assault come to an finish.
The attacker makes use of instruments or media to ship the malware. For instance, malicious electronic mail attachments, phishing emails handy over credentials, a textual content message fooling a consumer into giving consumer authorization, and the like.
Naturally, the malicious actor makes use of all the data from the surveillance section to persuade the goal of a message or hyperlink, in order that he clicks by means of it with out considering.
If the group and its workers are conscious of phishing assaults and different widespread cyber-attacks, their implementation shall be tough.
#4. Exploitation

The attacker is aware of the issues and has penetrated the sufferer’s system.
Now the identified vulnerability shall be exploited to execute the delivered malicious code. On this course of, the attacker may acquire extra perception into the system and uncover vulnerabilities.
Any susceptible system related to the community is vulnerable to being compromised.
#5. Set up
As soon as the attacker has scanned for all the issues, the attacker will concentrate on putting in the malware and introduce different malicious code to take advantage of numerous different issues that have been initially unknown.
In different phrases, infiltration is accomplished at this stage the place the attacker penetrates deep into the compromised community.
#6. Command and management
As soon as the infiltration is full, it’s time for the malicious actor to take management of the compromised system or community.
They’ll select to trace and monitor info remotely or wreak havoc to disrupt the system and providers. These may be within the type of DDoS assaults or including a again door that permits them to comfortably enter the system with out anybody noticing.
#7. Motion on aims
Relying on the goal of the assault, the malicious actor performs the ultimate blow to realize the goal.
They’ll encrypt and ransom information, infect the system to unfold malware, disrupt providers, or steal information to leak or modify it. Many related prospects embrace for the actions.
How Does Cyber Kill Chain Assist Shield In opposition to Assaults?

Understanding how attackers penetrate your community and techniques may also help organizations and their workers defend in opposition to cyberattacks.
For instance, with Cyber Kill Chain, one understands that vulnerabilities in a community may also help the attacker to infiltrate rapidly. Subsequently, organizations can think about using Endpoint Detection and Response instruments so as to add early detection strategies to their cybersecurity technique.
Equally, you possibly can select to make use of a firewall to guard the cloud infrastructure and cloud-based DDoS safety providers to step up the safety recreation.
To not overlook: VPNs will also be used to safe enterprise in an organization.
Organizations can use the Cyber Kill Chain mannequin successfully by selecting options that handle every stage of a cyber assault.
Is a cyber kill chain sufficient?
Sure and no.
As I discussed earlier, Cyber Kill Chain solely covers among the fundamentals of a cyber assault. And even when a corporation defends itself in opposition to it, it’s already a fantastic victory.
Though some cybersecurity specialists have expanded the mannequin with an eighth stage.
The eighth stage contains monetization:
This section explains how the attackers monetize a profitable assault. Be it the ransom request or using cryptocurrency, the group should additionally roll up its sleeves to deal with such conditions.
Total, the mannequin is taken into account considerably out of date as innovation within the digital world progresses. Cyberattacks at the moment are extra complicated, though the fundamental rules stay the identical. For instance, the CKC framework doesn’t record all forms of assaults, however limits itself to malware.
Furthermore, it doesn’t cope with threats from inside, as a rogue worker may have penalties for the group.
On condition that cyber-attacks have gotten more and more complicated because of the mixture of cloud and synthetic intelligence, different fashions will also be referred to, resembling MITER ATT&CK and Unified Kill Chain.
It’s also possible to discover one of the best breach and assault simulation instruments to arrange for cyberattacks.

