Scan internet functions for SQLI, RXSS, LFI, RFI, CRLF and 25+ extra with Invincible cloud scanner
The safety of your web site is important to your on-line enterprise. In case your internet/utility servers are misconfigured or not correctly secured, your internet functions might be in danger.
Hundreds of internet sites are hacked daily and up to date analysis by Invicti reveals that the highest 3 hottest vulnerabilities XSS, SQL injection & File recording.
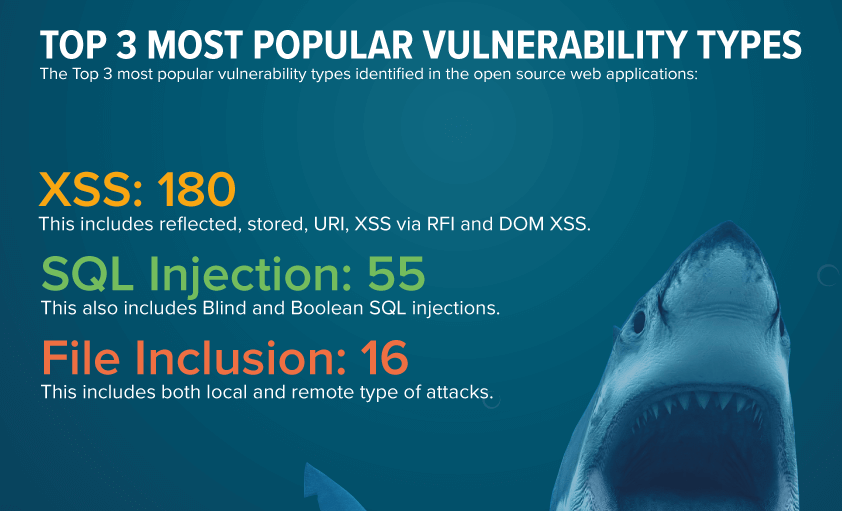
As an internet site proprietor or safety administrator, that you must discover all choices to make sure your on-line enterprise is safe from hackers to keep away from lack of enterprise and status.
On this article, I am going to clarify how you need to use the Invicti cloud to scan your web site for safety vulnerabilities so you possibly can take motion earlier than another person finds them.
The next abbreviations are used beneath:-
- SQLI – SQL Injection
- RXSS – Distant cross-site scripting
- XSS – Cross-Web site Scripting
- LFI – Native File Recording
- RFI – Distant File Recording
- CRLF – Carriage Return and Line Feed
Let’s begin…
Create a TRIAL account or ship an electronic mail to [email protected] in case you are engaged on an Open Supply Venture.
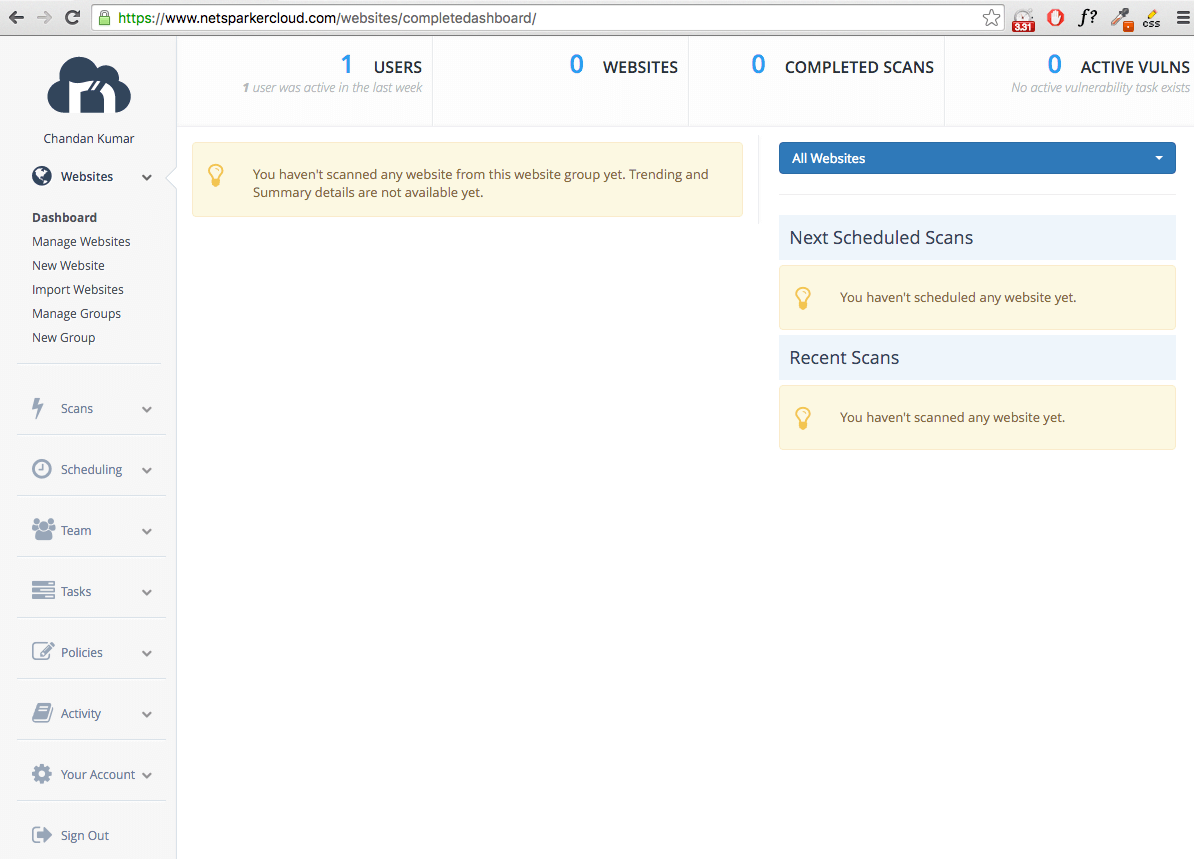
As soon as your account is prepared, log in along with your credentials to Invicti Cloud. You get the attractive dashboard to set your internet URL and begin the scan
- Click on Scans >> New Scan within the left navigation
- Enter your web site particulars and click on No Save

- You will need to confirm possession to forestall misuse. You’ll be able to confirm by way of electronic mail, file add, HTML tag, or DNS file.
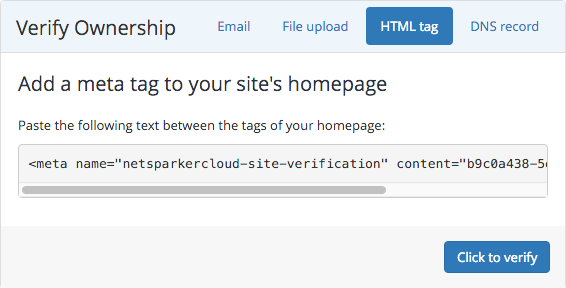
- Select the specified verification methodology and click on Confirm
- Within the subsequent window, you may be given an choice to configure the scan
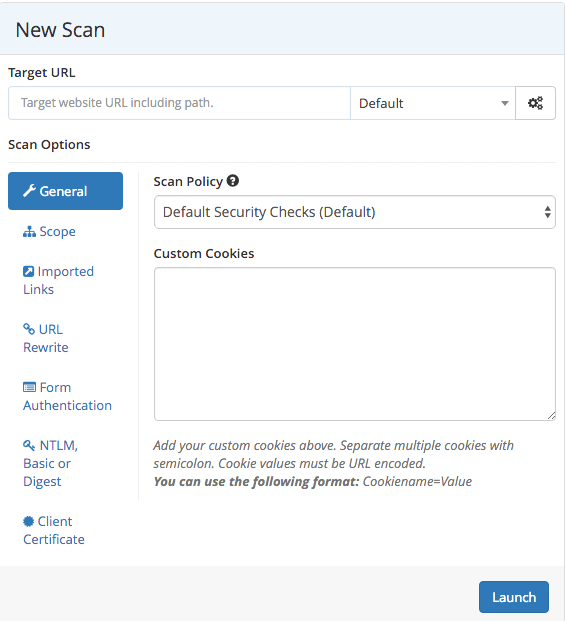
- Examine them out and choose the one you favor.
- Necessary to pick the scope, whether or not you need to scan solely the entered URL or the entire area.

- When you’re achieved with the configuration, click on Begin
- The subsequent display reveals the progress of the scan.
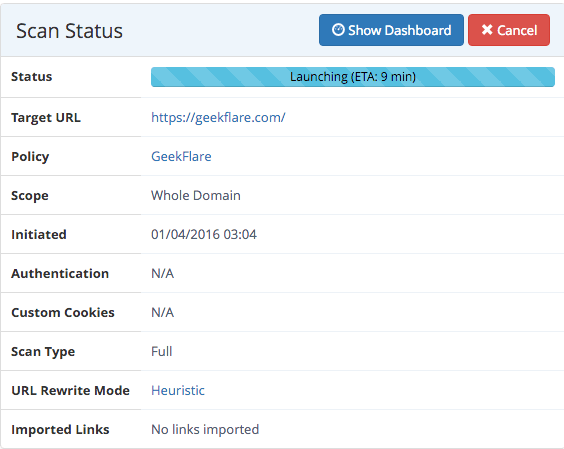
Time for a cup of espresso 🙂
In the meantime, you possibly can try one other FREE on-line safety vulnerability scanner.
As soon as the scan has began, additionally, you will obtain an electronic mail with a hyperlink saying “scan standing view”. So don’t fret for those who shut the browser. You’ll be able to at all times verify your electronic mail and go to a standing web page.

- The scan might take a couple of hours you probably have chosen to scan “Complete Web site”, so please be affected person. As soon as a scan is full, you’ll obtain an electronic mail.
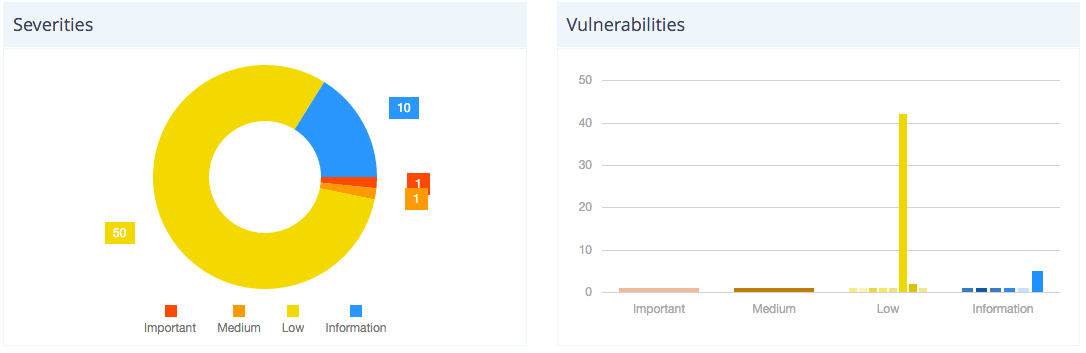
- When logging in, additionally, you will see these particulars within the good dashboard with severity and vulnerabilities which you could take motion on.
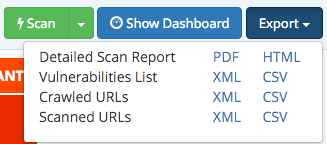
It’s also possible to export the report by following it in XML, CSV, PDF or HTML format.
- Detailed scan report
- Listing of vulnerabilities
- Crawled URLs
- Scanned URLs
That is what the abstract seems like.
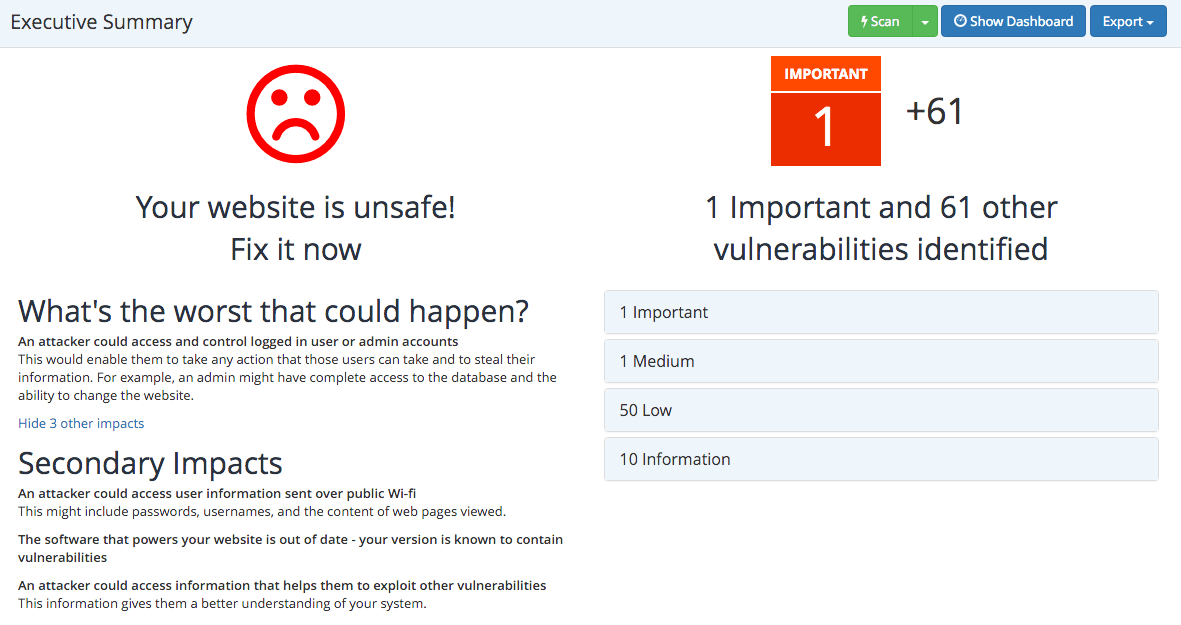
Not good, I want to repair them quickly.
And also you? Have you ever not carried out the scan but? Go forward and examine the vulnerabilities and repair them earlier than malicious events discover your web site and make it unavailable?

