As knowledge flows ceaselessly throughout enterprise networks and techniques, so does the chance of cyber threats. Whereas there are lots of types of cyber assaults, DoS and DDoS are two forms of assaults that operate in a different way by way of scale, execution, and affect however share comparable aims.
We’ll make clear the distinctions between these two forms of cyber assaults that will help you safeguard your techniques.
What’s a DoS Assault?
A Denial of Service DoS assault is an assault that’s carried out on a service aimed toward inflicting a disruption to the conventional operate or denying different customers entry to that service. This could possibly be by sending extra requests to a service than it may well deal with, making it gradual or damaged.
The essence of DoS is to flood a goal system with extra site visitors than it may well deal with, with the only purpose of constructing it inaccessible to its supposed customers. A DoS assault is often carried out on a single machine.
What’s a DDoS Assault?

A Distributed Denial of Service DDoS can also be just like a DoS assault. The distinction, nonetheless, is that DDoS makes use of a group of a number of linked on-line units, also referred to as botnets, to flood a goal system with extreme web site visitors to disrupt its regular operate.
DDoS operate like an surprising site visitors jam clogging the freeway, stopping different autos from reaching their vacation spot on time. An enterprise system prevents reputable site visitors from reaching its vacation spot by crashing the system or overloading it.
Primary Sorts of DDoS Assaults
Varied types of DoS/DDoS assaults present up alongside the development of know-how, however on this part, we are going to have a look at the key types of assaults that exist. Broadly these assaults come within the type of attacking a community’s quantity, protocol, or utility layer.
#1. Quantity-based assaults

Each community/service has an quantity of site visitors it may well deal with at a given interval. Quantity-based assaults purpose to overload a community with a bogus quantity of site visitors, making the community unable to course of any extra site visitors or change into gradual for different customers. Examples of this sort of assault are ICMP and UDP.
#2. Protocol-based assaults
Protocol-based assaults purpose to overpower server assets by sending giant packets to focus on networks and infrastructure administration instruments equivalent to firewalls. These assaults goal the weak point in layers 3 and 4 of the OSI mannequin. SYN flood is a sort of protocol-based assault.
#3. Utility layer assaults
The appliance layer of the OSI mannequin generates the response to a shopper’s HTTP request. An attacker targets layer 7 of the OSI mannequin chargeable for delivering these pages to a consumer by sending a number of requests for a single web page, making the server occupied with the identical request and turns into unattainable to ship the pages.
These assaults are tough to detect as a result of a reputable request can’t be simply differentiated from an attacker’s request. The kind of this assault consists of slowloris assault and an HTTP flood.
Completely different Sorts of DDoS Assaults

#1. UDP assaults
Person Datagram Protocol (UDP) is a sort of connectionless communication with a minimal protocol mechanism used totally on real-time functions the place a delay in receiving knowledge can’t be tolerated, e.g., video conferencing or gaming. These assaults occur when an attacker sends a lot of UDP packets to a goal making the server unable to answer reputable requests.
#2. ICMP flood assaults
Web Management Message Protocol (ICMP) flood assaults are a sort of DoS assault that sends an extreme variety of ICMP echo request packets to a community, resulting in community congestion and wastage of the community bandwidth resulting in a delay in response time for different customers. It might additionally lead to an entire breakdown of the community/service being attacked.
#3. SYN flood assaults
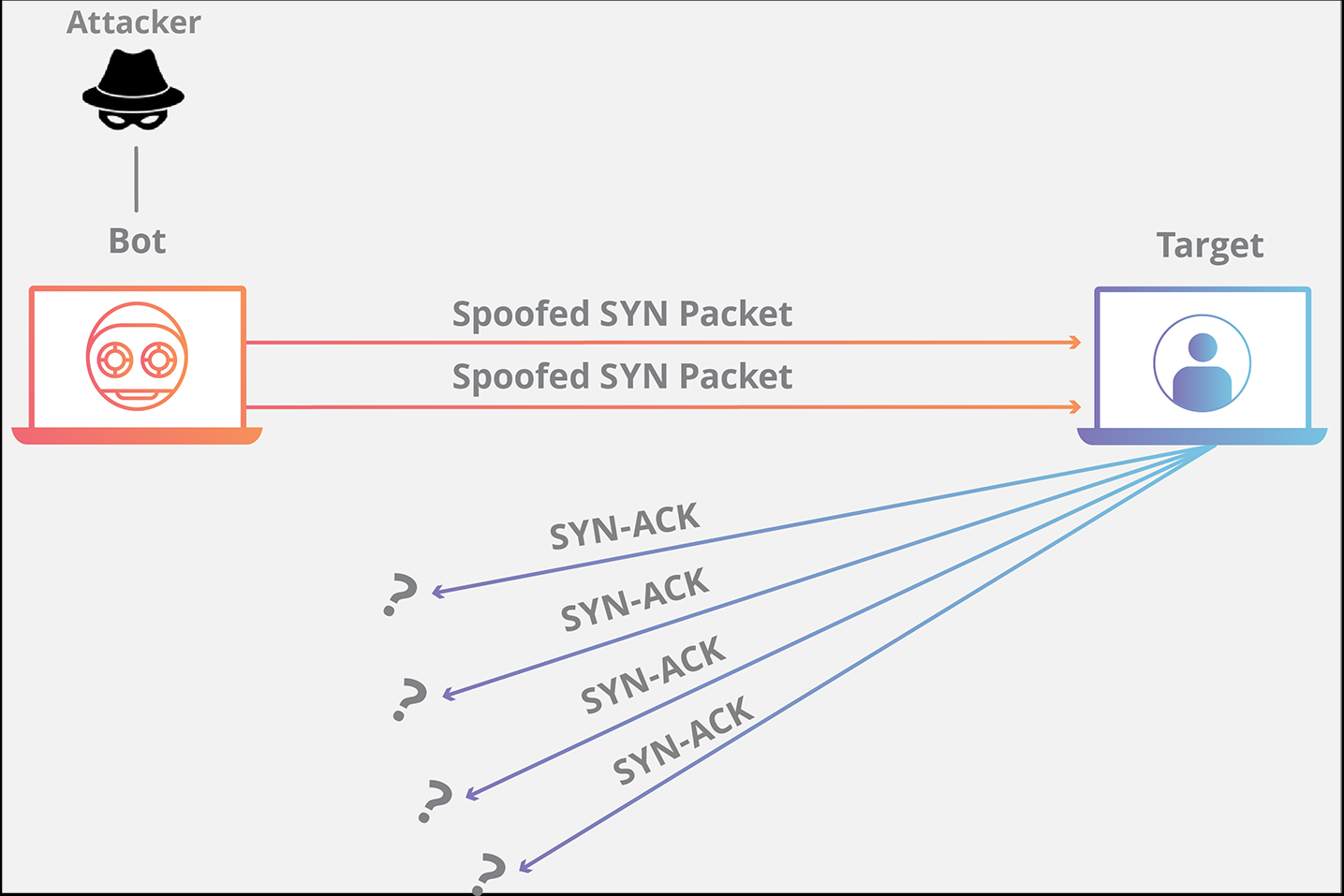
Such a assault will be defined by a waiter in a restaurant. When a buyer locations an order, the waiter delivers the order to the kitchen, after which the kitchen fulfills the client’s order, and the client is served in a great state of affairs.
In an SYN flood assault, a single buyer retains inserting order upon order solely after receiving any of their earlier orders until the kitchen is simply too congested with so many orders and never in a position to fulfill anybody else orders. SYN floods assault exploit weaknesses in TCP connection.
The attacker sends a number of SYN requests however doesn’t reply to any of the SYN-ACK responses making the host repeatedly watch for a response from the request tying up assets till no order request will be made to the host.
#4. HTTP flood Assaults
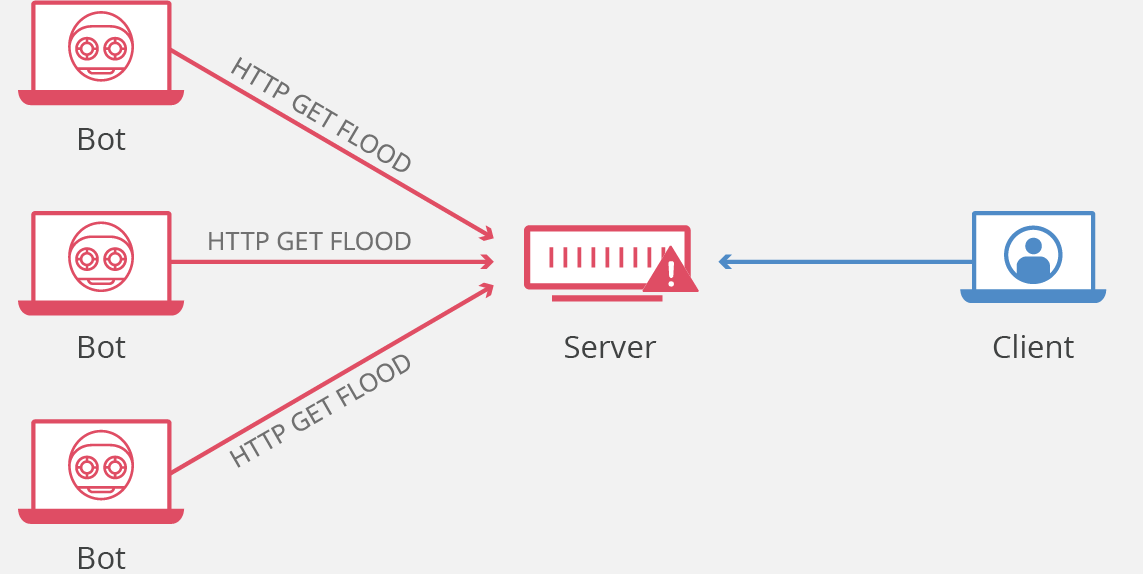
One of many commonest and easiest strategies of this assault is the HTTP flood assault, which is carried out by sending a number of HTTP requests to a server from a distinct IP tackle. The purpose of those assaults is to eat the server’s energy, community bandwidth, and reminiscence with legitimate-looking requests making it inaccessible for precise customers’ site visitors.
#5. Slowloris assault
A slowloris assault is carried out by establishing a number of partial requests to a goal, protecting the server open to the connection, ready for the total request that by no means will get despatched, overflowing the utmost permitted connection allowed, and resulting in a denial of service for different customers.
Different assaults embody ping of dying POD, amplification, teardrop assault, IP fragmentation assault, and flooding assault, amongst others. The aim of this assault is to overload the service/server, limiting it from with the ability to course of reputable requests from reputable customers.
Why do DoS assaults occur?

In contrast to different assaults that target getting knowledge from the server, DoS attacker goals to hinder the server through the use of up its assets, making it unresponsive to reputable customers’ requests.
With extra technological advances, extra companies are serving prospects utilizing the cloud by way of the net. For enterprises to keep up an edge in right now’s market house, it’s virtually indispensable for them to have an online presence. Alternatively, opponents might leverage DDoS assaults to discredit their competitors by shutting down their companies, making them look unreliable.
DoS assaults may be used as ransomware by attackers. Overflooding a enterprise server with irrelevant requests and asking the enterprise to pay a ransom earlier than they name off their assaults and make the server accessible to reputable customers.
Some teams have additionally focused platforms that don’t agree with their ideologies for both political or social causes. Total, DoS assaults don’t have permission to tamper with the information on the server; fairly, they’ll solely shut down the server from being utilized by different customers.
Mitigating DoS/DDoS Assaults

Realizing that there’s a risk of being attacked, companies ought to make sure that they put in measures to make sure that their techniques/servers will not be simply susceptible to this assault with out placing up a combat. Listed below are some measures firms can take to make sure they’re secure.
Monitor your site visitors
Understanding your community site visitors can play an enormous function in mitigating DoS assaults. Each server has a sample of site visitors that it receives. A sudden spike on the excessive aspect, away from the common site visitors patterns, signifies the presence of irregularity, which may be a DoS assault. Understanding your site visitors might provide help to act quick in circumstances like this.
Charge limiting
By limiting the variety of requests that may be despatched to a server/community inside a specific time, DoS assaults will be mitigated. Attackers will often ship a number of requests concurrently to overflood the server. With a fee restrict in place, when the permitted quantity of requests is acquired inside a specific timeframe, the server will mechanically delay the surplus request making it tough for the DoS attacker to overflow the server.
Distributed server
Having distributed server in a distinct area is a worldwide finest apply. It additionally helps mitigate DoS assaults. If an attacker launches a profitable assault on a server, the opposite enterprise servers won’t be affected and might nonetheless service reputable requests. Utilizing a content material supply community to cache servers in numerous areas close to customers additionally serves as a layer of prevention towards DoS assaults.
Put together a DoS/DDoS assault plan

Being ready for any type of assault is essential to lowering the quantity of injury that the assault may cause. Each safety crew ought to have a step-by-step actionable plan on what to do when an incident happens to keep away from searching for options inside an assault. The plan ought to embody what to do, who to go to, find out how to keep reputable requests and so forth.
Monitoring your system
Steady monitoring of the server for any abnormality is essential for all-around security. Actual-time monitoring assist to simply detect assaults on time and tackle them earlier than they escalate. It additionally helps the crew know what common and irregular site visitors is from. Monitoring additionally helps to dam IP addresses sending in malicious requests simply.
Instruments to Stop DoS and DDoS

One other technique of mitigating DoS/DDoS assaults is by leveraging net utility firewall instruments and monitoring techniques which have been constructed to detect and stop the incidence of a profitable assault shortly. These instruments are automated to serve this operate and might present all-around real-time safety.
Sucuri
Sucuri is an online utility firewall (WAF) and intrusion prevention system (IPS) for web sites. Sucuri blocks any type of DoS assault targetted at layers 3, 4, and seven of the OSI mannequin. A few of its key options embody proxy service, DDoS safety, and quick scanning.
Cloudflare
Cloudflare is likely one of the most extremely rated DDoS mitigation instruments. Cloudflare additionally gives content material supply networks CDN in addition to three layers of safety, web site DDoS safety(L7), utility DDoS safety(L4), and community DDoS safety(L3).
Imperva
Imperva WAF is a proxy server that filters all incoming site visitors sends and ensures they’re secure earlier than passing it over to the net server. Proxy service, safety patching, and website availability continuity are among the key options of Imperva WAF.
Stack WAF
Stack WAF is straightforward to arrange and helps with exact menace identification. Stack WAF supplies utility safety, together with web site, APIs, and SaaS merchandise, content material safety, and utility layer DDoS assault safety.
AWS Protect
AWS Protect displays site visitors in real-time by taking a look at move knowledge to detect suspicious site visitors. It additionally makes use of packet filtering and site visitors prioritization to assist management site visitors by the server. It’s price noting that the AWS defend is simply out there throughout the AWS setting.
Now we have reviewed some practices that would assist mitigate a profitable DoD/DDoS assault on a server. You will need to observe that no indicators of threats/abnormalities needs to be dismissed with out being correctly dealt with
DoS vs. DDoS Assaults
DoS and DDoS on the floor stage are rather a lot comparable. On this part, we are going to cowl among the notable variations that distinguish them aside from one another.
| Parameter | DoS | DDoS |
|---|---|---|
| Site visitors | DoS comes from a single origin. Therefore the quantity of site visitors it may well generate is comparatively low in comparison with DDoS | DDoS assault employs a number of bots/techniques, which implies it may well trigger a considerable amount of site visitors from totally different origins concurrently and overflow a server shortly |
| Supply | Single system/bot | A number of techniques/bot on the identical time |
| Mitigation | DoS assaults are simpler to detect and terminate since they arrive from a single origin. | DDoS assaults have a number of origins making it tough to establish the supply of all of the targets and terminate the assault |
| Complexity | Simpler to execute | Requires giant assets and a little bit of technical know-how |
| Pace | Sluggish in comparison with DDoS | DDoS assaults are very quick |
| Impression | Restricted affect | Excessive affect on system/server |
Backside Line
Organizations ought to make sure that the safety of their system is prioritized in each case; a breach/break in companies might result in a possible lack of belief from customers. DoS and DDoS assaults are all unlawful and dangerous to the goal system. Therefore all measures to make sure that these assaults will be detected and managed needs to be taken critically.
You might also discover prime cloud-based DDoS safety for small to enterprise web sites.

