The Nginx net server is used on greater than 30% of the web site worldwide and rising.
Given the proliferation of on-line net threats, one of many challenges for net engineers is to be properly conscious of the best way to harden and safe Nginx.
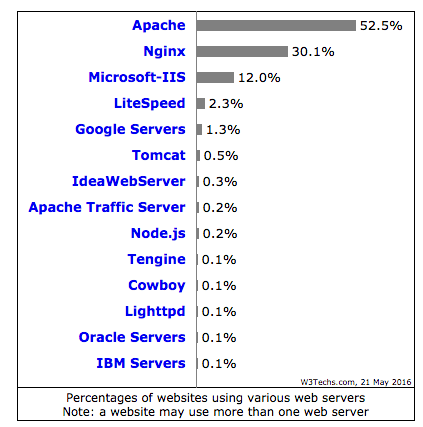
Nginx is understood for its efficiency and light-weight net server/proxy and is used on most of the busiest websites.
- Pinterest.com
- reddit.com
- wordpress.com
- Stackoverflow.com
- Mail.ru
For those who host your net purposes on Nginx and are involved about safety, one of many first stuff you’ll wish to implement is Net Utility Firewall (WAF).
Mod Safety is an Open Supply WAF from Trustwave SpiderLabs and was made out there for Nginx in 2012.
On this handbook I clarify how to try this to obtain, to put in And configure Mod safety with Nginx.
The next demonstration is completed on CentOS hosted with DigitalOcean.
For those who’re new to Nginx, I like to recommend taking this basic course.
Obtain Nginx and ModSecurity
You’ll be able to obtain the nginx straight in your server or in your native PC after which switch it.
- Obtain the most recent model from the hyperlink under
http://nginx.org/en/obtain.html
- For those who obtain straight on the server, you should use wget as under
wget http://nginx.org/obtain/nginx-1.9.15.tar.gz
- Extract them utilizing the gunzip command
gunzip -c nginx-1.9.15.tar.gz | tar xvf –
- You will note that the brand new folder has been created
drwxr-xr-x 8 1001 1001 4096 Apr 19 12:02 nginx-1.9.15
- Obtain the most recent model of Mod Safety from the hyperlink under
https://github.com/SpiderLabs/ModSecurity
- You should utilize under instructions straight from the server
wget https://www.modsecurity.org/tarball/2.9.1/modsecurity-2.9.1.tar.gz
gunzip -c modsecurity-2.9.1.tar.gz | tar xvf –
Let’s set up them
Set up Nginx with Mod Safety
It is very important compile the Nginx and mod safety supply code.
- Log right into a server and be sure you have root privileges.
Comment: in case you are doing it on a model new server, you could want to put in the next libraries.
yum set up gcc make automake autoconf libtool pcre pcre-devel libxml2 libxml2-devel curl curl-devel httpd-devel
First, let’s compile mod safety. Go to modsecurity-2.9.1 folder and use the instructions under.
./configure --enable-standalone-module make
Subsequent oneset up Nginx with mod safety
./configure --add-module=../modsecurity-2.9.1/nginx/modsecurity make make set up
This concludes that Nginx has been put in with Mod Safety and it is time to configure it.
Configure Mod Safety with Nginx
To repeat modsecurity.conf-recommended & unicode.mapping file from the extracted folder containing the ModSecurity supply code downloaded above to the nginx conf folder. You can even use the discover command.
discover / -name modsecurity.conf-recommended discover / -name unicode.mapping
[root@GeekFlare-Lab conf]# cp /choose/nginx/binary/modsecurity-2.9.1/modsecurity.conf-recommended /usr/native/nginx/conf/ [root@GeekFlare-Lab conf]# cp /choose/nginx/binary/modsecurity-2.9.1/ unicode.mapping /usr/native/nginx/conf/ [root@GeekFlare-Lab conf]#
Let’s rename modsecurity.conf-recommended Disagreeable modsecurity.conf
mv modsecurity.conf-recommended modsecurity.conf
- Again up the nginx.conf file
- Open the nginx.conf file and add the next underneath the “location /” directive.
ModSecurityEnabled on; ModSecurityConfig modsecurity.conf;
So it ought to appear like this
location / {
ModSecurityEnabled on;
ModSecurityConfig modsecurity.conf;
}
Now Mod Safety is built-in with Nginx. Restart the Nginx to ensure it runs with out errors.
Let’s confirm…
There are two potential strategies to substantiate that Nginx was compiled with Mod Safety.
First…
Show the compiled module utilizing –V with the nginx executable.
[root@GeekFlare-Lab sbin]# ./nginx -V nginx model: nginx/1.9.15 constructed by gcc 4.4.7 20120313 (Purple Hat 4.4.7-16) (GCC) configure arguments: --add-module=../modsecurity-2.9.1/nginx/modsecurity [root@GeekFlare-Lab sbin]#
Second…
Go to the Logs folder and think about the error file. It is best to see the next
2016/05/21 21:54:51 [notice] 25352#0: ModSecurity for nginx (STABLE)/2.9.1 (http://www.modsecurity.org/) configured. 2016/05/21 21:54:51 [notice] 25352#0: ModSecurity: APR compiled model="1.3.9"; loaded model="1.3.9" 2016/05/21 21:54:51 [notice] 25352#0: ModSecurity: PCRE compiled model="7.8 "; loaded model="7.8 2008-09-05" 2016/05/21 21:54:51 [notice] 25352#0: ModSecurity: LIBXML compiled model="2.7.6"
This concludes that you’ve got efficiently configured ModSecurity with Nginx.
By default, the configuration is in discovery mode solely, which suggests no motion is taken and your net purposes are protected.
In my subsequent article, I defined the best way to configure the OWASP ruleset and allow Mod Safety to guard in opposition to net safety vulnerabilities.

