A information to repair Logjam vulnerability in Apache HTTP and Nginx internet server
Introduction
Logjam vulnerability was discovered on Might 20, 2015 in TLS (EXPORT encryption) libraries by a staff of laptop scientists from CNRS, Inria Nancy-Grand Est, Inria Paris-Rocquencourt, Microsoft Analysis, Johns Hopkins College, College of Michigan, and the College of Pennsylvania: David Adrian, Karthikeyan Bhargavan, Zakir Durumeric, Pierrick Gaudry, Matthew Inexperienced, J. Alex Halderman, Nadia Heninger, Drew Springall, Luke Valenta, Benjamin VanderSloot, Eric Wustrow, Santiago Zanella-Beguelin, and Paul Zimmermann.
The Logjam vulnerability helps the attacker downgrade (man-in-the-middle) TLS connections to 512-bit export-grade cryptography. This helps an attacker learn and modify knowledge despatched over the community connection.
You see, that is harmful as a result of an attacker can learn bank card or delicate info in case your software is susceptible to Logjam. This jogs my memory of the FREAK assault.
Logjak vulnerability can exist in all protocols corresponding to HTTPS, SSH, IPSec and SMTP that use TLS.
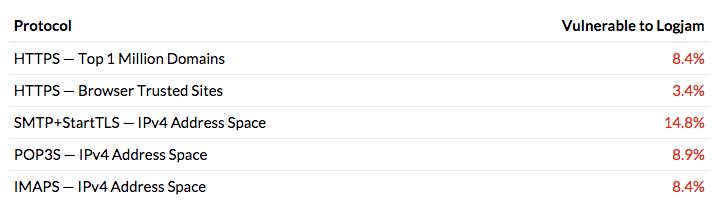
From 24e Might, there are 8.4% of the highest 1 million domains are affected by the Logjam vulnerability.
Check if the consumer is susceptible
The simplest method to check is to entry this SSL Lab consumer check web page within the browser.
Alternatively, you may also do this one.
Check if the server is susceptible
There are a number of instruments you should use for testing.
TLS Scanner – a web-based scanner powered by Testssl.sh that checks the affected web site for TLS misconfiguration and vulnerability, together with Logjam.
KeyCDN – one other device to check if the positioning is susceptible to Logjam.
Repair Logja assault vulnerability
You’ll be able to disable EXPORT encryption packs within the respective internet server configuration to mitigate this vulnerability.
Apache HTTP server
Disable export encryption by including the next to the SSL configuration file.
SSLCipherSuite !EXPORTRestart Apache and that is it.
Nginx
Add the next to the nginx.conf file
ssl_ciphers '!EXPORT';
#Be aware: - If you have already got ssl_ciphers configured, you simply want so as to add !EXPORT in present line as an alternative of including new one.You can too go right here to repair this in Sendmail, Tomcat, IIS, HAProxy, Lighthttpd, and so on.
What’s subsequent?
In case you are in search of steady safety safety on your on-line enterprise, think about using cloud-based WAF.

