Tweaking IBM HTTP Server (IHS) for manufacturing surroundings
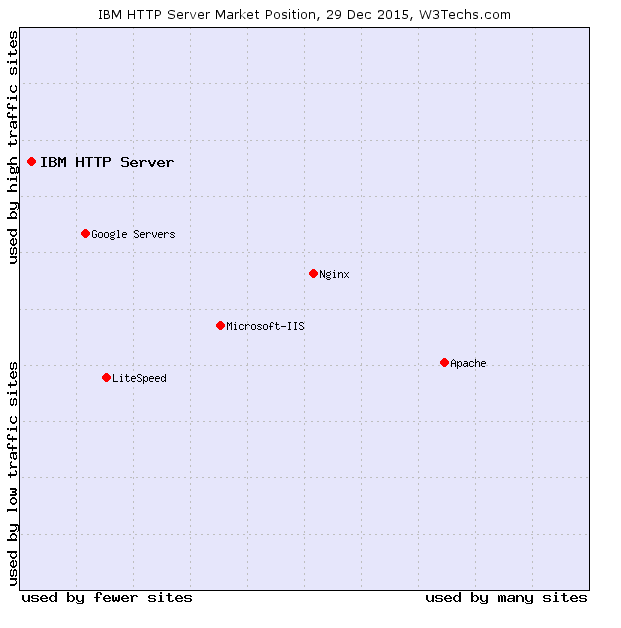
IBM HTTP Server is commonly used at the side of IBM WebSphere Software Server. Among the standard websites that use IBM HTTP Server are:
- Airtel.in
- Marriott. com
- Hsbc.nl
- mercedes-benz.com.eg
- Argos.nl
IHS is predicated on Apache HTTP Server, however modified by IBM to assist enterprise purposes and upkeep assist. It has a really small market share within the net server world, however remains to be broadly used with WebSphere Software Server.
The default IHS configuration gives loads of delicate data that may assist hackers put together for an assault and disrupt enterprise operations. As an administrator, you have to be conscious of hardening the IHS configuration to safe the net purposes.
On this article, I will clarify easy methods to create an IHS production-ready surroundings to remain secure.
A few issues: –
- You could have put in IHS in a Linux surroundings, if not you’ll be able to test the set up information right here.
- It is suggested that you just again up a configuration file.
- You could have HTTP header extensions in a browser or you need to use the web Header Checker device.
- As a result of size of the article, I’ll discuss SSL configuration within the subsequent submit.
Cover server banner and product data from HTTP header
In all probability one of many first duties to carry out when establishing a manufacturing surroundings is masking the IHS model and server banner in a header. This isn’t important, however is taken into account low threat because of the data leakage vulnerability and needs to be enough for PCI DSS compliant purposes.
Let’s have a look at how non-existent (404) request response within the default configuration.
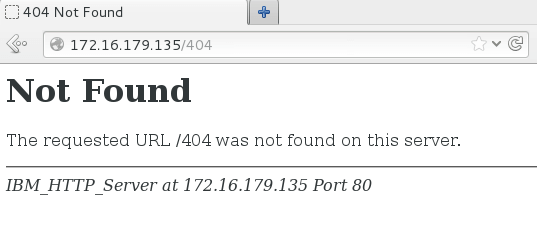
Oh no, it reveals that I am utilizing IBM HTTP Server together with server IP and port quantity, which is ugly. Let’s conceal them.
Answer: –
- Add the next three directives to your IHS’s httpd.conf file.
AddServerHeader Off ServerTokens Prod ServerSignature Off
- Save the file and restart the IHS
Let’s confirm this by opening a non-existent file. You may also use the HTTP Header device to confirm the response.
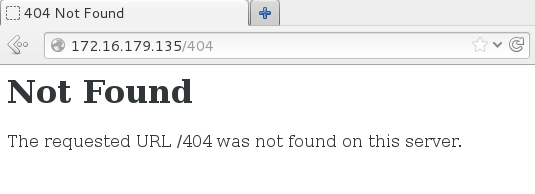
Significantly better! Now it doesn’t give product, server and port data.
Flip off stage
Etag header can reveal inode data and will help a hacker to carry out NFS assaults. IHS exposes the etag by default and this is easy methods to repair this vulnerability.
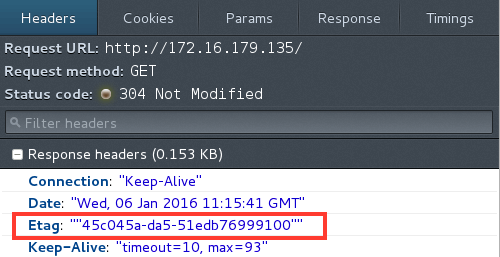
Answer: –
- Add the next directive to a root listing.
FileETag none
For instance:
<Listing /> Choices FollowSymLinks AllowOverride None FileETag none </Listing>
- Restart the IHS server to take impact.

Run IHS with a non-root account
Default configuration runs an online server with root & no person person, which isn’t really useful as going by way of a privileged account might have an effect on your entire server in case of a safety breach. To mitigate the danger, you’ll be able to create a particular person to run IHS situations.
Answer: –
- Create person and group referred to as ihsadmin
groupadd ihsadmin useradd –g ihsadmin ihsadmin
Now, change the possession of the IHS folder to ihsadmin in order that the newly created person has full permission to it. Assuming you put in within the default location – /choose/IBM/HTTPServer
chown –R ihsadmin:ihsadmin /choose/IBM/HTTPServer
Let’s change the person and group worth in httpd.conf
Person ihsadmin Group ihsadmin
Save the httpd.conf and restart the IHS server. It will assist IHS to begin as an ihsadmin person.
Implement HttpOnly and Safe flag in Cookie
By securing cookies and utilizing httponly, you cut back the danger of XSS assaults.
Answer: –
To implement this it is advisable maintain it mod_headers.so is enabled in httpd.conf.
If not, uncomment the road beneath in httpd.conf
LoadModule headers_module modules/mod_headers.so
And add beneath Header parameter
Header edit Set-Cookie ^(.*)$ $1;HttpOnly;Safe
Save the configuration file and restart the net server.
Mitigate Clickjacking assault
The clickjack method is thought the place an attacker can trick customers into clicking a hyperlink and executing embedded code with out the person’s information.
Answer: –
- Be sure mod_headers.so is enabled and add the header parameter beneath to the httpd.conf file
Header all the time append X-Body-Choices SAMEORIGIN
- Save the file and restart the server.
Let’s confirm by opening the URL, it ought to have X-Body choices as proven beneath.
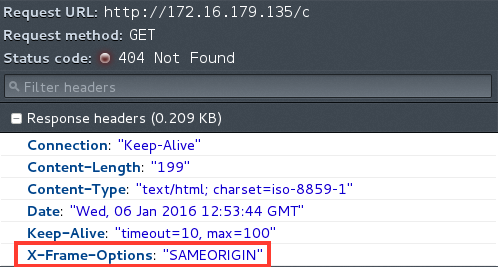
Configure listening guideline
This is applicable when you’ve got a number of Ethernet interfaces/IPs on the server. It’s advisable to configure absolute IP and Port in Pay attention directive to keep away from forwarding DNS requests. That is typically seen in a shared surroundings.
Answer: –
- Add the supposed IP handle and port in httpd.conf beneath Pay attention directive. Ex:-
Pay attention 10.0.0.9:80
Add X-XSS safety
You may apply Cross for Web site Scripting (XSS) safety by implementing the next header if disabled by the person within the browser.
<IfModule mod_headers.c> Header set X-XSS-Safety "1; mode=block" </IfModule>
Disable HTTP request tracing
If the Hint methodology is enabled within the net server, Cross Web site Tracing Assault could also be potential and cookie data could also be stolen. By default they’re enabled and you may disable them with the parameter beneath.
Answer: –
- Modify the httpd.con file and add the road beneath
TraceEnable off
- Save the file and restart the IHS occasion to take impact.
I hope the above ideas provide help to strengthen the IBM HTTP server for a manufacturing surroundings.

