That is our exact tutorial to strengthen your safety towards IoT vulnerabilities.
The Web of Issues may simply turn into one of many subsequent massive factor.
However you would not imagine me if I informed you that by 2030, the anticipated variety of IoT gadgets will likely be practically thrice the variety of folks residing on Earth.
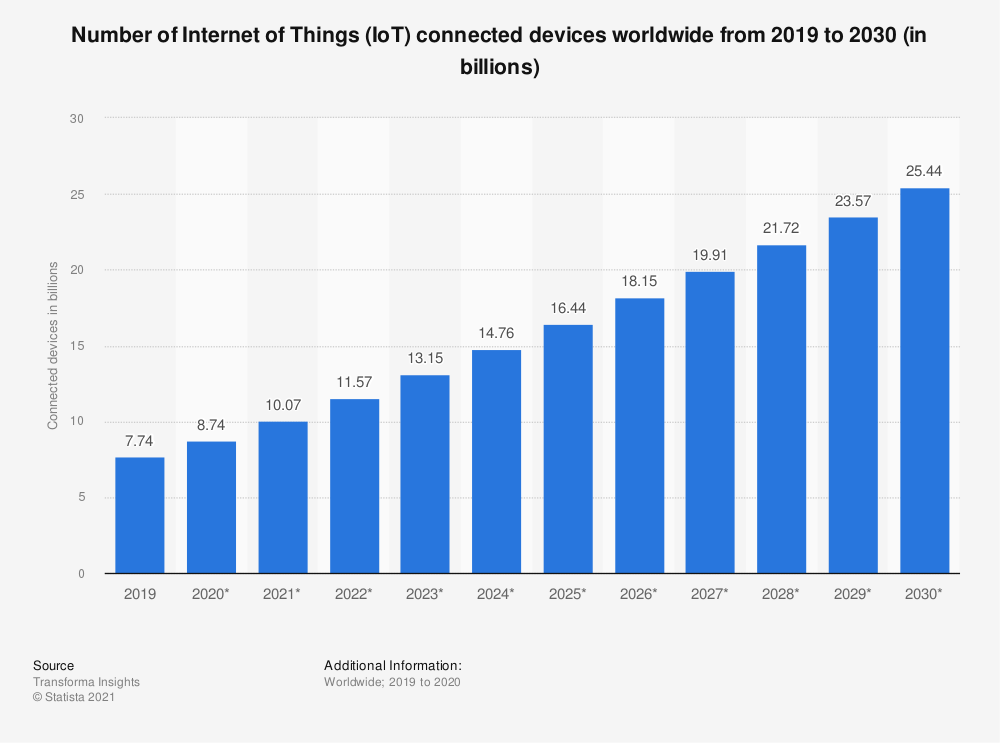
In different phrases, that is three IoT gadgets per individual. That is loads of gadgets and much more web.
And the web, which tries to make our lives simpler, brings many vulnerabilities. So it may be irreversibly idiotic to implement IoT with out closing the safety loopholes.
However let’s dig a little bit deeper and focus on first…
What’s IoT (Web of Issues)?
This Stuff collaborate over the web.
A typical instance is a Tesla, or reasonably a bunch, that shares info and makes the autopilot safer by the hour.
A less complicated instance is a smartwatch. It information knowledge out of your physique and sends it to the smartphone to observe your important indicators, akin to coronary heart charge, hours of sleep, steps, and so forth.
Amazon Echo (or different good dwelling tools) additionally qualifies as an IoT gadget.
In brief, IoT is a system of gadgets that electronically switch info to one another.
And we are going to regularly see that lots of them management essential features of our lives. They’ll have an essential voice in our houses, places of work, vehicles, well being and no matter.
So it’s essential to strengthen the fences to maintain the safety intact and the info non-public.
Nonetheless not satisfied!
Check out these disturbing occasions, which have torn aside any false sense of safety within the IoT neighborhood.
One such incident reported by a Reddit consumer, Dio-V:
Once I load the Xiaomi digital camera in my Google dwelling hub, I get photos of different folks’s homes!
One other unlucky case, as recalled by Samantha Westmoreland:
The thermostat saved going up – and a voice began talking from a digital camera within the kitchen – then performed vulgar music. “So I unplugged it and pointed it on the ceiling.”
The purpose is to not scare you. However these issues, as massive as they appear, are simply the tip of the iceberg.
Thus, IoT is a website that requires in-depth troubleshooting and restore earlier than being broadly adopted.
Vulnerabilities in IoT gadgets
Subsequent sections will spotlight some areas that ought to attraction to customers and producers.
Weak passwords
It’s the default weak passcodes on IoT gadgets that in the end enabled the most important DDoS assault on October 21, 2016. This introduced Amazon Internet Providers and its purchasers like Netflix, Twitter, Airbnb, and so forth.

So default passwords like Admin, 12345 are the enemies of your digital safety. Utilizing robust passwords steered by password managers is step one in stopping an intruder.
The second is utilizing two-factor authentication (2FA). And it is lots higher should you use {hardware} authentication like Yubikey.
No encryption
The Web of Issues performs with delicate knowledge. And about 90% of information is distributed with none safety envelope.
That is an enormous safety flaw that producers ought to deal with instantly. For his or her half, the customers can confirm their gadget encryption coverage.

Since putting in an antivirus or comparable software program could be troublesome because of low processing energy and compatibility issues, utilizing a VPN can show to be an answer. Merely put, a VPN protects your Web Protocol (IP) handle and encrypts your knowledge.
Irregular replace cycle
Every producer is accountable for offering a wholesome replace cycle to their gadgets. IoT gadgets lacking safety and firmware updates are extra weak to hackers discovering new bugs.

Once more, it’s as much as the customers to test their producer’s replace historical past earlier than buying.
And there may be nothing a consumer can do besides keep away from a model with a nasty replace file.
Susceptible utility
Builders should combine IoT gadgets with particularly designed purposes. Any modified software program could comprise outdated safety protocols that compromise the safety of an IoT gadget.

And an attacker can compromise a weak IoT utility to snoop and assault your complete community.
Incorrect administration
This part requires a central administration console for all IoT gadgets in a system.
And not using a unified administration system, it’s simpler to mismanage IoT gadgets, particularly when there are a lot of gadgets on a community.

These platforms want to trace important metrics for all IoT gadgets, together with safety alerts, firmware updates, and general danger monitoring in a single place.
Community isolation
IoT gadgets are sometimes a part of a community, exposing the total vary of gadgets on board. So the IoT gadget should use a separate community tunnel.
This prevents the perpetrator from profiting from community sources and allows superior monitoring of IoT community site visitors.
Principally, it’ll preserve your complete community untouched in case a single gadget is compromised.
Bodily surveillance
Many IoT gadgets, akin to safety cameras, work remotely. In that case, it turns into extraordinarily simple to bodily assault a tool.
Moreover, it may be managed and manipulated in malicious methods solely to defeat the very objective of its set up. For instance, an offender can take away the reminiscence card from a remotely put in safety digital camera and consider (or change) the info.

Whereas it’s troublesome to repair this downside fully, periodic checks will certainly assist.
For superior tools one can observe the relative place on the time of set up. As well as, there are sensors to establish and monitor any micrometer deviation from the unique place.
Conclusion
IoT is undeniably helpful and we won’t simply throw all of them away till they’re foolproof.
Usually, these gadgets are fairly secure on the time of buy. However regularly they begin to miss updates or fall prey to mismanagement.
As customers, we have to preserve our wits about us and adapt to greatest practices to handle each IoT gadget. As well as, attempt to preserve the producer’s observe file in thoughts when making a purchase order.
On a facet observe, take a look at our tackle monitoring private knowledge breaches.