Software program provide chain safety options assist mitigate dangers and shield your techniques from harmful assaults.
Prior to now few years, safety has turn out to be essential for corporations and people, given the rising degree of cyberattacks. These assaults can occur to any group, division, system, IT infrastructure, and software program provide chain.
Trendy software program provide chains embrace pre-existing libraries, CI/CD techniques, open-source repositories, model controllers, deployment techniques, monitoring and testing instruments, and so forth.
There are such a lot of components included in constructing a software program answer and the code is even utilized in a number of tasks. This will increase the assault floor for hackers who’re at all times looking out for vulnerabilities in any of the techniques you employ.
And once they discover it, they may leverage it and hack your techniques. Consequently, it might probably result in information leaks, malware, ransomware, and whatnot.
This is the reason it’s necessary for organizations, builders, and software program distributors to boost their software program provide chain safety.
On this article, we’ll focus on what precisely a software program provide chain assault appears to be like like, why you need to safe your provide chain, and one of the best safety options to assist mitigate dangers.
Let’s start!
What Is Sofware Provide Chain Safety?
A software program provide chain consists of all of the techniques, processes, instruments, and issues (principally every little thing) that helps develop an utility in its software program improvement lifecycle (SDLC).
And software program provide chain safety means securing all these techniques, elements, and practices. It might embrace protocols, interfaces, proprietary or third-party code, exterior instruments, infrastructure techniques, deployment techniques, and the checklist goes on.
Your provide chain is weak to assaults similar to different techniques in your group. In a provide chain assault, the hacker finds and leverages vulnerabilities in any of your techniques and processes within the provide chain and infiltrates it. It may result in information breaches and different safety dangers.
Some widespread software program provide chain assaults are:
- A breached CI/CD pipeline involving construct servers, deployment instruments, testing frameworks, code repositories, and so forth.
- Malicious code inside an open-source software. This could occur by submitting malicious commits to the code repo, as an example.
- CI/CD misconfigurations in deployment and testing processes
Some well-known software program provide chain assaults:
- SolarWinds hack: Hackers discovered a vulnerability of their Orion platform and compromised 30k+ organizations worldwide.
- CodeCov Breach: In April 2021, attackers breached the auditing software, CodeCov, affecting its widespread customers.
- Mimecast assault: Attackers gained entry to one among their digital certificates for authentication.
Why Is Software program Provide Chain Safety Vital?

Within the above examples of assaults, only one vulnerability in code, generally, led to a widespread breach affecting people and organizations.
When a improvement workforce deploys software program for business or inner use, the product’s safety is important, together with the code they haven’t written and the third-party instruments they use. As a result of in the event you belief exterior assets blindly, they might convert into threats and assaults because of vulnerabilities in them.
To this, the software program provide chain makes positive that your total code, instruments, and assets are of their finest safety types and are untampered with, up-to-date, and haven’t any vulnerabilities or malicious code.
And to implement this, you need to examine every software program part throughout the SDLC, together with your in-house code, open-source deployments, protocols, interfaces, dev instruments, outsourced providers, and different issues related to the software program construct.

As well as, you should use a complete, dependable, and environment friendly software program provide chain safety answer to mitigate points and shield every software program part. It does so by scanning the software program for identified exploits and dependencies and implementing community safety mechanisms.
This fashion, these instruments assist forestall unapproved modifications and unauthorized entry to discourage threats and assaults.
Let’s speak about a number of the finest software program provide chain safety instruments to mitigate assaults and shield your software program provide chain.
Slim.ai
Slim.ai permits you to construct containers with safety and pace to guard your software program provide chain with out writing any new code.
It is going to assist you robotically discover and take away vulnerabilities in software program techniques from containerized functions earlier than they ship to the manufacturing part. This may even safe your workloads for software program manufacturing.
Slim.ai will strengthen and optimize your containers whereas managing them successfully. Additionally, you will get insights into the contents of your containers by deeply analyzing their packages, metadata, and layers.
You may seamlessly combine Slim.ai into your CI/CD pipelines and allow automation to save lots of effort and time in mitigating safety dangers with none handbook work.
You’re going to get to make use of Slim Starter Kits, that are templates that you should use to create your app in any language or framework. With container intelligence, you possibly can view picture development, package deal particulars, and vulnerabilities. This can assist you perceive your safety posture and create picture friendliness.
Docker Wasm
Wasm is a light-weight, quick, and new different to Home windows or Linux containers you employ in Docker. Docker + Wasm will assist you construct, run, and share trendy functions with better safety.
There are various advantages of utilizing Docker in securing the software program provide chain. It is going to make your software program improvement extra predictable and environment friendly by automating the duties and eradicating the necessity for repetitive configuration duties. Your total software program improvement lifecycle will turn out to be sooner, simpler, and extra moveable.
Docker presents a complete end-to-end platform that can give you APIs, CLIs, and UIs with safety engineered to work out of the field throughout your SDLC, making the method extra environment friendly.
- Docker pictures are wonderful for letting you effectively create your utility on Mac and Home windows.
- Use Docker Compose to construct multi-container software program.
- Bundle software program as container pictures which might be moveable and run persistently in numerous environments, akin to AWS ECS, Google GKE, Aure ACI, Kubernetes, and extra.
- Combine with completely different instruments throughout the software program improvement pipeline, together with CicleCI, GitHub, VS Code, and so forth.
- Personalize picture entry for builders with role-based entry controls (RBAC) and acquire deeper insights into exercise historical past utilizing Docker Hub Audit Logs.
- Enhance innovation by rising collaboration with builders and workforce members and publishing your pictures simply to Docker Hub.
- Efficiently deploy functions independently on completely different containers and languages. This can scale back potential conflicts between libraries, frameworks, and languages.
- Use Docker Compose CLI and leverage its simplicity in constructing functions sooner. You may launch them shortly on the cloud with Azure ACI or AWS ECS or do it regionally.
CycloneDX
CycloneDX is definitely a contemporary full-stack BOM customary providing superior capabilities for securing provide chains from on-line dangers and assaults.

It helps:
- {Hardware} Invoice of Supplies (HBOM): It’s for stock {hardware} constituents for ICS, IoT, and different linked and embedded units.
- Software program Invoice of Supplies (SBOM): It’s for stock software program providers and elements and their dependencies then.
- Operations Invoice of Supplies (OBOM): Full-stack runtime stock configurations, environments, and extra dependencies.
- Software program-as-a-Service (SaaSBOM): It’s for stock endpoints, providers, classifications, and information flows that gasoline cloud-native functions.
- Vulnerability Exploitability eXchange (VEX): It’s to convey how weak elements might be exploited in merchandise.
- Vulnerability Disclosure Stories (VDR): It’s to speak unknown and identified vulnerabilities that have an effect on providers and elements.
- BOV: It’s to share weak information between weak intelligence sources and techniques.
The OWASP Basis backs CycloneDX, whereas the CycloneDX Core Working Group manages it. It’s additionally supported by the knowledge safety group from internationally.
Aqua
Aqua offers full-lifecycle provide chain safety for software program. It will probably shield all of your hyperlinks inside your software program provide chain to reduce assault surfaces and keep code integrity.
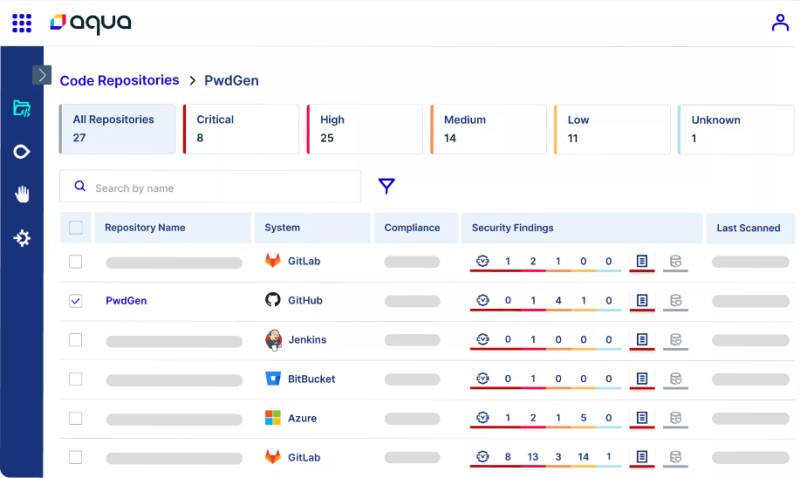
With the assistance of Aqua, you possibly can spot dangers and vulnerabilities in all of the phases of your software program lifecycle by scanning pictures and code. It is going to additionally permit discovering uncovered secrets and techniques, IaC misconfigurations, and malware in order that no challenge can go to the manufacturing part.
You may safe your processes and techniques all through the availability chain with a purpose to develop and ship your software program to manufacturing. Aqua will assist you monitor your DevOps instruments’ safety posture, making certain safety controls are in place.
Options and Advantages:
- Common code scanning: Aqua can scan your total supply code in only a few minutes and detect vulnerabilities, safety loopholes, open-source license issues, and extra. By scanning codes periodically, you’ll be alerted of latest dangers with altering codes. You’re going to get code scanning by Aqua Trivy Premium and get constant outputs all through the SDLC.
- In-workflow alerts: Scan code and get notifications irrespective of the place you’re working from. You may obtain notifications instantly within the IDE whenever you code, Supply Code Administration (SCM) system as feedback on the pull requests, cloud repository, and the CI pipeline even earlier than the software program launch.
- Open-source dependency monitoring: Aqua will grade every of your open-source packages based mostly on their recognition, dangers, maintainability, and high quality. Subsequent, it notifies your builders of the critically harmful packages when they’re launched. This can allow you to ascertain and implement an organization-wide high quality degree that you need to meet earlier than including any new code to the codebase.
- Pipeline safety: Achieve full visibility throughout your CI pipelines and navigate by hundreds of software program launch tracks resulting in the manufacturing setting. You may simply implement Static Pipeline Evaluation for every pipeline (like GitLab CI, Bitbucket Pipeline, Jenkins, GitHub Actions, CircleCI, and so forth.) and perceive every instruction.
- Subsequent-gen SBOM: Don’t be restricted by fundamental SBOM creation; as a substitute transcend and file every motion and step from when the developer commits code to the entire construct course of till the era of your closing artefact. Code signing may even assist customers confirm your code historical past and verify that the generated code is similar one ending up in your improvement toolchain.
- Managing CI/CD posture: Aqua will allow you to spot and resolve essential misconfigurations in your DevOps platform (like Jenkins, GitHub, and so forth.) and implement Zero-Belief safety in it. It will probably implement the coverage of Least Privilege Entry that will help you audit privileges all through the SDLC. It will probably additionally implement Separation of Duties (SoD) to decrease safety dangers whereas making certain compliance.
Furthermore, you possibly can set up and uphold belief by creating SBOMs signed digitally and making use of integrity gates to confirm artefacts throughout the CI/CD pipeline. It is going to assist make sure that solely your code goes to the manufacturing part and never anything with it.
ReversingLabs
Get superior software program provide chain safety (SSCS) on your CI/CD workflows, launch packages, and containers by ReversingLabs, which permits your DevSecOps workforce to deploy the appliance with higher confidence.
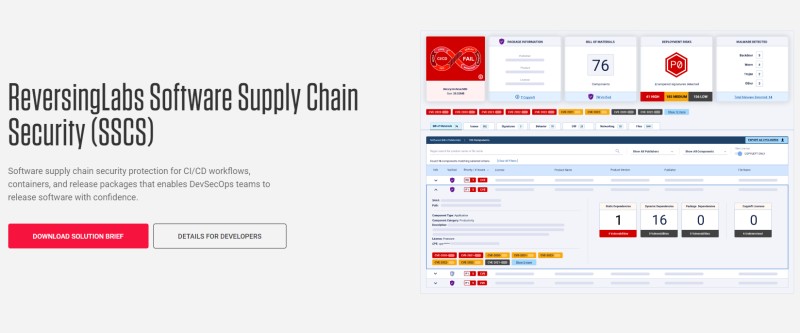
The software with will let you quickly analyze bigger launch packages, open-source libraries, third-party software program, and containers for threats. You can too detect, remediate, and prioritize high-risk threats hidden inside software program dependency layers.
Aqua presents customized approval insurance policies to be able to affirm your software program’s safety high quality confidently earlier than releasing it to manufacturing. This software takes care of safety in your total SDLC from supply code management to managing software program part dependencies, the CI/CD course of, and launch pictures.
Thus, you possibly can simply detect and repair CI/CD workflow dangers, compromises, malicious open-source packages, secret exposures, and other forms of threats at each level in your group’s software program improvement lifecycle.
Moreover, you possibly can transcend and shield your prospects from undesirable tampering which might inject unauthorized behavioral adjustments, backdoors, and malware into the software program.
You’re going to get to carry out trouble-free integrations at each stage of the supply pipeline. These integrations will assist you resolve high-risk threats sooner and at an early stage. ReversingLabs is a good funding not just for improvement groups but in addition for SOC groups.
Snyk
Improve your software program provide chain safety with Synk, which will help you shield the software program’s essential elements, akin to container pictures, open-source libraries, developer instruments, and cloud infrastructure.
Snyk will assist you comprehend and handle your provide chain safety by monitoring dependencies, making certain safe design, and fixing vulnerabilities. It makes positive you design software program with safety in thoughts, proper from the start.
Utilizing Snyk, you possibly can observe the recognition, upkeep, and safety of 1M+ open-source packages in numerous ecosystems.
You may scan your software program to generate a invoice of supplies with a purpose to establish the elements used and the interplay between them. Snyk will assist you repair extra security-related points in much less time.
- Snyk Vulnerability Database and Synk Advisor are two of the instruments that present helpful and up-to-date details about essential points and the methods to forestall them in order that managing safety threats turns into simpler earlier than the undertaking even begins.
- Snyk’s audit providers, Snyk Container and Snyk Open Supply, are instruments to investigate tasks and create SBOM with a listing of identified vulnerabilities, open-source packages, and fixation recommendation.
- Snyk permits you to combine with a number of instruments, workflows, and pipelines to allow safety in your software program provide chain. Integrations embrace PHP, Java, JS, Python, AWS, GCP, RedHat, Jenkins, Docker, Kubernetes, GitHub, GitLab, Slack, and plenty of extra.
Moreover, Snyk is backed by main safety intelligence techniques within the business, providing you instruments to safe your open-source dependencies, customized code, cloud infrastructure, and containers from only a single platform.
Conclusion
On-line dangers are increasing, posing threats to companies, property, and folks. So, if you’re a software program developer or a enterprise coping with software program improvement, you need to improve your software program provide chain safety by leveraging strategies and instruments just like the above. These instruments will assist safe your total software program provide chain by mitigating threats effectively.
You might also discover DevSecOps instruments.

