Multi-factor authentication is among the most safe strategies to safeguard information from theft and hackers.
What’s Multi-Issue Authentication (MFA)?
Have you ever ever encountered a situation the place you have been prompted to offer additional data after getting into your username and password to entry a web site, a banking app, or one other system or system? The title of this method is “multi-factor authentication” (MFA).
Multi-factor authentication (MFA) confirms a consumer’s identification by using two or extra components, resembling a code, token, PIN, biometric information, or a mix of those, earlier than offering entry to information or a system.
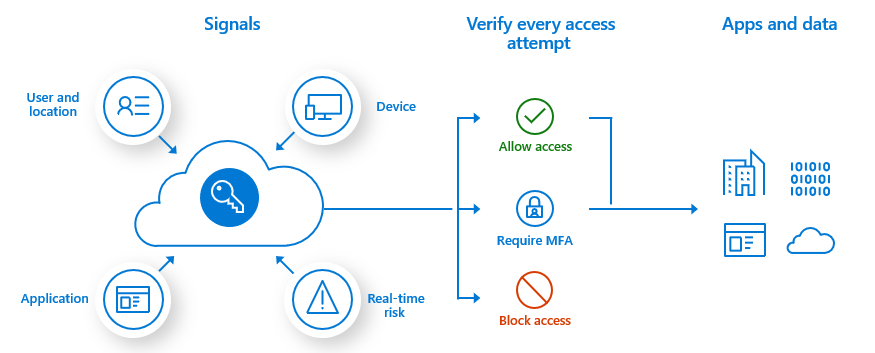
Easy authentication wants one piece of information, resembling a password. Multi-factor authentication makes use of a couple of issue to entry a useful resource to extend safety.
Contemplating right this moment’s internet world and the rising incidence of information theft, MFA is a vital part of any safety system to protect the consumer’s personal data in opposition to unauthorized entry.
These days, most web accounts, together with banking and social media accounts, and devices like telephones and laptops are secured with MFA.
MFA provides an additional layer of safety by requiring entry to one of many further components, even when the consumer’s password was compromised. Because of this even when somebody have been to be taught the consumer’s password, they might nonetheless want entry to one of many further components to achieve entry.
It’s considerably harder for hackers to entry accounts when a couple of authentication issue is used since they should know many items of data.
People and authorities organizations incessantly use MFA and different corporates to safeguard delicate information and be sure that solely licensed individuals might entry their programs or information to spice up safety.
MFA is gaining recognition, particularly as companies change from utilizing customary passwords to extra sturdy identification verification strategies. Multi-factor authentication (MFA) is a strong device for stopping unlawful entry to networks and consumer information by using a number of phases of identification verification.
MFA is important for safeguarding consumer data in right this moment’s interconnected networks and rising information theft instances. It would help in decreasing the danger of identification theft, information breaches, and different cyberattacks.
This put up will have a look at different features of MFA, together with some platforms providing MFA providers.
How Does MFA Work?
Earlier than offering somebody entry to a system or account, a safety measure referred to as MFA verifies the particular person’s identification utilizing numerous authentication strategies. It’s meant to make it way more tough for attackers to entry delicate data or assets.
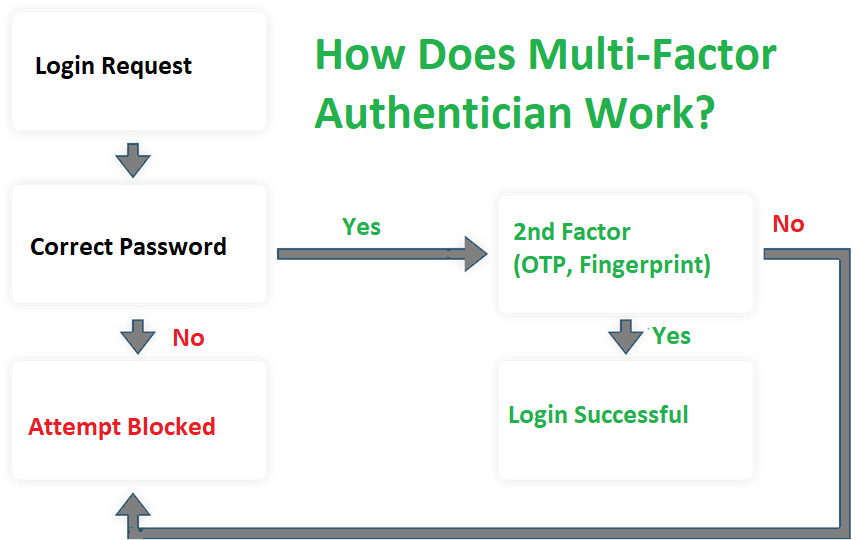
MFA combines a bodily factor—resembling a code delivered to your telephone—with one thing —resembling a password. It may possibly additionally use biometric information, resembling fingerprints, to determine identification.
Finish customers generally enter their username and password when logging into an account utilizing multi-factor authentication. After that, they are going to be requested to authenticate their identification, often with a couple of further selections.
One-time passwords (OTPs) delivered by way of SMS or codes entered by way of authenticator apps are different options.
You may as well use an authenticator app to submit biometric data like a fingerprint or facial scan. Some enterprise corporations might require customers to authenticate by way of a bodily token, resembling a key or swipe card.
Third-party authenticator (TPA) functions like Google, which generally show an authentication code incessantly altering and randomly produced, present multi-factor authentication.
Elements in an MFA Setup
Authentication happens when somebody needs to entry a useful resource resembling a community, system, or software. To make use of the ultimate product (system or service), the consumer should present assist with their identification and verification of their declare to that identification.
Organizations and people can implement multi-factor authentication utilizing the authentication components listed under:
The MFA components could be grouped into three features:
- Information Issue: One thing , resembling a password or PIN
- Possession Issue: One thing you will have, resembling a {hardware} token or USB dongle
- Inherent Issue: One thing you will have, resembling a fingerprint, eye, or facial scan
E mail Codes: The consumer searching for entry by way of e-mail will obtain these codes. Some of the typical types of MFA is getting a code by way of e-mail.
Textual content Tokens: Some of the widespread MFA components is textual content tokens. A one-time password (OTP) within the type of a PIN might be despatched to your telephone if you enter your username and password.
Digital Tokens: Multi-factor authentication-enabled cellular authenticator apps enhance the safety of logging into on-line accounts and web sites. Microsoft’s Authenticator app provides randomly generated and incessantly modified code, just like Google’s. The generated code from the cellular authenticator should be entered after the consumer’s username and password to entry the specified system or service.
Verification Utilizing Biometrics: Verification utilizing biometrics may contain something from facial recognition to fingerprint identification. Customers of PCs or sensible units can profit from this know-how to enhance their on-line safety.
{Hardware} Tokens: This method produces codes utilizing a tiny gadget. Some of the safe MFA strategies is that this one. It’s used extensively in companies, banking, and different extremely sure functions.
If you wish to entry data on a cellular system, chances are you’ll make the most of a USB or USB-C “dongle”.
Safety Questions: Properly-known questions might often be requested as a part of MFA. When creating your account, you may be prompted to decide on a safety query resembling:
- What was the title of your first pet?
- What road did you develop up on?
- What’s your mom’s maiden title?
- What was your childhood nickname?
You have to first enter your username and password to entry your account and reply to a safety query. However as a result of comparable data could be simply collected from different social media instruments, MFAs of this sort have to be up to date.
MFA might be protected and safe if tokens, passcode, PINs, biometric scan, and so on., are applied dynamically.
MFA Vs. 2FA
Let’s look at how MFA (Multi-Issue Authentication) and 2FA (Two-Issue Authentication) fluctuate:
The usage of a number of components to confirm an individual’s identification whereas searching for entry to a useful resource, web site, or different software is named multi-factor authentication or MFA.
Multi-factor authentication provides extra assurance that customers are who they are saying they’re by demanding a couple of type of identification affirmation, which lowers the danger of undesirable entry to delicate information. Multi-factor authentication is subsequently outlined as any mixture of two or extra components.
Whereas merely utilizing two components is known as 2FA. The best and best technique for including a protected layer of authentication on high of login credentials is two-factor authentication (2FA).
Following the entry of their credentials, customers should verify their identification utilizing a special issue, resembling a code obtained by way of e-mail or SMS, safety questions, and so on. Even when somebody steals a buyer’s password maliciously, these protocols stop suspicious login makes an attempt to the system.
The kind of authentication used relies upon completely on the sensitivity of the information and different circumstances. As an illustration, MFA is used when the system or information is said to finance or banking, however easy 2FA is used when accessing e-mail providers.
Drawback of MFA
Adopting and utilizing MFA has no disadvantages aside from psychological ease. MFA has no drawbacks in case you can handle a number of safety measure entries. MFA measures are typically essential to guard your information and safe your system.
MFA will solely consistently ask you to enter safety measures in case you log off out of your preliminary login. Subsequently, so long as you might be logged into the system, there is no such thing as a chance of inconvenience.
The login necessities should strike a steadiness between safety and comfort to make sure safe and dependable entry. Nonetheless, they need to be manageable to keep away from inflicting extreme hardship for customers.
MFA Apps
#1. Microsoft Multifactor authentication in Azure AD
An identification administration resolution that allows enterprises to manage consumer entry to functions and providers is Microsoft’s Azure Energetic Listing (AD). Azure AD has capabilities like multi-factor authentication (MFA).
A necessary safety layer for securing enterprise networks, apps, and information is Microsoft’s Azure AD MFA. MFA requires customers to register with two or extra identity-verifying documentation.
It allows customers to get into their accounts by using each one thing they know (their password) and one thing they possess (an authentication code). With each items of data, consumer accounts could be accessed because of the extra diploma of safety.
By demanding a number of types of authentication when a consumer logs in, Microsoft’s Azure AD MFA provides consumer accounts an additional layer of safety. This offers a protection in opposition to unauthorized entry in addition to malicious entry makes an attempt. MFA could be arrange for particular consumer accounts or as a basic coverage for all customers inside an organization.
By making authentication more difficult for potential attackers, this authentication technique lowers the potential for an unauthorized particular person accessing a consumer’s account.
#2. Authsignal’s Multi-Issue Authentication (MFA and Passwordless Auth)
Authsignal’s multi-factor authentication and identification software program is simple to deploy and is a number one selection for cloud-hosted know-how firms. Centered on the authentication and orchestration of buyer identification, Authsignal delivers a drop-in suite of instruments to strongly authenticate customers, stop fraud, and safe buyer journeys wherever in your buyer expertise.
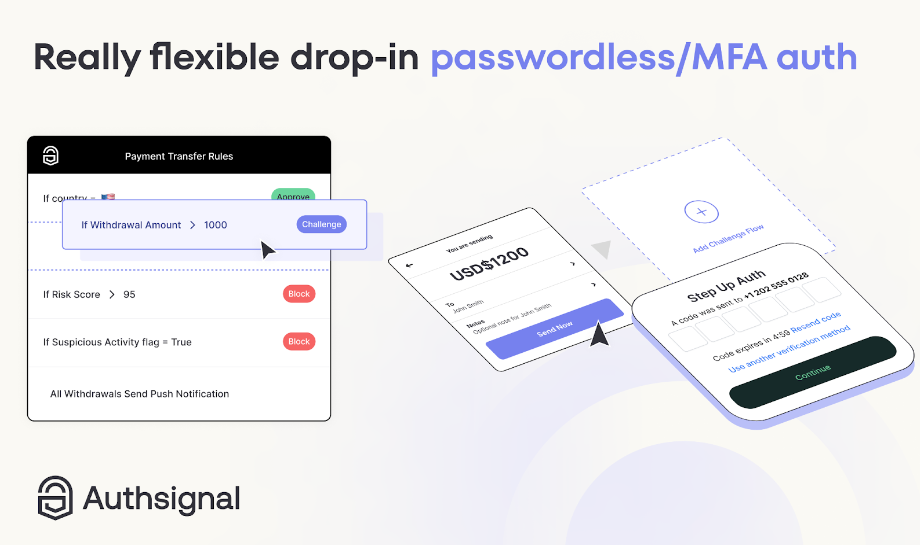
Authsignal’s strategy to multi-factor authentication allows passwordless problem flows to be inserted into your present buyer journeys or identification stacks wherever there’s a necessity to extend belief and security.
Their suite of authentication instruments works along with your present identification stack and could be deployed wherever in your buyer flows. Engineering time is minimized by means of a single API. There’s no migration required. Leveraging their out-of-the-box integrations with Auth0, Microsoft Azure AD B2C, AWS Cognito, Twillo, Messagbrid, and Authsignal works along with your present know-how stack.
The No-Code Guidelines Engine allows buyer journeys to be deployed in hours, considerably decreasing the associated fee and time of engineering and improvement groups usually related to hardcoding guidelines. Drop in Passwordless Authentication challenges wherever within the buyer journey.
Scale back Buyer Help time with a single view of the client. Using our monitor motion API, Authsignal provides a single FraudOps view of your clients’ actions, enabling the discount of queue instances and bringing peace of thoughts to fraud and operational groups. Acquire an entire audit path of actions.
Options:
- Versatile multi-factor authentication, deployed in any web site or software
- Authenticate consumer identification and combine with a number of identification distributors
- No code guidelines engine – construct guidelines in minutes, create problem flows, block, permit, problem and evaluate
- A single view of the client
- Customizable UX and UI with help to your branding
- Passwordless Authentication help for
- TOTP/authenticator apps
- SMS OTP
- FIDO2/WebAuthn
- E mail magic hyperlinks
#3. Akamai’s Multi-Issue Authentication (MFA)
Akamai’s Multi-Issue Authentication (MFA) is a user-friendly, cloud-based authentication resolution that gives a protected, skilled expertise.
Akamai’s MFA is a cloud-based system with easy and simple options, resembling automated one-time password (OTP) distribution, multifactor prospects, and direct software interplay.
Akamai’s distinctive MFA know-how makes it easy to authenticate customers utilizing their voice, face, fingerprints, or different biometric components by offering unmatched perception and management over consumer identities.
Organizations can simply and rapidly arrange a safe authentication resolution with Akamai MFA that’s custom-made to their distinctive necessities whereas providing their customers the benefit of a streamlined expertise. Its MFA platform is very customizable and expandable, making it easy to fulfill the wants of assorted consumer teams.
These MFA options give enterprises superior authentication capabilities that help in defending their networks in opposition to refined threats and intrusions. Its MFA options are made to ensure complete compliance with trade necessities, making them some of the safe authentication options in the marketplace proper now.
The simplicity of Akamai’s MFA makes it the right resolution for companies of all sizes.
#4. Duo Multi-factor authentication (MFA)
The safety of digital identities from potential attackers is changing into less complicated because of rising know-how. Duo MFA Safety, a Cisco product, is presently the main MFA resolution.
Duo is a SaaS-based, safe zero-trust entry platform for companies of all sizes that provide two-factor authentication, single sign-on, and safe distant entry.
Duo MFA provides a layer of safety to any service or web site that requires authentication. It’s designed for the cloud and on-premises use.
Customers should full a further step to achieve protected entry utilizing Duo’s Multi-Issue Authentication (MFA) resolution.
This extra step is integrated into the consumer’s authentication process and asks the consumer to show their identification by supplying one thing they know (password or pin), one thing they’ve (token or smartphone), or one thing they’re (fingerprint or face).
Organizations might enhance safety by shielding customers from defective credentials, phishing scams, and different undesirable actions utilizing an entire MFA resolution from Duo.
#5. Lastpass Multifactor Authentication
Many merchandise can be found from Lastpass Multifactor Authentication to assist safeguard consumer information. Your LastPass account is given further safety, guaranteeing that solely you may entry your information.

Utilizing multifactor authentication, LastPass offers a easy and safe technique to safeguard your on-line accounts. By confirming their identification with a further issue, resembling a code or fingerprint, this authentication system allows customers so as to add an additional diploma of safety to their accounts.
Moreover, it offers password administration so chances are you’ll log in to any system and not using a password. Cloud apps, VPNs, and entry factors can all be secured with LastPass.
Customers might rapidly configure the multifactor authentication process with LastPass in order that their accounts are all the time safe. It provides customers the boldness that even when hackers or different harmful actors already know their passwords, they received’t be capable to entry their accounts.
It turns into harder for unauthorized events to get entry when many authentication parts are used, resembling passwords, biometrics, and safety questions. Customers can really feel safe realizing that their information is protected and personal when utilizing these merchandise.
It’s easy to put in throughout all sizes of companies because of its essential options, resembling adaptive authentication, easy deployment, centralized, granular management, and automation of consumer provisioning with Microsoft AD, Google Workspace, and Azure AD.
Last Phrases
To make clear, including extra authentication parts to the authentication course of is what MFA entails. A subset of MFA often called two-factor employs simply two credential components. You have to set up MFA in your group since utilizing a password as the only real issue must be safer.
The clock is ticking. After studying the distinctions between 2FA and MFA and the risks of using single-factor passwords to entry firm programs, it is best to make strengthening safety your high precedence to safeguard the information.
Subsequent, you may discover consumer authentication platforms.

