Phishing is a method that criminals use to trick customers into revealing login credentials, bank card particulars, and different non-public information.
Normally, attackers seem as if they’re from identified and trusted organizations. This permits them to trick the customers into opening a compromised web site hyperlink, malicious emails, attachments, or real messages.
A hyperlink may very well be a server that installs malware that steals delicate data, akin to login credentials and different non-public information, from the sufferer. Normally, attackers current malicious communication as if it comes from a reliable entity like a cellphone firm or one other service supplier.
How Harmful are Phishing Assaults?
A phishing assault is a giant safety threat, whether or not focusing on a person or a company. As soon as they comprise a community, they will set up malware, infect all of the computer systems, after which use this to launch inner and exterior assaults. Moreover, the attackers might entry delicate firm non-public information, which they may use to blackmail the group or promote to rivals.
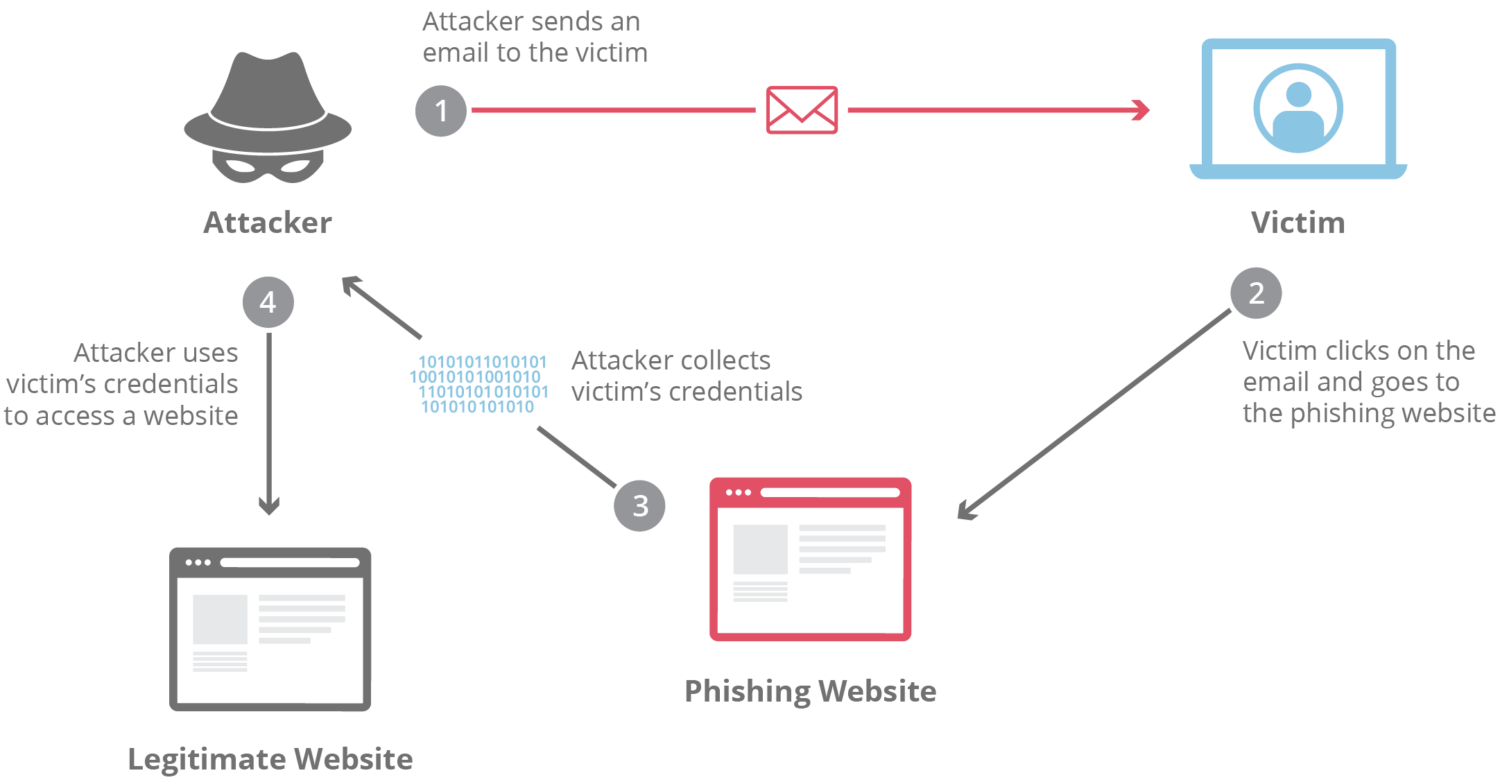
As soon as profitable, the fraudsters usually use stolen credentials, bank card particulars, or different non-public data to entry different providers on the sufferer’s community, make unauthorized purchases, and extra.
Typically, a phishing assault might result in fame and monetary losses for an organization or particular person. Additionally, the attackers may take the community down – resulting in outages and big monetary losses. One other hazard is dropping the credibility and belief of consumers, who might then transfer to a competitor.
Examples of Latest Phishing Assaults
Under are a couple of of the latest phishing assaults:
#1. Google and Fb Faux Bill Funds
Between 2013 and 2015, a Lithuanian scammer obtained over $100 million from Google and Fb by a sequence of faux invoices masquerading from a big Asian-based producer. Inside two years, the fraudster despatched a number of pretend multi-million-dollar invoices resembling these from the provider.
These included pretend contracts and letters purportedly signed by Google and Fb representatives. By the point they found the rip-off, the 2 had paid over $100 million.
#2. Colonial Pipeline Phishing Assault
A ransomware assault nearly crippled your complete operations of the Colonial Pipeline within the USA. The 2021 assault compromised the billing programs and enterprise community -forcing the corporate to cease most of its operations.
After getting an worker’s password by phishing, the attackers put in malicious ransomware software program on the corporate’s community. This allowed them to compromise the programs and demand a ransom, which the corporate paid to keep away from additional harm and disruption of providers.
Initially, the pipeline paid $4.4 million for the decryption key. Nevertheless, the corporate misplaced extra because of the one-week shutdown that led to the non-delivery of oil price $2.86 billion.
#3. Sony Image Spear Phishing Assault
In Sony Image’s case, the attackers despatched spear phishing emails to the staff after acquiring their data, akin to names and titles, from LinkedIn.
Then, posing as colleagues, the attackers despatched malicious e mail messages containing malware to the unsuspecting workers. The assault led to a breach that affected over 100TB of information, which price the corporate over $100 million to kind out.
Sorts of Phishing Assaults
Unhealthy actors use quite a lot of methods to trick goal customers. The method varies relying on the target, and under are some frequent phishing sorts.
Spear Phishing
Spear phishing is an assault that targets a selected group or particular person as an alternative of random customers. As such, it requires some information of the goal group or person. The attacker should dig deeper and procure inside data akin to a person’s energy construction, private life, hobbies, or something they will use to customise the phishing message.

The attacker then customizes the message and sends it to the sufferer pretending to be a consumer, provider, or boss requiring a change of bill particulars or switch of some cash to a specified account. Usually, recognizing a spear assault is tough as a result of the attackers trick a sufferer utilizing correct details about the person or group.
Whaling Phishing
Whaling phishing is an assault just like spear phishing however targets the corporate’s executives. These phishing emails, typically adopted by a cellphone name, usually result in tricking the executives into authorizing funds to the fraudsters-controlled accounts.
Alternatively, the whaling phishers might trick the executives into revealing their logging credentials. As soon as profitable, the perpetrators might carry out a CEO fraud wherein they use the compromised account of an govt to fraudulently authorize cost to their accounts.
Vishing
Vishing is a method wherein perpetrators use telephones to rip-off unsuspecting customers. The attackers faux to be representatives from respected organizations akin to banks, phone corporations, and so on.

In the course of the name, they could trick you into offering delicate data such because the cell phone line pin. They might additionally request that you just ship some cash to a selected account.
Some criminals might use a hybrid method. On this case, they may first ship a rip-off e mail and observe it with a phone or vishing name, making it look extra real.
E mail Phishing
E mail phishing is when a fraudster sends hundreds of generic messages to completely different customers, hoping that some will fall prey and make funds to the attacker. Usually, they design phishing messages that mimic reputable emails from a trusted firm.

These messages could have the identical templates, logos, signatures, phrasing, and different options that make them seem reputable. In addition to the messages, they create a site that intently resembles that of a reputable firm, making it laborious to suspect something until after scrutiny.
The fraudsters will even create a way of urgency and threats, akin to an account about to run out, until the person takes motion, akin to resetting the password or paying some cash.
Misleading Phishing
Misleading phishing entails perpetrators who impersonate a identified and acquainted e mail sender. Fraudsters usually some reputable hyperlinks and contacts in malicious emails. As such, the e-mail filters can’t block or flag the messages as spam.
For the reason that e mail seems to be real, the attacker might lead the person to disclose delicate data akin to banking data, login credentials, or some delicate firm information.
Criminals trick customers by asking them to vary passwords, confirm an account, make funds, and so on.
Clone Phishing Assaults
In clone phishing, the fraudsters create an e mail tackle just like the reputable one. They then e mail a person, who might share delicate data with the criminals if not cautious.
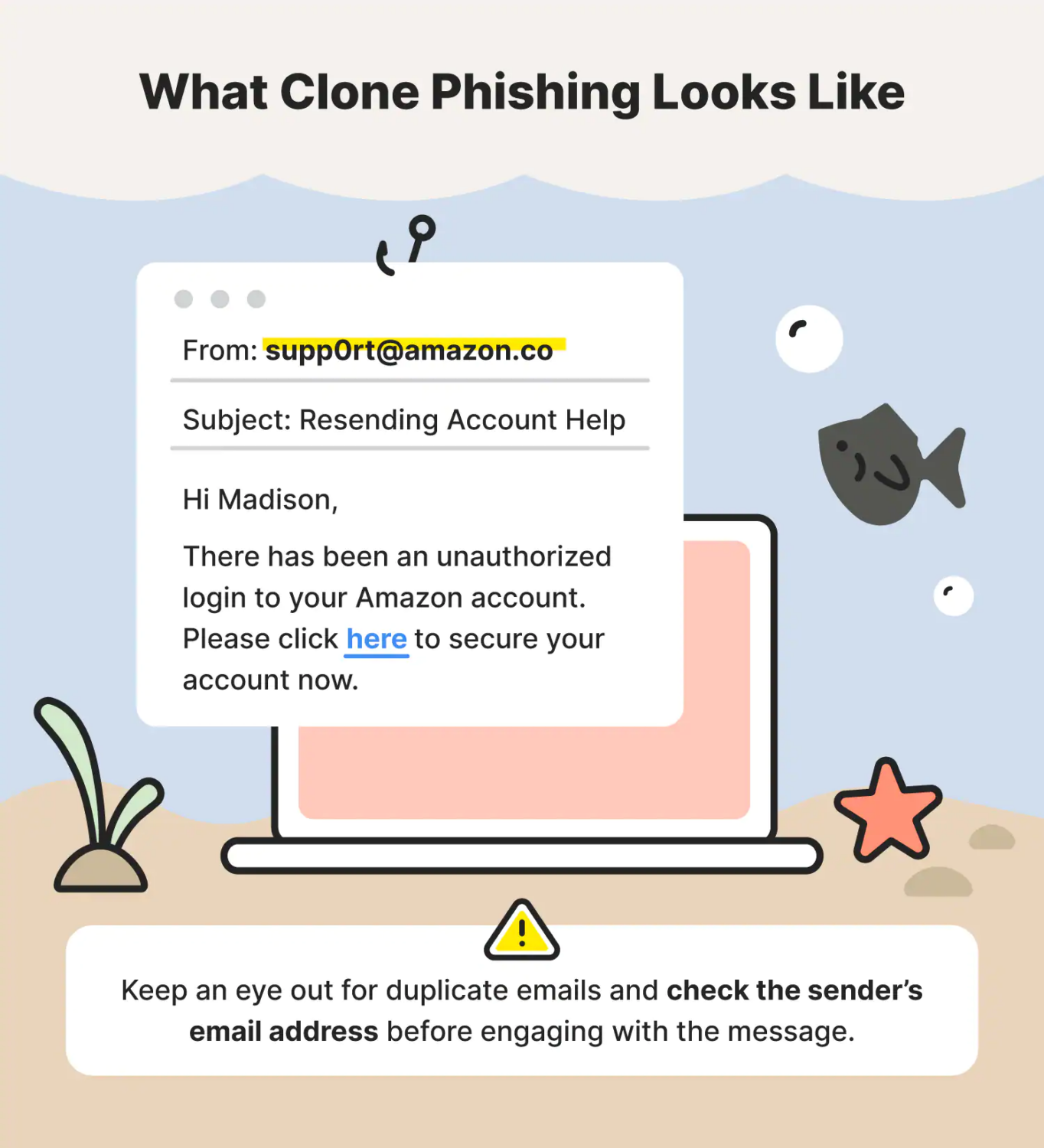
For instance, an attacker might ship a message that appears like it’s coming out of your boss and requesting you to share login credentials for a sure account. They could additionally masquerade as a vendor and request some cost particulars.
Angler Phishing
Angler phishing is an assault that targets customers by cloned web sites, pretend non-public messages, or social media. On this phishing, the perpetrator seems to be for his or her goal victims by social media. They then determine the individuals who complain rather a lot a few respected financial institution, service supplier, or different identified group.
The fraudster then masquerades as a buyer assist official from the group and gives to assist the complainer. At this level, the attacker methods the sufferer into sharing login credentials or different delicate information.
Tips on how to Establish Phishing Makes an attempt
One of many efficient strategies of figuring out spear and different phishing makes an attempt is the SPEAR, as defined under.
- Spot the e-mail or message sender
- Peruse the topic and guarantee it’s related to what you do and that it doesn’t hold forth or uncommon to what you normally obtain
- Examine the attachments and hyperlinks within the message. Hover over the hyperlinks to see if they’re related and matches the topic or requested motion
- Assess the message to see whether it is related and doesn’t comprise an unfamiliar tone, urgency, inconsistencies, grammar errors, or spelling errors
- Request affirmation from the real e mail account proprietor. Think about checking with the stated sender if they’ve despatched you that message.
In addition to the above, listed here are extra suggestions.
- The e-mail has inconsistent domains, URLs, hyperlinks, and e mail addresses
- A generic or uncommon greeting, salutation, and language
- E mail messages requesting private or non-public information akin to bank card particulars, cost data, login credentials, and so on.
- An e mail message with a requirement for pressing motion, akin to a requirement to vary password, pay some cash, and different actions
Now, let’s discover how we are able to forestall phishing assaults.
Stopping Phishing Assaults
Organizations and customers can take varied measures to forestall phishing assaults. Let’s take a look at it.
#1. Implementing a Strict Password Administration Coverage
Admins may set up and implement sturdy password administration insurance policies. In such circumstances, they need to require sturdy passwords that customers should change usually. Moreover, customers shouldn’t use a single password for a number of functions and ought to be prevented from reusing older passwords.
#2. Use Multi-Issue Authentication
Multifactor authentication ensures {that a} person passes a number of verification ranges earlier than accessing a service, akin to a monetary transaction. Even when an attacker obtains the credentials, akin to a username and password, they may nonetheless require one other type of authentication, akin to offering a code despatched to the real person’s registered gadget, akin to a cell phone.
Different multifactor strategies embrace biometrics, badges, OTPs, Pins, and extra. Since it’s not possible for the attacker to cross the second authentication, even once they have the password, it’s not possible to entry and compromise the programs.
#3. Creating Worker Consciousness
Conducting consciousness campaigns for workers and the manager is a method of decreasing the dangers of phishing assaults. Its goal ought to be to advertise secure on-line actions and empower the employees, together with the manager, to determine and act on malicious emails.
Customers ought to know the dangers of clicking hyperlinks or opening paperwork that look suspicious, in addition to revealing delicate data to strangers. Moreover, they need to be discouraged from posting delicate private and firm data on social media.
#4. Set up E mail Safety Software program and Instruments
Set up dependable and efficient e mail safety software program to detect and cease phishing scams and different threats. Typical options embrace antivirus software program, firewalls, spam filters, and extra. Moreover, the group can set up internet filters to detect malicious web sites and forestall workers from accessing them.
#5. Not Clicking on the Hyperlink
Customers ought to keep away from clicking on hyperlinks or attachments from unfamiliar senders. You will need to take precautions when appearing on such emails, together with people who seem like from reliable sources.
In case it seems to be suspicious, confirm the hyperlinks by both hovering over them or copying them to a brand new browser window to see if it matches the content material of the e-mail.
#6. Guaranteeing E mail Is From a Dependable Area
Customers ought to keep away from opening or appearing on emails from suspicious domains. For instance, if somebody sends you an e mail purporting to be from Microsoft, they’re utilizing an e mail tackle with a unique area. If unsure, copy the area title and seek for it on the web.
If its content material doesn’t correspond with the message, it’s best to deal with it suspiciously. Though most phishing emails are marked as SPAM, some might cross the spam filter and seem real.
#7. Keep away from Giving Data on an Unsecured Web site
If a hyperlink takes you to an unfamiliar web site, you shouldn’t present any delicate or non-public data. It’s best to by no means disclose your organization’s or private information to strangers; in any other case, the fraudsters might steal this data and carry out unauthorized actions.
Closing Phrases
Phishing assaults have been on the rise and don’t appear to be slowing down as fraudsters proceed adopting new methods. Whereas the group can enhance its safety posture, dangerous person conduct is without doubt one of the main contributors to phishing assaults.
As such, utilizing dependable safety instruments and secure on-line person conduct is without doubt one of the simplest methods of stopping assaults and making certain the safety and security of your delicate enterprise information.
Subsequent, you may try the very best URL scanners to examine if a hyperlink is secure.

