Privilege escalation assaults happen when dangerous actors exploit misconfigurations, bugs, weak passwords, and different vulnerabilities that permit them to entry protected property.
A typical exploit could begin with the attacker first getting access to a low-level privilege account. As soon as logged in, attackers will examine the system to establish different vulnerabilities they will exploit additional. They then use the privileges to impersonate the precise customers, acquire entry to focus on assets, and carry out varied duties undetected.
Privilege escalation assaults are both vertical or horizontal.
In a vertical kind, the attacker features entry to an account after which execute duties as that consumer. For the horizontal kind, the attacker will first acquire entry to a number of accounts with restricted privileges, after which compromise the system to achieve extra permissions to carry out administrative roles.
Such permissions allow the attackers to carry out administrative duties, deploy malware, or do different undesirable actions. For instance, they will disrupt operations, modify safety settings, steal information, or compromise the methods such that they go away open backdoors to take advantage of sooner or later.

Usually, identical to the cyber-attacks, privilege escalation exploits the system and course of vulnerabilities within the networks, companies, and functions. As such, it’s attainable to stop them by deploying a mixture of fine safety practices and instruments. A company ought to ideally deploy options that may scan, detect, and forestall a variety of potential and current safety vulnerabilities and threats.
Finest practices to stop privilege escalation assaults
Organizations should shield all their vital methods and information in addition to different areas which will look enticing to the attackers. All that an attacker requires is to penetrate a system. As soon as inside, they will search for vulnerabilities that they exploit additional to achieve extra permissions. Aside from defending the property towards exterior threats, it’s equally vital to place sufficient measures to stop inside assaults.
Whereas precise measures could differ in keeping with the methods, networks, atmosphere, and different components, under are some methods organizations can use to safe their infrastructure.
Defend and scan your community, methods, and functions
Along with deploying a real-time safety resolution, it’s important to often scan all of the elements of the IT infrastructure for vulnerabilities that would permit new threats to penetrate. In the direction of this, you need to use an efficient vulnerability scanner to search out unpatched and insecure working methods and functions, misconfigurations, weak passwords, and different flaws that attackers can exploit.

Whereas you need to use varied vulnerability scanners to establish weaknesses in outdated software program, it’s often tough or not sensible to replace or patch all of the methods. Particularly, it is a problem when coping with legacy elements or massive scale manufacturing methods.
For such circumstances, you may deploy extra safety layers akin to net software firewalls (WAF) that detect and cease malicious site visitors on the community stage. Usually, the WAF will shield the underlying system even when it’s unpatched or outdated.
Correct privilege account administration
You will need to handle the privileged accounts and be sure that they’re all safe, used in keeping with the very best practices, and never uncovered. The safety groups have to have a list of all of the accounts, the place they exist, and what they’re used for.
Different measures embody
- Minimizing the quantity and scope of the privileged accounts, monitoring, and maintaining a log of their actions.
- Analyzing every privileged consumer or account to establish and handle any dangers, potential threats, sources, and attacker’s intents
- Main assault modes and prevention measures
- Observe the least privilege precept
- Stop admins from sharing accounts and credentials.
Monitor consumer habits
Analyzing consumer habits can uncover if there are compromised identities. Normally, the attackers will goal the consumer identities which offer entry to the group’s methods. In the event that they succeed to acquire the credentials, they’ll log into the community and should go undetected for a while.
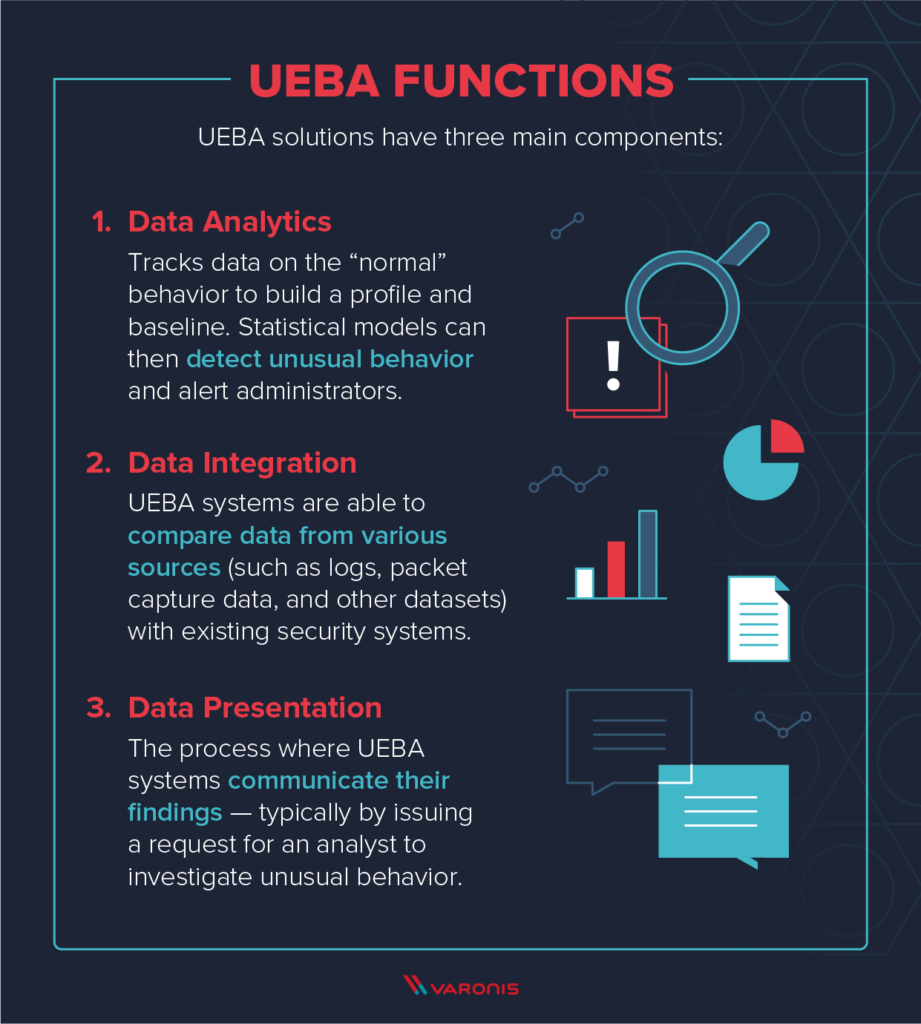
Since it’s tough to manually monitor every consumer’s habits, the very best method is to deploy a Consumer and Entity Conduct Analytics (UEBA) resolution. Such a instrument repeatedly screens consumer exercise over time. It then creates a professional habits baseline which it makes use of to find uncommon actions which are indicative of a compromise.
The ensuing profile accommodates data akin to location, assets, information information and companies the consumer accesses and frequency, the particular inside and exterior networks, variety of hosts in addition to processes executed. With this data, the instrument can establish suspicious actions or parameters that deviate from the baseline.
Sturdy password insurance policies and enforcement
Set up and implement robust insurance policies to make sure that the customers have distinctive and laborious to guess passwords. Moreover, utilizing a multi-factor authentication provides an additional layer of safety whereas overcoming the vulnerabilities which will come up when it’s tough to manually implement robust password insurance policies.
Safety groups also needs to deploy the mandatory instruments akin to password auditors, coverage enforcers, and others that may scan methods, establish and flag weak passwords, or immediate for motion. The enforcement instruments be sure that customers have robust passwords when it comes to size, complexity, and firm insurance policies.
Organizations also can use enterprise password administration instruments to assist customers generate and use advanced and safe passwords that adjust to insurance policies for companies that require authentication.
Extra measures akin to multi-factor authentication to unlock the password supervisor improve its safety additional therefore making it nearly unattainable for attackers to entry the saved credentials. Typical enterprise password managers embody Keeper, Dashlane, 1Password.
Sanitize consumer inputs and safe the databases
The attackers can use susceptible consumer enter fields in addition to databases to inject malicious code, acquire entry, and compromise the methods. For that reason, safety groups ought to use finest practices akin to robust authentication and efficient instruments to guard the databases and all types of information enter fields.
A superb observe is to encrypt all the info in transit and at relaxation along with patching the databases and sanitizing all consumer inputs. Extra measures embody leaving information with read-only and giving the write entry to the teams and customers who require them.
Practice customers
The customers are the weakest hyperlink in a company’s safety chain. It’s due to this fact vital to empower them and prepare them on how one can carry out their duties securely. In any other case, a single click on from a consumer can result in the compromising of a complete community or system. A number of the dangers embody opening malicious hyperlinks or attachments, visiting compromised web sites, utilizing weak passwords, and extra.

Ideally, the group ought to have common safety consciousness applications. Additional, they need to have a strategy to confirm that the coaching is efficient.
Privilege escalation assaults prevention instruments
Stopping the privilege escalation assaults requires a mixture of instruments. These embody however not restricted to the options under.
Privileged Entry Administration (PAM) software program options
Heimdal
Heimdal’s Privileged Entry Administration (PAM) is an enterprise-grade safety resolution designed to assist organizations safe their most important property and information by controlling privileged entry to delicate methods and functions. The product offers a complete set of instruments to handle, monitor, and audit privileged entry, whereas implementing least privilege ideas and lowering the assault floor.
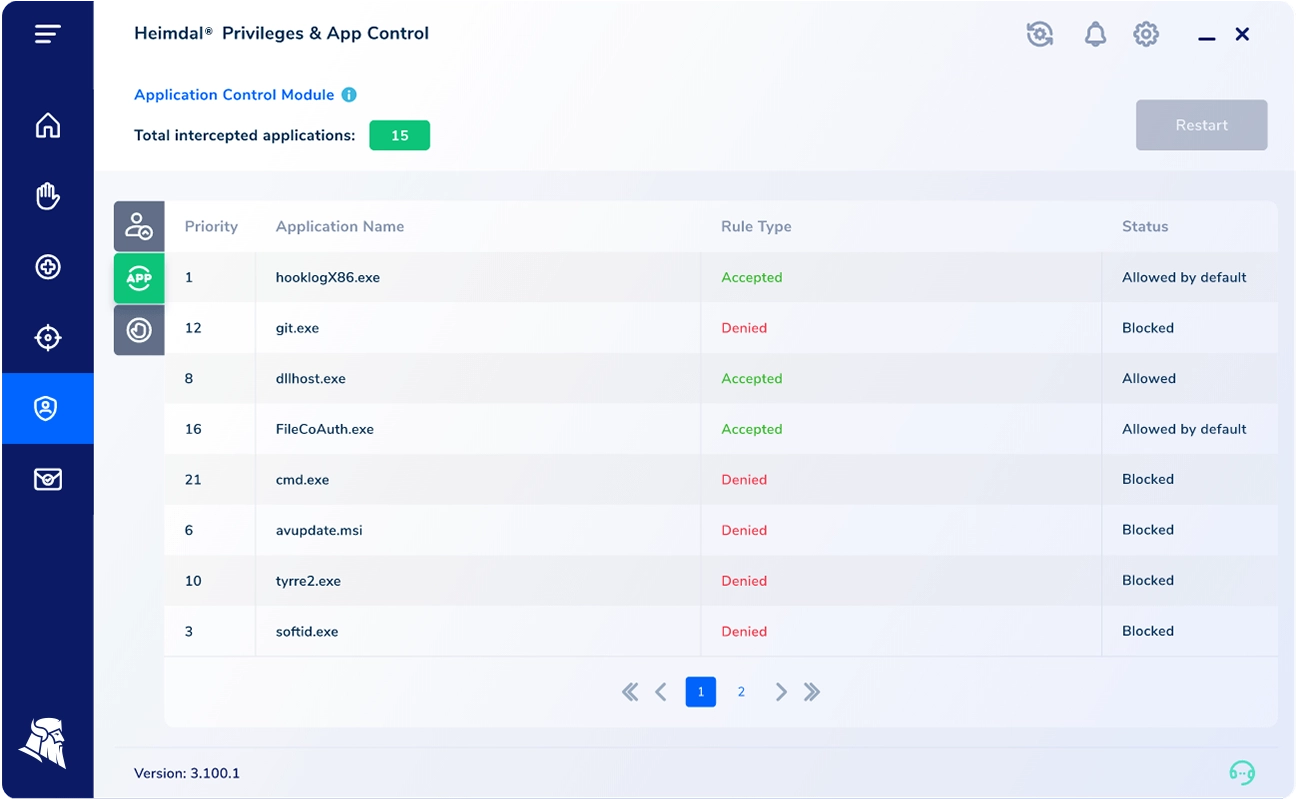
With Heimdal’s PAM resolution, organizations can simply establish and handle privileged accounts throughout their IT infrastructure, together with on-premises and cloud environments, through the use of a centralized dashboard. It offers granular management over entry rights and permissions, permitting directors to outline insurance policies and implement multi-factor authentication, session recording, and password administration to make sure safe entry to vital methods and information.
It additionally consists of a number of superior options, akin to session monitoring and recording, which offers real-time visibility into privileged consumer actions, serving to detect and reply to suspicious habits. Moreover, it gives automated workflows to streamline entry request and approval processes, lowering the burden on IT groups and guaranteeing compliance with trade laws and requirements.
The answer’s reporting and analytics capabilities present insights into consumer habits, audit trails, and compliance standing, permitting organizations to proactively establish and mitigate dangers and vulnerabilities.
Heimdal’s PAM resolution additionally integrates with current IT methods and functions, offering seamless entry administration throughout the group. Total, Heimdal’s PAM resolution gives a complete and easy-to-use resolution for managing privileged entry, lowering the danger of information breaches, and guaranteeing compliance with trade requirements and laws. With its superior options and integration capabilities, the answer offers a strong protection towards cyber threats and helps organizations obtain a powerful safety posture.
JumpCloud
Jumpcloud is a Listing as a Service (DaaS) resolution that securely authenticates and connects customers to networks, methods, companies, apps, and information. Usually, the scalable, cloud-based listing is a service that manages, authenticates, and authorizes customers, functions, and units.
Options embody;
- It creates a safe and centralized authoritative listing
- Helps cross-platform consumer entry administration
- Gives single sign-on capabilities that assist controlling consumer entry to functions by way of LDAP, SCIM, and SAML 2.0
- Gives safe entry to on-premise and cloud servers
- Helps multi-factor authentication
- Has automated administration of safety and associated capabilities akin to occasion logging, scripting, API administration, PowerShell, and extra
Ping Id
Ping Id is an clever platform that gives multi-factor authentication, single sign-on, listing companies, and extra. It allows organizations to reinforce consumer identification safety and expertise.
Options
- Single sign-on that present safe and dependable authentication and entry to companies
- Multi-factor authentication that provides additional safety layers
- Enhanced information governance and talent to adjust to privateness laws
- A listing companies that present safe administration of consumer identities and information at scale
- Versatile cloud deployment choices akin to Id-as-a-Service (IDaaS), containerized software program, and so forth.
Foxpass
Foxpass is a scalable enterprise-grade identification and entry management resolution for on-premise and cloud deployments. It offers RADIUS, LDAP, and SSH key administration options which ensures that every consumer solely accesses particular networks, servers, VPNs, and different companies on the time allowed.
The instrument can combine seamlessly with different companies akin to Workplace 365, Google Apps, and extra.
AWS Secrets and techniques Supervisor
AWS Secrets and techniques Supervisor offers you with a dependable and efficient means to safe the secrets and techniques required to entry the service, functions, and different assets. It means that you can simply handle, rotate, and retrieve the API keys, database credentials, and different secrets and techniques.
There are extra secret administration options you may discover.
Consumer and Entity Conduct Analytics resolution (UEBA)
Exabeam
The Exabeam Safety Administration Platform is a fast and straightforward to deploy an AI-based behavioral analytics resolution that helps to trace consumer and account actions throughout totally different companies. You can too use Exabeam to ingest the logs from different IT methods and safety instruments, analyze them, and establish and flag dangerous actions, threats, and different points.
Options embody
- Logging and offering helpful data for incident investigations. These embody all periods when a selected account or consumer accessed a service, server or software, or useful resource for the primary time, account logs in from a brand new VPN connection, from an uncommon nation, and so forth
- The scalable resolution is relevant for a single occasion, cloud, and on-premise deployments
- Creates a complete timeline that clearly reveals the total path of an attacker primarily based on the traditional and irregular account or consumer habits.
Cynet 360
The Cynet 360 Platform is a complete resolution that gives behavioral analytics, community, and endpoint safety. It means that you can create consumer profiles together with their geolocations, roles, working hours, entry patterns to on-premise and cloud-based assets, and so forth.
The platform helps to establish uncommon actions akin to;
- First-time logins to the system or assets
- Uncommon login location or utilizing a brand new VPN connection
- A number of concurrent connections to a number of assets inside a really brief time
- Accounts that entry assets off-hours
Password safety instruments
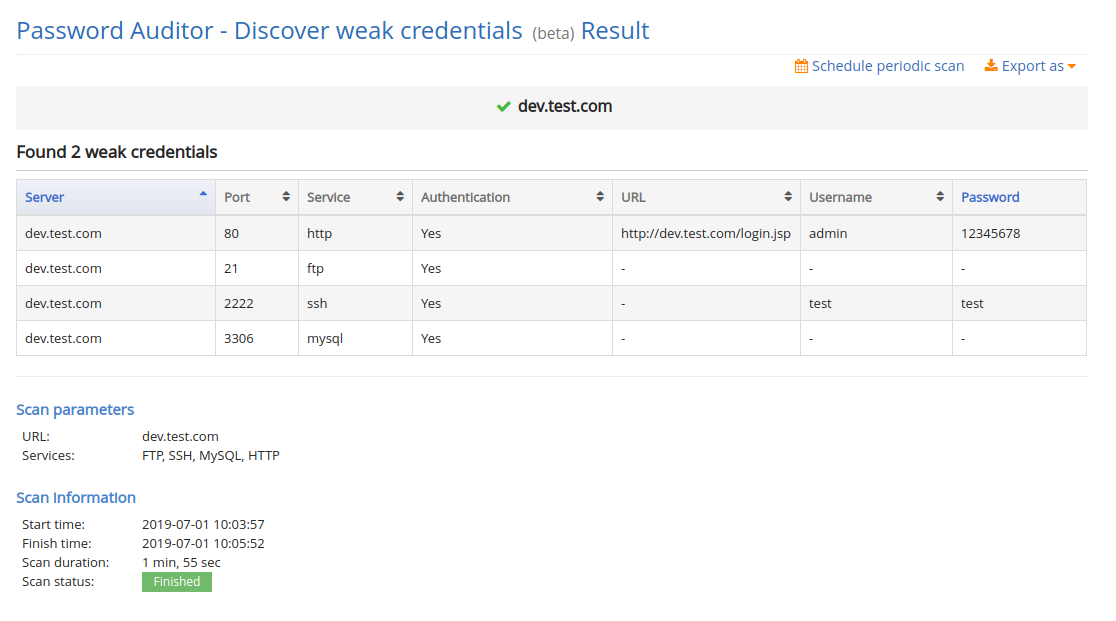
Password Auditor
The password auditor instruments scan the hostnames and IP addresses to routinely establish weak credentials for community companies and net functions akin to HTTP net kinds, MYSQL, FTP, SSH, RDP, community routers, and others that require authentication. It then makes an attempt to log in utilizing the weak, and the widespread username and password combos to establish and alert about accounts with weak credentials.
Password Supervisor Professional
The ManageEngine password supervisor professional offers you with complete administration, management, monitoring, and auditing resolution of the privileged account all through its complete lifecycle. It will possibly handle the privileged account, SSL certificates, distant entry in addition to the privileged session.
Options embody
- Automates and enforces frequent password resets for vital methods akin to servers, community elements, databases, and different assets
- Shops and organizes all of the privileged and delicate account identities and passwords in a centralized and safe vault.
- Allows organizations to satisfy the vital safety audits in addition to compliance with regulatory requirements such because the HIPAA, PCI, SOX, and extra
- Permits group members to securely share administrative passwords.
Vulnerability scanners
Invicti
Invicti is a scalable, automated vulnerability scanner, and administration resolution that may scale to satisfy any group’s necessities. The instrument can scan advanced networks and environments whereas seamlessly integrating with different methods together with the CI/CD options, SDLC, and others. It has superior capabilities and is optimized to scan and establish vulnerabilities in advanced environments and functions.
Moreover, you need to use Invicti to check the online servers for safety misconfigurations that attackers can exploit. Usually, the instrument identifies SQL Injections, distant file inclusion, Cross-site Scripting (XSS), and different OWASP Prime-10 vulnerabilities in net functions, net companies, net pages, APIs, and extra.
Acunetix
Acunetix is a complete resolution with built-in vulnerability scanning, administration, and straightforward integration with different safety instruments. It helps to automate vulnerability administration duties akin to scanning and remediation therefore enabling you to save lots of on assets.
Options embody;
- Integrates with different instruments akin to Jenkins, third occasion points trackers akin to GitHub, Jira, Mantis, and extra.
- On-premise and cloud deployment choices
- Customizable to swimsuit the client atmosphere and necessities in addition to cross-platform assist.
- Rapidly establish and reply to a variety of safety points together with, widespread net assaults, Cross-site Scripting (XSS), SQL injections, malware, misconfigurations, uncovered property, and so forth.
Conclusion
Identical to the cyber-attacks, privilege escalation exploits the system and processes vulnerabilities within the networks, companies, and functions. As such, it’s attainable to stop them by deploying the best safety instruments and practices.
Efficient measures embody implementing the least privileges, robust passwords, and authentication insurance policies, defending delicate information, lowering the assault floor, securing the accounts credentials, and extra. Different measures embody maintaining all methods, software program, and firmware up-to-date and patched, monitoring consumer habits, and coaching customers on secure computing practices.

