Keep tuned whereas we inform you about a few of the notorious cyber extortion makes an attempt and the attainable methods to cease them upfront.
A financial institution theft may be very unsafe for a complicated dangerous actor. It bodily jeopardizes the prison whereas it occurs and awards hefty punishments if caught.
In distinction, you stay largely untouched for those who orchestrate a futuristic ransomware assault.
Conclusively, cyber extortions are far much less dangerous and extra worthwhile compared to typical thefts or robberies. As well as, the weaker penalties have additional favored cybercriminals.
Issue within the untraceable cryptocurrencies, and we must always already begin strengthening our defenses.
Cyber Extortion is a web-based assault to extract hefty ransom quantities. That is normally accomplished by threatening server failures with a DDoS assault or encrypting your information, denying entry.
Cyber extortion is an act of blackmail in these varieties:
Knowledge Hostage
A foul actor stops you from accessing your community of computer systems and asks for a ransom to revive entry. This usually occurs while you by accident click on a malicious hyperlink that downloads malware, encrypts the recordsdata, and locks you out.
Alternatively, somebody hijacks your system, copies delicate information, and frightens you to pay or danger exposing that to most of the people. This generally entails social engineering through which they only play psychological tips making you falsely imagine the hack when there may be none.
DDoS
Typically used to cowl up a knowledge theft, Distributed Denial of Service (DDoS) is when your community is flooded with pretend service requests stopping your precise customers from getting in.
That is carried out with a community of contaminated servers (botnets) or by memcaching, inflicting server slowdowns or failure. Relying on the size of your on-line enterprise, losses may be big.
One can simply fund a DDoS assault for as little as $4 per hour whereas inflicting tons of of 1000’s in loss to the sufferer. Apart from the instant loss, downtime pushes your prospects to the rivals inflicting further damages over time.
Main Cyber Extortion Assaults
Let’s check out a few of the largest such occasions recorded previously.
#1. WannaCry
Beginning on twelfth Might 2017, WannaCry was a world ransomware assault on computer systems operating Microsoft Home windows. Its precise scale is but unknown as a result of it nonetheless persists in some varieties.
On the primary day in workplace, WannaCry contaminated 230K computer systems in 150+ international locations. This affected huge corporates and governments all over the world. It might copy, set up, execute, and unfold itself inside the community with none human interplay.
With WannaCry, Hackers took benefit of a Home windows vulnerability utilizing the exploit EternalBlue. Apparently, EternalBlue was developed by the US NSA to use a Home windows vulnerability. The exploit code by some means received stolen and revealed by a hacker group named The Shadow Brokers.
Microsoft, realizing about the issue, issued an replace to patch it. However the majority of customers who had been operating outdated programs grew to become the prime goal.
The savior this time was Marcus Hutchins, who by accident sinkholed the malware by registering a site talked about within the exploit code. That labored as a kill change and stored WannaCry at bay. However there may be much more to it, together with the kill change struggling a DDoS assault, Hutchins dealing with over the kill change to Cloudflare which you can seize at TechCrunch.
International estimated losses are round $4 billion.
#2. CNA Monetary
On March 21, 2021, Chicago-based CNA Monetary got here to know that somebody copied delicate private information of their staff, contract employees, and their dependents. This got here to mild after greater than two weeks, because the hack was going undetected from March 5, 2021.
This was a hybrid assault that included information theft in addition to protecting the CNA system hostage. The hackers, a Russia-based hacking group Evil Corp, used malware to encrypt CNA servers. After negotiations on the preliminary ransom quantity of $60 million, the hackers lastly settled for $40 million, as per Bloomberg.
#3. Colonial Pipeline
Colonial Pipeline hack brought about disruptions in gasoline provide from one of many largest pipelines within the USA. The investigation revealed that it was the results of a single password leak on the darkish net.
Nonetheless, it was unknown how the dangerous actors received the proper username matching the compromised password. The hackers accessed Colonial programs utilizing a Digital Non-public Community meant for distant staff. Since there was no multi-factor authentication, a username and password had been all however sufficient.
After per week of this exercise, on Might 7, 2021, one of many present staff noticed a ransom word demanding $4.4 million in cryptocurrencies. Inside hours, the officers shut the whole pipeline employed cyber safety corporations to confirm and mitigate the harm. Additionally they seen a 100GB information theft, and the hacker threatened to reveal it within the occasion of non-payment of the ransom quantity.
The ransomware crippled the billing and accounting part of Colonial IT programs. The ransom quantity was paid shortly after the assault to DarkSide, a hacking group based mostly in japanese Europe. DarkSide supplied a decryption device that proved so sluggish that it took per week to normalize the pipeline operations.
Apparently, the US Division of Justice launched a public assertion on June 7, 2021, citing the restoration of 63.7 bitcoins from the unique cost. In some way, the FBI received maintain of the personal keys associated to the hacker accounts and introduced again $2.3 million, apparently lower than that was paid owing to the sudden stoop in bitcoin costs in that interval.
#4. Dyn
Along with doing many issues web, Dyn primarily acts as a DNS service supplier for a few of the huge names, together with Twitter, Netflix, Amazon, Airbnb, Quora, CNN, Reddit, Slack, Spotify, PayPal, and so on. These had been introduced down with a significant DDoS assault on October 21, 2016.
The attacker used the Mirai botnet, which deployed numerous compromised IoT gadgets to ship false DNS requests. This visitors jammed the DNS servers inflicting excessive slowdowns piling an unknown quantity of losses worldwide.
Whereas the size of the assault makes it troublesome to calculate the precise quantity of injury suffered by the web sites, Dyn misplaced huge.
Round 14,500 domains (roughly 8%) switched to a unique DNS supplier instantly after the assault.
Whereas many extra suffered comparable assaults just like the Amazon Internet Companies, GitHub, let’s keep away from going off-road and transfer into drawing a rock-solid technique to stop such cyber extortion occasions.
Learn how to Stop Cyber Extortion?
A few of the very fundamental preventive measures that may allow you to protect towards such web assaults are:
#1. Keep away from Clicking Malicious Hyperlinks
Attackers usually make the most of this infantile attribute of human psychology: curiosity.

Phishing Emails had been the gateway of round 54% of ransomware assaults. So, along with reminding your self and your staff about spam emails, manage workshops.
This may embrace dummy phishing emails with weekly campaigns to supply reside coaching. It’s going to work extra like vaccinations through which a small quantity of useless virus hundreds shield towards reside threats.
Moreover, you’ll be able to practice staff in sandboxing-like applied sciences to open suspicious hyperlinks and functions.
#2. Software program Updates and Safety Options
Regardless of your OS, outdated software program is inclined to cyber extortion assaults. Folks might simply have prevented WannaCay had they up to date their Home windows PCs in time.
Yet another frequent false impression is you’re secure if utilizing a Mac. That’s fully unfaithful. And Malwarebytes state of malware report tears via any false sense of safety amongst Mac customers.
Home windows OS has seen main assaults just because Mac wasn’t that common. Microsoft’s OS nonetheless has a market share of near 74%, and focusing on Mac customers isn’t merely definitely worth the hassle.
However since that’s slowly altering, Malwarebytes witnessed a 400% bounce in threats geared toward Mac OS from 2018 to 2019. As well as, they famous 11 threats per Mac compared to 5.8 threats for a Home windows system.
Conclusively, investing in a complete web safety answer like Avast One can undoubtedly show its price.
Moreover, you’ll be able to deploy intruder detection programs like Snort or Suricata for a greater security web.
#3. Use Sturdy Passwords
The Colonial Pipeline assault was brought about resulting from an worker utilizing a weak password twice.
As per an Avast survey, about 83% of People use weak passwords, and as many as 53% use the identical passwords on a number of accounts.
Admittedly, pushing customers to make use of robust passwords for their very own has already proved an uphill activity. Asking them to try this at work appears almost inconceivable.
So, what’s the answer? Person authentication platforms.
You may make use of those platforms to implement robust passwords necessities at your group. These are Third-party specialists with versatile plans in keeping with the corporate’s dimension. You may as well begin with always-free tiers with Ory, Supabase, Frontegg, and so on.
At a private degree, use password managers.
Furthermore, take the ache of updating passwords now and again. It will guarantee your security even when your credentials get stolen by some means. And that’s an entire lot simpler with premium password managers like Lastpass, which might auto-update your passwords with only a click on.
However don’t simply cease with a sophisticated password; strive being artistic with the username too.
#4. Offline Backups
The sophistication degree of such assaults can generally trick even the big-name cybersecurity consultants, not to mention a small enterprise proprietor.
Subsequently, maintain up to date backups. It will assist deliver your system up on a fateful day.
And offline backups are an added benefit. They’re your safe chilly storage, unreachable by cyber extortionists.
Apart from, pay attention to the accessible restore capabilities as a result of extended downtimes can generally make the requested ransom look profitable. And that’s exactly why some enterprise house owners negotiate with the menace actors and find yourself paying big quantities.
Alternatively, Third-party backup and information restoration options like Acronis can turn out to be useful. They supply ransomware safety and hassle-free information restoration mechanisms.
#5. Content material Supply Community (CDN)
Many have detected and averted huge DDoS assaults due to competent content material supply networks.
As mentioned above, it was, in any case, a wonderful CDN, Cloudflare, which maintained the WannaCry killswitch on-line continuous for 2 years. It additionally helped it to resist quite a few DDoS assaults inside that timeframe.
A CDN maintains a cached copy of your web site across the globe on a number of servers. They switch extra hundreds to their community, avoiding server overloads and downtimes.
This technique not solely protects towards DDoS threats however ends in blazingly quick web sites for worldwide prospects.
Lastly, there can’t be an entire checklist to guard you towards cyber extortion. Issues evolve, and it’s finest to have a cybersecurity professional on board each time.
However what if it occurs anyway? What ought to be your plan of action for those who get hit with a web-based extortion try.
Cyber Extortion Response
The very first thing that involves thoughts after a ransomware assault aside from the same old anxiousness is to pay and get accomplished with it.
However that won’t all the time work.
A survey performed by SOPHOS, a UK-based IT safety agency, exhibits that paying the ransom isn’t one of the simplest ways out. The assault survey report mentions that solely 8% of firms received the whole information again after paying the ransom. And 29% had been capable of restore solely 50% or much less of the stolen/encrypted information.
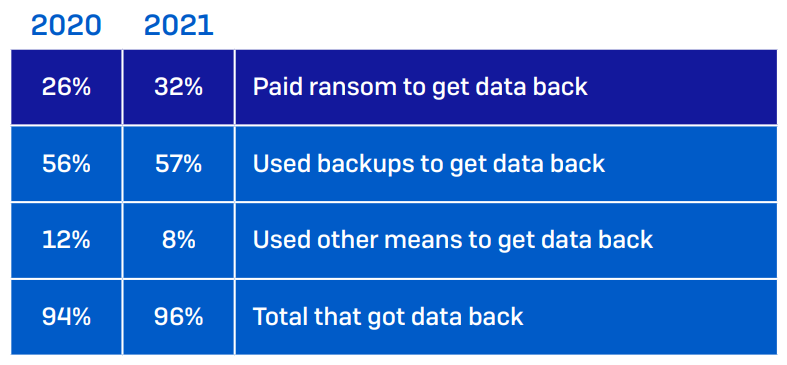
So, your act of compliance with ransom calls for might backfire. It makes you depending on the dangerous actor and his instruments to decrypt your information delaying different rescue efforts.
Furthermore, there is no such thing as a assure that the device given by the hacker will ever work. It might fail or additional infect your system. As well as, paying the criminals highlights your group as their paying prospects. So, there’s a very excessive probability of the same assault sooner or later.
Conclusively, paying ought to be your final resort. Utilizing different strategies like restoring backups is safer than paying an unknown prison with cryptocurrencies.
As well as, a number of corporations contacted main cybersecurity consultants and knowledgeable the legislation enforcement authorities. And that’s what saved them, like within the case of Colonial Pipeline extortion restoration by the FBI.
Cyber Extortion: Conclusion
It is best to word that it’s not as unusual as one might imagine. And the clearly finest method is to bolster your shields and maintain backups.
If it occurs regardless, maintain calm, begin native rescue operations, and get in touch with consultants.
However strive to not give in to the ransom calls for as a result of that may not work even for those who pay your fortunes out.
PS: Going via our cybersecurity guidelines for your enterprise might show useful.



