Cyber resilience is the flexibility of a company to maintain its community, methods, functions, and information on-line no matter cyberattacks and threats.
Regardless of the provision of fine safety instruments, hackers and cybercriminals are discovering methods to use some vulnerabilities. Consequently, they will nonetheless conduct profitable cyber-attacks on protected methods. Organizations ought to, subsequently, be ready to get better from such assaults whereas guaranteeing minimal harm.
Whereas a cyber safety answer protects digital property from assaults, cyber resilience limits the harm, downtimes, service disruptions, and monetary losses cyberattack would trigger.
Moreover, it supplies a possibility to carry out a post-attack evaluation which permits the group to optimize its safety and catastrophe restoration methods.
What Is Cyber Resilience?
Cyber resilience is the flexibility of a company to plan, put together, detect, face up to, and get better from a cyber-attack, compromises, and different safety incidents. It limits the influence of a cyber-attack, thus minimizing the harm and related losses.
The target of a cyber resilience program is to make sure enterprise continuity regardless of the safety challenges that maintain evolving day-after-day. An excellent technique helps scale back an assault’s influence, guaranteeing continued enterprise operations.
With ever-evolving cyber threats, there’s at all times a danger of an assault, even when you may have deployed the strongest safety options. This will increase the danger of surprising occasions that may disrupt regular enterprise operations. For that reason, organizations ought to put in place measures that shield digital property whereas guaranteeing fast restoration in case of an assault.
A typical cyber resilience program entails getting ready, detecting, and responding to assaults and finally recovering from them as rapidly as potential. A company that’s cyber-resilient is best at guaranteeing enterprise continuity throughout and after a cyberattack.
Constructing a Cyber Resilience Technique
Some practices that assist to construct cyber resilience embrace:
- Deploying an efficient safety system to guard all of the community, methods, customers, and information.
- Establishing and implementing efficient and dependable enterprise continuity and catastrophe restoration plan (BCDR).
- Carry out common backups to make sure that the corporate has the newest information and may restore it in case of a breach or compromise. Nonetheless, you will need to have the backup system on a unique and safe community of its personal.
- Reviewing preparedness by performing common checks, simulations, and analyses. Conducting simulation checks permits the group to guage its preparedness and talent to deal with a cyber-attack. It permits groups to determine and deal with any gaps.
- Set up a public relations technique to supply immediate communication to prospects and different stakeholders in case of an assault and restoration. This could guarantee them of continued companies and therefore keep the belief and fame.
- A post-attack evaluation supplies a possibility to determine and deal with weaknesses within the safety methods and preparedness therefore defending the methods in opposition to current and future threats.
Subsequent, we are going to talk about how cyber resilience works.
How Cyber Resilience Works
Cyber resilience combines a number of applied sciences, measures, and practices that present a number of layers of protection and catastrophe restoration. It contains safety, detection, information backup, and catastrophe restoration options.
Consequently, this helps to dam cyber threats, shield the units and information, backup information and rapidly restore companies and information in case of an assault.
Not like cybersecurity which is principally the duty of the IT groups, cyber resilience entails everybody within the group. The IT groups should work with the chief and everybody else throughout the group.
Organizations can take the next steps to enhance their cyber resilience.
#1. Improve General Safety

Enhance the safety practices and measures to stop attackers from gaining entry or penetrating their community and methods.
Among the measures embrace utilizing dependable safety software program and instruments comparable to firewalls, a powerful password coverage, creating safety consciousness throughout the group, utilizing multifactor authentication, and extra.
#2. Detect Assaults and Breaches
Organizations ought to implement a dependable answer to rapidly detect and cease assaults to reduce the influence and harm. A typical answer ought to be capable to constantly monitor the community and pc methods for suspicious actions.
Additionally, the group ought to empower their staff to look at safe utilization of the methods and in addition be capable to determine indicators of compromises, breaches, and different assaults.
#3. Reply to Incidents
The IT groups will need to have a plan and instruments to reply to any detected assault. The plan ought to specify the groups and folks liable for resolving such points and the steps they need to take to reply to the assault. Doing so reduces the influence of the assault.
#4. Recuperate From the Safety Incidence

Companies ought to rapidly get better or restore their methods again to operations after addressing an assault. One technique is to have common backups and a dependable catastrophe restoration plan.
Even when the methods are affected, you ought to be ready to revive the methods and information from the backup rapidly.
Why Is Cyber Resilience Essential for Your Enterprise?
Even with very robust safety, there are nonetheless rising exterior and inner dangers that would end in profitable assaults.
In observe, it’s unimaginable to cease all assaults utterly. That stated, you should develop a technique, put together, reply, and get better from a cyber-attack in case it occurs.
In direction of this, organizations mix cyber safety and cyber resilience to stay aggressive and guarantee enterprise continuity within the occasion of a cyber-attack.
Cyber resilience ensures enterprise continuity even within the occasion of a safety incident. A enterprise that’s effectively ready can rapidly get better and proceed with its operations with little or no downtime and interruption.
Moreover bettering the safety posture, resilience supplies a variety of advantages to the group, prospects, or customers. Beneath are the opposite the reason why cyber resilience is necessary for what you are promoting.
- Stopping monetary losses attributable to downtimes and insecurity by buyers, prospects, and shareholders.
- Ensures enterprise continuity and minimal disruptions to operations within the occasion of a safety incident.
- Good fame and belief by prospects and different stakeholders
- Positive aspects aggressive benefit over different companies that aren’t resilient.
Subsequent, we are going to discover the distinction between cybersecurity and cyber resilience.
Cybersecurity Vs. Cyber Resilience
Cybersecurity focuses on defending digital property in opposition to cyberattacks comparable to malware, ransomware, information breaches, malicious software program, information theft, and extra.
Alternatively, cyber resilience is the flexibility of a company to stop damages and losses whereas guaranteeing the fast and environment friendly resumption of companies within the occasion of a cyberattack.
Whereas cybersecurity limits the threats, cyber resilience limits the harm and related losses following an assault.
Making use of each options implies that, moreover stopping and defending digital property in opposition to assaults, organizations can rapidly and reliably reply and get better from them.
Parts of a Cyber Resilience Program
The next are the main elements of a cyber resilience program.
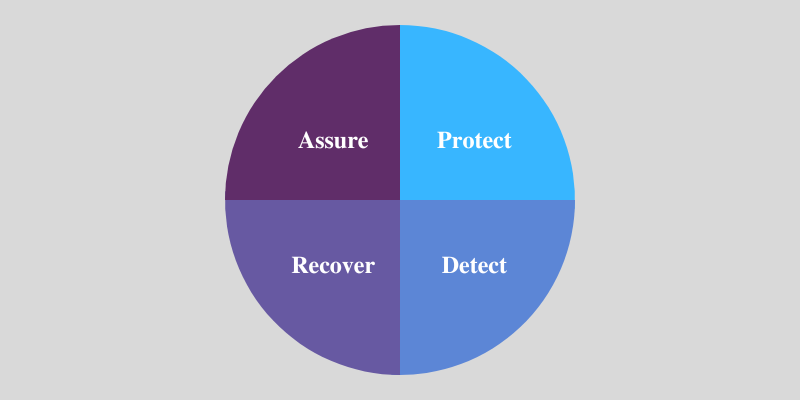
Shield
Safety is the primary stage of a cyber resilience technique. The method entails deploying dependable safety instruments and practices that stop cyber-attacks, unauthorized entry, and system failures. The method helps to guard the customers, networks, methods, units, and processes.
Safety depends on related applied sciences, individuals, processes, and practices. These concentrate on asset administration, safety insurance policies, entry management, encryption, and safety.
Different areas embrace updates and patch administration methods, environmental and bodily safety, coaching and workers consciousness applications, and extra.
Detect
The second step is to constantly monitor the whole infrastructure to detect and act on suspicious actions, assaults, unauthorized entry, and different threats that would compromise the methods.
In observe, the extent and scope of monitoring depend upon the scale and sort of the infrastructure in addition to compliance necessities.
Whereas automated monitoring supplies helpful insights, it’s advisable to additionally do some handbook audits of the logs. This permits groups to determine uncommon actions the automated instruments might have missed.
Recuperate
The group should be ready to rapidly resume regular companies within the occasion of an assault. This requires an environment friendly incident response technique along side enterprise continuity practices that guarantee minimal harm and disruption of companies.
Ideally, the enterprise ought to be capable to rapidly cease the assault and restore affected methods, functions, and information.
The aim of the restoration stage is to rapidly restore clear variations of the methods, functions, and information affected or compromised by the breach.
Guarantee
The final stage for the senior administration to supervise that the cyber resilience is correctly deployed. They need to assist this system whereas guaranteeing that it aligns with the group’s enterprise goals.
The peace of mind entails the dedication and involvement of the senior administration as much as the board stage, establishing a governance construction, and acquiring exterior validation.
Moreover, you will need to carry out inner audits and proceed bettering the processes to deal with current and rising threats.
Advantages of Cyber Resilience
Cyber resilience permits a company to get better from cyber incidents and proceed operations with little interruption. Advantages embrace:
- Fast restoration time therefore elevated productiveness and effectivity since there are fewer downtimes and repair disruptions.
- Improved safety in opposition to cyber threats and assaults. As the corporate builds its cyber resilience technique, it additionally strengthens its cyber safety instruments and practices – making it troublesome to assault sooner or later.
- Complying with authorized and business regulatory necessities.
- Lowering monetary losses.
- Shield the group’s fame and enhance buyer confidence.
- Enhance total safety posture and catastrophe restoration practices.
Now, let’s discover a few of the finest studying sources for cyber resilience.
Studying Assets
A cyber resilience program might differ from one group to the opposite. And there are nice sources that may allow you to on the journey. If you’re within the technique of creating or bettering your cyber resilience technique, listed below are some sources.
#1. Digital Resilience: Is Your Firm Prepared for the Subsequent Cyber Risk?
As we speak, the query shouldn’t be in case your group will probably be attacked however when. As a supervisor, is your group ready for the inevitable? Do you monitor your networks to detect and comprise cyber-attacks and proceed service supply throughout and after assaults? Do you may have a restoration plan?
Sadly, only some organizations are ready to deal with cyber-attacks whereas guaranteeing minimal harm and repair disruption. The Digital Resilience ebook guides you on the right way to construct an efficient cyber resilience technique.
| Preview | Product | Score | Value | |
|---|---|---|---|---|
|
|
Digital Resilience: Is Your Firm Prepared for the Subsequent Cyber Risk? | $14.63 | Purchase on Amazon |
The ebook contains main sources for small and enormous companies to sort out cyber assaults.
#2. Cyber Resilience (River Publishers Collection in Safety and Digital Forensics)
Trendy cyber methods are advanced and depend on a variety of current and rising business 4.0 applied sciences comparable to IoT/IIoT, 5G, Blockchain, AI, AR, VR, and massive information.
| Preview | Product | Score | Value | |
|---|---|---|---|---|
|
|
Cyber Resilience (River Publishers Collection in Safety and Digital Forensics) | $28.12 | Purchase on Amazon |
The Cyber Resilience ebook talks about creating the cyber resilience administration idea of business 4.0 cyber methods, company cyber danger administration strategies, and technical implementation of the enterprise sustainability applications
#3. Cyber Resilience A Full Information – 2020 Version
The information lets you carry out a cyber resilience self-assessment to find out in case your technique aligns effectively with what you are promoting objectives. It empowers you to enhance and optimize the method of addressing issues, scale back prices, and customise the cyber resilience technique.
| Preview | Product | Score | Value | |
|---|---|---|---|---|
|
|
Cyber Resilience A Full Information – 2020 Version | $79.94 | Purchase on Amazon |
When you buy the Cyber Resilience information, you’ll get a cyber-resilience dashboard obtain that you need to use to find out what you should do to develop a dependable program.
Remaining Phrases
As organizations proceed to depend on digital methods to enhance operations and effectivity, they should shield themselves in opposition to rising cyber threats and assaults.
Deploying a powerful safety answer and practices helps to stop assaults that would in any other case result in service disruptions, monetary losses, and broken fame.
As assaults turn out to be extra advanced and a few not simple to detect, safety methods, nonetheless robust, might not cease all breaches.
As such, organizations ought to put in place measures that permit them to rapidly cease, reply and get better from the inevitable assaults, therefore proceed delivering companies with minimal or no disruption.
Subsequent, you may try EDR instruments to rapidly detect and reply to cyber-attacks.



