That is your information to pretexts, their sorts, some actual scams, and most significantly, tips on how to keep away from them.
There could be no poor on planet Earth if there had been a straightforward path to wealth.
However that’s clearly not the case. So folks usually go on an journey in luring others out of their hard-earned cash. These makes an attempt can take many attention-grabbing kinds, corresponding to romance, impersonation, cryptocurrency, and even a USB stick.
Whereas there are a number of phrases for such particular scams, there may be one well-known class that encompasses all the things: pretext.
What’s pretext?
Merely put, making pretense is making a scenario, usually with urgency, that lures you into offering essential info that you simply in any other case would not give.
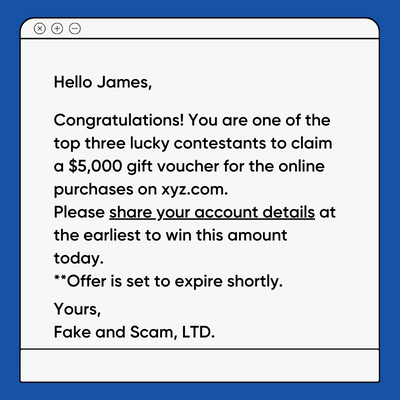
However that is extra sophisticated than only a random textual content message. Based mostly on the modus operandi, pretext has a number of methods, as mentioned under.
#1. Phishing
Phishing is the most typical methodology many people expertise once in a while. This contains receiving emails, textual content messages, and so forth., asking you to click on on a hyperlink that downloads malware or takes you to a spoofed web site.
The previous may end up in something from stolen delicate info to a locked PC that requires you to pay giant sums to regain entry.
However, a pretend web site may be the precise reproduction of the unique and steal all the knowledge you enter, beginning with the login credentials.
#2. Needs
Vishing is a subset of phishing and makes use of voice calls. So, as a substitute of emails, you might obtain cellphone calls pretending to be help employees from the providers you already use or out of your financial institution.
Right here a sufferer could also be intimidated or given a way of urgency to finish an motion in an effort to proceed utilizing the providers. As well as, one also can make the opposite supply giant quantities, which he can solely get after paying the ‘processing payment’.
#3. Scareware
Scareware happens amongst Web customers who attempt to go to questionable web sites or click on on a fraudulent e-mail or SMS hyperlink. That is adopted by a popup telling you that your system is contaminated and asking to obtain a free program for a radical cleanup.
Now who likes viruses? Nobody. Though downloading that ‘antivirus’ from that ‘pop-up’ can wreak havoc in your machine, together with putting in spy ware, ransomware and the like.
#4. To lure
Baiting makes use of curiosity and the urge to have one thing for others as the primary weapon to perform evil intent.
For instance, a USB drive mendacity on the ground of a medium-sized firm with untrained employees will entice quite a lot of consideration. Then somebody picks up the freeware from the premises and plugs it into the corporate’s system, placing that particular pc, if not your complete community, in danger.
As well as, you can even spot a particularly good supply on a web-based platform that may expire quickly. An harmless click on can endanger not solely a PC, however a complete establishment.
So these have been a few of the pretexts used for on-line assaults. Now let’s have a look at how these mechanisms are embedded in real-looking, real-life conditions used to deceive many.
Romantic Scams
That is essentially the most sophisticated rip-off and troublesome to find. In any case, who needs to lose the love of their life to a bit suspicion, proper?
Romance scams begin with a stranger on a relationship software. It may very well be a pretend relationship web site created to seize the non-public info of susceptible hopeless romantics. Nonetheless, it is also a reputable relationship web site like Loads of Fish with a fraud posing as your preferrred match.
Both manner, issues will typically transfer shortly (however not at all times), and you will nonetheless be blissful to seek out your soul mate.
Nonetheless, video encounters shall be denied to you, and face-to-face relationship will appear unimaginable as a result of ‘circumstances’. As well as, your chat companion may request that the dialog be faraway from that relationship web site.
As well as, this rip-off could lead the unhealthy actor to ask his companion to finance the journey for the face-to-face assembly. Or generally it includes a hard-to-believe funding alternative with eye-catching returns.
Whereas romance scams are available in many flavors, the same old targets are gullible ladies in search of a dependable companion. Apparently, navy personnel are additionally navy personnel who’re caught up in on-line relationships and leak labeled info.
Merely put, in case your on-line companion is all for one thing aside from you, be it cash or essential info, likelihood is it is a rip-off.
Impersonation Rip-off

Impersonation is pure social engineering at its finest. This one has fooled many, together with CEOs of respected corporations and famend universities.
How else would you outline the CEO of Bitpay who siphoned off 5,000 Bitcoins ($1.8 million on the time) with simply an e-mail?
Right here the hacker acted good and received entry to the e-mail particulars of one among Bitpay’s managers. The scammer then emailed Bitpay’s CEO about settling a fee to their company consumer, SecondMarket. The fraud was not found till one of many SecondMarket workers was notified of the transaction.
As well as, Bitpay was by no means in a position to declare insurance coverage as a result of this was not a hack, however a basic case of easy phishing.
Nonetheless, impersonation also can go the route of harassment.
In such instances, folks obtain threatening calls from “regulation enforcement officers” demanding quick settlements, or face authorized hassle.
In Boston (Massachusetts, USA) alone, impersonation induced damages as much as $3,789,407, with greater than 405 victims in 2020.
Nonetheless, imitation may also be bodily. For instance, you might obtain an sudden go to from ‘technician(s)’ out of your web supplier to ‘repair sure issues’ or for a ‘routine verify’. You are too shy or too busy to ask for the small print, and also you allow them to in. They compromise your programs or, even worse, they try an outright heist.
One other frequent impersonation assault is CEO e-mail fraud. It comes as an e-mail out of your CEO asking you to carry out a ‘activity’, which generally includes a transaction with a ‘provider’.
The important thing to avoiding falling sufferer to such assaults is to loosen up and never act rashly. Simply attempt to manually confirm the small print of the decision, e-mail, or go to, and you will most likely avoid wasting cash.
Cryptocurrency Scams

It isn’t a wholly new class, however only a pretext involving cryptocurrencies.
However as a result of crypto training remains to be scarce, folks are likely to fall for it time and again. The most typical state of affairs in such scams is an outrageous funding alternative.
Crypto scams can lure a number of victims and it may take a while to ship the ultimate blow. These plots may be staged by legal organizations making an attempt to lure traders into pumping their hard-earned cash into ponzi schemes.
And at last, the unhealthy guys gobble up the folks’s possessions when the “coin” reaches a major worth, orchestrating what is called the carpet-pulling. What follows are the traders sobbing over thousands and thousands of ineffective crypto with negligible market worth.
As well as, one other sort of cryptocurrency rip-off can trick non-tech savvy folks into revealing their non-public keys. As soon as achieved, the scammer transfers the cash to a different pockets. Because of the anonymity of cryptocurrencies, tracing the stolen cash is commonly troublesome and restoration turns into a pipe dream.
The savior right here is analysis.
Attempt to confirm the legitimacy of the staff behind such developments. As a rule of thumb, don’t spend money on new cash till they’ve established a sure popularity and worth available in the market. Even in any case, crypto is unstable and vulnerable to scams. So do not make investments if you cannot afford to lose all of it.
to know extra! Try this crypto rip-off information from Bybit.
The best way to battle pretenses

Detecting pretexts will not be simple, and the coaching it is advisable defend towards them can’t be a one-off. The folks answerable for these scams are continually evolving of their fraud mechanisms.
Nonetheless, the gist of such strategies stays the identical and you’ll observe the next tricks to get a head begin.
#1. Be taught to say NO!
Most individuals endure from this urge to cooperate with unusual emails and cellphone calls, even when deep down they know one thing is up.
Respect your instincts. You may verify together with your colleagues earlier than doing something delicate, corresponding to sharing checking account info, transferring cash, and even clicking a suspicious hyperlink.
#2. Practice your employees
It’s human nature to overlook. A single warning on the time of accession will subsequently not do a lot good.
As an alternative, you’ll be able to run month-to-month rip-off drills to make sure your staff stays on high of such techniques. Even a weekly e-mail with info on the newest pretext assaults will do the trigger a terrific service.
#3. Spend money on an excellent antivirus program
Normally, pretexts contain utilizing unreliable hyperlinks. Due to this fact, it turns into a lot simpler you probably have a premium antivirus to take care of such assaults.
They’ve central databases that share info and superior algorithms that do the arduous be just right for you.
Moreover, open the hyperlink in a search engine if it does not appear clickable.
#4. Textbooks and programs
Whereas the web is filled with useful (and unhealthy) recommendation for avoiding pretexts, some want the traditional manner of studying. On this case, there are a couple of helpful books:
| Instance | Product | Judgement | Value | |
|---|---|---|---|---|
|
|
The Social Engineer’s Playbook: A Sensible Information to Pretexts |
$17.09 |
Purchase on Amazon |
|
|
|
A pleasant introduction to assault and prevention via social engineering |
$5.08 |
Purchase on Amazon |
Such assets are particularly helpful for in-depth, self-paced coaching that won’t improve your display time.
An alternative choice that’s notably appropriate on your workers is Udemy’s social engineering course. The principle benefit of this course is its lifetime entry and availability on cellular and TV.
This course covers digital and bodily pretexts, together with psychological manipulation, assault methods, non-verbal communication, and extra, which shall be useful to newcomers.
Use the information protect!
As talked about earlier, these rip-off artists are discovering new methods to idiot the typical web consumer. Nonetheless, they will additionally goal the neatest folks.
The one manner ahead is to teach and share such incidents with colleagues on social media platforms.
And you’ll be stunned to know that dishonest is now frequent within the metaverse as properly. Learn the way to stop fraud in Metaverse and take a look at this information to becoming a member of and accessing Metaverse in case you’re new to those unusual computing worlds.


