“Those that can provide up important liberty to achieve slightly short-term safety deserve neither liberty nor safety.” -Benjamin Franklin
Social Engineering has been on the forefront of safety considerations for a while now. It has been extensively mentioned by trade specialists. But not many individuals absolutely notice the potential hazard it poses and the way harmful it may be.
For hackers, Social Engineering might be the best and most effective solution to crack safety protocols. The rise of the web gave us very highly effective capabilities by connecting gadgets with out the barrier of distance. This gave us developments in communication and interconnections, however created loopholes that led to a breach of private info and privateness.
Because the earliest, pre-technological instances, people have encoded and secured info. A popularly recognized technique from historical instances is the Caeser Cipher by which messages are encoded by shifting the locations within the checklist of alphabets. for instance, “hi there world” if shifted by 1 place may very well be written as “ifmmp xpsmf”, the decoder studying the message “ifmmp xpsmf” must transfer the letters again one place within the checklist of alphabets to know the message.
So simple as this encryption method was, it lasted for practically 2,000 years!

As we speak we have now developed extra superior and sturdy safety programs, however safety is a problem.
You will need to word that hackers use quite a lot of methods to acquire important info. Let’s take a fast have a look at a few of these methods to know why social engineering is so vital.
Brute Drive & Dictionary Assaults

A brute power hack includes a hacker with a sophisticated set of instruments constructed to penetrate a safety system utilizing a calculated password by acquiring all potential character combos. In a dictionary assault, the attacker executes an inventory of phrases (from the dictionary) in hopes of discovering a match with the consumer’s password.
A brute power assault, whereas very highly effective, appears much less probably as of late as a result of nature of present safety algorithms. To place issues in perspective, if my account password is ‘qwertyuiop1202@990!!!’ is , the entire sum of characters is 22; subsequently a pc wants 22 factorials to calculate all potential combos. That is rather a lot.
Greater than that, there are hashing algorithms that take that password and convert it right into a hash to make it even more durable for a brute power system to guess. For instance, the beforehand written password will be hashed d734516b1518646398c1e2eefa2dfe99. This provides an much more severe layer of safety to the password. We’ll have a look at safety methods in additional element later.
In case you are a WordPress website proprietor in search of brute power safety, try this information.
DDoS assaults
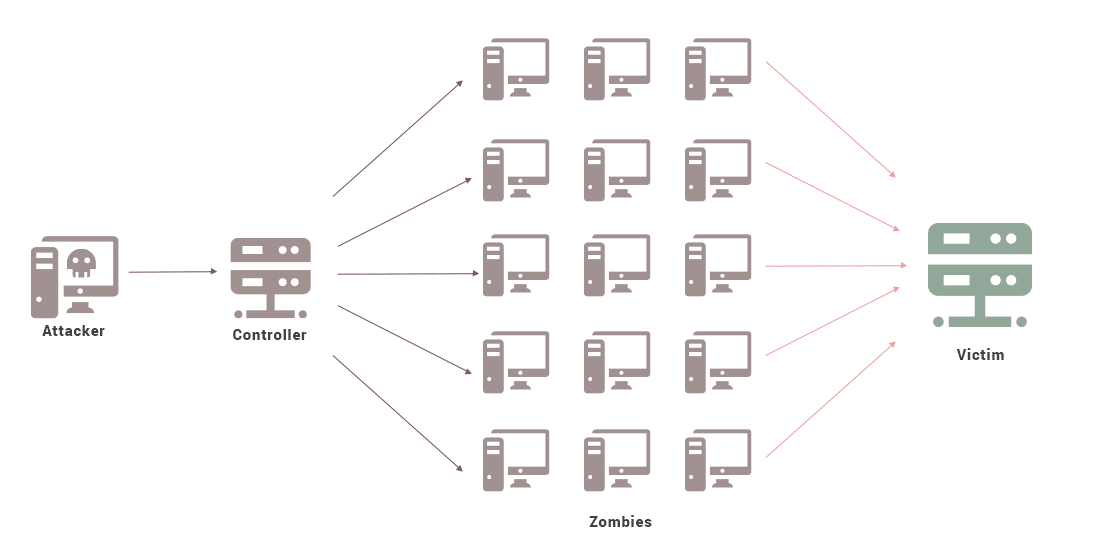
Distributed Denial of Service assaults happen when a consumer is blocked from accessing respectable web assets. This may be on the consumer aspect or on the service the consumer is making an attempt to entry.
A DDoS normally leads to a lack of income or consumer base. To allow an assault like this, a hacker can take management of a number of computer systems all around the web that can be utilized as a part of a “botnet” to destabilize the community or in some circumstances flood community site visitors with unusable packets of knowledge leading to overuse and thus downtime of community assets and nodes.
Phishing

This can be a type of hacking the place the attacker makes an attempt to steal consumer credentials by creating faux login web page substitutes. Sometimes, the attacker sends a malicious electronic mail to a consumer appearing as a trusted supply, reminiscent of a financial institution or a social media web site, normally with a hyperlink for the consumer to enter their credentials. The hyperlinks are normally made to appear to be respectable web sites, however a better look proves them fallacious.
For instance, a phishing hyperlink as soon as used paypai.com to rip-off Paypal customers into giving up their credentials.
A typical phishing electronic mail format.
“Pricey consumer,
We have observed suspicious exercise in your account. Click on right here to vary your password now to forestall your account from being locked.”
There’s a 50% probability that you just had been phished in a single go. No? Have you ever ever logged into a web site and after clicking login/login it nonetheless takes you again to the login web page, sure? You will have been efficiently phished.
How is social engineering achieved?
Whilst encryption algorithms grow to be even more durable to crack and safer, social engineering hacks are nonetheless as highly effective as ever.
A social engineer usually collects details about you to entry your on-line accounts and different protected assets. Sometimes, an attacker will get the sufferer to voluntarily reveal private info via psychological manipulation. A scary a part of that is that this info does not essentially have to come back from you, simply somebody who is aware of.
Often the goal shouldn’t be the one being socially engineered.
For instance, a preferred telecom firm in Canada was within the information early this 12 months for a social engineering hack on its buyer, with customer support personnel socially engineering the main points of the goal in an enormous SIM swap hack that led to a lack of $30,000 in cash.
Social engineers play on folks’s insecurities, negligence and ignorance to get them to reveal important info. At a time when distant help is extensively used, organizations have confronted many extra situations of hacks like this as a result of inevitability of human error.
Anybody generally is a sufferer of social engineering, what’s even scarier is that you may be hacked with out even figuring out it!
How do you shield your self towards social engineering?

- Keep away from utilizing private info reminiscent of date of beginning, pet title, baby title, and so on. as login passwords
- Do not use a weak password. If you cannot keep in mind the advanced one, use a password supervisor.
- Search for the apparent lies. A social engineer does not really know sufficient to hack you straight away; they provide the fallacious info hoping you’d give the best one, after which they ask for extra. Do not fall for it!
- Confirm the authenticity of the sender and area earlier than taking motion from electronic mail messages.
- Contact your financial institution instantly in case you discover any suspicious exercise in your account.
- Once you all of a sudden lose sign reception in your mobile phone, report back to your community supplier instantly. It may very well be a sim swap hack.
- Allow 2-factor authentication (2-FA) on companies that help it.
Conclusion
These steps usually are not a direct treatment for social engineering hacks, however they may assist make it troublesome for a hacker to get to you.

