How are you securing your API?
It’s the age of the digital economic system explosion, and large information hundreds are being piped by means of APIs. Enterprise, gaming, training, climate, science, arts . . . you identify it; every thing works on APIs. For a world so essentially reliant on APIs, there’s surprisingly little deal with safety.
For builders, the defaults of their frameworks are sufficient; and even worse, when no frameworks are getting used, they assume they’re following safety practices. For system admins, the default safety provided by their infrastructure or service supplier is what they depend on.
Not a reasonably sight in any respect, should you ask me.
Evidently, there’s lots at stake, which we understand solely when one thing actually horrible occurs.
However first issues first. 🙂
Why safe API endpoints?
This must be a no brainer, proper?
We have to safe endpoints as a result of, properly, that’s what the enterprise relies on.
Whereas that’s a powerful sufficient argument in itself, I need to broaden the point of view a bit of and spotlight different associated, however equally lethal, penalties.

Enterprise loss 📉
That is the plain one. If somebody succeeds in messing along with your API endpoints, it can convey every thing to a screeching halt. Safety breaches also can take a whole lot of time to get well from, which interprets to suicide in enterprise phrases. Whereas it’s true that the majority companies in all probability received’t be affected by an hour or two of downtime, for some, it’s not permissible.
Think about a foreign money alternate being down for a couple of minutes!
Compliance points
Not securing your APIs correctly can land you in deep trouble, relying on which geographies or industries you’re coping with. For example, should you’re serving the banking business (within the EU, particularly), the price of being found serving with insecure APIs will end in large authorized and compliance troubles. A lot in order that it would even spell the top of your small business.
Fame loss
Being hacked is painful sufficient in itself, but when information will get out in public, there’s going to be an irrecoverable loss to your model picture. For example, Sony has been hacked a number of occasions very badly by now, and in safety circles, the corporate is a laughing inventory of kinds.
Even when no precise lack of information or cash is incurred, good luck attempting to persuade your scuttling prospects. 🙂
Inflated infrastructure payments 💰
When your API runs on infrastructure, it consumes sources (bandwidth, CPU, and reminiscence, principally). For example, the place the API just isn’t secured correctly, and malicious outsiders are in a position to work together with it, it’s attainable for them to drive the API to maintain doing a whole lot of pointless work (operating heavy database queries, for instance), which may shoot up your payments for on causes.
On platforms the place computerized scaling of sources is enabled (like AWS), the outcomes will be surprising (off-topic, however should you ever get caught in a soup like this on AWS, they’re fairly understanding of the state of affairs and promptly waive off the inflated invoice — as of writing, no less than!).
Crew morale
So, you is likely to be considering, that the group that allow these compromises occur will lose morale over them. Nicely, not fairly. It’s attainable that the compromises had been attributable to weak infrastructure safety, which is able to dishearten the builders or vice versa.
Ought to this occur sufficient time, you’ll have a tradition in your fingers that you simply’ll remorse letting develop.
Competitor’s positive aspects
So let’s say there was a breach, however there was no precise loss. Nonetheless, your opponents will use the incident to drum up their very own API and assert how rather more safe theirs is (even when it’s not!). As soon as once more, good luck attempting to persuade the market. 🙂
All in all, there are penalties to safety breaches that transcend dropping cash.
Finest Practices for Securing API endpoints
Fortunately, there are specific easy-to-implement and well-understood practices which you can apply to your API endpoints for securing them. Right here’s what most safety consultants suggest.
HTTPS all the time 🔒
In case your API endpoints permit API shoppers to speak over http or different non-secure protocols, you’re placing them at an enormous threat. Passwords, secret keys, and bank card info can simply get stolen as any man-in-the-middle assault, or packet sniffer instrument can learn them as plain textual content.
So, all the time make https the solely possibility out there. Irrespective of how trivial an endpoint may appear, connecting over http shouldn’t even be an possibility. TLS certificates doesn’t price a lot; you should purchase for as little as $20 from the SSL retailer.

One-way password hashing
Passwords ought to by no means be saved as plain textual content, as within the occasion {that a} safety breach happens, all of the person accounts will probably be compromised. On the similar time, symmetric encryption ought to be strictly averted, as any attacker ingenious and protracted sufficient will be capable to break them.
The one recommended possibility is uneven (or “one-way”) encryption algorithms for storing passwords. That approach, neither an attacker nor any developer or sysadmin inside the firm will get to learn buyer passwords.
Sturdy authentication 💪
Now, virtually each API has a type of authentication, however for my part, the OAuth2 system works the very best. Versus different authentication strategies, it divides your account into sources and permits solely restricted entry to the auth token bearer.
On the similar time, one other excellent apply to set tokens to run out each, say, 24 hours, in order that they must be refreshed. This manner, even when your token will get leaked, there’s an opportunity that the 24-hour deadline will cut back the impression of the breach.
Apply fee limiting
Except you could have an API that’s utilized by tens of millions of individuals each minute, it’s an excellent concept to implement a restrict of what number of calls a shopper could make to the API in a given time window.
That is principally to discourage bots, which may preserve sending tons of of simultaneous requests each second and make your API eat up system sources for no good motive. All net improvement frameworks include a rate-limiting middleware (and if not, it’s pretty straightforward so as to add it by way of a library) that takes only a minute or so to arrange.
Validate enter
This feels like a no brainer, however you’ll be shocked what number of APIs fall for this. Validating enter not simply means checking that the incoming information is in an accurate format, but in addition that no surprises are attainable. A easy instance is SQL injection, which may wipe out your databases should you let the question strings go by with little or no checking.
One other instance is to validate the POST request dimension and return a correct error code and message to the shopper. Making an attempt to just accept and parse ridiculously massive inputs will solely serve to explode the API.
Implement IP tackle filtering, if relevant
Should you’re into B2B providers and your APIs are utilized by companies from set places, think about including an additional layer of safety that restricts IP addresses that may entry your API. For each new location and new shopper, the IP tackle will must be checked towards the incoming request.
Sure, it provides nuisance to onboarding, however the finish result’s a lot tighter safety than will be in any other case achieved.
Instruments for Growing API Safety
Are there instruments that may assist us scan vulnerability, and even higher, provide the primary line of protection in the case of securing APIs?
Luckily, sure. There are a number of instruments you need to use however be cautioned that on the finish of the day, no safety technique is ideal. Having stated that, these instruments can enhance your API safety manyfold, so they’re really helpful.

AppTrana
AppTrana’s devoted API Safety options provide a complete risk-based answer to guard towards a variety of API threats, together with OWASP API prime 10, API-based DDoS and bot assaults, embedded threats, information leakage, and so forth. With limitless automated API scanning backed with guide pen-testing, it constantly screens your threat rating to strengthen the safety posture.
AppTrana’s API safety ensures essentially the most complete answer with the mixture of Threat detection, API Risk detection, API Constructive Safety insurance policies, API-Particular DDoS insurance policies, API-Particular Bot modules, and API Discovery options.
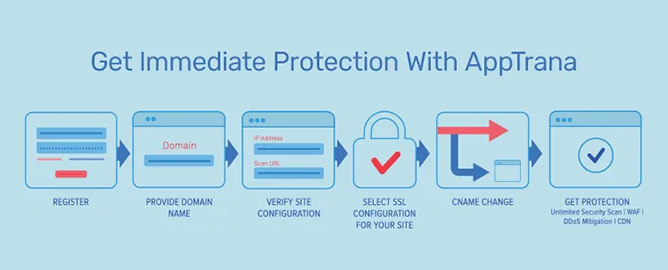
Its API discovery ensures full visibility into API calls, together with undocumented and shadow APIs, to grasp your API assault floor. This devoted API safety collects details about person particulars, API utilization habits, menace exercise, API name maps, and extra to showcase the safety standing with real-time analytics.
Utilizing Indusface AppTrana, you possibly can generate tailor-made API-specific insurance policies to dam API-focused abuse in actual time.
Cloudflare
Cloudflare’s superior net utility firewall (WAF) is essential for making certain safe and environment friendly functions and APIs. It defends towards DDoS assaults, blocks unauthorized bot entry, detects malicious information, and scans for browser provide chain assaults.
Cloudflare’s intensive worldwide community facilitates the transmission of huge quantities of site visitors by means of its API gateway. To make sure the safety of its APIs, Cloudflare employs a complete framework encompassing API discovery, built-in API administration and analytics, and layered API defenses.
API Gateway gives safe and environment friendly API administration, together with discovery, Layer 7 safety, Mutual TLS, optimistic API safety, abuse detection, and delicate information detection. It facilitates endpoint identification and monitoring, protects towards assaults, implements authentication, verifies OpenAPI schemas, and prevents information leaks.
Cloudflare API Gateway protects towards OWASP API dangers.
Invicti
Invicti comes with a USP of “proof-based scanning”. In easier phrases, it’s typically attainable that irregular community circumstances or some lesser-known API behaviors are construed as safety loopholes, that are later discovered to be improper.
This wastes sources, as all of the vulnerabilities reported, must be scanned once more manually to verify that they aren’t false positives. Invicti says the instrument is ready to offer you a powerful sufficient proof of idea for the stories, eradicating doubts concerning the weak hyperlinks discovered.
With firms like Sony, Religare, Coca-Cola, Huawei, and so forth., on their shopper listing, you possibly can ensure that these of us are doing one thing proper. 🙂
Okta
Strive Okta to allow your builders to focus on enhancing the person expertise in addition to safe your enterprise information effectively. It provides OAuth 2.0 authorization and is designed for each cellular and net functions. It’s also suitable with third-party API administration providers.
Use Okta to create, audit, and keep all of the insurance policies for API entry by means of user-friendly and purpose-built consoles while not having customized codes. It provides you further flexibility so that you simply don’t must safe your APIs utilizing further gateway situations.
Okta encompasses identity-driven coverage to regulate several types of customers and providers below one roof. Outline entry relying upon person profiles, networks, teams, consent, and purchasers. Prolong tokens utilizing dynamic information out of your inside methods to take pleasure in sooner integration and seamless migration.
It facilitates a centralized administration for APIs and allows you to defend API sources. Okta focuses on safety by permitting you to safeguard entry between completely different micro-services.
42crunch
42Crunch is an API safety platform for builders to seamlessly combine safety measures into the API improvement pipeline, making certain proactive testing, fixing, and safety from improvement to runtime.
The platform is trusted by prime manufacturers like Verizon, Ford, Bridgestone, Allianz, and so forth.
The corporate claims to be the one platform that ensures safety governance and compliance from design to runtime.
It does this by means of API Audit, which performs 300 safety checks; API Scan, which detects vulnerabilities in testing and runtime; and API Shield, which enforces runtime API safety insurance policies with a small, containerized micro-API firewall.
42Crunch’s API Safety Testing instruments assist uncover API safety weaknesses, whereas API Safety ensures runtime safety with content material validation, menace detection, site visitors management, and an API micro-firewall. Greater than 800k builders undertake 42crunch API instruments.
Probely
Probely is a vulnerability scanner utilized by SaaS companies, builders, safety groups, DevOps, and compliance professionals. It scans net apps and APIs, finds vulnerabilities, and provides detailed stories on find out how to resolve them.
Some prime firms like Olx, Development Micro, and Leisure Companions belief this platform, which helps varied net functions and APIs, together with microservices and standalone APIs following an OpenAPI (Swagger) Specification or Postman Assortment.
Probely gives a documented API and adapts vulnerability severity in line with context. It integrates with CI/CD pipelines, automates safety testing for net apps and APIs, and syncs with issue-tracking platforms.
It ensures compliance with requirements like PCI-DSS, OWASP TOP 10, ISO27001, HIPAA, and GDPR. Strive it free for 14 days.
APIsec
APIsec gives an automatic platform for proactive and steady API safety testing. It builds shopper belief by completely testing updates and releases to make sure a safe manufacturing atmosphere.
The platform automates complete safety testing for APIs all through the software program improvement lifecycle (SDLC). It permits API discovery, evaluation, and execution of personalized assault situations earlier than manufacturing.
APIsec helps to eliminate repetitive guide third-party testing by automating the API safety testing.
APIsec seamlessly integrates with CI/CD, ticketing, and communication platforms, making certain a clean workflow. Aligning API penetration exams with threat evaluation permits the detection of safety points early on, decreasing technical debt in utility improvement.
The platform provides an unauthenticated API scanner, freed from cost, to determine misconfigurations and different primary safety flaws. It additionally provides free programs like API safety fundamentals and professional API pen testing; if , you possibly can go to APIsec College.
Cequence
Cequence is a multi-award-winning platform for API discovery, stock, compliance, and dynamic testing. The platform aids within the identification and prevention of fraud, assaults, exploits, and information leaks in real-time.
It provides a complete answer for figuring out API assault surfaces in an effort to guarantee menace safety in addition to compliance and laws. The platform will be simply built-in along with your current API and safety infrastructure.
Cequence claims to have saved tens of millions of {dollars} and billions of customers whereas additionally making certain the safety of transactions. Some prime firms that use this platform embrace RBS, American Specific, Ulta Magnificence, PoshMark, T-mobile, Telstra, and so forth.
API Discovery and Threat Evaluation, Remediation of Delicate Information Publicity, Account Takeover Prevention, and API Threat Evaluation are a few of its key options. The platform provides free API safety evaluation.
Conclusion
There’s no scarcity of API safety instruments out there available in the market, whether or not it’s open supply, free or industrial, or any mixture of those.
Strive a number of of them from the listing and see what works greatest in your requirement.

