The normal perimeters of networks have disappeared. Entry to a corporation’s purposes and digital property happens from far locations, and controlling these accesses turns into a critical problem. The times when community borders may very well be protected are lengthy gone. Now could be the time for brand new zero-trust safety methods.
When an organization’s digital property must traverse lengthy distances on the unsafe paths of the Web, the stakes are so excessive that you may belief nothing and nobody. That’s why it is best to undertake the zero-trust community mannequin to limit all customers’ entry to all community assets always.
In zero-trust networks, any try and entry a useful resource is restricted from a consumer or a tool, no matter whether or not they have beforehand accessed the identical useful resource. Any consumer or machine should all the time undergo an authentication and verification course of to entry assets, even when they’re bodily throughout the group. These authentications and verifications have to be quick to keep away from that the safety insurance policies degrade the efficiency of the purposes and customers’ expertise.
Zero-trust vs. VPN

The zero-trust community mannequin is changing the VPN mannequin historically utilized by corporations for his or her staff to entry their digital property remotely. VPNs are being changed as a result of they’ve a significant flaw that zero-trust networks can resolve. In VPNs, any breach that happens within the encrypted channel that connects a consumer to the group’s community grants potential attackers limitless entry to all firm assets linked to the community.
On outdated, on-premises infrastructures, VPNs labored properly, however they generate extra dangers than options on cloud or blended infrastructures.
Zero-trust networks repair this shortcoming of VPNs however add a possible draw back: they will result in extra complexity by way of implementation and upkeep, as authorizations have to be stored up-to-date for all customers, gadgets, and assets. This requires further work, however IT departments obtain better management over assets and a discount in vulnerabilities in return.
Luckily, the advantages of a zero-trust community could be realized with out the necessity for added upkeep and deployment efforts, because of instruments that automate and help in community administration duties. The instruments mentioned under make it easier to apply zero-trust insurance policies with minimal effort and prices.
NordLayer
NordLayer affords an adaptive community entry safety resolution primarily based on the Safety Service Edge framework. Delivered as Software program as a Service (SaaS) community safety resolution, it embodies the important thing Zero Belief rules and offers safe distant entry, minimizing the group’s dangers.
Implicit belief is faraway from all infrastructure, utilizing Safe Net Gateways as portals into the interior firm community. The hyperlink from the consumer’s endpoint to the SWG is encrypted with AES 256-bit cipher, whereas the gateway itself enforces arrange safety insurance policies stopping varied threats. No unsupervised connection will sneak previous NordLayer’s protection mechanisms.
The visitors between the SWG and consumer’s machine can also be facilitated by cutting-edge tunneling protocols like NordLynx (a proprietary-made model of WireGuard developed by Nord Safety). In the meantime, different choices like IKEv2 and OpenVPN (UDP and TCP) variations improve cross-device compatibility. That method, it’s doable to arrange NordLayer on routers and different {hardware} gadgets.
A consumer’s identification could be checked a number of occasions earlier than accessing delicate information or work assets. NordLayer additionally helps Single Signal-On (SSO) with Azure AD, OneLogin, Okta & G Suite, facilitating the transition between your at present used instruments and the Zero Belief community. Leveraging cloud entry safety dealer capabilities, NordLayer enhances community visibility and retains better entry management into vital group assets.
The answer doesn’t require companies to discard the at present used instruments, both — NordLayer could be mixed with current infrastructure. The product doesn’t restrict consumer rely, making it extremely scalable with out drastically growing the subscription value. This makes consumer segmentation simpler and simpler by offering a transparent overview of the community individuals. On prime of that, licenses could be simply transferred between customers, adapting to fast-paced work surroundings dynamics.
Perimeter 81
Perimeter 81 affords two approaches to managing and protecting a corporation’s purposes and networks safe, each on cloud and on-premises environments. The 2 proposals begin from providing zero-trust networks as a service. To do that, Perimeter 81 makes use of a software-defined perimeter structure, which offers nice flexibility to onboard new customers and affords better visibility into the community. As well as, the service is appropriate with the primary cloud infrastructure suppliers.
Zero Belief Software Entry is predicated on the belief that each firm has vital purposes and companies that almost all customers don’t want entry to. The service permits elevating boundaries to particular customers primarily based on their roles, gadgets, areas, and different identifiers.
In the meantime, Zero Belief Community Entry defines a segmentation of the group’s community by belief zones, which permits the creation of belief limits that management the move of knowledge with a excessive granularity degree. Trusted zones are made up of units of infrastructure components with assets that function on the similar degree of belief and supply comparable performance. This reduces the variety of communication channels and minimizes the opportunity of threats.
Perimeter 81’s Zero Belief Community Entry (ZTNA) service affords a whole and centralized view of the group’s community, guaranteeing the least privileged entry doable for every useful resource. Its security measures reply to Gartner’s SASE mannequin, as safety and community administration are unified on a single platform.
The 2 Permiter 81 companies are included in a pricing scheme with a variety of choices. These choices vary from a fundamental plan with the necessities to safe and handle a community to an enterprise plan that may scale unlimitedly and offers devoted 24/7 assist.
These days, Perimeter 81 was named ZTNA chief.
ZScaler Personal Entry
ZScaler Personal Entry (ZPA) is a cloud-based, zero-trust community service that controls entry to a corporation’s non-public purposes, no matter whether or not they’re situated in a proprietary information middle or a public cloud. With ZPA, purposes are fully invisible to unauthorized customers.
In ZPA, the connection between purposes and customers is carried out following an inside-out technique. Moderately than extending the community to incorporate customers (correctly achieved if utilizing a VPN), customers are by no means contained in the community. This strategy considerably minimizes the dangers by avoiding the proliferation of malware and the dangers of lateral motion. As well as, ZPA’s scope is just not restricted to net purposes however any non-public software.
ZPA makes use of a micro tunnel know-how that enables community directors to section the community by software, avoiding the necessity to create synthetic segmentation within the community or apply management by firewall insurance policies or managing entry management lists (ACLs). The micro tunnels make use of TLS encryption and customized non-public keys that strengthen safety when accessing company purposes.
Due to its API and ML (machine studying) enhancements, ZPA lets IT departments automate zero-trust mechanisms by discovering apps and creating entry insurance policies for them and by producing segmentation robotically for every completely different app workload.
Cloudflare Entry
Cloudflare’s zero-trust community service is supported by a proprietary community with entry factors distributed all through the world. This permits IT departments to supply high-speed, safe entry to all of a corporation’s assets — gadgets, networks, and purposes.
Cloudflare’s service replaces conventional, network-centric safety perimeters, utilizing as an alternative safe, close-range accesses that guarantee optimum velocity for distributed workgroups.
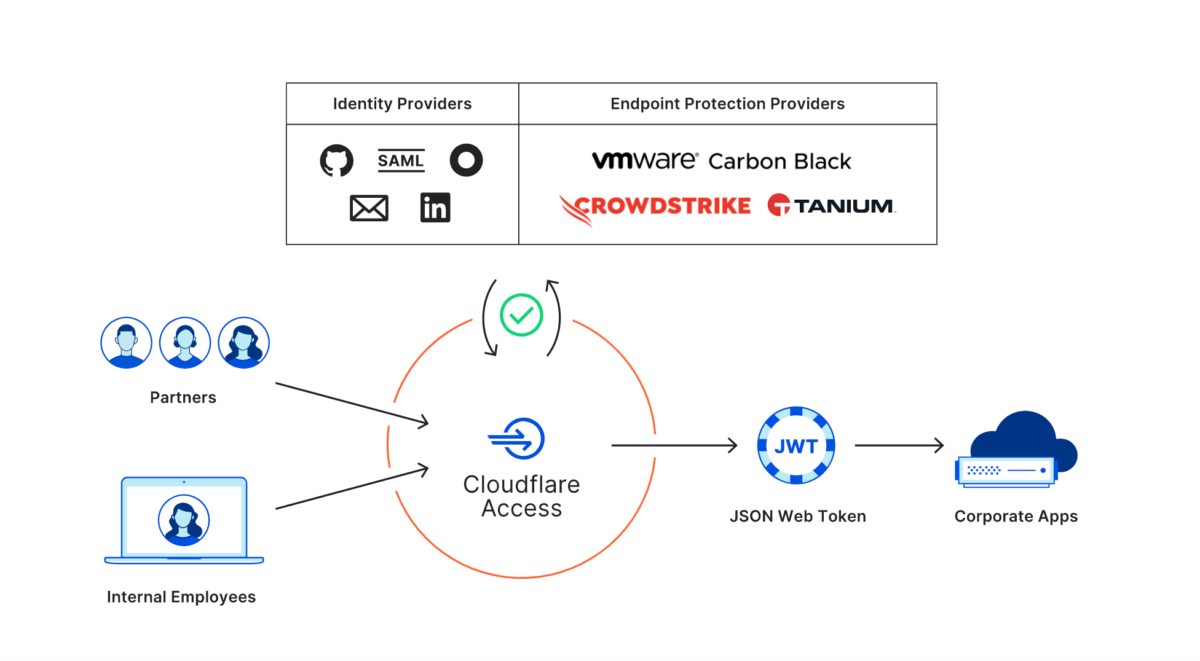
Cloudflare’s zero-trust entry operates total purposes in a corporation, authenticating customers via its personal world community. This enables IT managers to report every occasion and every try and entry a useful resource. As well as, it makes it straightforward to keep up customers and so as to add extra customers.
With Cloudflare Entry, the group can keep its identification, safety suppliers, machine posture, location necessities per software, and even its current cloud infrastructure. For identification management, Cloudflare integrates with Azure AD, Okta, Ping, and machine posture, with Tanium, Crowdstrike, and Carbon Black.
Cloudflare affords a free model of its service that gives the primary instruments and lets you shield as much as 50 customers and purposes. You should select the paid variations of the service to scale to many customers or purposes, which add different advantages akin to 24x7x365 phone and chat assist.
Wandera
Wandera Personal Entry zero-trust networking resolution affords quick, easy, and safe distant entry to a corporation’s purposes, whether or not they function in SaaS or are deployed internally. The service stands out for its simplicity, with set up procedures that may be accomplished in minutes and don’t require specialised {hardware}, certificates, or sizing.
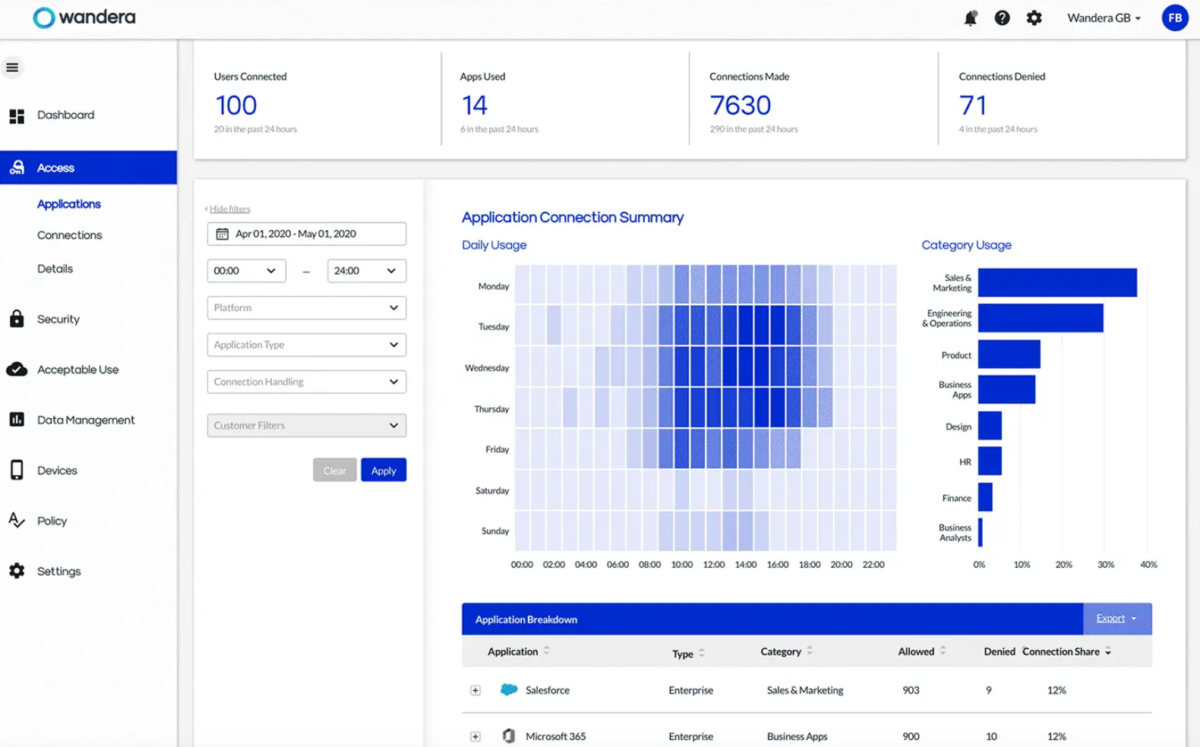
Wandera Personal Entry affords flexibility for distributed work groups, working on heterogeneous platforms, with managed or owned gadgets (BYOD). The answer offers real-time visibility into software entry, figuring out shadow IT, and robotically proscribing entry from contaminated or insecure gadgets, because of risk-aware entry insurance policies.
With Wandera Personal Entry, identity-centric safety fashions could be applied, guaranteeing that solely licensed customers can connect with the group’s purposes. The usage of application-based micro tunnels connects customers solely to the purposes they’re licensed to entry. The appliance of safety insurance policies stays constant throughout all infrastructures, be it cloud, data-center, or SaaS purposes.
Wandera’s safety system is powered by an clever menace detection engine known as MI:RIAM. This engine is fed day by day with the knowledge supplied by 425 million cell sensors, which ensures safety in opposition to the widest vary of recognized and zero-day threats.
Okta
Okta affords a zero-trust safety mannequin that encompasses a variety of companies, together with software, server, and API safety; unified and safe consumer entry to on-prem and cloud purposes; adaptive, context-based, multi-factor authentication, and automated off-boarding to mitigate orphan account dangers.
Okta’s common listing service offers a single, consolidated view of each consumer in a corporation. Due to the mixing of consumer teams with AD and LDAP, and connections with HR techniques, SaaS purposes, and third-party identification suppliers, Okta Common Listing integrates all types of customers, whether or not they’re firm staff, companions, contractors, or clients.
Okta stands out for its API safety service since APIs are considered a brand new type of shadow IT. Okta’s API entry administration reduces hours of designing and making use of XML-based insurance policies to a matter of minutes, facilitating onboarding of latest APIs and integration with companions for the usage of APIs. Okta’s coverage engine permits implementing finest practices in API safety, simply integrating with identification frameworks akin to OAuth. API authorization insurance policies are created primarily based on purposes, consumer context, and group membership to make sure that solely the fitting customers can entry every API.
Okta’s integration community avoids vendor lock-in, giving organizations the liberty to select from greater than 7,000 pre-built integrations with cloud and on-prem techniques.
CrowdStrike Falcon
The CrowdStrike Falcon Id Safety zero-trust safety resolution shortly stops safety breaches as a result of compromised identities, defending identities for all customers, areas, and purposes in a corporation utilizing zero-trust insurance policies.
Falcon Id Safety goals to cut back prices and dangers and improve the ROI of instruments in use by lowering engineering useful resource necessities and eliminating redundant safety processes.
The unified management of all identities makes it straightforward to implement Conditional Entry and Adaptive Authentication methods, in addition to guaranteeing a greater consumer expertise and better protection of multi-factor authentication (MFA), even for legacy techniques.
The CrowdStrike distant entry resolution affords full visibility into the authentication exercise of all accounts and endpoints, offering location information, supply/vacation spot, kind of login (human or service account), amongst others. In flip, it protects the community from insider threats, akin to deprecated privileged accounts, misassigned service accounts, irregular habits, and credentials compromised by side-movement assaults.
By integrating with current safety options, the deployment of Falcon Id Safety is carried out in minimal time and with out friction. Along with providing direct integration with safety options for vital property, akin to CyberArk and Axonius, CrowdStrike affords high-performance APIs that enable corporations to combine with nearly any system.
Conclusion
The brand new regular appears to remain, and IT directors have to get used to it. Distant work will proceed to be a day by day actuality, and group networks won’t ever once more have clearly outlined boundaries.
On this context, IT directors should undertake zero-trust community and software options as quickly as doable if they don’t need to put their organizations’ most valuable digital property in danger.

