Utilizing the correct software-defined perimeter (SDP) resolution may help you safe your organizational property and infrastructure from attackers and unauthorized customers.
Evidently, the distributed workforce is prevailing throughout the globe, particularly after the present pandemic. Customers could hook up with your organizational community from anyplace, utilizing any machine and connectivity, which will be insecure.
This is the reason it’s important to have a stronger safety strategy like software-defined perimeter options as a substitute of counting on a network-based strategy.
Though conventional community structure supplies safety by separating your community from the surface world utilizing applied sciences like firewalls, routers, and many others., for entry controls, these strategies are based mostly on accessibility and visibility.
With blurred community perimeters within the present situation with the arrival of cloud applied sciences, there are a number of entry factors to infiltrate conventional entry controls. Your exterior workforce and gadgets could carry a number of dangers, sufficient to trigger safety breakdowns and render your conventional strategies insufficient.
SDP options may help you encounter such dangers by offering highly effective, risk-free entry controls.
On this article, we are going to uncover just a few issues about SDPs, how they’re useful, and a few of the greatest SDP options you possibly can introduce in your organizational safety toolkit.
Let’s start!
What Are Software program-Outlined Perimeter Options (SDP)?
Software program-defined perimeter (SDP) is a safety strategy to safe infrastructures, reminiscent of routers, servers, functions, and programs linked to the web. It hides the programs hosted on the cloud and on-premises from attackers and third events. And the options with SDP capabilities are often called software-defined perimeter options or SDP options.
This safety strategy goals to determine a community perimeter with the assistance of software program moderately than {hardware}. Companies utilizing an SDP resolution primarily makes their infrastructure and programs invisible to maintain them protected from unauthorized customers and attackers.
SDP was developed in 2007 by the Protection Data System Company (DISA). Additional, the Cloud Safety Alliance (CSA) took an interest within the SDP idea and developed its framework. Curiously, Google was among the many first organizations to undertake the concept and create an SDP resolution – GoogleBeyond Corp.
How Do SDP Options Work?
As a substitute of relying on conventional strategies based mostly on community safety, SDP options assist safe all of the functions, customers, and their connectivity. A software-defined perimeter resolution creates a digital perimeter or boundary surrounding a enterprise’s property and infrastructure at its community layer.
This perimeter separates the property from exterior access-based controls proscribing person privileges but permitting community entry. An SDP resolution can authenticate each person identification and gadgets. It allows you to entry the property solely after evaluating the machine state and validating person identification.
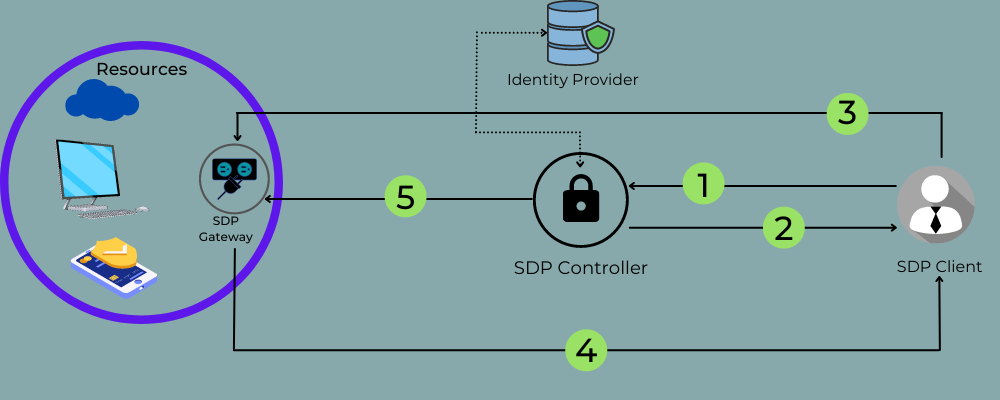
So, when the SDP resolution has authenticated the machine and the person, it creates a separate connection between the machine and the server it tries accessing. The authenticated person is supplied with a separate community connection and never linked to a wider community. Nobody apart from the authenticated person can entry this community and the accepted providers.
This technique varieties sturdy safety for the group implementing an SDP resolution. It prevents attackers and unauthorized from infiltrating the community or accessing the property.
Advantages of SDP Options for What you are promoting?
With growing cybersecurity dangers, distributed workforce, and a number of machine utilization, methods like software-defined perimeter (SDP) options appear to make good sense. Let’s perceive how SDP options will be helpful for what you are promoting.
Elevated Web Safety
The web comes with inherent dangers from attackers who wish to penetrate your community and programs to steal info, take over accounts, and pose numerous threats. The chance has turn into extra grave after distributed workforce preparations like earn a living from home. Now, your staff, freelancers, or contractors could be working with you from around the globe utilizing totally different gadgets and networks, which could possibly be insecure.
Therefore, you possibly can safe your community and organizational property from malicious brokers utilizing an SDP resolution. It helps you enhance web safety inside your group for every person and machine whereas stopping unauthorized customers.
Safer Multi-Cloud Entry
You may securely entry a number of cloud providers utilizing only one atmosphere utilizing an SDP resolution.
You might have been utilizing providers like Microsoft Workplace 365, AWS infrastructure providers, a cloud improvement platform, cloud storage, and different providers. All of them want safety, and an SDP resolution is an effective way to safe them. This will even assist you begin your Zero Belief safety journey by securing each connection, machine, and person no matter the place they’re positioned or hosted.
Quicker Mergers and Acquisitions
Mergers and Acquisitions (M&A) with conventional strategies will be very complicated and time-consuming when converging networks, gadgets, IPs, and property. Utilizing an SDP resolution will simplify this course of and safe them with strict safety insurance policies that require correct authentication for every person and machine. It would additionally minimize down the time spent on settling the processes to get began shortly and run your operations.
Low Third-Occasion Dangers
Usually, organizations could give further privileges to third-party customers that they don’t want to meet their roles. For those who don’t monitor entry on your third-party customers correctly, it could create safety loopholes for attackers.
However if you happen to use an SDP resolution, you possibly can handle this concern by giving required entry to each person, together with third-party customers, sufficient to do their jobs. The approved customers can solely entry your community, functions, and property they’re allowed to. Therefore, they gained’t have the ability to see different property or make modifications to them. This considerably lowers safety dangers.
An Different to VPN
Utilizing VPNs can typically be tedious, powerful to handle, and invite safety dangers. VPN could provide encrypted entry however could not let you entry a sure community. This is the reason many organizations are in search of a greater, safer various to VPNs, reminiscent of SDP options.
Other than the above advantages, SDP options can even assist you limit wider community entry in order that customers can solely entry particular providers and forestall vulnerability and port scanning by attackers and malicious software program. An SDP resolution can assist a number of gadgets, join numerous programs, and isolate mission-critical knowledge and apps for safety.
So, if you wish to introduce SDP in your group, listed below are a few of the greatest software-defined perimeter (SDP) options for small to massive companies.
Perimeter 81
Construct a concrete wall round your community with Perimeter 81’s software-defined perimeter resolution and change VPN legacy. It will possibly assist you design a stronger and extra versatile entry coverage e-book for machine and person authentication.
Perimeter 81 deploys safety instruments for contemporary organizations with distant customers, entry necessities, and sophisticated cloud networks. It would assist cut back the assault floor by offering each person with restricted and distinctive entry to the cloud networks. As well as, it gives Zero Belief entry, granular entry controls, and hybrid safety.
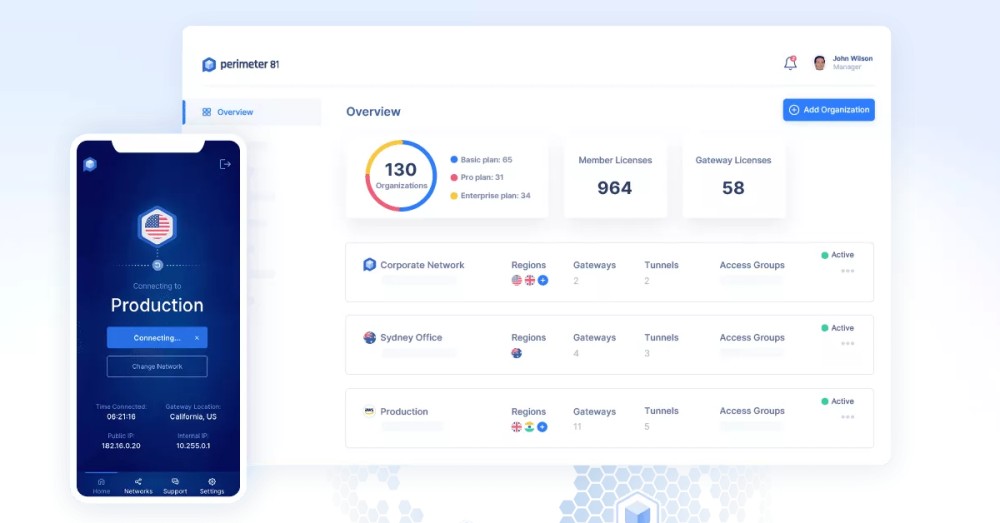
Perimeter 81’s SDP supplies a micro-segmentation utility so that you could give entry to a specific community at a time and defend your most delicate info. The central dashboard additionally helps you create a central coverage based mostly on the machine, location, person, and extra.
Whether or not you need SDP on your cloud or on-premises infrastructure, you possibly can reap the benefits of the complete SDP mannequin to combine together with your group. It gives many extra advantages, reminiscent of overcoming the {hardware} limitations, offering a number of layer safety, working remotely with the identical energy.
Expertise some great benefits of SDP in your group, with Perimeter 81 at $8/person/month plus $40/month/gateway. Avail of a 30-day money-back assure with each plan.
NordLayer
NordLayer supplies a Safe Service Edge resolution inside an SDP atmosphere. This makes the service extremely versatile and scalable, catering to dynamic office environments. With NordLayer, it’s straightforward to safe functions, delicate info, and your worker’s knowledge exchanges.

Utilizing encrypted tunnels to safe entry from staff’ gadgets to Safe Net Gateways, NordLayer seals all entry factors into the group. Staying devoted to the Zero Belief mantra, every entry is totally checked earlier than being allowed into the community. That is achieved by imposing multi-factor authentication and verifying the person’s identification with biometrics.
The app is constructed from the bottom up to not confuse on a regular basis customers whereas nonetheless offering the depth of configuration for community directors. They will orchestrate the service from the handy net interface establishing safety insurance policies. Options like ThreatBlock, jailbroken machine detection, and DNS filtering give further customization alternatives in order that IT managers can modify the service to suit their danger situations.
NordLayer helps to realize compliance necessities by contributing to general office cybersecurity. The service itself obtained ISO/IEC 27001 certification for managing knowledge safety.
As well as, NordLayer’s deployment doesn’t disrupt any current infrastructure — it may be mixed with presently used instruments. The product is hardware-free and constructed with extremely agile workplaces in thoughts.
That stated, community efficiency isn’t an afterthought. NordLayer helps cutting-edge NordLynx tunneling protocol, an upgraded WireGuard tunneling protocol. With a minimal drop again in web speeds, your VoIP calls and different bandwidth-intensive functions gained’t be affected.
Appgate
Strengthen and simplify your entry controls for every person with Appgate’s software-defined perimeter resolution. It helps cut back the assault floor by giving entry and authorization to restricted customers whereas making workloads, functions, and ports invisible for others.
Confirm each person identification based mostly on the context like date, time, machine posture, function, and placement and modify entitlements dynamically based on the identification modifications. Utilizing micro-segmentation helps you eradicate entry and visibility to undesirable sources.

Furthermore, safe bi-directional visitors helps you management each connection between sources. You may as well cut back complexity by simplifying some insurance policies, giving versatile internet hosting and person entry, automating entry, and extra. Apart from, SDP can provide excessive efficiency, i.e., 93% effectivity and fewer than 1ms latency, together with boosting your productiveness and lowering a number of instrument utilization.
With a number of tunneling, you possibly can concurrently join customers to the accepted SaaS, on-premises sources, and cloud. Zero Belief entry permits for streamlined automation, reminiscent of automated insurance policies, automated infrastructure, workflows, machine checking, and placing knowledge to work. Moreover, permit your customers to work in hybrid environments with out re-authenticating or switching except there’s a requirement for multi-factor authentication.
Cloudflare Zero Belief
Use Cloudflare’s Zero Belief utility entry and finish phishing, malware, and knowledge loss. It prevents you from these conventional instruments that join customers to varied company functions and grant entry, which exposes you to knowledge loss.
Cloudflare replaces conventional strategies with the worldwide edge SDP, making the web safer and sooner for customers throughout the globe. It gives a safe, dependable, and quick community to your prospects, companions, and staff to assist them do their work. You additionally get constant controls throughout on-premises, SaaS, and cloud functions.
Cloudflare’s Zero Belief entry integrates with many accessible identification suppliers. It additionally protects your functions with posture, identification, and person context0driven guidelines. As well as, you possibly can audit your worker actions inside your SaaS functions simply.
Isolate programs from the endpoints to dam malware and phishing earlier than they strike utilizing a safe gateway. Cloudflare Zero Belief gives 80% much less time resolving safety posture, a 91% discount in floor assaults, and setup time inside 30 minutes to unlock safer web and sooner utility entry.
Get spectacular options in each plan you buy, together with non-public routing, community firewall, cloud entry, safe gateway, HTTP/s inspection, and DNS decision. Use the platform for FREE for as much as 50 customers, or pay $7/person for extra advantages.
Twingate
Twingate makes Zero Belief community entry easy for you. It implements the least entry privilege to non-public sources and supplies a wonderful end-user expertise. It additionally secures particular person gadgets, sources, and customers as a substitute of simply networks to assist companies safe their essential info.
Twingate makes use of a verified person identification as a substitute of an IP handle to outline community entry rights, grant entry per person context (reminiscent of location, time, date, machine posture, and many others.), and supply fine-tuned insurance policies with analytics for higher visibility.
Twingate doesn’t want readdressing or reconfiguring your infrastructure and makes end-user setup simpler, similar to putting in an utility. You may strive Twingate with out changing VPN by deploying Zero Belief inside 25 minutes. As well as, you should utilize two-factor authentication for something, together with RDP, SSH, and different providers. It additionally helps identification suppliers like OneLogin, Google Workspace, Azure AD, and Okta.
Twingate is FREE for as much as 5 customers. It prices $10/month/person for as much as 150 customers, together with 5 gadgets per person, ten distant networks, identification supplier integration, useful resource degree entry management, and extra.
ZoneZero
ZoneZero gives a centralized Zero Belief safety resolution based mostly on identification and multi-factor authentication for each person, reminiscent of VPN customers, community customers, distant entry customers, and extra. You may as well add secondary multi-factor authentication to any utility, together with proprietary providers, legacy functions, file shares, SFTP, databases, net functions, SSH, RDP, and many others.
ZoneZero supplies nearly every little thing you want in a single place, like:
- Separating management and knowledge planes
- Making use of required person insurance policies
- Permitting you to get segmentation based mostly on identification inside your community
- Introducing multi-factor authentication to utility, service, or VPN
- Utilizing Protected-T’s reverse entry expertise
- Providing identity-based Zero Belief
- Enabling fast deployment and seamless implementation
- Providing central administration for full efficacy and transparency
Zscaler
Zscaler supplies Zero Belief entry seamlessly to non-public functions operating inside the knowledge heart or public cloud. You don’t have to decide on between safety and person expertise with this resolution; it does each concurrently. It additionally makes your programs and functions invisible to unauthorized customers and protects your important knowledge.
Zscaler helps managed gadgets, unmanaged gadgets, and personal functions. You may take pleasure in seamless entry throughout gadgets and functions and get total visitors visibility for sooner troubleshooting and a greater person expertise. It additionally offers approved customers direct entry to non-public functions to attenuate the chance of lateral motion.
Your community admins gained’t should handle FW or ACLs insurance policies and phase networks. As a substitute, micro tunnels permit them to phase by utility. You may as well safe your non-public apps utilizing customized PKI and TLS-based encrypted tunnels.
Zscaler API makes Zero Belief simpler for IT, and its API creates entry insurance policies robotically for the found functions and generates auto-segmentation of utility workloads. With Zscaler’s Zero Belief community entry structure, DDoS assaults and IP leaks are uncommon.
Zscaler is designed for easy administration, larger scalability, excessive availability, and robust safety. Whether or not you could have distant customers or on-premises customers, you possibly can deliver the identical energy for all with Zscaler’s cloud-delivered non-public and public service edge.
Take a FREE trip with Zscaler Personal Entry to see how customers are linked with their non-public functions.
Verizon
Put an additional layer of confidence with Verizon Software program Outlined Perimeter in defending your property from community assaults. It applies the Zero Belief strategy for inner community segmentation, cloud functions, and distant entry.
Verizon permits customers to entry community sources by isolating servers and defending them from server exploitation because of configuration errors and vulnerabilities. Its multi-factor authentication prevents your community from credential theft, reminiscent of pass-the-hash, and builds TLS tunnels to keep away from man-in-the-middle assaults.

Every SDP occasion is assigned to a single buyer and can’t be shared with others, whereas the gateways and controllers will be positioned after they want them. The safety resolution will even give an ultra-fast efficiency for the functions utilizing an optimum path to the info.
Purchase the providers you want, set up them your self, and have full transparency into which customers use what gadgets on which utility and from the place. Verizon’s skilled and managed providers are a greater various to community monitoring and in-house administration. You additionally get main SLA and complete instruments to assist your IT group focus in your initiatives.
Jamf
Join customers to the functions, knowledge, and gadgets safely with Jamf Personal Acess and enhance productiveness. It helps fashionable firms guarantee safe entry to the sources if their staff work from numerous places on totally different gadgets. Jamf ensures the correct customers entry approved gadgets, no matter their location.
Jamf Personal Entry integrates with cloud identification suppliers to make sure all of the customers have safe entry to the sources. It gives Zero Belief Community Acess that replaces VPN expertise and conditional entry. It builds a Micro tunnel to forestall community motion and permits the least entry privileges.

Jamf Personal Acess supplies fashionable cloud infrastructure with no {hardware} to handle, no renewing contracts, and no complexity to configure the software program. It additionally integrates with Single Signal-On to eradicate the hassles of managing certificates. As well as, you’ll expertise environment friendly and quick connectivity, higher end-user privateness, and optimized community infrastructure because it permits non-business functions to attach with the web straight.
Attempt Jamf Personal Entry for your self by taking a FREE trial, and purchase it when you could have developed confidence.
Conclusion
Utilizing sturdy safety methods and providers reminiscent of a software-defined perimeter resolution (SDP) may help you safe your functions, servers, programs, customers, gadgets, and community from attackers and unauthorized customers. It would considerably cut back the assault floor and guarantee solely approved customers can entry accepted property.
So, if you wish to shift from conventional network-based safety approaches, you possibly can introduce an SDP resolution like those we simply mentioned and hold your group and property safe from assaults.
You might also take a look at VPN vs. SDP vs. ZTNA.

