A suspicious login detection answer might help you add an additional layer of safety to your software program merchandise/providers and web site.
It secures your customers’ accounts, protects their credentials and different knowledge, and provides them another reason to decide on you over others.
However questioning what is the level of all this in case you’ve already put some effort into your software’s safety?
Is not it sufficient?
The reply is that it’s by no means sufficient in relation to cybersecurity. The safer you can also make your software, the higher it’s.
In keeping with Akamai, 43% of all on-line login makes an attempt are malicious. That is alarming to anybody working or utilizing any web site, software program services or products that shops private info.
And for this reason it is best to make your software program safer by implementing safety programs comparable to suspicious login detection.
Let’s perceive what it’s and the way it may be helpful for your corporation.
What’s suspicious login detection?
There are numerous behaviors you can flag as suspicious based mostly on their login nature. A hacker can use a number of passwords to entry a consumer account for software program, websites, or providers.
Some suspicious detections are low danger, whereas others could also be increased danger. It may be carried out by logging in:
- At an uncommon time
- From totally different places
- From totally different gadgets
- After many failed makes an attempt
Purposes are typically in danger from third-party safety breaches, comparable to huge password leaks. The second this occurs, the hacker can steal obligatory or crucial details about a consumer. They will then misuse the knowledge, misuse it with threats, or steal the account altogether.
A suspicious login detection system informs you of the mischief that will quickly occur. This software identifies the patterns of login conduct which can be barely totally different from the common logins.
Some functions use bots that examine uncommon speeds throughout login makes an attempt. At that time they are often blocked from logging in and you may be notified. Alternatively, they might be prompted for added steps comparable to e mail verification, MFA problem, and a code despatched to a registered cellular quantity.
Why is it important to implement suspicious login detection?
Safety is a significant concern within the SaaS market. Within the present state of affairs, many use SaaS merchandise for numerous functions of their day by day lives. That being mentioned, everybody seeks safety, whether or not or not it’s fee credentials comparable to giving card particulars, deal with, telephone numbers, and so forth., or credentials comparable to usernames or passwords.
When you do not present safety in your SaaS product, consumer info might be hacked or misused. Because of this, your clients will discover it troublesome to belief you.
This is the reason in case you run a SaaS product firm, it’s essential to concrete your safety measures in order that your clients will belief you and your organization with their private info. You cope with enormous buyer knowledge daily, so safety insurance policies and programs additionally be sure that each buyer’s knowledge is protected.
Implementing a safe answer like Suspicious Login Detection might be efficient in your SaaS services or products to offer the next stage of safety in your clients’ knowledge and be sure that nobody can misuse it or threaten customers.
The way it helps customers keep protected?
In at the moment’s busy schedule, everyone seems to be searching for handy operation. Individuals use web sites and functions daily, together with Gmail, Snapchat, Instagram, Fb, Amazon, Flipkart, eBay, productiveness instruments, time administration, and plenty of extra.
Utilizing an API to detect suspicious logins, comparable to Zenlogin, ensures that customers’ knowledge is protected. And even when one thing suspicious occurs, it could possibly warn you to take fast motion and shield your customers’ accounts and knowledge.
A safe login permits the customers to confirm their login with numerous authentication mechanisms. Customers obtain alerts or notifications when somebody tries to log into their account from one other machine, uncommon places, and far more.
Suspicious login detection helps you shield your info throughout login. The second you obtain an alert, it is able to provide you with some steps to comply with with the intention to instantly safe the account with none errors or issues.
Examples of login notifications:
You’ll obtain alerts in emails or textual content messages about suspicious exercise, comparable to:
- Obtain a warning message when somebody tries to vary your password
- Ask a safety query throughout login in case your login is questionable
- Obtain an e mail associated to the account while you sort the identical within the field
- Get a warning on the identical web page while you log in if the unsuitable username or password is entered
- Obtain a textual content notification from a service like Gmail in your cellular asking you to sort sure or no or ship a textual content code for verification
When an uncommon login happens from a brand new machine or location, customers ought to safe an account if they don’t carry out the exercise.
However how?
Customers ought to rigorously assessment the security measures and skim the privateness coverage when logging into an software. Ensure the appliance takes care of your credentials.
For safe login, customers can comply with a couple of steps on a person stage:
- Create complicated and lengthy passwords with uppercase, lowercase, particular characters, numbers, and so forth.
- Utilizing a fancy username as a substitute of an apparent one
- By no means share important credentials
- Utilizing totally different passwords for various actions
- Keep away from giving out private info.
Customers can comply with the steps above to cut back the chance of threats of their accounts. However what in case you might strengthen your SaaS product or software program from the bottom up?
It provides an additional layer of safety to your software program and additional reduces the risk floor. You are able to do this by utilizing a wonderful answer for detecting suspicious logins.
There are numerous in the marketplace, however it’s essential to ensure you are utilizing one of the best software program for the protection of your customers. A dependable API for detecting suspicious logins is from Zenlogin. Let’s have a look at the way it might help you safe your software program.
How can Zenlogin assist?
Zenlogin gives safety with its suspicious login detection API. It may possibly ship fast e mail notifications to customers upon detecting suspicious login exercise. It gives a fast means so as to add a layer of safety to your SaaS merchandise and software program.
Zenlogin can present peace of thoughts to builders, product managers, founders and different stakeholders by making certain their customers are utilizing safe software program and their knowledge just isn’t compromised.
Utilizing Zenlogins API to detect suspicious logins removes the overhead of in-house improvement of the safety system. Zenlogin detects suspicious logins and alerts customers through emails.
What are the options and advantages of Zenlogin?
Listed below are a number of the key options and advantages of Zenlogin that may assist maintain your software program safe in order that customers can belief you.
Simple for builders
Zenlogin makes it straightforward for builders to combine it into your software program product. It additionally comes with preset sensitivity intervals and preset e mail notifications. It saves your builders plenty of time, in order that they contribute to innovation.
Sensitivity controls
Zenlogin offers you higher management over the occasions when a consumer is warned about suspicious login makes an attempt. It’ll additional improve your customers’ belief in your product and model.
First-class safety
Zenlogin is designed to offer top-notch safety. It ensures the best strategy to improve the safety of your software, service or web site. They use the newest safety applied sciences to strengthen their stage of safety. The safety answer protects all knowledge within the software and prevents hackers from misusing or accessing it.
Map integration
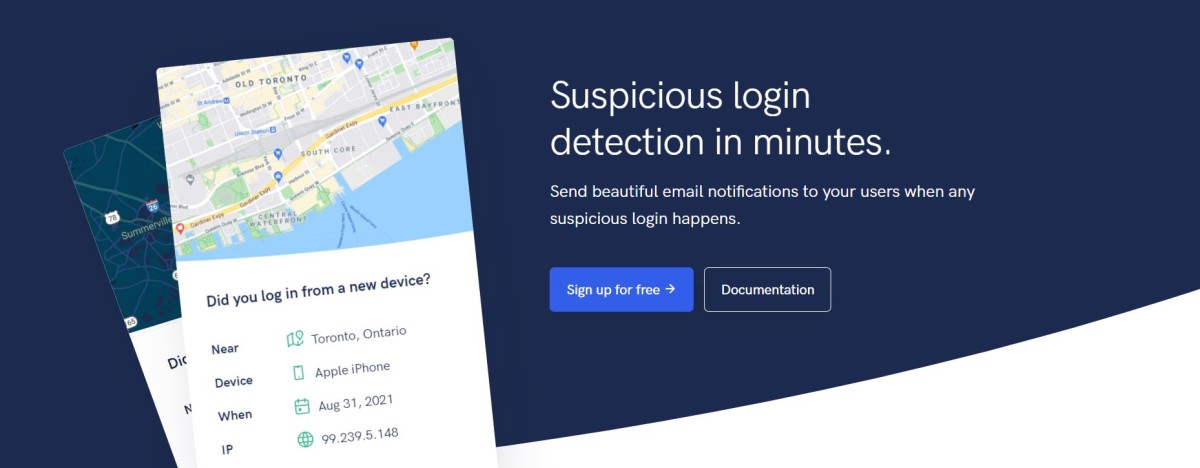
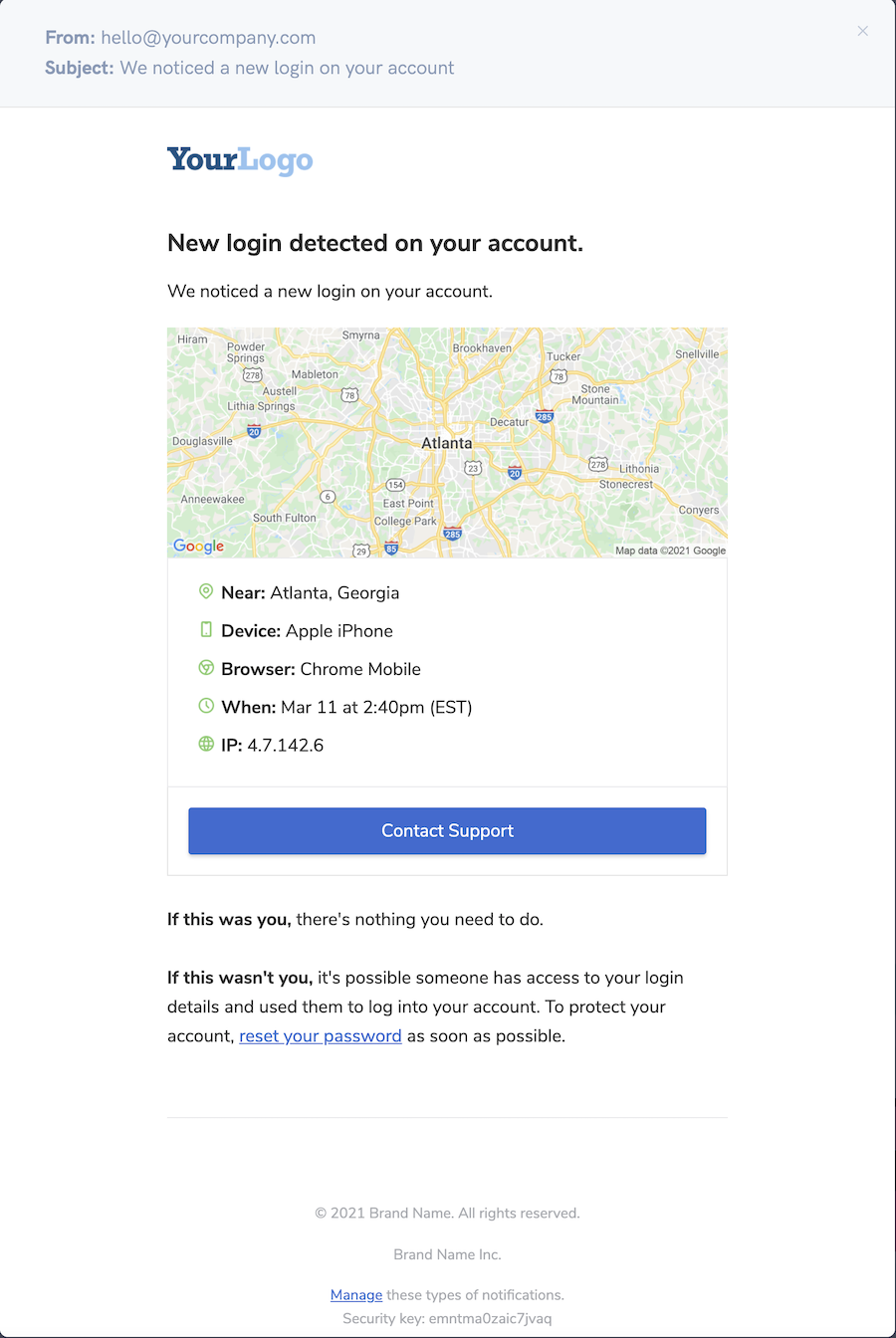
It lets you combine stunning playing cards into e mail notifications. It permits customers to shortly visualize if their account is beneath risk or compromise.
Detailed logs
You may monitor all suspicious login makes an attempt on customers’ accounts and log them in a single place inside Zenlogin. It incorporates all the mandatory particulars you need to maintain monitor of to offer a safer software to your customers.
Customized Guidelines
With Zenlogin you’ll be able to outline some particular guidelines and allow your group to be notified instantly when there’s a suspicious login try on their accounts.
Fast to arrange
Zenlogin is simple and fast to arrange for any endpoint inside minutes. So it saves plenty of time and vitality. You can begin utilizing it after pasting in a couple of strains of code written in Curl, PHP, Python, Ruby or Node.js.
Aside from all these, Zenlogin affords premium name assist, doesn’t retailer any private info and easy e mail notifications.
How does Zenlogin work?
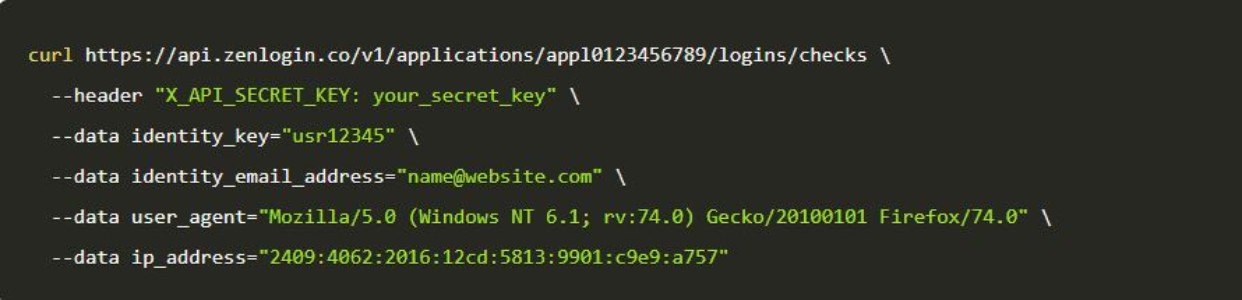
You may construct top-notch safety in your functions in minutes utilizing Zenlogins API to detect suspicious logins in a couple of straightforward steps. Here is how Zenlogin works.
1. Paste a code snippet
To get began, all it’s essential to do is paste in a smaller code snippet. Zenlogin helps all main server-side languages comparable to PHP, Python, Node.js, Ruby, Curl, and so forth.
2. Modify the safety stage
Choose the sensitivity stage for the detection of suspicious logins. You’ll obtain an e-mail with quite a few fields to fill in. Primarily based on this, your safety stage is customized to your corporation wants and consumer base.
3. Shield the customers
The above integrates Zenlogin’s suspicious login detection API into your software, website or providers. Then the API will begin monitoring logins and warn you when one thing appears to be like suspicious. And you may also begin monitoring all suspicious exercise and enhance your product.
Right here is the instance of an e mail notification.
Costs
On the time of writing this text, Zenlogin has two pricing plans which can be appropriate for various firms.
- Free: This plan is free endlessly when you have lower than 5,000 requests per 30 days and permit 500 e mail alerts per 30 days.
- Professional: It is a paid plan priced at $49/month. It permits 25,000 requests per 30 days and a pair of,500 login emails per 30 days and premium options comparable to detailed logs, map integration, customized guidelines, the choice to take away branding, and so forth.
Plus, you’ll be able to strive the Professional plan free of charge for 30 days and determine if it really works for your corporation or not.
Conclusion 👩💻
The net world affords many alternatives, comfort and choices to make our lives simpler. Nevertheless it additionally consists of dangers and risks.
Subsequently, SaaS firms should shield their software program merchandise/providers and customers from knowledge theft by implementing safe applied sciences comparable to suspicious login detection options comparable to Zenlogin.