Cybersecurity points are rising and turning into extra sophisticated as expertise advances.
Although you possibly can’t cease cybercriminals from getting smarter, you possibly can make use of safety techniques like IDS and IPS to scale back the assault floor and even block them. This brings us to the battle – IDS vs. IPS to decide on what’s higher for a community.
And if you would like the reply to that, you could perceive what these applied sciences are of their essence, how they work, and their varieties. It’ll show you how to select the higher possibility in your community.
That stated, each IDS and IPS are safe and efficient, every with its professionals and cons, however you possibly can’t take an opportunity in the case of safety.
That is why I’ve give you this comparability – IDS vs. IPS that will help you perceive their capabilities and discover the higher answer to safeguard your community.
Let the battle start!
IDS vs. IPS: What Are They?
Earlier than we begin evaluating IDS vs. IPS, let’s discover out what they’re within the first place, beginning with IDS.
What Is an IDS?
An Intrusion Detection System (IDS) is a software program answer that displays a system or community for intrusions, coverage violations, or malicious actions. And when it detects an intrusion or violation, the software program stories it to the administrator or safety personnel. It helps them examine the reported incident and take appropriate treatments.
This passive monitoring answer can warn you to detect a risk, however it may possibly’t take direct measures in opposition to it. It’s like a safety system put in in a constructing that may notify the safety guard about an incoming risk.
An IDS system goals to detect a risk earlier than it infiltrates a community. It offers you the ability to check out your community with out obstructing the community visitors circulate. Other than detecting coverage violations, it may possibly guard in opposition to threats like info leaks, unauthorized entry, configuration errors, Trojan horses, and viruses.
It really works greatest once you don’t need to hinder or decelerate the visitors circulate even when a problem surfaces however to safeguard your community property.
What Is An IPS?
Intrusion Prevention System (IPS) can be referred to as Intrusion Detection & Prevention System (IDPS). It’s a software program answer that displays a system or community actions for malicious incidents, logs info on these actions, stories them to the administrator or safety personnel, and makes an attempt to cease or block them.
That is an lively monitoring and prevention system. You’ll be able to contemplate it as an extension of IDS as a result of each strategies monitor malicious actions. Nevertheless, in contrast to IDS, IPS software program is positioned behind the community firewall speaking in keeping with the incoming visitors and blocking or stopping detected intrusions. Consider it because the (cyber) safety guard in your community.
Upon detecting a risk, IPS can take varied actions equivalent to sending alarms, dropping recognized malicious packets, blocking the malicious IP deal with from accessing the community, and resetting connections. As well as, it may possibly additionally appropriate errors associated to cyclic redundancy verify (CRC), defragmented packet streams, clear up additional community layers and transport choices, and mitigate errors related to TCP sequencing.
IPS is the most suitable choice for you if you wish to block assaults as quickly because the system detects them, even when it’s a must to shut all visitors, together with the professional ones, for safety. Its aim is to mitigate harm from each exterior and inside threats in your community.
IDS vs. IPS: Sorts
Sorts of IDS
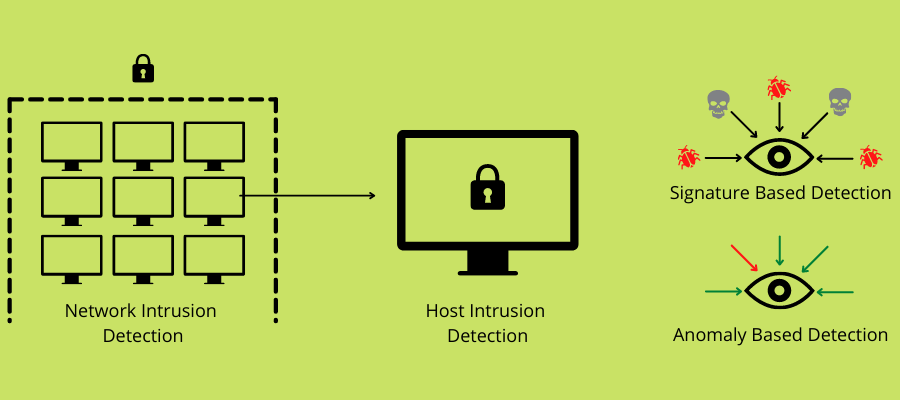
IDS is split based mostly on the place the risk detection occurs or what detection technique is employed. IDS varieties based mostly on the place of detection, i.e., community or host, are:
#1. Community Intrusion Detection Techniques (NIDS)
NIDS is part of community infrastructure, monitoring packets flowing by it. It co-exists with the units with a faucet, span, or mirroring skill like switches. NIDS is positioned at a strategic level(s) inside a community to observe incoming and outgoing visitors from all of the linked units.
It analyzes visitors passing by the entire subnet, matching these visitors passing the subnets to the identified assault library. As soon as NIDS identifies the assaults and senses an irregular habits, it alerts the community admin.
You’ll be able to set up a NIDS behind the firewalls on the subnet and monitor whether or not or not somebody tries to infiltrate your firewall. NIDS may also examine comparable packets’ signatures with matching data to hyperlink malicious detected packets and cease them.
There are two forms of NIDS:
- On-line NIDS or in-line NIDS offers with a community in real-time. It analyzes Ethernet packets plus applies particular guidelines to find out whether or not it’s an assault or not.
- Off-line NIDS or faucet mode offers with collected information. It passes the information by some processes and decides the result.
Moreover, you possibly can mix NIDS with different safety applied sciences to extend prediction and detection charges. For instance, NIDS based mostly on Synthetic Neural Community (ANN) can analyze large information volumes well as a result of its self-organizing structuring permits INS IDS to acknowledge assault patterns extra effectively. It might probably predict assaults based mostly on earlier errors that led to the intrusion and helps you develop an early-stage incomes system.
#2. Host-based Intrusion Detection Techniques
Host-based Intrusion Detection Techniques (HIDS) are the answer working on separate units or hosts on a community. It might probably solely monitor incoming and outgoing information packets from the linked units and alert the admin or customers upon detecting suspicious exercise. It displays system calls, file adjustments, utility logs, and so forth.
HIDS takes snapshots of the present recordsdata within the system and matches them to the earlier ones. If it finds {that a} important file is deleted or modified, the HIDS sends an alert to the admin to analyze the problem.
For instance, HIDS can analyze password logins and examine them in opposition to identified patterns utilized to hold out brute drive assaults and establish a breach.
These IDS options are used extensively on mission-critical machines whose configurations aren’t anticipated to vary. Because it displays occasions straight on hosts or units, a HIDS answer can detect threats {that a} NIDS answer would possibly miss.
It is usually efficient in figuring out and stopping integrity breaches equivalent to Trojan horses and dealing in encrypted community visitors. This fashion, HIDS protects delicate information like authorized paperwork, mental property, and private information.
Other than these, IDS can be of different varieties, together with:
- Perimeter Intrusion Detection System (PIDS): Performing as the primary line of protection, it may possibly detect and find intrusion makes an attempt on the central server. This setup normally consists of a fiber optic or digital gadget sitting onto a server’s digital perimeter fence. When it senses a malicious exercise equivalent to somebody attempting to try entry by a unique technique, it alerts the admin.
- VM-based Intrusion Detection System (VMIDS): These options can mix the IDS talked about above or one among them. The distinction is that it’s deployed remotely utilizing a digital machine. It’s comparatively new and primarily utilized by managed IT service suppliers.
Sorts of IPS
Basically, intrusion prevention techniques (IPS) are of 4 varieties:
#1. Community-based Intrusion Prevention System (NIPS)
NIPS can establish and forestall suspicious or malicious actions by analyzing information packets or checking protocol exercise all through a community. It might probably collect information from the community and host to detect permitted hosts, working techniques, and purposes on the community. As well as, NIPS logs information on regular visitors for locating adjustments from the bottom up.
This IPS answer mitigates assaults by limiting bandwidth utilization, sending TCP connections, or rejecting packets. Nevertheless, NIPS shouldn’t be efficient in analyzing encrypted visitors and dealing with direct assaults or excessive visitors hundreds.
#2. Wi-fi Intrusion Prevention System (WIPS)
WIPS can monitor a wi-fi community to detect suspicious visitors or actions by analyzing wi-fi community protocols and taking measures to stop or take away them. WIPS is carried out sometimes overlaying the present wi-fi LAN community infrastructure. Nevertheless, it’s also possible to deploy them standalone and implement a no-wireless coverage in your group.
This IPS answer can stop threats like a misconfigured entry level, denial of service (DOS) assaults, honeypot, MAC spoofing, man-in-the-middle assaults, and extra.
#3. Community Behaviour Evaluation (NBA)
NBA works on anomaly-based detection, on the lookout for anomalies or deviations from regular habits to suspicious habits within the community or system. Due to this fact, for it to work, the NBA should undergo a coaching interval to be taught the conventional habits of a community or system.
As soon as an NBA system learns the conventional habits, it may possibly detect deviations and flag them as suspicious. It’s efficient, but it surely received’t work whereas nonetheless within the coaching section. Nevertheless, as soon as it graduates, you possibly can depend on it.
#4. Host-based Intrusion Stop Techniques (HIPS)
HIPS options can monitor important techniques for malicious actions and forestall them by analyzing their code habits. What’s greatest about them is that they will additionally detect encrypted assaults other than safeguarding delicate information associated to private identification and well being from the host techniques. It really works on a single gadget and is commonly used with a network-based IDS or IPS.
IDS vs. IPS: How Do They Work?
There are completely different methodologies utilized in monitoring and stopping intrusions for IDS and IPS.
How Does An IDS Work?
IDS makes use of three detection strategies to observe visitors for malicious actions:
#1. Signature-based or Information-based Detection
Signature-based detection displays particular patterns like cyberattack signatures that malware makes use of or byte sequences within the community visitors. It really works the identical means as antivirus software program when it comes to figuring out a risk by its signature.
In signature-based detection, the IDS can establish identified threats simply. Nevertheless, it might not be efficient in new assaults with no out there patterns, as this technique works solely based mostly on earlier assault patterns or signatures.
#2. Anomaly-based or Conduct-based Detection
In anomaly-based detection, the IDS displays violations and intrusions in a community or system by monitoring system logs and figuring out whether or not any exercise appears anomalous or deviated from regular habits specified for a tool or community.
This technique can detect unknown cyberattacks as properly. IDS may also use machine studying applied sciences to construct a trusted exercise mannequin and set up it because the baseline for a standard behavioral mannequin to check new actions and declare the result.
You’ll be able to practice these fashions based mostly in your particular {hardware} configurations, purposes, and system wants. In consequence, IDS with habits detection have enhanced safety properties than signature-based IDS. Though it might present some false positives typically, it really works effectively in different points.
#3. Popularity-based Detection
IDS utilizing reputation-based detection strategies, acknowledge threats based mostly on their repute ranges. It’s performed by figuring out communication between a pleasant host inside your community and the one trying to entry your community based mostly on their repute for violations or malicious actions.
It collects and tracks completely different file attributes like supply, signature, age, and utilization statistics from customers utilizing the file. Subsequent, it may possibly use a repute engine with statistical evaluation and algorithms to investigate the information and decide whether or not it’s threatening or not.
Popularity-based IDS is used primarily in anti-malware or antivirus software program and carried out on batch recordsdata, executable recordsdata, and different recordsdata which may carry unsafe code.
How Does An IPS Work?
Much like IDS, IPS additionally works with strategies like signature-based and anomaly-based detection, along with different strategies.
#1. Signature-based Detection
IPS options utilizing signature-based detection monitor information packets incoming and outgoing in a community and examine them with earlier assault patterns or signatures. It really works on a library of identified patterns with threats carrying malicious code. When it discovers an exploit, it data and shops its signature and makes use of it for additional detection.
A signature-based IPS is of two varieties:
- Exploit-facing signatures: IPS identifies intrusions by matching signatures with a risk signature within the community. When it finds a match, it tries to dam it.
- Vulnerability-facing signatures: Hackers goal present vulnerabilities in your community or system, and the IPS tries to guard your community from these threats which may go undetected.
#2. Statistical Anomaly-based or Conduct-based Detection
IDS utilizing statistical anomaly-based detection can monitor your community visitors to seek out inconsistencies or anomalies. It units a baseline to outline the conventional habits for the community or system. Based mostly on this, the IPS will examine the community visitors and flag suspicious actions that deviate from the conventional habits.
For instance, the baseline could possibly be a specified bandwidth or protocol used for the community. If the IPS finds visitors rising the bandwidth abruptly or detects a unique protocol, it is going to set off an alarm and block the visitors.
Nevertheless, you need to deal with configuring the baselines intelligently to keep away from false positives.
#3. Stateful Protocol Evaluation
An IPS, utilizing stateful protocol evaluation, detects deviations of a protocol state like anomaly-based detection. It makes use of predefined common profiles in response to accepted practices set by trade leaders and distributors.
For instance, the IPS can monitor requests with corresponding responses, and every request should include predictable responses. It flags responses falling exterior the anticipated outcomes and analyzes them additional.
When an IPS answer displays your techniques and community and finds suspicious exercise, it alerts and performs some actions to stop it from accessing your community. Right here is how:
- Strengthening firewalls: The IPS would possibly detect a vulnerability in your firewalls that paved the best way for the risk to enter your community. To supply safety, the IPS would possibly change its programming and strengthen it whereas fixing the problem.
- Performing system clean-up: Malicious content material or broken recordsdata would possibly corrupt your system. That is why it performs a system scan to wash it up and take away the underlying challenge.
- Closing periods: The IPS can detect how an anomaly has occurred by discovering its entry level and blocking it. For this, it’d block IP addresses, terminate the TCP session, and so forth.
IDS vs. IPS: Similarities and Variations
Similarities Between IDS and IPS
The early processes for each IDS and IPS are comparable. Each of them detect and monitor the system or community for malicious actions. Let’s see their widespread grounds:
- Monitor: As soon as put in, IDS and IPS options monitor a community or system based mostly on the desired parameters. You’ll be able to set these parameters based mostly in your safety wants and community infrastructure and allow them to examine all of the visitors incoming and outgoing out of your community.
- Menace detection: Each of them learn all the information packets flowing in your community and examine these packets to a library containing identified threats. Once they discover a match, they flag that information packet as malicious.
- Be taught: Each of those applied sciences use fashionable applied sciences like machine studying to coach themselves for a interval and perceive rising threats and assault patterns. This fashion, they will higher reply to fashionable threats.
- Log: Once they detect suspicious exercise, they document it together with the response. It helps you perceive your safety mechanism, discover vulnerabilities in your system, and practice your safety techniques accordingly.
- Alert: As quickly as they detect a risk, each IDS and IPS ship alerts to safety personnel. It helps them to be ready for each circumstance and take fast motion.
Till this, IDS and IPS work equally, however what occurs after differentiates them.
Distinction Between IDS and IPS
The primary distinction between IDS and IPS is that IDS works as a monitoring and detection system whereas IPS works as a prevention system other than monitoring and detection. Some variations are:
- Response: IDS options are passive safety techniques that solely monitor and detect networks for malicious actions. They will warn you however don’t take any motion on their very own to stop the assault. The community admin or safety personnel assigned should take motion instantly to mitigate the assault. Alternatively, IPS options are lively safety techniques that monitor and detect your community for malicious actions, alert, and robotically stop the assault from occurring.
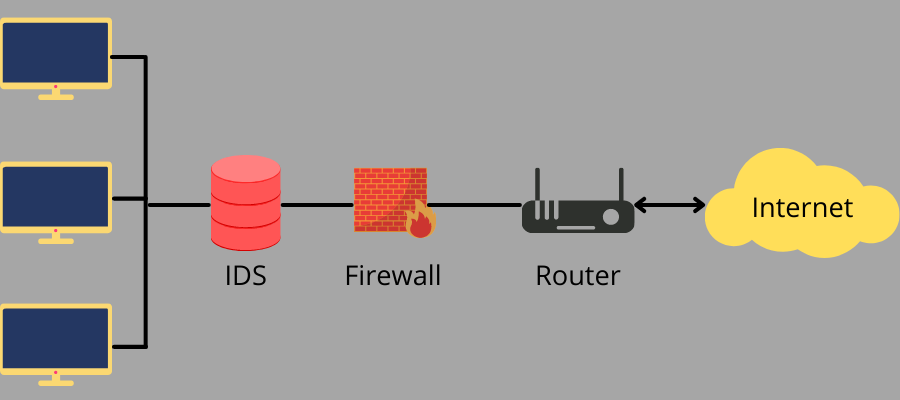
- Positioning: IDS is positioned on the fringe of a community to gather all occasions and log and detect violations. Positioning this fashion offers the IDS the utmost visibility for information packets.IPS software program is positioned behind the community firewall speaking in keeping with the incoming visitors to stop intrusions higher.
- Detection mechanism: IDS makes use of signature-based detection, anomaly-based detection, and reputation-based detection for malicious actions. Its signature-based detection solely contains exploit-facing signatures. Alternatively, IPS makes use of signature-based detection with each exploit-facing and vulnerability-facing signatures. Additionally, IPS makes use of statistical anomaly-based detection and stateful protocol evaluation detection.
- Safety: In case you are below risk, IDS could possibly be much less useful as your safety personnel wants to determine how you can safe your community and clear up the system or community instantly.IPS can carry out computerized prevention by itself.
- False positives: If IDS offers a false optimistic, you could discover some comfort. But when IPS does so, the entire community would endure as you have to to dam all of the visitors – incoming and outgoing the community.
- Community efficiency: As IDS shouldn’t be deployed in-line, it doesn’t scale back community efficiency. Nevertheless, community efficiency can scale back resulting from IPS processing, which is in keeping with the visitors.
IDS vs. IPS: Why They Are Essential for Cybersecurity
You could hear varied incidences of knowledge breaches and hacks occurring in nearly each trade with a web based presence. For this, IDS and IPS play an necessary function in safeguarding your community and techniques. Right here’s how:
Improve Safety

IDS and IPS techniques use automation for monitoring, detection, and prevention of malicious threats. They will additionally use rising applied sciences like machine studying and synthetic intelligence to be taught patterns and treatment them successfully. In consequence, your system is safe from threats like viruses, DOS assaults, malware, and so forth., with out requiring additional sources.
Implementing Insurance policies
You’ll be able to configure IDS and IPS based mostly in your organizational wants and implement safety insurance policies in your community that each packet getting into or leaving the community should adhere to. It helps you shield your techniques and community and spot deviations rapidly if somebody tries to dam the insurance policies and break into your community.
Regulatory Compliance
Information safety is severe within the fashionable safety panorama. That is why regulatory compliance our bodies like HIPAA, GDPR, and so forth., regulate firms and ensure they spend money on applied sciences that may assist shield buyer information. By implementing an IDS and IPS answer, you adjust to these rules and face no authorized bother.
Saves Popularity
Implementing safety applied sciences like IDS and IPS exhibits you care to guard your prospects’ information. It offers your model a very good impression in your prospects and elevates your repute inside and out of doors your trade. As well as, you additionally save your self from threats which may leak your delicate enterprise info or trigger repute harm.
Can IDS & IPS work collectively?
In a phrase, Sure!
You’ll be able to deploy each IDS and IPS collectively in your community. Deploy an IDS answer to observe and detect visitors whereas letting it perceive visitors motion comprehensively inside your community. Additionally, you should utilize IPS in your system as an lively measure to stop safety points in your community.
This fashion, it’s also possible to keep away from the overhead of selecting IDS vs. IPS altogether.
Furthermore, implementing each applied sciences offers you all-around safety in your community. You’ll be able to perceive earlier assault patterns to set higher parameters and put together your safety techniques to struggle extra successfully.
Among the suppliers for IDS and IPS are Okta, Varonis, UpGuard, and so forth.
IDS vs. IPS: What Ought to You Select? 👈
Selecting IDS vs. IPS have to be solely based mostly in your group’s safety wants. Take into account how massive your community is, what your finances is, and the way a lot safety you could select the one.
When you ask what’s higher basically, it have to be IPS because it gives prevention, monitoring, and detection. Nevertheless, it will assist when you selected a greater IPS from a reliable supplier as it may possibly present false positives.
As each have professionals and cons, there’s no clear winner. However, as defined within the earlier part, you possibly can go for each of those options from a dependable supplier. It’ll supply superior safety to your community from each the standpoints – intrusion detection and prevention.