For those who’re defending Nginx with Mod Safety, you may need OWASP core rule set (CRS) enabled to guard towards the next threats.
- Safety towards HTTP protocol violation
- Frequent internet assaults
- Bots, crawlers, malicious exercise safety
- Trojan safety
- Data leakage safety
- Cross-Web site Scripting Assaults
- SQL injection assaults
Will you agree?
In my earlier submit I defined find out how to set up Nginx and Mod Safety and as promised right here is find out how to configure them with OWASP CRS for higher safety.
ModSecurity is an open supply Internet Software Firewall (WAF) and is configured by default to detect solely. Meaning it’s essential allow the required configuration (as follows) to guard your web sites.
ModSecurity CRS obtain
- Obtain the most recent CRS zip file from the next hyperlink and switch it to the server
https://github.com/SpiderLabs/owasp-modsecurity-crs/zipball/grasp
- extract the file
unzip SpiderLabs-owasp-modsecurity-crs-2.2.9-26-gf16e0b1.zip
- Copy the next to the nginx conf folder
modsecurity_crs_10_setup.conf.instance base_rules
Configure Nginx to combine OWASP ModSecurity CRS
Since you’ve determined to make use of OWASP CRS, it’s essential merge the conf file included in SpiderLabs OWASP CRS that you just simply copied (modsecurity_crs_10_setup.conf.instance ) into the nginx folder.
Nginx would not assist a number of ModSecurityConfig directives like Apache, so you need to merge all of the conf strains into one file.
Let’s do it…
- Add base_rules & modsecurity_crs_10_setup.conf.instance to modsecurity.conf file
cat modsecurity_crs_10_setup.conf.instance base_rules/*.conf >>/usr/native/nginx/conf/modsecurity.conf
You even have to repeat every part *.information file to the nginx conf folder
cp base_rules/*.information /usr/native/nginx/conf/
Fast Verification:
Be sure to have added the ModSecurityEnabled and ModSecurityConfig directive within the nginx.conf file below location. If not, add them as under.
location / {
ModSecurityEnabled on;
ModSecurityConfig modsecurity.conf;
}
- Restart Nginx
By doing particularly you’ve efficiently built-in OWASP CRS into Mod Safety on Nginx. It is time to make the little important changes.
Configure OWASP Core Rule Set to begin defending
All adjustments shall be made on this part modsecurity.conf file so keep in mind to again it up.
Firstly
Allow audit logging
It’s important to generate logs in order that what’s being blocked. Add SecAuditLog directive if it doesn’t exist.
SecAuditLog /usr/native/nginx/logs/modsec_audit.log
Restart Nginx and you will notice the generated log file
-rw-r----- 1 root root 0 Might 22 07:54 /usr/native/nginx/logs/modsec_audit.log
Allow safety rule engine
Begin with Mod Safety safety by enabling the principles engine as under
SecRuleEngine On
Allow default motion as Deny
Configure the default motion as “block” for any request that matches the principles.
SecDefaultAction "part:1,deny,log"
Above three configurations is important and now ModSecurity is able to take the motion and shield it.
This is one other configuration you would possibly like.
Change the server header banner
Default Nginx configuration will reveal server info with its model, which is very really useful to masks in case you are working in a PCI-DSS atmosphere.
You might also do that with out Mod Safety as defined right here.
Default header:
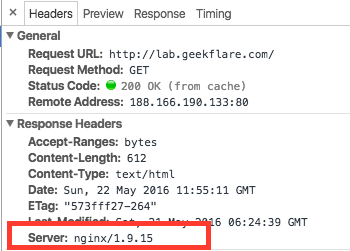
You are able to do this shortly by including a rule.
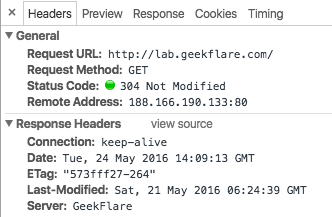
SecServerSignature GeekFlare
And now it appears to be like like this:
I hope above instruction helps you combine OWASP Core Rule Set with Nginx internet server for higher safety.

