A well-liked saying within the cyber safety house is that given sufficient time, any system might be compromised. Scary because it sounds, the assertion highlights the true nature of cyber safety.
Even the most effective safety measures usually are not foolproof. Threats are continuously evolving, and new methods of assaults are being formulated. It’s secure to imagine that an assault on a system is inevitable.
Due to this fact, any group eager on defending the safety of its techniques must put money into risk identification even earlier than an assault occurs. By early detection of threats, organizations can swiftly implement injury management measures to reduce the chance and influence of the assault and even cease the attackers earlier than they deploy full-blown assaults.
Along with stopping assaults, risk detection can flush out malicious actors who could steal information, collect data for use in future assaults and even go away loopholes that may be exploited sooner or later.
A great way to detect threats and vulnerabilities earlier than they’re exploited by malicious actors is thru risk searching.
Menace Searching

Every time a cyber assault happens, comparable to a knowledge breach, malware assault, or perhaps a denial of service assault, it’s typically the results of cyber attackers lurking in a system for a while. This may span anyplace from a couple of days to weeks and even months.
The extra time attackers spend undetected in a community, the extra injury they’ll trigger. It’s, due to this fact, essential to weed out attackers who might be lurking in a community with out detection earlier than they really launch an assault. That is the place risk searching is available in.
Menace searching is a proactive cyber safety measure the place safety specialists do an intensive search in a community to find and root out potential threats or vulnerabilities which will have evaded present safety measures.
Not like passive cyber safety measures comparable to computerized risk detection, risk searching is an energetic course of involving an in-depth search of community endpoints and information saved in a community to find malicious or suspicious actions which will point out a risk lurking in a community.
Menace searching goes past on the lookout for what is thought additionally to weed out new and unknown threats in a community or threats that might have evaded a community’s defenses and haven’t but been remedied.
By implementing an efficient risk hunt, organizations can discover and cease malicious actors earlier than they execute their assaults, thus lowering the injury carried out and securing their techniques.
How Menace Searching Works

To be each profitable and efficient, risk searching depends closely on the instinct, strategic, moral, important pondering, and problem-solving expertise possessed by cyber safety specialists. These uniquely human expertise complement what might be carried out by way of automated safety techniques.
To conduct a risk hunt, safety specialists begin by defining and understanding the scope of networks and techniques the place they’ll carry out the risk hunt. All related information, comparable to log information and site visitors information, are then collected and analyzed.
In-house safety specialists are essential in these preliminary steps as they normally have a transparent understanding of the networks and techniques in place.
The gathered safety information is analyzed utilizing varied strategies to determine anomalies, hidden malware or attackers, suspicious or dangerous exercise, and threats that safety techniques could have flagged as resolved however weren’t truly resolved.
Within the occasion {that a} risk is detected, it’s investigated and remedied to forestall exploitation by malicious actors. In case malicious actors are found, they’re expunged from the system, and measures are carried out to safe additional and stop a compromise on the system.
Menace searching gives organizations with a possibility to study their safety measures and enhance their techniques to raised safe them and stop future assaults.
Significance of Menace Searching

Among the advantages of risk searching embody:
Scale back the damages of a full-blown cyber assault
Menace searching has the good thing about detecting and stopping cyber attackers who’ve breached a system earlier than they’ll collect sufficient delicate information to conduct a extra deadly assault.
Stopping attackers proper of their tracks reduces the damages that might have been incurred due to an information breach. With the proactive nature of risk searching, organizations can reply to assaults a lot sooner and therefore cut back the chance and influence of cyber assaults.
Scale back false positives
When utilizing automated cybersecurity instruments, that are configured to detect and determine threats utilizing a algorithm, circumstances come up the place they increase alerts the place there are not any actual threats. This will likely result in the deployment of countermeasures to threats that don’t exist.
Menace searching which is human-driven, eliminates false positives as safety specialists can conduct in-depth evaluation and make professional judgments on the true nature of a perceived risk. This eliminates false positives.
Assist safety specialists to know an organization’s techniques
A problem that arises after putting in safety techniques is verifying whether or not they’re efficient or not. Menace searching can reply this query as safety specialists conduct in-depth investigations and analyses to detect and remove threats which will have escaped the put in safety measures.
This additionally has the good thing about permitting in-house safety specialists to realize a greater understanding of the techniques in place, how they work, and easy methods to higher safe them.
Retains safety groups updated
Conducting a risk hunt includes utilizing the newest accessible know-how to detect and mitigate threats and vulnerabilities earlier than they’re exploited.
This advantages holding a company’s safety workforce updated with the risk panorama and actively participating them in discovering unknown vulnerabilities that may be exploited.
Such a proactive exercise leads to better-prepared safety groups who’re knowledgeable of latest and rising threats, thus stopping them from being shocked by attackers.
Shortens investigation time
Common risk searching creates a information financial institution that may be leveraged to hasten the method of investigating an assault within the occasion that it happens.
Menace searching includes in-depth examine and evaluation of techniques and vulnerabilities which have been detected. This, in flip, leads to a build-up of information on a system and its safety.
Due to this fact, within the occasion of an assault, an investigation can leverage gathered information from earlier risk hunts to make the investigation course of a lot sooner, permitting a company to answer an assault higher and sooner.
Organizations stand to learn tremendously by doing common risk hunts.
Menace Searching vs. Menace Intelligence

Though associated and infrequently used collectively to boost the cyber safety of a company, risk intelligence, and risk searching are distinct ideas.
Menace intelligence includes amassing and analyzing information on rising and present cyber threats to know the ways, strategies, procedures, motives, targets, and behaviors of the risk actors behind the cyber threats and assaults.
This data is then shared with organizations to help them in detecting, stopping, and mitigating cyber assaults.
However, risk searching is a proactive technique of trying to find potential threats and vulnerabilities which will exist in a system to handle them earlier than they’re exploited by risk actors. This course of is led by safety specialists. The risk intelligence data is utilized by safety specialists conducting a risk hunt.
Forms of Menace Searching

There are three foremost varieties of risk searching. This contains:
#1. Structured searching
It is a risk hunt based mostly on an indicator of assault(IoA). An indicator of assault is proof {that a} system is presently being accessed by unauthorized actors. IoA happens earlier than a knowledge breach.
Due to this fact structured searching is aligned with the ways, strategies, and procedures(TTPs) which might be employed by an attacker with the goal of figuring out the attacker, what they’re attempting to attain, and responding earlier than they do any injury.
#2. Unstructured searching
It is a sort of risk hunt carried out based mostly on an indicator of compromise(IoC). An indicator of compromise is proof {that a} safety breach occurred and a system was accessed by unauthorized actors prior to now. In any such risk searching, safety specialists search for patterns all through a community earlier than and after an indicator of compromise is recognized.
#3. Situational or Entity Pushed
These are risk hunts based mostly on a company’s inner threat evaluation of its techniques and the vulnerabilities they discovered. Safety specialists use externally accessible and newest assault information to search for related patterns and behaviors of assault in a system.
Key Components of Menace Searching
An efficient risk hunt includes in-depth information assortment and evaluation to determine suspicious behaviors and patterns which will point out potential threats in a system.
As soon as such actions are detected in a system, they have to be totally investigated and understood by way of the usage of superior safety investigation instruments.
The investigation ought to then yield actionable methods that may be carried out to resolve the vulnerabilities discovered and mediate the threats earlier than they are often exploited by attackers.
A closing key element of the method is reporting the findings of the risk hunt and offering suggestions that may be carried out to safe a company’s techniques higher.
Steps in Menace Searching
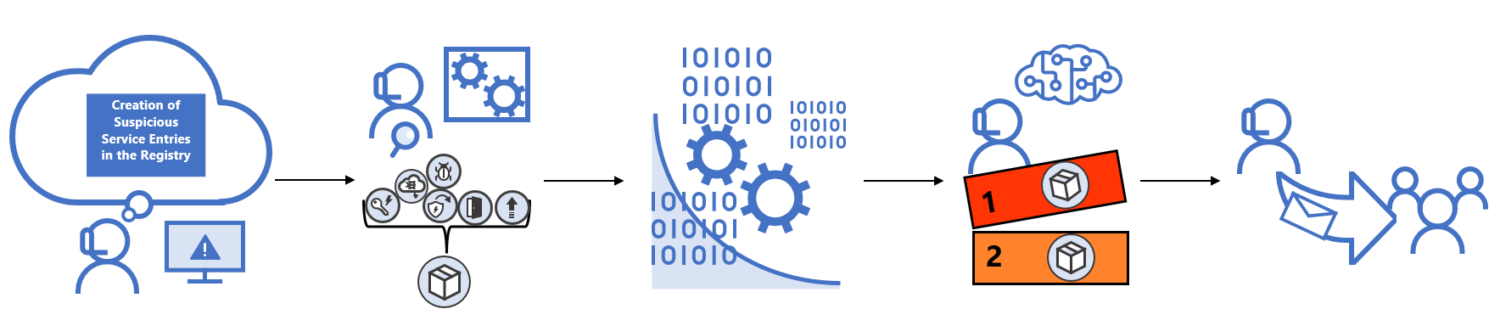
An efficient risk hunt includes the next steps:
#1. Formulating a speculation
Menace searching goals to uncover unknown threats or vulnerabilities that may be exploited by assaults. Since risk searching goals to seek out the unknown, step one is formulating a speculation based mostly on the safety standing and information of vulnerabilities in a company’s system.
This speculation offers risk searching a bearing and a basis upon which methods for the entire train might be laid.
#2. Information Assortment and evaluation
As soon as a speculation has been formulated, the subsequent step is gathering information and risk intelligence from community logs, risk intelligence experiences to historic assault information, with the goal of proving or disapproving the speculation. Specialised instruments can be utilized for information assortment and evaluation.
#3. Establish triggers
Triggers are suspicious circumstances that warrant additional and in-depth investigation. Info gotten from information assortment and evaluation could show the preliminary speculation, such because the existence of unauthorized actors in a community.
Through the evaluation of collected information, suspicious behaviors in a system could also be uncovered. These suspicious actions are triggers that have to be investigated additional.
#4. Investigation
As soon as triggers have been uncovered in a system, they’re investigated to know the complete nature of the chance at hand, how the incident might need occurred, the motive of the attackers, and the potential influence of the assault. The results of this investigation stage informs the measures that will probably be put in place to resolve the uncovered dangers.
#5. Decision
As soon as a risk has been totally investigated and understood, methods are carried out to resolve the chance, stop future assaults, and enhance the safety of the present techniques to handle the newly uncovered vulnerabilities or strategies that may be exploited by attackers.
As soon as all of the steps are accomplished, the train and repeated to search for extra vulnerabilities and higher safe the techniques.
Challenges in Menace Searching

Among the high challenges that come up in a risk hunt embody:
Lack of expert personnel
Menace searching is a human-driven safety exercise, and thus its effectiveness is closely pegged on the abilities and the expertise of the risk hunters conducting the exercise.
With extra expertise and expertise, risk hunters can have the ability to determine vulnerabilities or threats that slip conventional safety techniques or different safety personnel. Getting and retaining professional risk hunters is each expensive and difficult for organizations.
Issue in figuring out unknown threats
Menace searching may be very tough to conduct as a result of it requires the identification of threats which have evaded conventional safety techniques. Due to this fact, these threats don’t have any recognized signatures or patterns for simple identification, making the whole very tough.
Accumulating complete information
Menace searching depends closely on amassing massive quantities of knowledge on techniques and threats to information speculation testing and investigation of triggers.
This information assortment can show to be difficult as it could require superior third-party instruments, and there’s additionally a threat of the train not being compliant with information privateness rules. Moreover, specialists should work with massive quantities of knowledge which might be difficult to do.
Being updated with risk intelligence
For a risk hunt to be each profitable and efficient, the specialists conducting the train must have up-to-date risk intelligence and information of the ways, strategies, and procedures being employed by attackers.
With out entry to data on the newest tactic, strategies, and procedures utilized by assaults, the entire threat-hunting course of could also be hindered and rendered ineffective.
Conclusion
Menace searching is a proactive course of that organizations ought to contemplate implementing to safe their techniques higher.
Since attackers work around the clock to seek out methods of exploiting vulnerabilities in a system, it’s useful for organizations to be proactive and hunt for vulnerabilities and new threats earlier than attackers discover them and exploit them to the detriment of organizations.
You might also discover some free forensic investigation instruments for IT safety specialists.

